
Canonical releases Ubuntu Linux 24.04 LTS 'Noble Numbat'
Following a short beta test period, Canonical today released Ubuntu Linux 24.04 LTS. Codenamed “Noble Numbat,” this version promises enhanced performance, security, and developer productivity. Available for download at Ubuntu’s official site, this release marks a significant update supported for at least 12 years, emphasizing Canonical’s commitment to long-term support.
Mark Shuttleworth, CEO of Canonical, highlighted the release’s focus, “Ubuntu 24.04 LTS takes a bold step into performance engineering and confidential computing to deliver an enterprise-grade innovation platform.” This version introduces TCK certified Java, LTS for .NET, and the latest Rust toolchain, catering extensively to developer needs.

New tool lets enterprises build their own secure gen AI chatbots
Many companies have blocked access to public LLMs like ChatGPT due to security and compliance risks, preventing employees from taking advantage of the benefits of generative AI for day-to-day use.
Even when employees do have access, mainstream LLMs lack the ability to query an organization’s internal data, making insights unreliable and considerably limiting enterprise value for chat applications.

Younger women are going into cybersecurity but more needs to be done
New research from ISC2 shows improved representation of women under 30 in cybersecurity roles but concludes that more need to be done to improve diversity.
The study gathered responses from 14,865 people who participated in the latest ISC2 Workforce Study finds 36 percent of those under 30 were women compared to only 13 percent of those 65 or over and 17 percent overall.

Politically motivated DDoS attacks on the rise
This year has already seen several warnings of attacks targeting elections that are happening around the world.
A new report from NETSCOUT has identified a rise in politically motivated DDoS attacks. Peru experienced a 30 percent increase in attacks tied to protests about former Peruvian President Fujimori’s release from prison in December.

TCL 50 XL 5G Android smartphone hits Metro by T-Mobile: Big features, small price
TCL Mobile is set to make waves in the budget smartphone market with the launch of the TCL 50 XL 5G, available at Metro by T-Mobile here now. As the inaugural device in the highly anticipated 50 Series, the TCL 50 XL 5G aims to bring high-end technology within reach of more consumers with its attractive price tag of just $159.
The TCL 50 XL 5G boasts a large 6.78-inch FHD+ display complemented by a smooth 120Hz refresh rate, ensuring vivid visuals and fluid motion for an immersive viewing experience. This smartphone is not just about the display; it also features dual speakers enhanced with DTS sound technology, offering a superior audio experience for both headphone users and open-air listening.

The increasing sophistication of synthetic identity fraud
Synthetic identity fraud is most commonly associated with fraud in banking or against credit unions but is often mistakenly overlooked in digital commerce. With fraudsters becoming cleverer about how they use synthetic identities, it’s a tactic that fraud fighters need to watch out for and guard against.
Synthetic identity fraud is when a fraudster takes a piece of real identifying information belonging to a legitimate individual and combines it with other identifying information that is either fake or real but belongs to someone else.

The NIST/NVD situation and vulnerability management programs
In the infosec world we continually preach about “defense in depth,” or layered security. The idea is that if a defensive measure at one layer fails, there are additional layers behind it that serve as a safety net. An interesting application of these concepts comes in examining the data feeds that provide information to our security tools. If one of the feeds goes down, will our security tooling continue to work as expected?
This recently came to light when the National Institute of Standards and Technology (NIST) announced that it cannot keep up with the number of software bugs being submitted to the National Vulnerability Database (NVD). According to NIST itself, it has only analyzed roughly one-third of the Common Vulnerabilities and Exposures (CVEs) submitted this year. Since many organizations rely on NVD information in their vulnerability management programs, this is distressing news. For organizations in this situation, the question then becomes: How do we minimize the impact of the NIST backlog?

How AI will shape the future of the legal industry
The Department for Science, Innovation and Technology (DSIT) announced a £6.4 million grant for small and medium-sized enterprises (SMEs) to invest in AI-technology skills-based training. This development is the latest in a string of AI funding initiatives across the UK corporate sector, indicating that 2024 is the year emerging technologies will revolutionize the workplace in all aspects.
AI technology is transforming business functions across industries. However, the legal sector, in particular, has demonstrated tremendous progress. Often portrayed as laggards when it comes to embracing innovation, legal’s cautious, conservative approach to tech adoption has become a thing of the past in the age of AI. A recent survey from the Legal Services Board (LSB) discusses how over 95 percent of legal businesses found that implementing new technologies has made them more responsive to clients’ needs. Moreover, 60 percent of surveyed legal businesses found their clients expect them to power their legal services through tech innovation.

Start menu ads are rolling out to all Windows 11 users -- here's how to turn them off
Windows 11's Start menu will soon advertise applications in the recommended section.
Microsoft released a new optional preview update for Windows 11 this week that introduces the feature. The changes it includes will roll out to all Windows 11 devices as part of the May 2024 cumulative security update.

Qualcomm introduces Snapdragon X Plus for Windows PCs
Today, Qualcomm introduces the Snapdragon X Plus platform, which features the all-new 10-core Qualcomm Oryon CPU and a 45 TOPS (Tera Operations Per Second) NPU, touted as the fastest NPU for laptops globally. This combination aims to set a new benchmark for mobile computing by providing up to 37% faster CPU performance while consuming up to 54% less power compared to its competitors.
Kedar Kondap, Senior Vice President and General Manager of Compute and Gaming at Qualcomm Technologies, highlighted the transformative potential of the new chipset. "Snapdragon X Series platforms deliver leading experiences and are positioned to revolutionize the PC industry," said Kondap. He emphasized that the Snapdragon X Plus would power "AI-Supercharged PCs," enabling radical new AI experiences amid rapid technological advancements.

Free test lets you check how websites measure up to privacy rules
Governments around the world have been busily introducing privacy rules over the last few years and only this month the US Congress introduced a draft of a new federal law, the American Privacy Rights Act (APRA).
But how do you know if the websites you use are following the rules? ImmuniWeb is launching a new free website privacy test with checks and verifications that cover specific requirements of the majority of modern privacy, data protection and consumer protection laws in the US, UK, Europe and other regions.
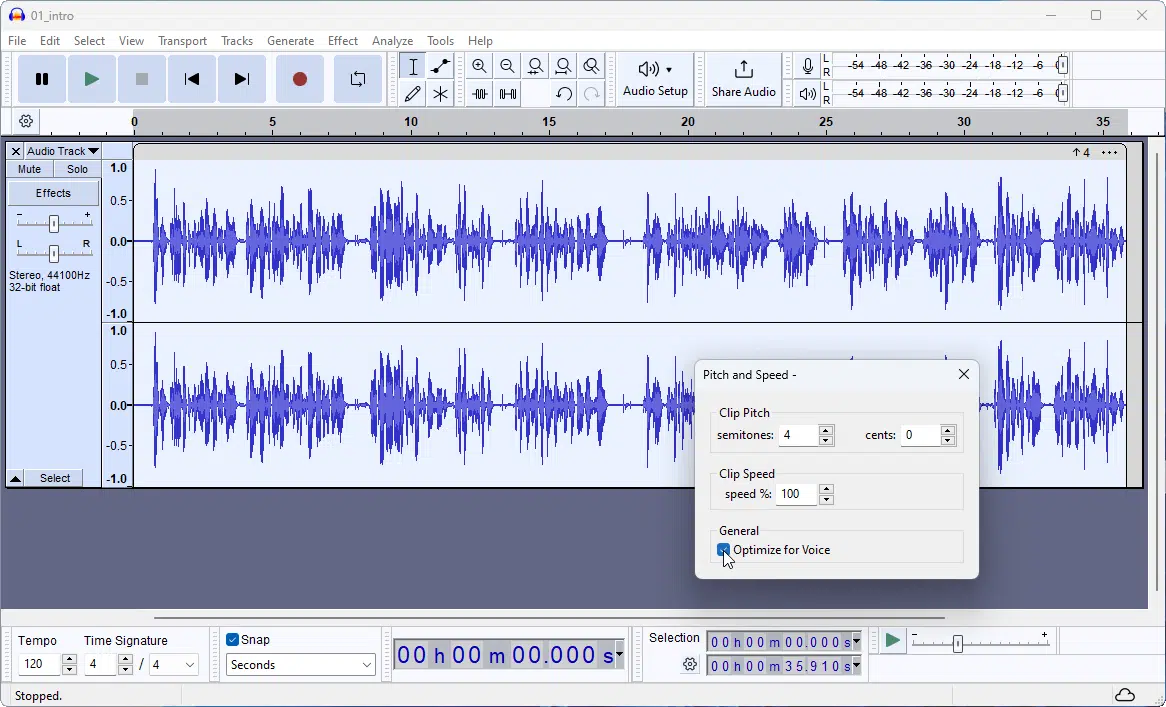
Audacity 3.5 adds cloud project saving for collaboration, backup and file versioning
Muse Group has released a major new version of its free, open-source audio editor for Windows, macOS and Linux. Audacity 3.5 adds cloud project saving support, plus adds automatic tempo detection, pitch shifting and more.
The headline new feature in Audacity 3.5 is a new cloud-saving feature, which works in tandem with Muse Group’s free audio hosting platform at audio.com. Users simply select 'File > Save to Cloud…' to save the current project. On first use, they will be prompted to link Audacity to a free audio.com account -- which can be created during the linking process.

Get 'Principles of Data Science -- Third Edition' (worth $39.99) for FREE
Principles of Data Science bridges mathematics, programming, and business analysis, empowering you to confidently pose and address complex data questions and construct effective machine learning pipelines.
This book will equip you with the tools to transform abstract concepts and raw statistics into actionable insights. Starting with cleaning and preparation, you’ll explore effective data mining strategies and techniques before moving on to building a holistic picture of how every piece of the data science puzzle fits together.

CISOs worry about gen AI leading to security breaches
A new survey of more than 400 CISOs in the US and UK reveals that 72 percent are concerned about security breaches related to generative AI.
The study from Metomic finds that CISOs from both the US and UK rank data breaches as their top security concern. Data breaches are continuing to surge across industries, but particularly for healthcare, finance, and manufacturing organizations. According to industry reports, US companies experienced 3,205 data breaches last year (up from 1,802 in 2022), with the average cost of a data breach in the US climbing to $9.48 million in 2023.

Six out of 10 businesses struggle to manage cyber risk
A new study from Barracuda Networks finds just 43 percent of organizations surveyed have confidence in their ability to address cyber risk, vulnerabilities, and attacks.
The findings also show that many organizations find it hard to implement company-wide security policies such as authentication measures and access controls. 49 percent of the smaller to mid-sized companies surveyed listed this as one of their top two governance challenges.


