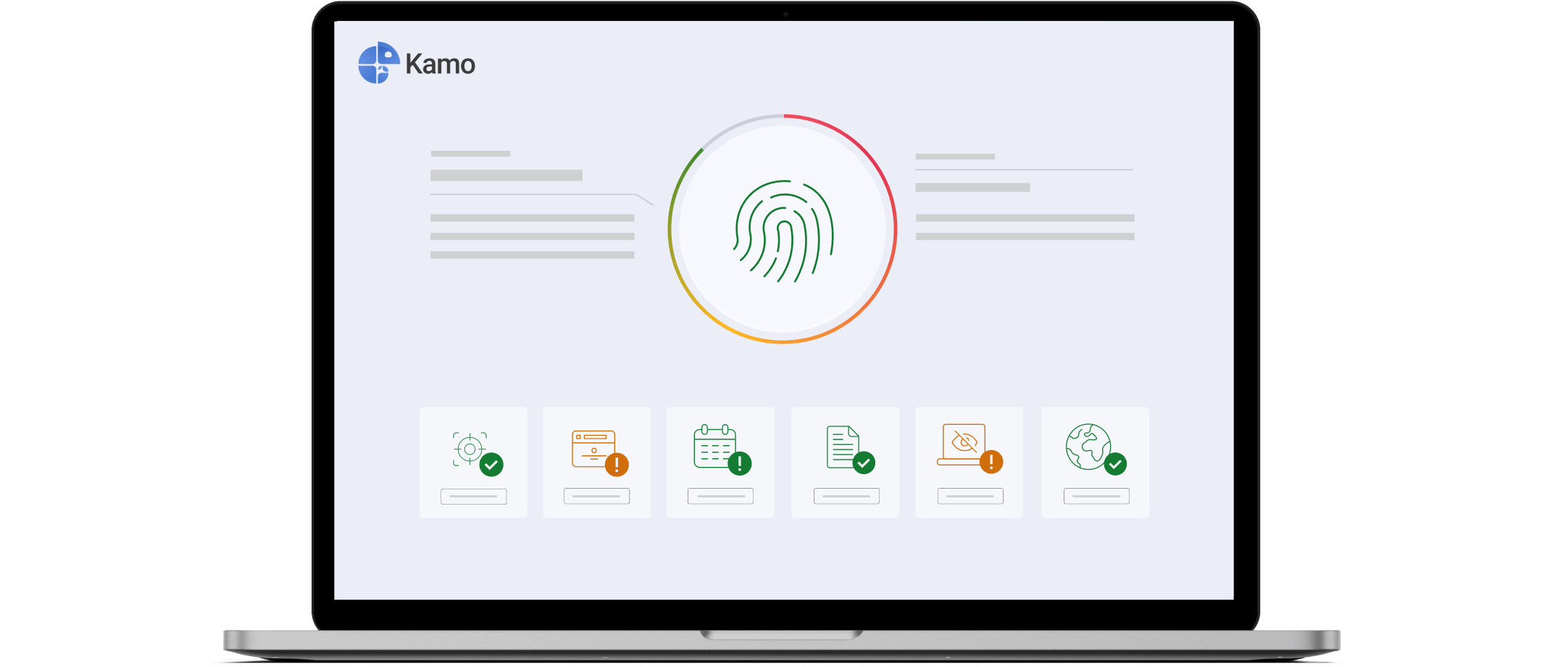
CCleaner boosts the speed of its Kamo VPN by up to 35%
CCleaner has added the WireGuard protocol to the Private Connection mode of its antitrack and online privacy tool, Kamo.
By replacing OpenVPN, the previous default protocol, the company says Kamo users will enjoy improved security, speed and connection reliability.
Best Windows apps this week
Five-hundred-and-thirty-two in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft released the second Moments update as a preview update for Windows 11 earlier this week. It brings tabs to Notepad, third-party widgets, new apps, and AI-powered Bing Chat to the operating system. Users who have interface modification tools installed should avoid the update for now, as it may result in startup issues.

Generative AI -- what it is and why there's no rush to adopt it [Q&A]
Generative AI has been getting attention recently for its novelty, unique applications and potential impact on the business world.
But, like any new invention, there's some confusion around what it actually is and what it can do. We spoke to Scott Varho, chief evangelist of 3Pillar Global, who argues that companies shouldn't be rushing to adopt generative AI without considering their needs and potential value.

New Radiant Logic solution improves identity decision making
Enterprises need real-time access to lots of data, but it's important that access to that data is properly controlled.
Radiant Logic is launching a new data intelligence offering that offers identity observability and visualization capabilities, all built on an extensible API-layer and available as a SaaS offering.
Windows 12: What we know and don't know about it, and what could happen
Is Microsoft working on the next version of Windows? Will it be Windows 12? If the answer is yes, how will it look like and differ from Windows 11?
There is quite a bit of uncertainty regarding Windows right now. Microsoft ended support for the popular Windows 7 and the not-so popular Windows 8 operating systems in January 2023, and in less than 3 years, Windows 10 is added to the list of operating systems that are no longer supported. This would leave Windows 11 as the sole version of Windows that is available and supported officially.
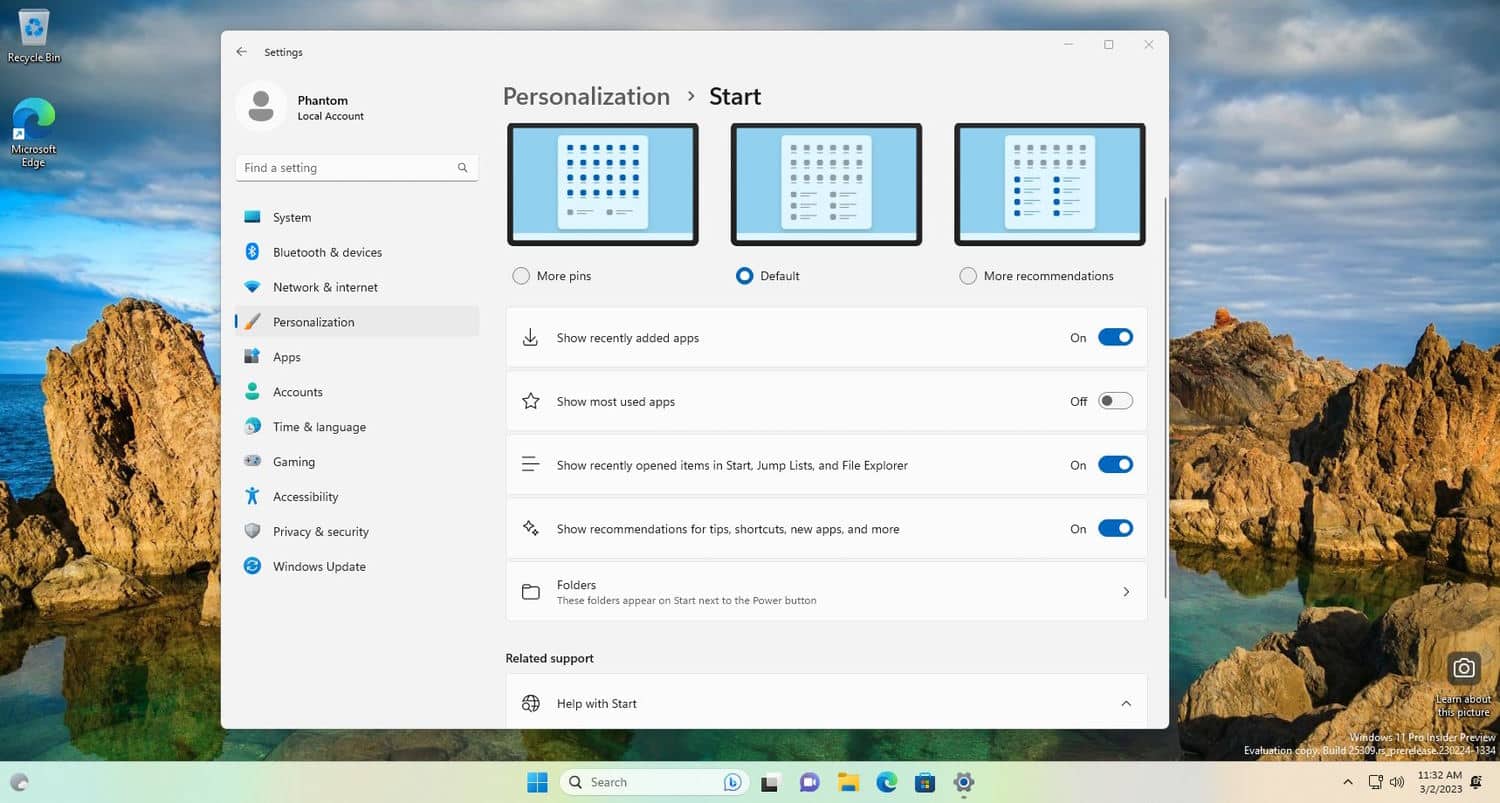
Microsoft finally appears to be listening! Windows 11 users can disable Start menu recommendations
There has been a lot of controversy surrounding Windows 11, but one of the most contentious issues with the operating system has been the recommended content Microsoft pushes on users in various ways.
One medium through which these recommendations -- everything from apps that may (but probably won't) be of interest, to tips and advice -- are delivered is via the Start menu. Hidden away in the latest build of Windows 11, however, is an official toggle that makes it possible to turn off these ads... er, recommendations... once and for all.

Microsoft releases emergency patches for Intel CPU vulnerabilities in Windows 10, Windows 11 and Windows Server
Following a security disclosure by Intel way back in June of last year about vulnerabilities affecting its processors, Microsoft has issued a series of out-of-band fixes for the flaws.
In all, Intel revealed details of four data-exposing chip flaws (CVE-2022-21123, CVE-2022-21125, CVE-2022-21127 and CVE-2022-21166) described collectively as Processor MMIO (memory-mapped I/O) Stale Data Vulnerabilities. Now Microsoft has released a total of six emergency updates for various versions of Windows 10, Windows 11 and Windows Server.
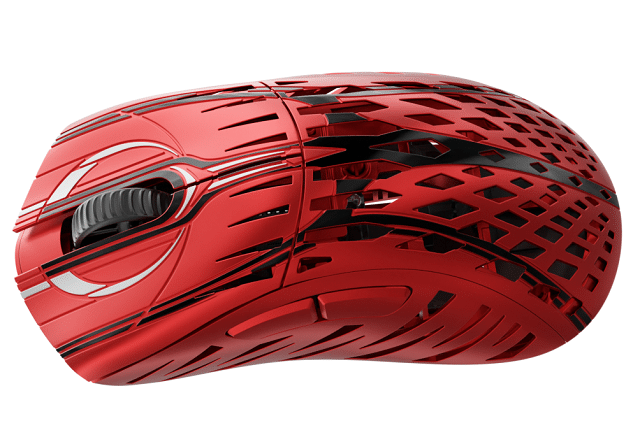
Pwnage launches Stormbreaker magnesium alloy wireless gaming mouse
When you think of gaming mice, your mind probably goes to brands such as Logitech G or HyperX, am I right? That is totally understandable. However, there are many other companies manufacturing these types of mice nowadays. Case in point, today, Pwnage launches a gaming mouse called "Stormbreaker."
What makes this mouse so special? Well, besides its beautiful magnesium alloy body, Stormbreaker features a 2,000Hz polling rate, 120 hour battery life, movable sensor, USB-C charging, and a unique pyramid USB receiver.

Microsoft releases Windows 11 Build 25309 with an enhanced volume mixer
A couple of days ago, Microsoft began to rollout a big update for Windows 11. The Moment 2 update introduces a number of major features, including AI-powered Bing preview on the taskbar.
Of course, development on future updates for Windows 11 continues uninterrupted and today the company releases a new build for Insiders in the Dev Channel.

Get 'Python Network Programming Techniques' (worth $37.99) for FREE
Gone are the days of manually logging on to different devices to type the same configuration commands over and over again. With this book, you'll find out how you can automate your network infrastructure using Python.
You'll get started on your network automation journey with a hands-on introduction to the network programming basics to complement your infrastructure knowledge. You'll learn how to tackle different aspects of network automation using Python programming and a variety of open source libraries.

The KM comeback: How IT leaders can optimize a knowledge-driven business future
Knowledge management (KM) -- a concept first established in the 1980s -- is now witnessing both a rapid comeback and a transformation. A perfect storm of factors is contributing to these trends, including the shift to remote and hybrid work; dramatic changes in customer and employee perceptions; "The Great Resignation" that took place in 2021 and the wave of tech company layoffs that followed it; and most notably, the continued explosion in the amount of unstructured content -- scattered across a growing number of siloed applications.
Knowledge Management has made its way back on the CIO agenda as one of the most important initiatives for business resiliency in the years ahead. And, now IT leaders assess how best to implement technologies that discover, cultivate and protect the collective knowledge of an organization and seamlessly disseminate it to employees where and when they need it. This new version of KM promises that the latest technology can help tame content chaos; however, doing that successfully means addressing a number of challenges.

What could the future hold for drivers in the Metaverse?
While the Metaverse is still somewhat in its infancy, it has tech-heads all over the globe coming up with all sorts of theories and concepts for the future. The world of augmented virtual reality is currently so undefined that we’re seeing governments like Dubai building strategies to create 40,000 jobs in the metaverse and bring $4 billion to their economy.
There have been all sorts of talk surrounding personal avatars and property in this futuristic landscape, but what about vehicles? Could we see the potential for people to buy or rent vehicles in this virtual reality?

Scammers turn to AI to improve their campaigns
The latest quarterly Consumer Cyber Safety Pulse Report from Norton looks at how cybercriminals can use artificial intelligence to create more realistic and sophisticated threats.
Tools like ChatGPT have captured people's attention recently and it seems cybercriminals have noticed them too. Its impressive ability to generate human-like text that adapts to different languages and audiences also makes it great for generating malicious threats.
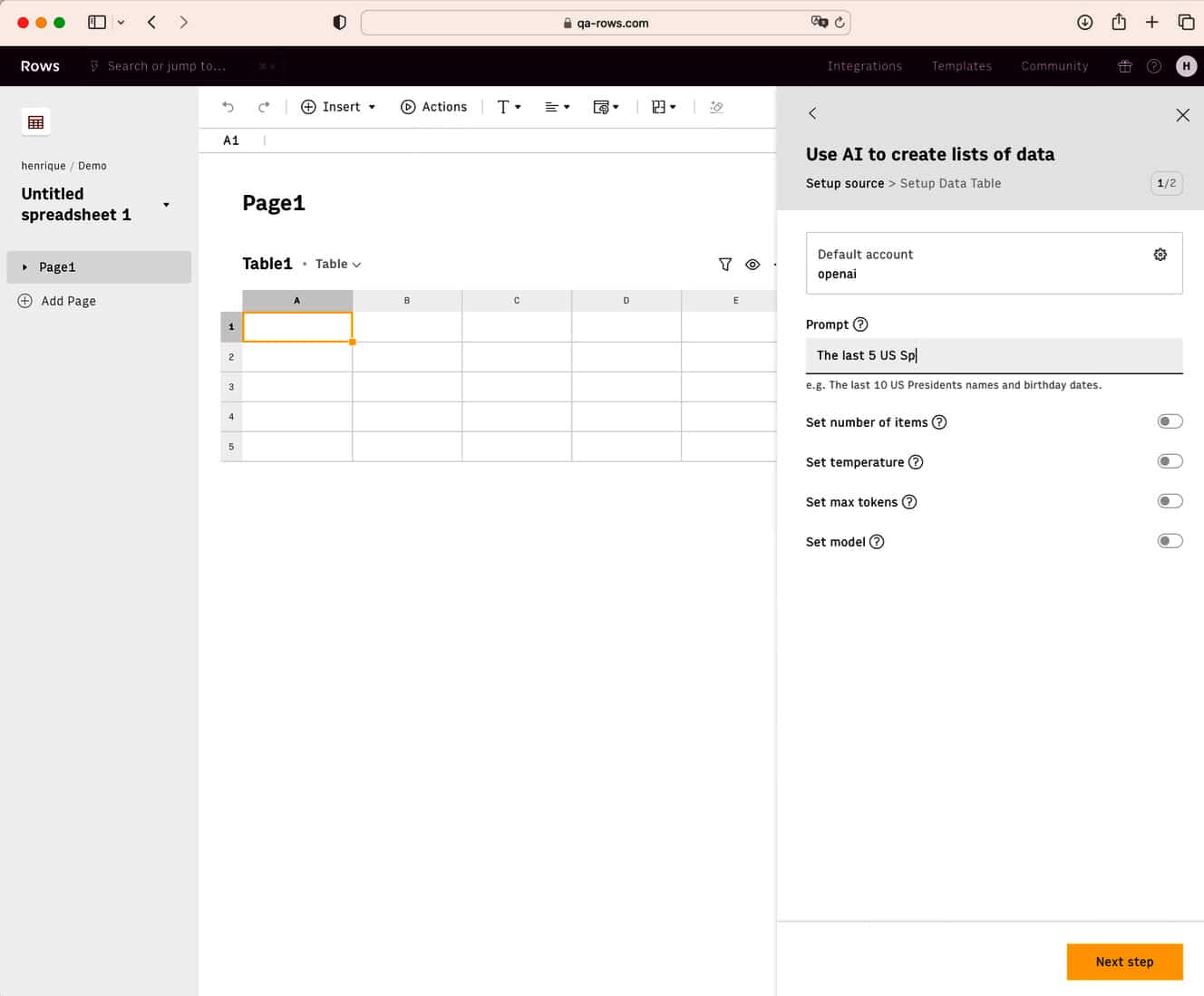
Rows brings the power of GPT-3 AI to spreadsheets
Following the massive success of OpenAI’s ChatGPT, AI is being added to a growing number of tools and services. A couple of days ago, Microsoft released Moment 2 for Windows 11, adding a number of new features to the new OS, including bringing its AI-powered Bing preview to the taskbar.
Today, Berlin-based spreadsheet company Rows announces a new version of its online worksheet tool which comes with GPT-3 AI capabilities built in, as well as third-party integrations, giving users access to over one billion functions.

Smooth integration is a challenge for machine learning professionals
A new survey of 200 US-based machine learning decision makers looks at the trends, opportunities and challenges in machine learning and MLOps (machine learning operations).
The study from ClearML finds that for 41 percent, the biggest challenge of their MLOps platform, tools, or stack, is friction in using tools with other technology. While 22 percent cite vendor lock -- difficulty switching to a different provider without significant costs, time, or disruptions -- as the biggest challenge.



