
People first, technology second -- Why SaaS developers should embrace human-centered design
The recent fascination with AI, fueled by the release of ChatGPT and Google and Bing trying to catch up with their own language models, has SaaS developers and designers intrigued by the possibilities of what they can do with the burgeoning technology.
But the AI explosion in progress underscores a question that must be asked about any innovation: What place do humans hold in the development of technology intended to benefit them?

Kodi 20.1 'Nexus' is finally here -- Download it NOW!
Two months ago, the stable version of Kodi 20 'Nexus' arrived, bringing with it a wealth of new features to the hugely popular home theater software, including support for multiple instances of binary add-ons, AV1 Video support, and a massive rework of the subtitle system.
Today, the Kodi Foundation releases a new version, and Kodi 20.1 is well worth installing it as comes with an assortment of important bug fixes and some backports.

How software pricing strategy is evolving [Q&A]
Buying software used to be relatively simple. You either paid a one-off fee, or an ongoing license, or sometimes a combination of both.
With the advent of cloud and SaaS, however, things have become rather more complicated. Usage based pricing is more common, plus in a difficult economic climate there's a spotlight on software costs.
Sorry, but it looks as though Microsoft is keeping the Windows 11 taskbar fixed at the bottom of the screen
A few days ago, news started to spread that Microsoft appeared to be working on a much-requested feature for Windows 11 -- the ability to move the taskbar to somewhere other than the bottom of the screen.
But it seems that this is not actually the case. The very same source that served as a catalyst for excitement has now poured water on the flames of anticipation. What appears to have happened is that Microsoft accidentally left code in place in a recent build of Windows 11 that made the taskbar movable; there remains no evidence that the option to reposition the taskbar will ever arrive.

Microsoft releases new Canary build of Windows 11... and it might be the most boring yet!
A few days ago, Microsoft announced sweeping changes to the Windows Insider program, introducing the new Canary channel for those wanting to live right on the cutting edge.
Now the company has pushed a new build to this channel in the form of Cumulative Update Build 25314.1010. Also known at the KB5025135 update, this build is possibly the least exciting Windows 11 release yet -- but that does not mean that it isn't important.

Microsoft is about to launch multi-modal GPT-4 complete with video
Microsoft has revealed that the company is about to launch GPT-4 and this time it is about more than just text and chat. The next iteration of the AI technology is described as multi-modal, meaning there is support for much more -- including video.
The news came at an event in Germany called KI im Fokus (AI in Focus) on Thursday. Here, Microsoft Germany's CTO and Lead Data & AI STU, Andreas Braun, said: "We will introduce GPT-4 next week, there we will have multimodal models that will offer completely different possibilities -- for example videos".

New pricing for Twitter API access is astonishingly expensive
When Twitter announced that it was ending free access to its API, it said nothing about what the new pricing structure would look like. But now the company has finally revealed the price tags for different tiers of access -- and it is worse than anyone predicted.
In all, there are now three tiers to choose from, each allowing for different numbers of tweets and giving varying levels of access. The cheapest, the Small Package tier, costs a staggering $42,000 per month (or just over $0.5 million per year), while the Large Package costs an eye-watering $210,000 per month (or a shade over $2.5 million per year).

Google kills off the Chrome Cleanup Tool for Windows
With the release of Chrome 111, Google is waving goodbye to the Chrome Cleanup Tool that has been available for a number of years.
After 8 years of service, Google has decided the Chrome Cleanup Tool -- which, the company explains, helps users to "recover from unexpected settings changes, and to detect and remove unwanted software" -- is simply no longer needed.

Get 'Modern API Development with Spring and Spring Boot' (worth $33.99) FREE for a limited time
The philosophy of API development has evolved over the years to serve the modern needs of enterprise architecture.
Developers need to know how to adapt to these modern API design principles. Apps are now developed with APIs that enable ease of integration for the cloud environment and distributed systems. With this Spring book, you'll discover various kinds of production-ready API implementation using REST APIs and explore async using the reactive paradigm, gRPC, and GraphQL.

Microsoft may soon let you move the Window 11 taskbar
With Windows 11, Microsoft made lots of questionable design, UI and UX choices, but one of the most baffling was the decision to make the taskbar immovable.
If you're one of the many people who would like to untether the taskbar from the bottom of the screen, there could be some good news. In recent preview builds of Windows 11, the taskbar can be moved to the top of the screen in a sign that the company may be ready to back-peddle on its stance that the taskbar has a fixed location.

Applying the Biden-Harris Administration's National Cybersecurity Strategy to your organization in five steps
As cyber threats continue to evolve and grow, it is increasingly clear that a coordinated and comprehensive approach to cybersecurity is necessary. Governments around the world have recognized the need for national cybersecurity strategies to protect their citizens, businesses, and critical infrastructure. In this article, we will explore the importance of a national cybersecurity strategy from the perspective of a cyber threat intelligence team.
The increasing frequency and severity of cyberattacks have highlighted the importance of having a comprehensive national cybersecurity strategy. Cyberattacks can result in the loss of sensitive data, disruption of critical services, financial losses, reputational damage, and even loss of life. A national cybersecurity strategy is essential to protect against cyber threats, safeguard national security, and maintain economic stability. It provides a framework for coordinating and prioritizing efforts to address cyber threats, promotes information sharing and collaboration, and enables rapid response to incidents.

Best Windows apps this week
Five-hundred-and-thirty-three in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft released the first build to the newly created Windows 11 Canary Insider channel. Earlier this week, Microsoft announced the creation of the new channel, which takes over the Dev channel's far-in-the-future developments.

The rise of hardware-based security and why it matters [Q&A]
Cybersecurity is usually viewed as something to be addressed via software. In recent years though we've seen a hardware element start to creep in -- Windows 11's requirement for TPM capability for example.
Can we expect to see more hardware-based security measures? And what benefits do these offer? We spoke to Ed Maste, senior director of technology at the FreeBSD Foundation (the non-profit organization supporting the open source FreeBSD operating system) to find out.
GitHub is introducing mandatory 2FA for all developers in new security drive
Starting next week, GitHub is going to require active developers on the site to enable at least one form of two-factor authentication (2FA). The security initiative will start with specially selected groups of developers and administrators on March 13.
Until the end of the year, GitHub will begin notifying those who have been selected of the 2FA requirement. As the year progresses, more and more users will be obliged to enable two-factor authentication.
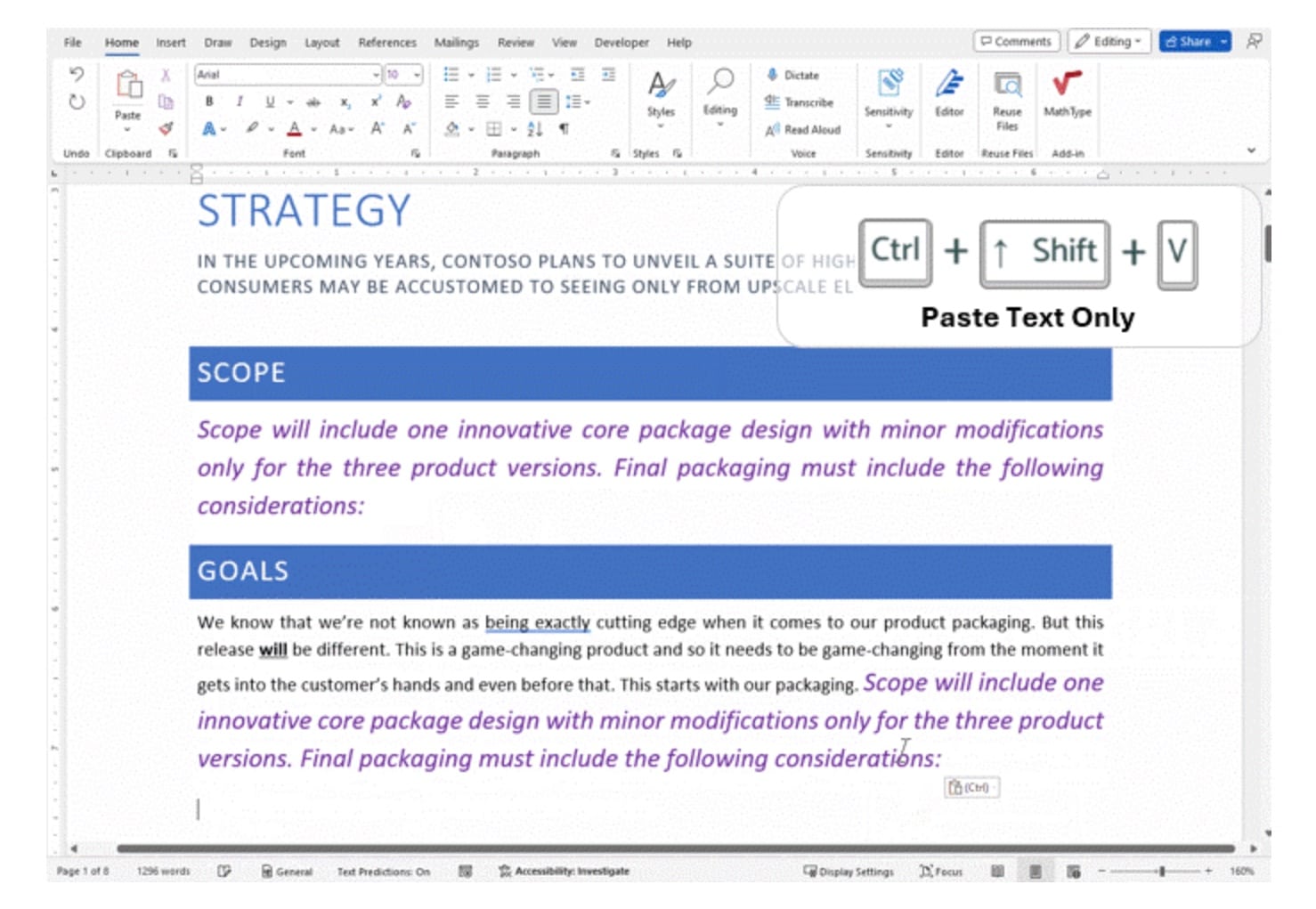
Microsoft is adding a new keyboard shortcut to paste unformatted text in Word
Having very recently introduced a new Paste As Plain Text module to PowerToys, Microsoft is now bringing the same option to Word.
Following the lead of many other applications, Microsoft's word processor is gaining a new keyboard shortcut that can be used to paste text and strip it of any formatting. Microsoft is calling the feature Paste Text Only, and it is available in both Word for Windows and Word for Mac.



