
Want NFL Sunday Ticket without DirecTV? Amazon Prime may give you that chance
We found out a while back that the NFL will not be renewing its DirecTV Sunday Ticket deal, after a years-long run. The top-viewed sports league has decided to move on and no longer require its viewers to get a satellite dish installed just to watch their favorite team in action. Instead, the NFL is moving on to something that it hopes will attract an even broader viewership.
For a while, it seemed that Apple TV+ was the lead streaming candidate, but a new survey indicates that is no longer the case. According to The Streamable, Apple TV+ actually trails its major competitors in terms of viewer choice.
Cloud security is complex -- but most vulnerabilities fall into three key categories
With most enterprises leveraging at least one type of cloud deployment today, the question arises: is the cloud more or less secure than on-premise solutions?
The reality is that for on prem or even private cloud environments, the approach to security largely relies on a barrier defense. When organizations are compromised within this barrier, it can basically become open season for malicious actors, which we’ve seen in marquee incidents such as the Target data breach, the Home Depot hack in 2014, or the recent Uber breach, which exploited an unpatched security vulnerability.

How technology investment could be the savior for businesses
It’s hard to hide from the doom and gloom messages that are encircling the world around economic uncertainty but despite this, business and technology leaders still have a job to do -- and with 2022 coming to a close, 2023 planning must be approached with a growth mindset.
As much as it may seem counterintuitive to spend in times of financial uncertainty, those businesses that make rash decisions to tighten the purse strings and reduce technology investment, may just be the ones that end up being left behind.
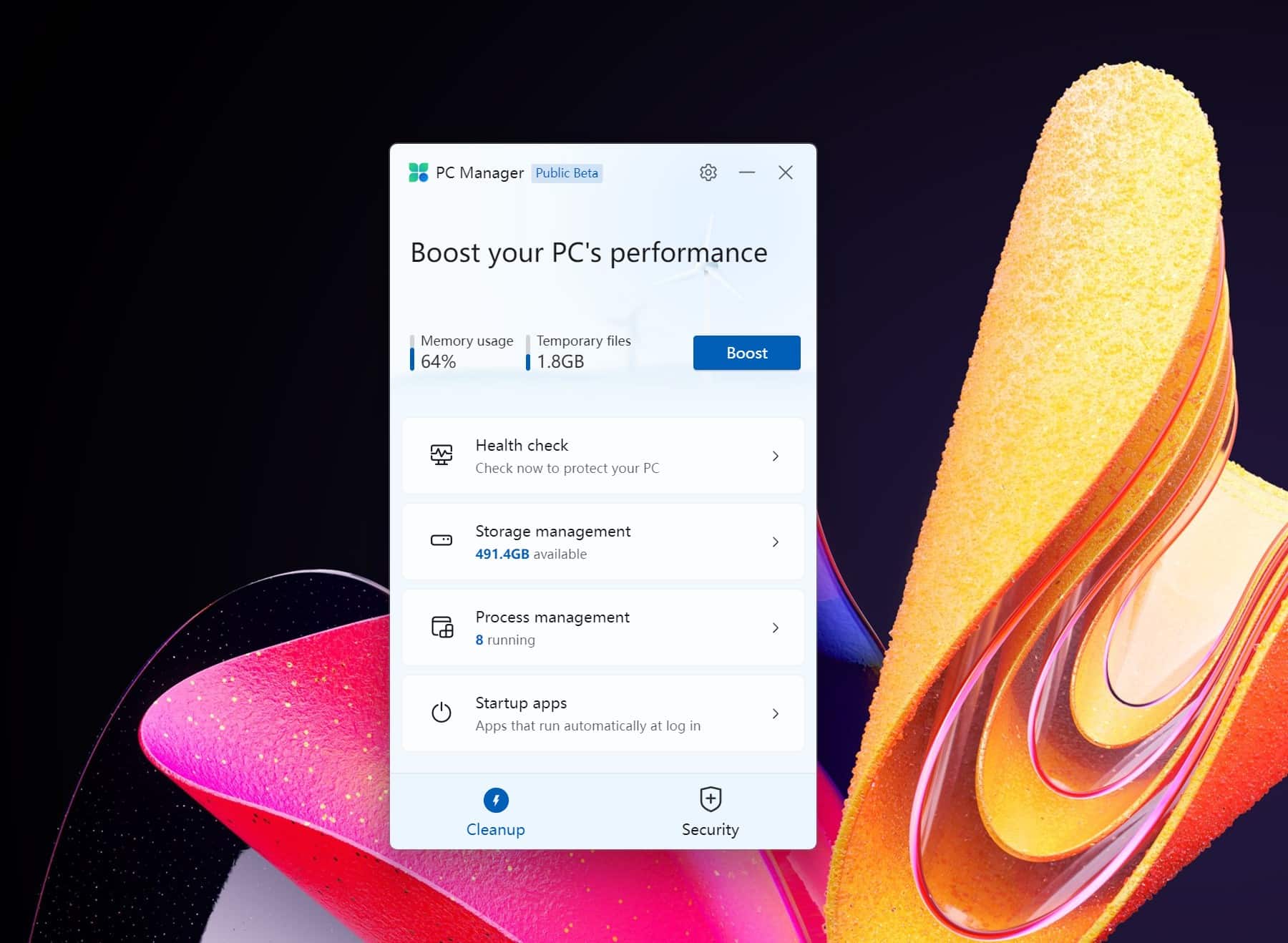
Microsoft PC Manager is a new Windows optimization app currently available in beta
Tools that claim to speed up Windows used to be hard to avoid. Now they are far less common, but Microsoft looks ready to get a piece of the action with a new system cleanup, optimization and security app called PC Manager.
Available in public beta, Microsoft PC Manager has been compared to CCleaner. The company is currently testing the app with the Chinese market, but there is nothing to stop you from downloading it and trying it out for yourself (it's available in English). A word of warning, however -- you will be pestered to change your default web browser to Microsoft Edge.

Monoprice launches Monolith MTM 100 Watt Bluetooth aptX HD powered speakers
Nowadays, our computers often serve as our centralized media centers. We use laptops and desktops to both watch videos and listen to music. Long gone are the days of having big stereo receivers paired with independent media devices such as CD and DVD players. Streaming is superior.
Unfortunately, many consumers rely on the terrible speakers that are integrated into their laptops or the ones that came with their desktop. These people are missing out on what is truly possible from computer audio. By upgrading to higher quality speakers, a whole new world of audio can be experienced.

Resiliency through visibility: Why supply chain disruption needs to be tackled by a holistic approach
A host of 'black swan' events have hit companies’ supply chains over the past two years, straining existing processes and structures. Beyond the obvious impact of COVID-19, the Suez Canal blockage, chip shortages, and Brexit -- now organizations are trying to mitigate disruptions from the war in Ukraine and rising inflation.
The end result: a stronger need than ever before to enhance levels of communication, collaboration and joint decision making across the supply chain, to reduce risk in the face of challenges still to come.

You need much longer to test the new Windows 11 2022 Update (22H2) -- this secret trick will let you massively extend the rollback time
Microsoft recently released the Windows 11 2022 Update (22H2) followed by a 'moment' update which introduced new features to the OS, including tabs in File Explorer.
If you’ve been reading our coverage of the problems that users have found with the Windows 11 2022 Update you might be concerned about installing it, but don’t worry you can roll back the operating system to your previous build. There’s just one problem -- Microsoft only gives you 10 days to do this, which is hardly any time at all. We think you need longer, much longer, so we’ll show you how to extend this allowance to 60 days.
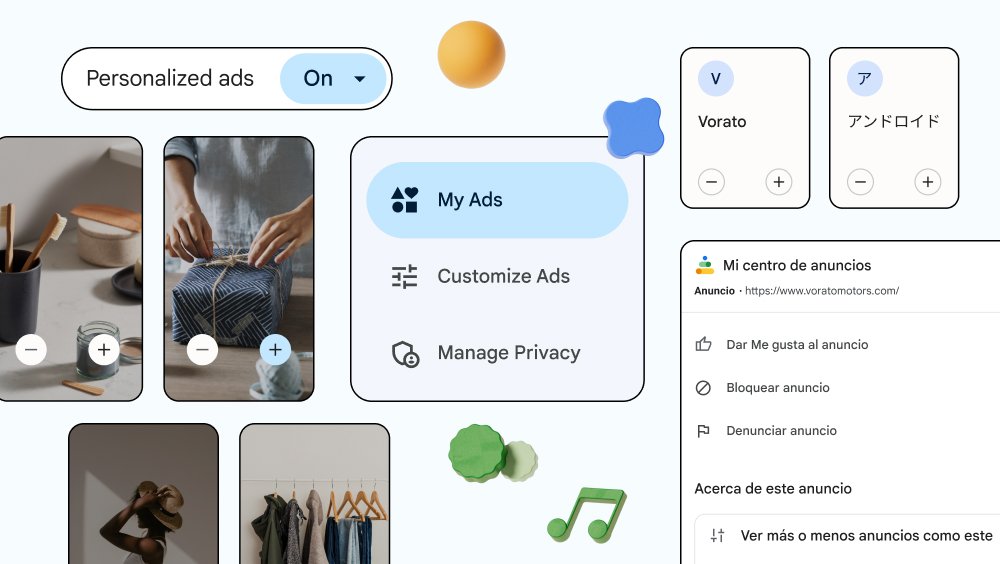
Google launches My Ad Center to give you more control over the ads you see
Ads are now part and parcel of using the internet and many apps, and much of what you see is because of Google. It is going to be a long time before Google changes its business model and is no longer reliant on showing you ads, but the company is aware of the annoyance people experience when they see advertising that is is completely inappropriate or touches on sensitive topics.
As such, Google has announced My Ad Center, a portal through which it is possible to gain more control over your ad experience. What this means in practice is that you will be able to do things such as choose whether or not you'd like to see tailored ads, control what sort of information Google is able to use to personalise your ads, and even opt out of seeing ads for certain topics.

Google open source project aims to boost supply chain security
Software supply chain security is at the top of a lot of agendas at the moment, more so since the Log4j vulnerability was discovered and since the US Executive Order on cybersecurity.
Google is seeking contributors to a new open source project called GUAC (Graph for Understanding Artifact Composition), which although in its early stages yet is poised to change how the industry understands software supply chains.
Best Windows apps this week
Five-hundred-and-thirteen in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Lots of important updates this week. Microsoft released the Windows 10 2022 Update, without mentioning its changes, and the first Moments update for the Windows 11 2022 Update. The latter introduced tabs in File Explorer and several other improvements.

Blame bad bots for online fraud sweeping the United Kingdom
Online fraud is becoming a scourge across the United Kingdom, and in the past year alone we’ve watched police tackle a record breaking number of scams.
One of the most dangerous attacks used by fraudsters is Account Takeover (ATO), whereby cybercriminals take ownership of online accounts by abusing stolen passwords and usernames, often accessed on the Dark Web. A Freedom of Information (FOI) request earlier this year revealed that ATO is the most common form of online fraud in the UK and new data from the 2022 Imperva Bad Bot Report shows ATO attacks rose a staggering 148 percent in 2021 alone.

CNAPP -- what is it and why should you care about it? [Q&A]
The IT world is littered with acronyms and one of the latest is CNAPP, standing for Cloud Native Application Protection Platform. If you haven't heard about it already you almost certainly will do soon.
We spoke to Stanimir Markov, CEO at Runecast, about CNAPP, what it is and how it can benefit modern enterprises and their cloud environments.

Google warns YouTube Premium Family subscribers of massive price rise
Google has started the process of informing YouTube Premium subscribers about an impending price rise for its Family plan. The hike is a significant one, with subscribers in the US looking at a $5 jump from $17.99 per month to $22.99.
The new pricing takes immediate effect for new subscribers, but existing users have at least 30 days from the date of receiving the email from Google. For those who signed up for YouTube Red when it existed, there is a brief stay of execution.

Cloud and hybrid working: The investment priorities for enterprises
Over the last two years, IT teams have come under immense pressure, having to quickly rethink their architecture to support home working, and best prepare for a hybrid-working model in the future. As a result, IT spending has never been higher with a total projected spend of $4.4 trillion USD in 2022, an increase of 4 percent on spend in 2021.
Widely accepted hybrid working practices and a reduced intensity of digital transformation projects have been reflected in IT investment decisions. According to A10 Networks’ recent Enterprise Perspectives research, investment in the cloud is a standout priority. This comes in addition to a growing focus on strengthening cybersecurity strategies with the policies and practices that must accompany the shift to an expanded office network/hybrid working environment.

Get 'Learning DevOps -- Second Edition' ($37.99 value) FREE for a limited time
In the implementation of DevOps processes, the choice of tools is crucial to the sustainability of projects and collaboration between developers and ops.
Learning DevOps -- Second Edition presents the different patterns and tools for provisioning and configuring an infrastructure in the cloud, covering mostly open source tools with a large community contribution, such as Terraform, Ansible, and Packer, which are assets for automation.


