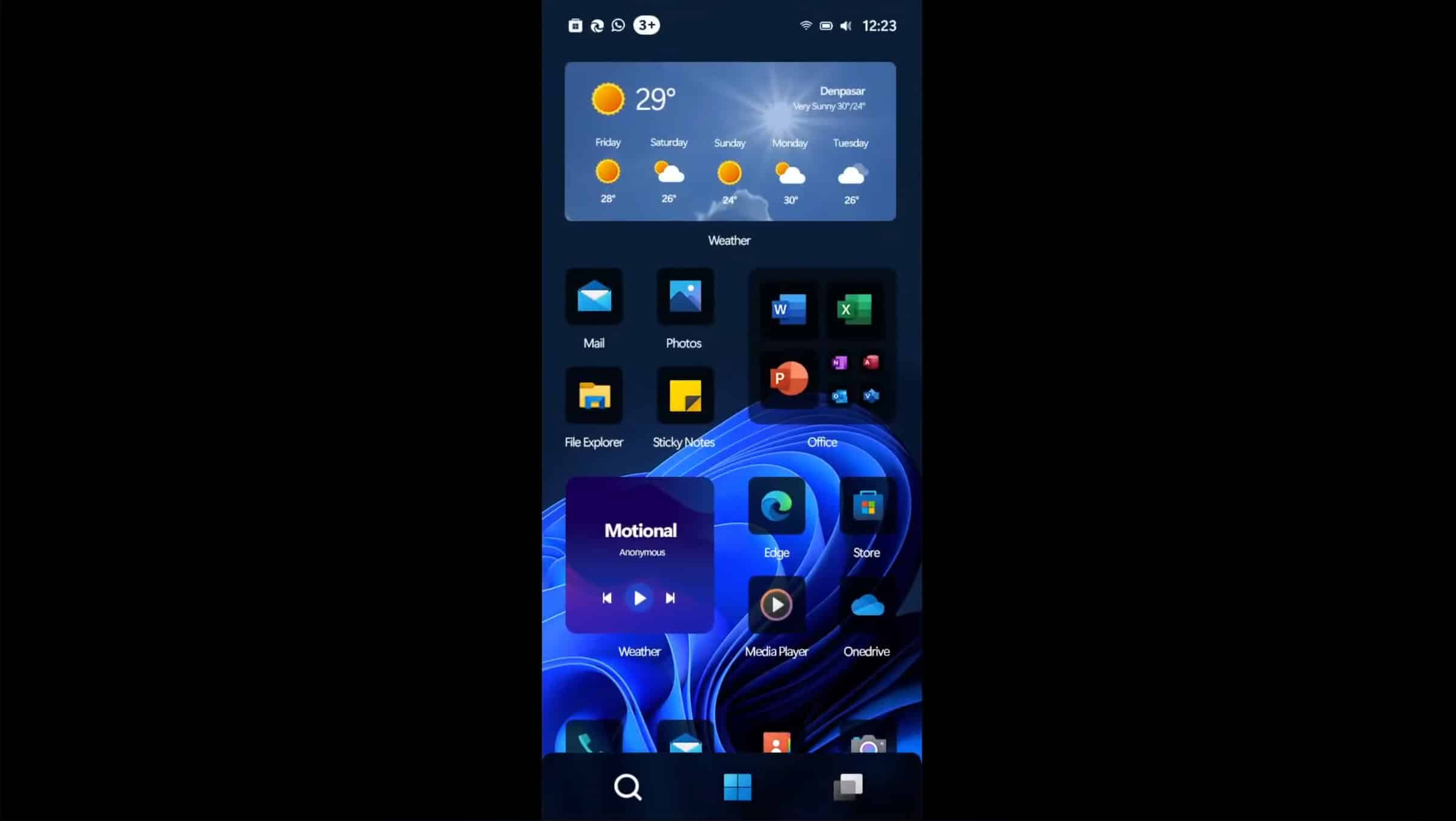
Windows 11 Mobile is everything a phone operating system should be
Microsoft made a significant investment in Windows 10 Mobile, including acquiring Nokia to produce its own handsets. Despite the strengths of the tiled mobile operating system, it was unable to compete with the dominant iOS and Android platforms. While Windows 10 became a successful operating system for PCs and tablets, Microsoft was eventually abandon its mobile ambitions
As Windows 11 gradually replaces Windows 10, the question remains whether it would perform better than its predecessor in the mobile space.

A small number of exposures can put 90 percent of critical assets at risk
New research reveals that a small volume of security exposures can put more than 90 percent of an organization's critical assets at risk of compromise.
The analysis of more than 60 million exposures in over 10 million entities from XMCyber, in collaboration with the Cyentia Institute, finds just two percent of security exposures can actually lead to critical assets and most exposures (75 percent) along attack paths lead to 'dead ends'.

Is ChatGPT AI the next Superman or humanity's Kryptonite? [Q&A]
Now that the dust has settled on the hype around ChatGPT, it may be a good time to unpack the full implications of this technology. While it might help sleep-deprived college students ace term papers and give copywriters a creative boost, it has a potentially dark underbelly.
We talked to David Carvalho, CEO and co-founder of Naoris Protocol, to unpack some of the not so pretty aspects of emerging AI technology and its potential to wreak havoc for businesses globally.
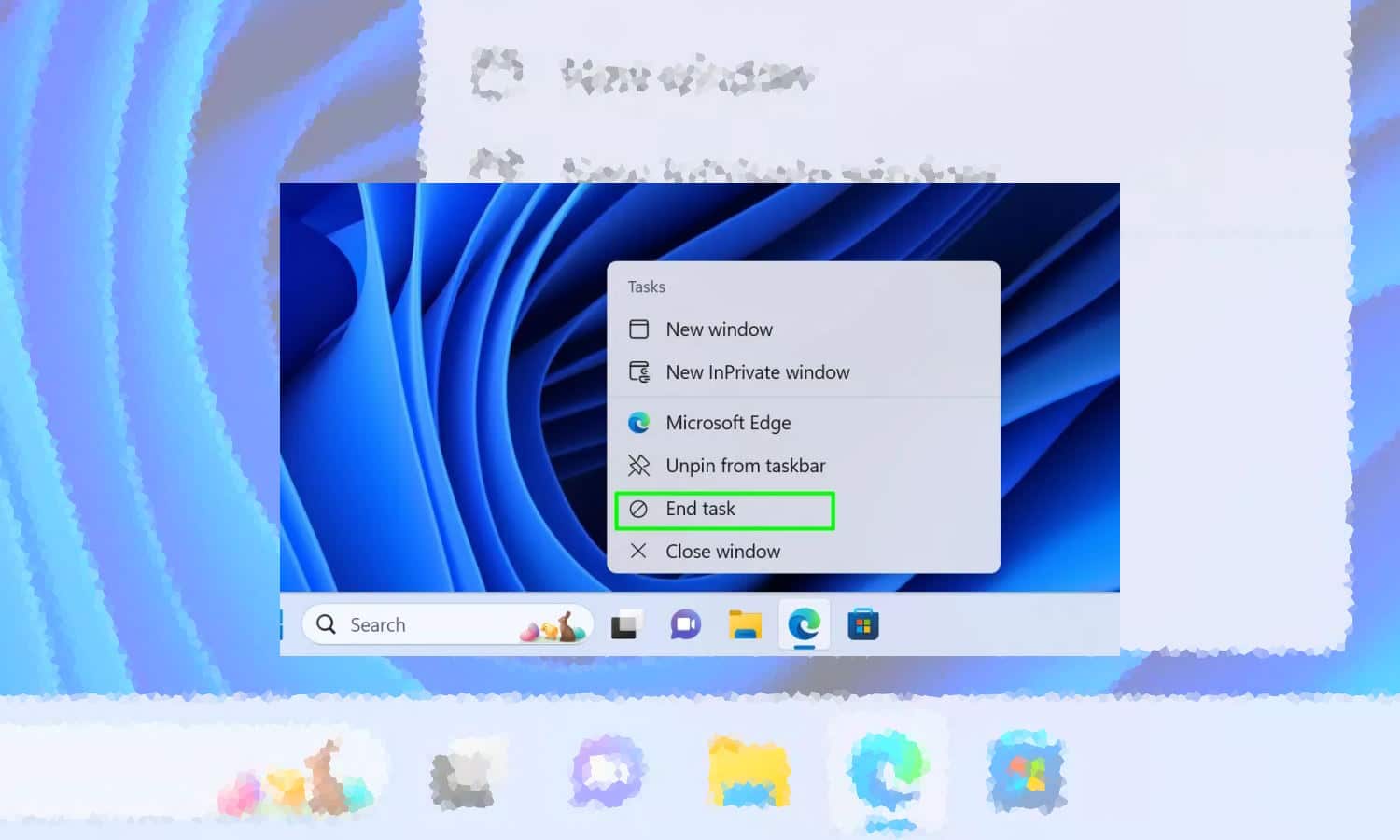
Microsoft is making it easier to terminate unresponsive apps in Windows 11 with new End Task option
Use Windows 11 for long enough, and you will almost certainly encounter an app that becomes unresponsive. And when an app freezes, you're likely to find that it misbehaves to the point that it is not possible to close it in the usual way.
When this happens, you may well fire up Task Manager, locate the troublesome app or process in the list and terminate it. But to help optimize this unnecessarily lengthy process, Microsoft is introducing a new End Task option that can be accessed from the Windows 11 taskbar.

Windows 10 vs. Windows 10X vs. Windows 11: A triple comparison
If you’re running a modern version of Windows, you'll either be on Windows 10 or Windows 11. For a while though, Microsoft was working on Windows 10X, a version of the OS designed for modern PCs.
Windows 10X was built from scratch on top of "Windows Core OS" and aimed to do away with legacy features and offer a simplified Windows experience. It was cancelled in 2021, although leaked builds did give us an idea of how it would look and what it would offer.

Locking cyber doors: How organizations can be cyber safe in 2023
Our tech-filled lives put us at daily risk of cybercrimes, as we spend the majority of our time interacting with devices that could give hackers access to our personal data. In fact, according to DataProt, nearly 60 Percent of Americans say they have experienced cybercrime or somehow fell victim to a hacker. As every aspect of our lives becomes more connected, the opportunities for bad actors rise.
Businesses are not immune to these persistent threats. Reports show that 70 Percent of small businesses are unprepared for a cyberattack, and almost 90 Percent of professional hackers can penetrate a company within 12 hours. It is no surprise that the Federal Bureau of Investigation (FBI) has officially ranked cybercrime as one of its agency’s most important interests.

The roll out of integrated AI image generator to all Microsoft Edge users begins
Microsoft has started the rollout of Edge Image Creator to all users. Continuing its love affair with all things related to artificial intelligence, the company's in-browser AI image generator is powered by OpenAI's DALL-E.
Rolling out the tool to Edge comes just a few weeks after Microsoft announced the launch of Bing Image Creator in the preview version of the browser and the new Bing. It means that everyone running the desktop version of Edge will have access to Image Creator.
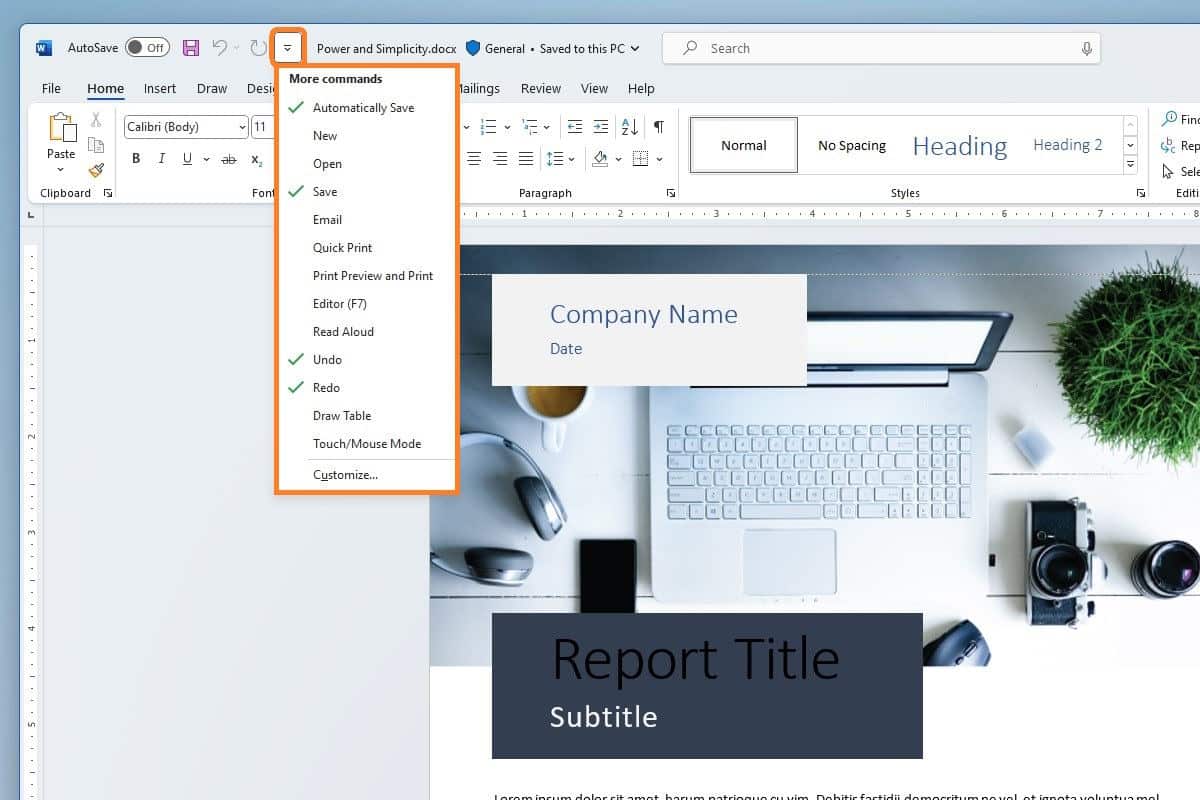
Microsoft bows to feedback and reverses Quick Access Toolbar changes in Office
Microsoft has acknowledged that changes to the Quick Access Toolbar in Office were "disruptive and slowed […] workflow. Having used the Microsoft 365 Visual Refresh to hide the QAT toolbar by default and move various commonly used button, the company has listened to user feedback ad reversed its changes.
Among the complaints that ultimately forced Microsoft to perform the U-turn were criticism of the decision to relocate the Undo and Redo buttons. In announcing the about-face, the company does not really admit to making a misstep, merely that the previous change "wasn't quite right".

Kodi forum breach exposes user data
A breach of the Kodi user forum has exposed the personal data of over 400,000 users. The web-based MyBB admin console was accessed -- on February 16 and February 21 2023 -- and the team says it first became aware of this when a dump of the forum's database was found for sale on an internet forum.
The database dump contains a wide range of user data, including names, email addresses, IP addresses, and passwords. The data was accessed using the account of a trusted but currently inactive member of the forum admin team.
Automation challenges unpacked -- Part 1: Endpoint diversity
Overall, 96 Percent of IT leaders in the State of Process Orchestration report say process automation is critical to helping them accelerate their digital transformation goals. Even so, 72 Percent agree that their real-world, business-critical processes are becoming more difficult to maintain. Why is that the case? For many companies, process automation challenges tie to two core concepts: endpoint diversity and process complexity.
I’ll cover process complexity in part two of this series, but for now, let’s dig into some of the challenges that stem from endpoint diversity and how to solve them.

Microsoft adds Bing Chat AI to SwiftKey Beta for Android
Microsoft, Google and just about every other tech firm in existence is busy embracing artificial intelligence. In the latest example of bandwagon-jumping, the Windows-maker's new beta version of the SwiftKey keyboard for Android has gained AI functionality.
New capabilities come courtesy of Bing Chat AI, with Android users "slowly" gaining access to the power of Microsoft's chatbot; it is not yet clear quite when iOS users might also get the same treatment. But just what does the arrival of Bing Chat integration mean for SwiftKey?

Outlook users face email issues as Microsoft starts using OneDrive cloud storage space for email attachments
If you are having trouble sending and receiving email via your Outlook.com account, you are not alone. Problems have started to surface following a recent policy change by Microsoft that means email attachments now eat into OneDrive storage limits -- as we reported previously.
Microsoft started to roll out the change at the beginning of February, but it seems that the pace of the rollout has increased as more and more users are hitting their storage limits and experiencing problems with their emails.

MSI urges caution when downloading BIOS and firmware updates following cyberattack and rumors of $4 million ransom demand
Computer maker MSI has confirmed that it fell victim to a security breach, confirming rumors that sprang up in recent days. The Taiwanese company says that it "suffered a cyberattack on part of its information systems", and has warned customers to exercise caution when downloading BIOS and firmware updates for its products.
Although MSI has shared little in the way of detail about the incident, the confirmation comes after the ransomware group Money Message was said to have breached the company's defenses. The group has made demands for $4 million with the threats of leaking stolen files.

Best Windows apps this week
Five-hundred-and-thirty-seven in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft's official Store on Windows 11 has a new section for widgets. Follow this link to open the Widgets section. Listed widgets may be installed so that they may be displayed in the Widgets interface.

Microsoft releases Windows 11 Build 23430
As well as a new Windows 11 build for Insiders on the bleeding edge Canary Channel, Microsoft has rolled out a new flight for testers on the Dev Channel.
New features here include a change to how urgent and important notifications are handled when 'do not disturb' is turned on -- users will have the option to click a 'view notification' button.


