Beyond detecting bots -- in the age of AI, it's all about intent

For the past two decades, cybersecurity teams have been laser focused on identifying ‘what’s bot -- and what’s not’. Over the past couple of years, this focus has shifted slightly, with security teams dedicating most of their attention to the most sophisticated bots.
New developments in AI over the past year have added a new level of complexity, with the emergence of beneficial business bots, like sophisticated AI agents, complicating what was once a binary task of differentiating bot from human.
Big tech's privacy paradox: Why regulatory alignment is now a technical imperative

The integration of Meta AI into WhatsApp represents a fascinating case study in how technical capabilities can undermine strategic positioning.
WhatsApp’s success was built on a simple technical promise -- end-to-end encryption that creates a secure communication channel. Yet, the introduction of an AI chatbot that explicitly warns users against sharing sensitive information exposes a fundamental architectural contradiction that has broader implications for the tech industry.
New AI platform knows when you're lying, tired, or overwhelmed

Neurologyca has launched a new multi-modal AI platform called Kopernica that introduces emotional context to machine intelligence.
Described by the company as a “first-of-its-kind,” Kopernica uses real-time data from facial expressions, vocal tones, and behavioral signals to detect and interpret human emotions, cognitive states, and potential health risks, such as strokes. The platform is being positioned as a foundational layer for emotionally aware AI systems.
Microsoft adds new AI Actions entry to the Windows 11 context menu
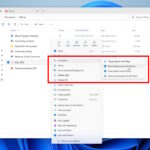
Microsoft, Google, Apple, et al -- they are all at it. There is not a big-name tech firm in existence that is not deeply invested in artificial intelligence, and for end users this means having AI tools dangled in front of them at any given opportunity.
Windows 11 has already seen more than its fair share of AI, and this is not something that shows any signs of changing.
YouTube is turning to AI to hit you with ads at the most annoying times

Unless you can count yourself among those who have a premium subscription, using YouTube means having to endure ads. This is annoying, but it could be getting a whole lot worse.
And things are getting worse because of artificial intelligence. Google has announced Peak Points, a Gemini ai-powered feature that gives advertisers way to hit you with ads when you are most engaged with a video.
The modern workplace has a burnout problem: Is AI the remedy?

Burnout has long been an issue in the workplace, made worse by today’s “always on” culture. In fact, data shows that 77 percent of employees report feeling burned out.
If left unchecked, not only will it lead to health consequences, but also negatively impacts business outcomes. For instance, burnout often worsens employee performance and creates talent retention challenges if morale becomes too negative.
Microsoft continues to foist Copilot on Windows 11 users by adding it to the context menu

Loved, loathed, feared, viewed with suspicion -- all valid reactions to the existence of Microsoft's Copilot. The AI-powered assistant has proved hard to avoid thanks to the company's crazed promotion of its latest baby, and now things are being ratcheted up a notch.
Microsoft latest attempt to get people to use the Copilot app is to add a new shortcut to the context menu. Right click on a file in Windows 11 and you'll be presented with an Ask Copilot link so you can subject your documents to artificial intelligence.
Google Maps can now use your screenshots to help you plan trips thanks to Gemini AI
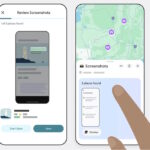
Screenshotting stuff can seem like a great way to remember something for later, but captures soon get lost and forgotten. Google is looking to change this by bringing new Gemini-powered features to Google Maps.
The company thinks that it can help you to make sense of the “travel blogs, news articles or social media posts” you’ve screengrabbed while researching a trip. Turning to AI to make sense of a heap of images is Google’s solution. Here’s how it can help you.
The big value of AI? Stopping humans from becoming confused robots

By now we’ve all been beaten around the head with the message that AI is the new rock star. It writes poems, paints like Picasso, and can probably tell you what you had for breakfast three Tuesdays ago. But really, if all we’re doing with AI is making it admire itself in a digital mirror, we're doing it wrong. AI is capable of all sorts of technological wizardry, but the most important thing it should be doing is keeping us from having a full-blown existential crisis trying to keep up!
These days, change doesn't politely knock -- it barges in like a caffeinated squirrel. A recent Nexthink report found that 94 percent of companies think their survival depends on AI in the next three years. But here's the kicker: less than half (47 percent) of employees have the skills to actually get to grips with AI. For some, it’s going to be like trying to teach a goldfish quantum physics. The divide between where they are now and where they need to be? It's a gap, a chasm, a digital Grand Canyon! But for the brave few who are willing to build a bridge for them, it’s a massive opportunity.
Microsoft now has AI agents that can change Windows 11 settings -- should we be delighted or terrified?
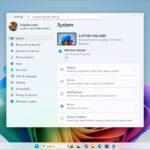
Artificial intelligence is now all but unavoidable, and Microsoft is taking every opportunity to crowbar more AI features into Windows 11. Copilot+ PCs are a big part of the company’s AI vision and now powerful new AI agents have been unveiled.
Described as being part of a “new generation of Windows experiences”, Microsoft has revealed new agents that use on-device AI to interpret natural language input to help a user find and change system settings. What could possibly go wrong?
Someone tried to activate every version of Microsoft Windows using ChatGPT -- Here's what happened
You’ve possibly seen people online try to use ChatGPT to generate valid product keys for paid software, including different versions of Microsoft Windows.
YouTuber Gameboy Hub set out to test how successful ChatGPT is at generating, or sourcing, product keys to activate various versions of Microsoft Windows -- starting from Windows 95 and working up to Windows 7 (from where, in theory, it could be possible to upgrade to Windows 10 and Windows 11).
Microsoft is updating the Copilot app with an introductory tutorial for newbies

Powerful new tools are only useful if people know what they can do and how to get them to do those things. For what feels like an eternity, Microsoft has been pushing Copilot as the greatest addition to Windows since... well, since Cortana it probably thinks.
For tech heads who have kept up with the latest news and developments, it’s easy to know what Copilot is, what it is about, and what it can do. But Microsoft realizes that not every Windows user is a tech head and is adding a guided tour to the app.
Microsoft has finally realized that not everyone cares about Copilot

Despite making claims to the contrary, Microsoft is not really thought of as being a company that takes much notice of user opinion. All too often it seems that incredibly unpopular options, features and changes are introduced with little regard for what users actually want.
But, to buck the trend, Microsoft has apparently been listening to feedback from people who are unhappy about the encroachment of Copilot into... well, pretty much everything, really. The decision to include a physical Copilot key on keyboards has been one such unpopular move, and the reaction from Windows 11 users has forced Microsoft’s hand.
Google reveals ZAPBench to predict brain activity in zebrafish and unlock new AI-powered neuroscience research

If we are lucky, Artificial intelligence might one day help scientists understand the human brain the same way language models predict the next word in a sentence. And now, that future is closer to becoming reality thanks to a new project from Google Research, Harvard University, and HHMI Janelia. You see, these teams have introduced the Zebrafish Activity Prediction Benchmark, better known as “ZAPBench,” which could help researchers create more accurate models for predicting brain activity.
ZAPBench isn’t just another dataset, folks. Actually, this new tool is based on two hours of brain recordings from larval zebrafish, capturing how roughly 70,000 neurons fired in response to different virtual reality scenarios. These tiny fish were shown various environmental changes, including shifting light patterns and moving water currents, while researchers recorded brain activity at an impressively detailed scale.
Making AI agents 'smarter' with connected data

The latest buzzy concept in the world of AI is now transcending its initial hype. Advances in Agentic AI are accelerating the development of autonomous business systems, building upon progress in machine learning. Acting as an independent ‘agent’, the technology can make informed decisions based on the multimodal data and algorithms they’re built on and then ‘learn’ from its experiences.
But even more excitingly, Agentic AI aims to execute tasks independently. It’s this ability to adapt, plan, and execute complex tasks without direct human intervention is what differentiates Agentic AI from its predecessors.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.