
Ultimate Ears launches EPICBOOM Bluetooth speaker
Ultimate Ears, the high-fidelity offspring of Logitech, is giving us yet another reason to jam out wherever we please with its newest release—the EPICBOOM portable Bluetooth speaker.
It's no secret that we're in the midst of an environmental crisis, and guess what? Ultimate Ears knows it too. The EPICBOOM isn't just about belting out crisp tunes; it's also about being good to Mother Earth. The speaker is crafted from 100 percent post-consumer recycled polyester fabric and a minimum of 59 percent post-consumer recycled plastic. "We design our products with our customers and their lifestyles in mind," says Jonah Staw, the General Manager of Ultimate Ears. Clearly, part of that lifestyle includes caring for the planet we call home.

Logitech Pebble 2 Combo blends style, functionality, and sustainability
Today, Logitech unveils the Pebble 2 Combo keyboard and mouse that seamlessly blends form and function. Not only is this combination beautiful, but it is quite affordable too.
This combo is available in five colors: Tonal Graphite, Tonal White, Tonal Rose, Tonal Sand, and Tonal Blue. With a minimalist design, both the Pebble Keys 2 K380s keyboard and the Pebble Mouse 2 M350s make a subtle yet strong style statement. Plus, they are crafted from recycled plastic.

Logitech G launches PRO X TKL LIGHTSPEED keyboard and SUPERLIGHT 2 mouse
Today, Logitech G (a name synonymous with top-of-the-line gaming peripherals), has unveiled the latest products in its award-winning PRO series: the Logitech G PRO X TKL LIGHTSPEED gaming keyboard and the Logitech G PRO X SUPERLIGHT 2 gaming mouse. These gaming peripherals were developed in collaboration with elite esports athletes.
According to Brent Barry, Head of Esports and PRO Series at Logitech G, this new lineup "represents a pure and uncompromised product collection, designed for the maximum performance of elite esports professionals and the most competitive gamers." The products are born out of years of intensive consultation and development with top esports athletes, yielding high-performance gear for those who accept nothing less than the best.

Google is turning Android 3D
There is so much focus on AI from the likes of Google, Microsoft et al that it's easy to forget that there are other things happening in the tech world. Case in point: Google's new 3D look for Android.
Sadly, we're not talking about a three-dimensional mobile operating system offering virtual reality or anything like that. Google is simply updating its branding, and this means a new logo for Android.

KLEVV unveils CRAS C910 Lite M.2 NVMe PCIe Gen4x4 SSD
When it comes to storage solutions, performance and reliability are key. Today, KLEVV announces its all-new PCIe Gen4x4 M.2 Solid State Drive, the CRAS C910 Lite, which promises to deliver both in spades.
The CRAS C910 Lite comes in storage capacities that range from 500GB to a whopping 4TB, all housed in an ultra-thin, single-sided M.2 2280 design that weighs just 7 grams. This makes it perfect for everything from mini-PCs to the latest ultrabooks.

Kingston launches XS1000 external SSD
Kingston has once again upped the ante in portable storage solutions by unveiling its new XS1000 external SSD. Slotting alongside the existing XS2000, this new release is another feather in Kingston's already well-adorned cap, offering consumers even more choice in a competitive market.
The XS1000 doesn't just talk the talk; it walks the walk. We're looking at read speeds of up to 1,050MB/s and write speeds up to 1,000MB/s. With a maximum capacity of 2TB, the XS1000 not just fast but incredibly spacious, giving you room to store a colossal amount of data. Plus, it’s small enough to be mistaken for a key fob (69.54 x 32.58 x 13.5mm) and weighs less than 29 grams.

Manjaro Linux 23.0 'Uranos' is here with GNOME, Plasma, and XFCE editions
The developers of Manjaro have delivered version 23.0 of the operating system, and this time, it's code-named “Uranos.” Following the lauded release of Talos in April 2023, the developers at Manjaro haven't taken a moment's rest. Whether you're in the GNOME, Plasma, or XFCE camp, there’s a lot to unwrap, so let's dive in.
First on our list is the GNOME edition, which has been tuned to the melodious notes of the GNOME 44 series, a release that originally made its debut back in March. The point releases from 44.1 to 44.4 have each added their own layer of polish and precision, and for those interested in the details, the release notes are your go-to source.

The IT assets that could put your organization at risk
Attackers are always looking for routes that will offer them a way into organizations' networks. New research released today by Armis shows the devices that are most likely to pose a threat.
Interestingly the list includes various personal devices as well as business assets, suggesting attackers care more about their potential access to assets rather than the type and reinforcing the need for security teams to account for all physical and virtual assets as part of their security strategy.
Millions of Freecycle users need to change their passwords following a huge data breach
Swap-unwanted-stuff-for-free site Freecycle has acknowledged a security breach that took place at the end of last month. Hackers were able to access a wealth of data including usernames, User IDs, email addresses and passwords.
The organization says that it has notified the "appropriate US authorities" of the incident, as well as the Information Commissioner's Offier (ICO) in the UK. Few details of what happened have been revealed, but Freecycle is advising all members to change their account passwords as a security measure.

Two out of three companies lose data due to failed backups
Of the 90 percent of UK enterprises that have been forced to turn to their backup system, only 27 percent were able to recover all of their information and documents -- down from 45 percent in 2022.
A survey from encrypted drive maker Apricorn finds 32 percent of the security decision makers in large enterprises surveyed attributed the unsuccessful recovery to a lack of robust backup processes, up from two percent in 2022.

Tronsmart Bang Max Bluetooth speaker features 130W sound and dynamic lights
If you've ever found yourself desperately searching for that perfect speaker that brings both sonic supremacy and an electrifying light show to your events, look no further. Tronsmart, a brand that has consistently delivered top-notch audio gadgets, is back in the limelight with their newest flagship—the Bang Max Bluetooth speaker.
With an unbelievable 130W sound output, the Bang Max doesn't just play music; it commands your auditory senses. And the party doesn't stop at the eardrums. This technological marvel boasts dynamic, pulsating lights that sync with the beat of your favorite tunes, creating an immersive atmosphere that is as much a visual feast as it is an auditory one.
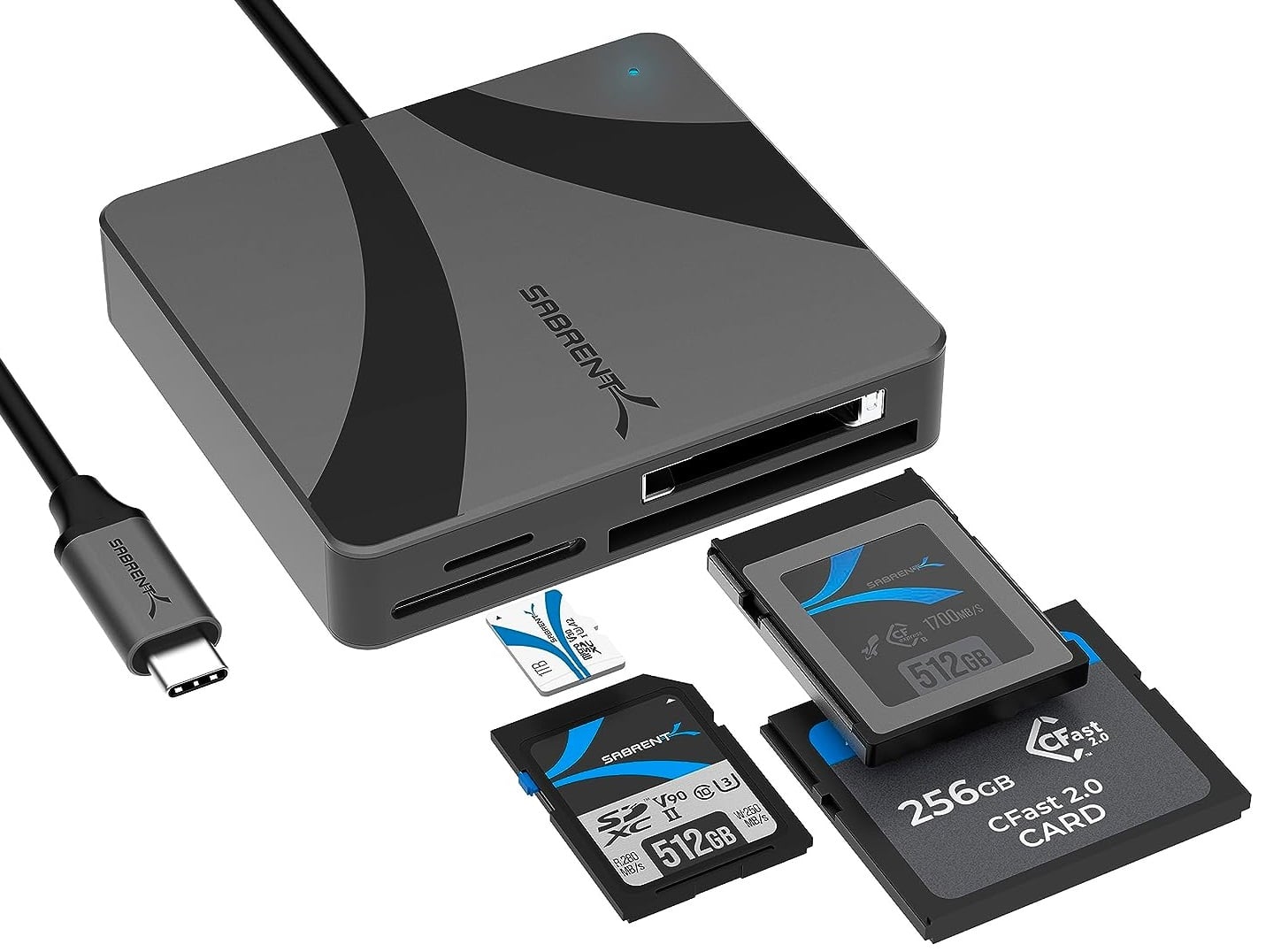
Sabrent launches CR-C4PM USB-C multi-card reader
Ah, memory cards! These tiny repositories are where our most cherished memories reside -- be it those perfect beachside vacation photos or crucial files for an impending work deadline. But let’s be honest, dealing with different types of memory cards across various devices can be cumbersome. Enter the Sabrent USB-C Multi-Card Reader (CR-C4PM), a slick and versatile solution that is as portable as it is powerful.
This card reader has a lot going for it. It’s portable, rugged, stylish, and plug-and-play. You can feel the quality just holding it; the aluminum main body is adorned with an ABS casing for that added durability and aesthetic appeal. Oh, and let's not forget, it helps in improved heat dissipation. So, you don't have to worry about the reader or your precious cards getting fried during sustained operations.

The business-enabling power of privacy enhancing technologies
Over the past few years, there has been an acceleration in the enterprise-level understanding of Privacy Enhancing Technologies (PETs), a category best known for its ability to enable and preserve the security and privacy of data when it is being used or processed. While some technologies within the category, including homomorphic encryption, trusted execution environments, and secure multiparty computation, had previously been academically pursued but not computationally practical, the tide has changed.
Technological development, surging awareness, and increasing adoption of PETs in recent years have alerted regulators, analysts, and broader industry to their potential impact and opened up a wealth of exciting and transformative opportunities for businesses.

Microsoft Windows 11 users should switch to Ubuntu-based Linux Lite 6.6 now
You know, it's often hard to get people to leave their comfort zones. But, sometimes, staying where you're comfortable is the biggest impediment to progress. This is especially true when it comes to operating systems. While Windows 11 has been generating buzz with its new features and revamped UI, let's not forget the other contenders that are pushing boundaries. Linux Lite 6.6 is one such alternative, and dare I say, it's one of the most inviting Linux distributions out there for those looking to make a switch.
The Linux Lite team has really outdone themselves this time around. The 6.6 release is one of their largest since they launched back in 2012. They've added thousands of lines of new code, predominantly to support a vast range of languages. From Afrikaans to Ukrainian, Linux Lite 6.6 now supports a whopping 22 languages, covering areas such as Main Menu, Right Click Menu, Folder Names, and even Desktop Icons. This is an incredible leap toward making Linux Lite a truly global OS.

Transcend unveils ESD300 USB-C SSD
Transcend has unveiled its latest portable solid state drive. Called “ESD300,” it might be the size of a typical USB drive, but make no mistake—this is a full-fledged SSD with specs that’ll leave you smiling. We’re talking read/write speeds of up to 1,050/950 MB/s. And the robust aluminum casing isn’t just for show; it serves the vital function of dissipating heat, ensuring your data remains safe and sound.
The ESD300 comes equipped with a versatile USB Type-C connector, offering a bridge to an array of devices and operating systems—be it Windows, macOS, iPadOS, or Android. Forget the cable spaghetti or dongles; one connector to rule them all makes data transfer between devices a cinch.


