
Five sustainability trends businesses will embrace in 2024
A sense of urgency to address climate change has led many businesses to commit to carbon neutrality or net-zero emissions by 2030, and many more by 2050, yet just 5 percent of the UK’s biggest companies have said how they plan to get there.
This disconnect between ambition and action is something my firm is out to solve through IT infrastructure. These are five of the biggest sustainability trends I believe businesses must pay attention to in 2024.

Get 'GitHub For Dummies, 2nd Edition' (worth $18) for FREE
For today’s coders, GitHub is a must. The world’s largest software development platform, GitHub helps developers store, track, and collaborate on software projects.
In this easy-to-follow Dummies guide, you’ll find insight into creating repositories, establishing projects, collaborating, incorporating open-source resources, and establishing yourself as a valued member of the GitHub community.

Will Artificial Intelligence power online trading solutions in the future?
Artificial Intelligence (AI) has become a buzzword in various industries and the world of online trading is no exception. With its ability to analyze vast amounts of data and make predictions, AI has the potential to revolutionize the way we trade online. Or maybe that's not the case at all. The point in fact is that AI has been integrated into various systems across numerous different industries already.
However, using AI in the financial market, especially, in trading stocks, bonds, cryptocurrencies and other assets is up to debate. After all, is using AI's machine learning and predictive analysis considered cheating? How is it any different when investors rely on informer insights and leaked documents? The software is just better at processing data than human is.

New collaboration helps organizations defend against AI and quantum risks
One of the key recent concerns for security teams has been developing the ability to adapt to advancements in technology and innovations such as AI and quantum computing.
A new partnership between Accenture and SandboxAQ aims to give organizations the ability to scan all of their files, applications and network traffic to ensure that all of their data -- whether on-premise or hosted via major cloud providers -- is secure even if attackers break through firewalls and network endpoints.

Turtle Beach accelerates into the racing sim market with VelocityOne Race
Turtle Beach has announced its latest product -- the VelocityOne Race. This universal wheel and pedal system, compatible with Xbox and Windows PCs, is engineered to offer an immersive racing experience.
VelocityOne Race features the custom K: Drive motor, providing direct-drive force feedback for a realistic and detailed response to in-game events. Racers will find high-end aluminum pedals and Dynamic Brake Tek load-cell brakes underfoot, designed to mimic real-life braking. The system also allows racers to monitor real-time telemetry data in many popular games, enhancing the simulation experience.
94 percent of organizations suffer email security incidents
According to a new study, 94 percent of global organizations have experienced email security incidents last year, up two percent from the year before.
The latest Email Security Risk Report from Egress looks at attitudes and approaches to email security, the evolution of risks, and the impact of incidents, based on responses from 500 cybersecurity leaders.

YouTube seems to be slowing the site for anyone with an ad blocker
YouTube hates ad blockers, and the site has been trying to discourage visitors from using them for quite some time. After introducing warnings last year, the site now appears to be reducing performance for anyone who tries to make use of an ad blocker.
While there has been no official announcement about it, the slowdown has not gone unnoticed by YouTube users. Posts on Reddit reveal the laggy site experience for people using an ad blocker -- lag which disappears as soon as ads are re-enabled.

Microsoft launches Copilot Pro subscription for people willing to pay to supercharge their AI experience
Microsoft continues to throw everything at artificial intelligence, in particular its AI companion Copilot. The company's latest move sees it launching Copilot Pro, a subscription service which gives anyone -- not just businesses and organizations -- access to a more up-to-date and advanced version of the chatbot, including OpenAI's GPT-4 Turbo model.
Designed with "power users, creators and anyone looking to take their Copilot experience to the next level" in mind, Copilot Pro is a $20-per-month attempt by Microsoft to squeeze some money out of AI. The company has also expanded the availability of Copilot for Microsoft 365 to more commercial customers.

AVerMedia launches new PCIe capture cards -- HDMI 2.1 Live Gamer 4K 2.1 (GC575) and Live Streamer ULTRA HD (GC571)
AVerMedia has launched two new PCIe capture cards: the HDMI 2.1 Live Gamer 4K 2.1 (GC575) and Live Streamer ULTRA HD (GC571). These latest offerings are designed to cater to both experienced and novice streamers.
The flagship Live Gamer 4K 2.1 (GC575) is designed to be the premier consumer-grade HDMI 2.1 PCIe capture card in the world. This card is engineered to leverage the full potential of HDMI 2.1 technology. With features like 4K144 pass-through HDR/VRR, the card delivers every gameplay moment with exceptional clarity and smoothness. It also supports up to 4K60 capture, allowing streamers to record their gaming experiences with unprecedented precision.

Apple dethrones Samsung to become smartphone market king of 2023
In an unexpected turn of events, Apple has toppled Samsung from its long-held position as the leader of the smartphone market. This marks the first time since 2010 that a company other than Samsung has clinched the top spot. The 2023 landscape of consumer electronics saw Apple reaching an unprecedented market share, signaling a significant power shift in the industry.
Despite global smartphone shipments falling by 3.2% to 1.17 billion units in 2023, Apple's rise to prominence is a clear indicator of the market's rapid evolution. This decline, the most considerable in a decade, is attributed to macroeconomic challenges and high inventory levels at the year's start. However, a rebound is on the horizon, with the latter half of 2023 showing promising growth and setting the stage for a potential recovery in 2024. The fourth quarter of 2023 alone witnessed an 8.5% year-over-year growth, surpassing the forecasted 7.3%.
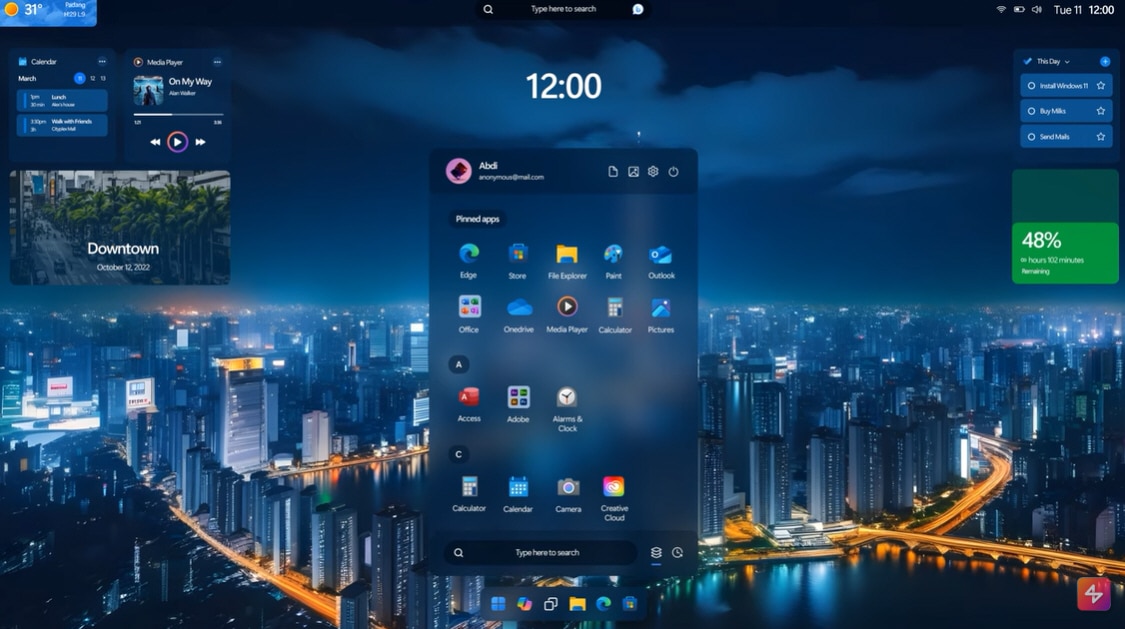
The 'revolutionary' Windows 12 is the Microsoft operating system we need!
Microsoft is set to pull the plug on Windows 10 in the near future, leaving people with the choice of upgrading to Windows 11, or hanging on for the inevitable follow up, which is expected to be Windows 12.
Although Microsoft hasn't officially announced that next-gen operating system yet, it has dropped plenty of hints, and rumors suggest we might see Windows 12 arrive sooner rather than later. If you’re wondering what the new OS might look like, we have an idea.

Xiaomi launches Redmi Note 13 Android smartphones
Xiaomi has officially launched its Redmi Note 13 Series at an event in Bangkok, Thailand. The series introduces five new devices: Redmi Note 13 Pro+ 5G, Redmi Note 13 Pro 5G, Redmi Note 13 Pro, Redmi Note 13 5G, and Redmi Note 13. These models aim to bridge the gap between mid-range and high-end smartphones, offering various enhancements in camera systems, design, display, and processing capabilities.
The Redmi Note 13 Series emphasizes camera improvements, particularly in the Pro models (Redmi Note 13 Pro+ 5G, Redmi Note 13 Pro 5G, and Redmi Note 13 Pro), which feature a 200MP camera with optical image stabilization (OIS). This camera system includes 2x/4x lossless zoom, a large 1/1.4" sensor, and enhanced image processing capabilities. The base models, Redmi Note 13 5G and Redmi Note 13, come equipped with a 108MP main camera and offer various camera filters. All devices in the series incorporate Xiaomi's Imaging Engine, aiming to improve computational photography and image processing.

Balancing risk and reward with low-code and no-code platforms [Q&A]
In recent years, enterprises have increasingly turned to low-code and no-code platforms in order to streamline their development processes.
With the introduction of AI, this sector is evolving even faster and Wing To, general manager of Intelligent DevOps at Digital.ai, believes this needs organizations to develop a cautious approach. We spoke to him to find out why.

Streaming the AFC Wild Card football game exclusively on Peacock was a huge success for the NFL, but it sucks for traditional TV consumers
Despite complaints from many football fans, the NFL's first-ever exclusively live-streamed playoff game, hosted on Peacock, has apparently set new records. The Kansas City Chiefs, led by two-time Super Bowl MVP Patrick Mahomes, triumphed over the Miami Dolphins with a score of 26-7, in what was the fourth-coldest NFL game ever recorded. This historic event took place in front of a crowd of over 71,000 fans, marking a significant milestone for both the NFL and Peacock.
The Peacock Exclusive AFC Wild Card Game reached a staggering 27.6 million total viewers, according to Nielsen data. The game peaked with 24.6 million viewers in the second quarter, and set a new U.S. record as the most-streamed event with an average audience of approximately 23.0 million viewers across various platforms. This surge in digital viewership represents a 6 percent increase from the previous year's primetime AFC Wild Card Game.
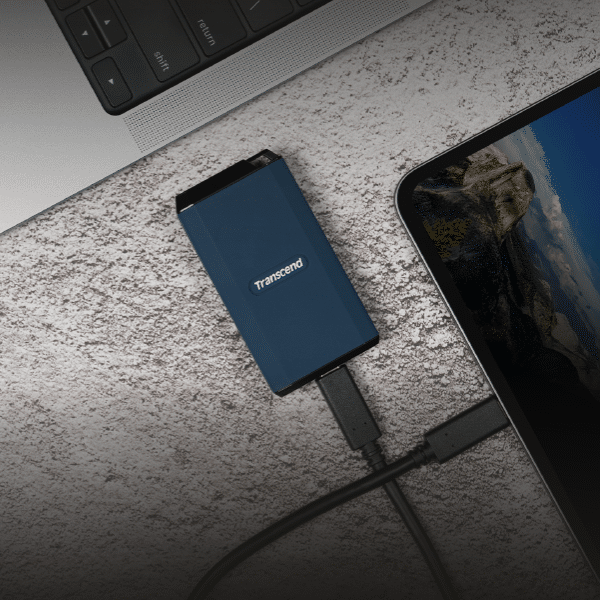
Transcend unveils new portable SSDs
Transcend has announced the launch of its new portable SSD lineup. The series includes five models: ESD410C, ESD360C, ESD330C, ESD320A, and ESD265C. Each model boasts unique features and designs, aimed at a diverse consumer base.
The ESD410C model stands out with its USB 20Gbps transfer rate, 4TB storage capacity, and a design that meets MIL-STD-810G standards for durability. This makes it suitable for professionals who require high-speed data transfers and a rugged storage solution.



