
Microsoft makes securing files faster with hardware-accelerated BitLocker
If you have use BitLocker to secure files within Windows 11, you will almost certainly have noticed something of a performance hit. Microsoft is not unaware of this, and is taking steps to help improve things.
The company is rolling out hardware-accelerated BitLocker, which should help to provide a speed boost on systems with NVMe drives. The new approach helps to avoid bottlenecks which can massively impact on performance.

Practical quantum, encryption risk and government regulation -- quantum computing predictions for 2026
It’s the time of year again when industry executives like to peer into their crystal balls and try to predict what the future might hold.
We’ll kick off this year’s roundups with a look at quantum, something which has been hovering on the edge a major breakthrough for a few years now but, so far, has always seemed to be just out of reach from a commercial perspective. Is that set to change in 2026?

Why concentrating data in AI models demands greater vigilance [Q&A]
Data that was once scattered across sprawling systems and silos -- providing natural obstacles to attackers -- is now concentrated and highly portable within AI models. This fundamental shift redefines the challenge of digital security.
We spoke to Dr. Luigi Caramico, CTO and co-founder of DataKrypto, to discuss how organizations can repond to this challenge.
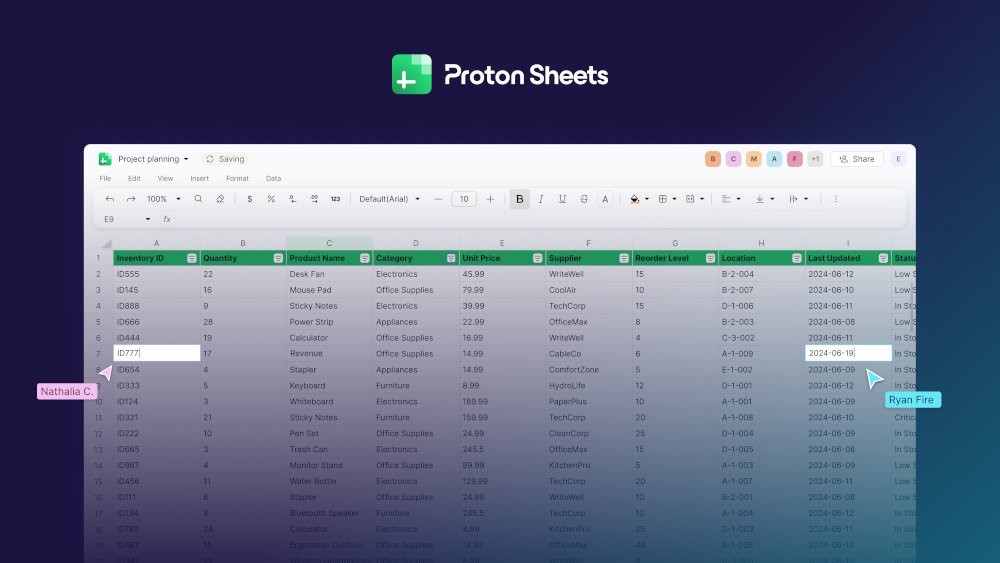
Proton launches end-to-end encrypted spreadsheets for secure collaboration
Spreadsheets are essential to modern businesses, used to plan budgets, manage inventory, supervise members, and organize proprietary data. But organizations are becoming increasingly concerned that these tools can leave their internal data exposed to surveillance, tracking, and AI training.
This why Proton is launching Proton Sheets, an easy-to-use private spreadsheet that lets teams collaborate while keeping control of their data.

Tor is switching to the Counter Galois Onion encryption algorithm
Tor (The Onion Router) is switching its encryption algorithm to help boost security and privacy. The change is being introduced to protect users against certain types of attack, and sees the browser adopting a new “research-backed new design” called Counter Galois Onion.
The algorithm that is being updated is the one used to encrypt user data as it travel across a circuit via multiple relays. In making the switch, Tor concedes that its previous encryption design “looks funny”, hence the need to replace it.

Cybercriminals turn to stealth to bypass malware detection
A new report reveals a 40 percent (quarter-over-quarter) increase in evasive, advanced malware. The data highlights encrypted channels as adversaries' favored attack vector using Transport Layer Security (TLS), the encryption protocol behind most secure web traffic.
The study from WatchGuard Technologies, which provides cybersecurity for MSPs, shows 70 percent of all malware is now delivered via encrypted connections, the findings highlight attackers’ increasing reliance on obfuscation and stealth, and the need for organizations to improve visibility into encrypted traffic and adopt flexible protection strategies.
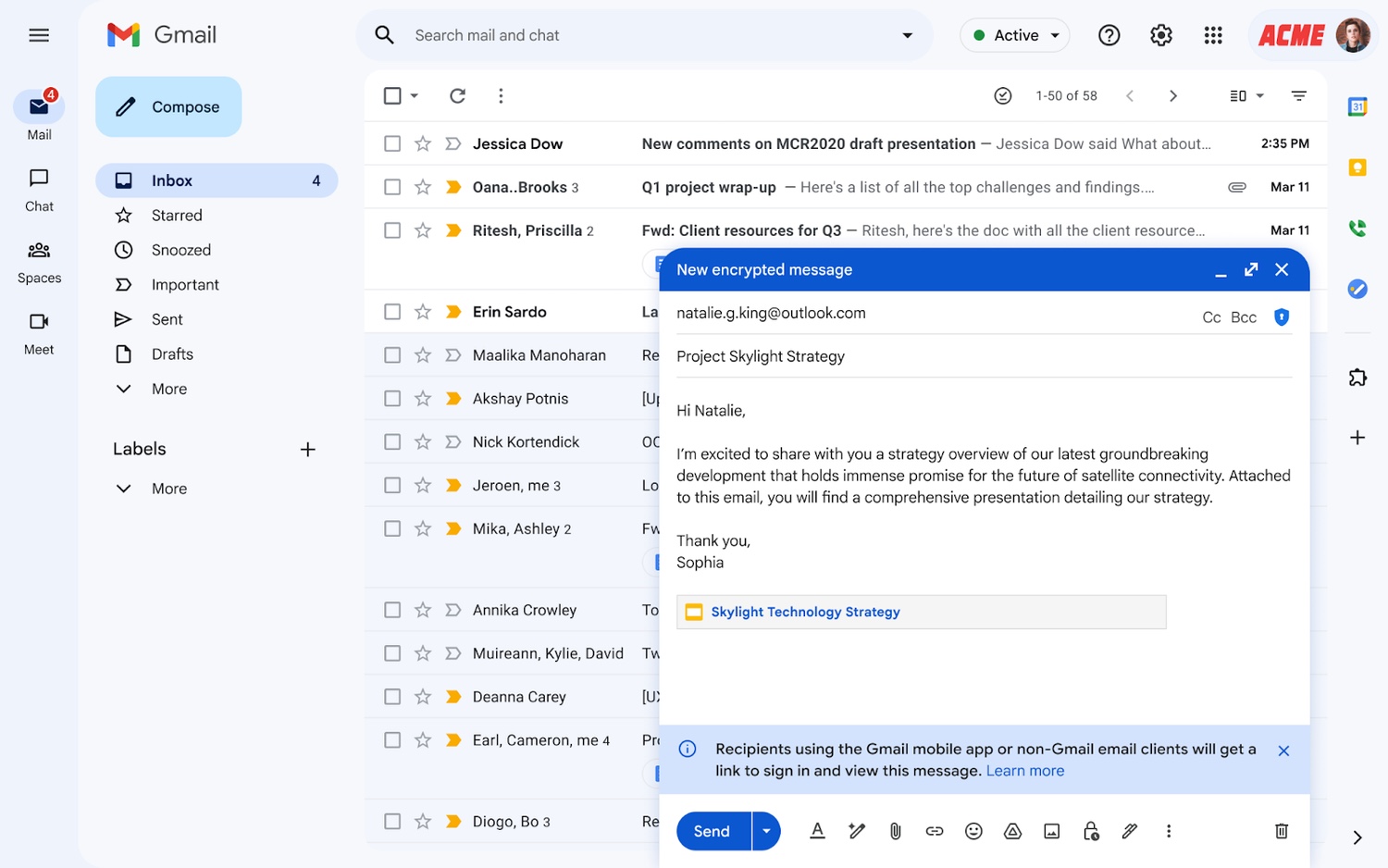
Gmail makes encrypted emails more useful for business users
Google has announced that it is now possible to send Gmail end-to-end encrypted emails to anyone. Until this change was introduced, E2E emailing was only supported between Gmail to Gmail communications.
But now email encryption is being opened up and made platform agnostic. While this means that encrypted emails can be sent to anyone, it is something that needs to be enabled, and there are a few things to keep in mind.

Cryptographic debt and quantum readiness [Q&A]
As White House Executive Orders, NIST mandates, and international deadlines accelerate the push toward post-quantum encryption, the clock is ticking for organizations still grappling with cryptographic debt.
We spoke to Dave Krauthamer, co-founder and field CTO at QuSecure, to learn more about emerging threats, compliance mandates, and mitigation frameworks for organizations looking to get ahead of the coming disruption.

UK Online Safety Act leads to rise in searches for fake ID and dark web access
We know that the UK’s Online Safety Act has had a number of consequences including a surge in interest in the use of VPNs. But VPNs aren’t the only things that have seen greater interest.
New research from Comparitech shows more people are searching for fake IDs, how to access the dark web, and torrenting services. The company has recorded a 56 percent increase in impressions for blog posts related to the law and guides to using VPNs as a means of accessing restricted content.
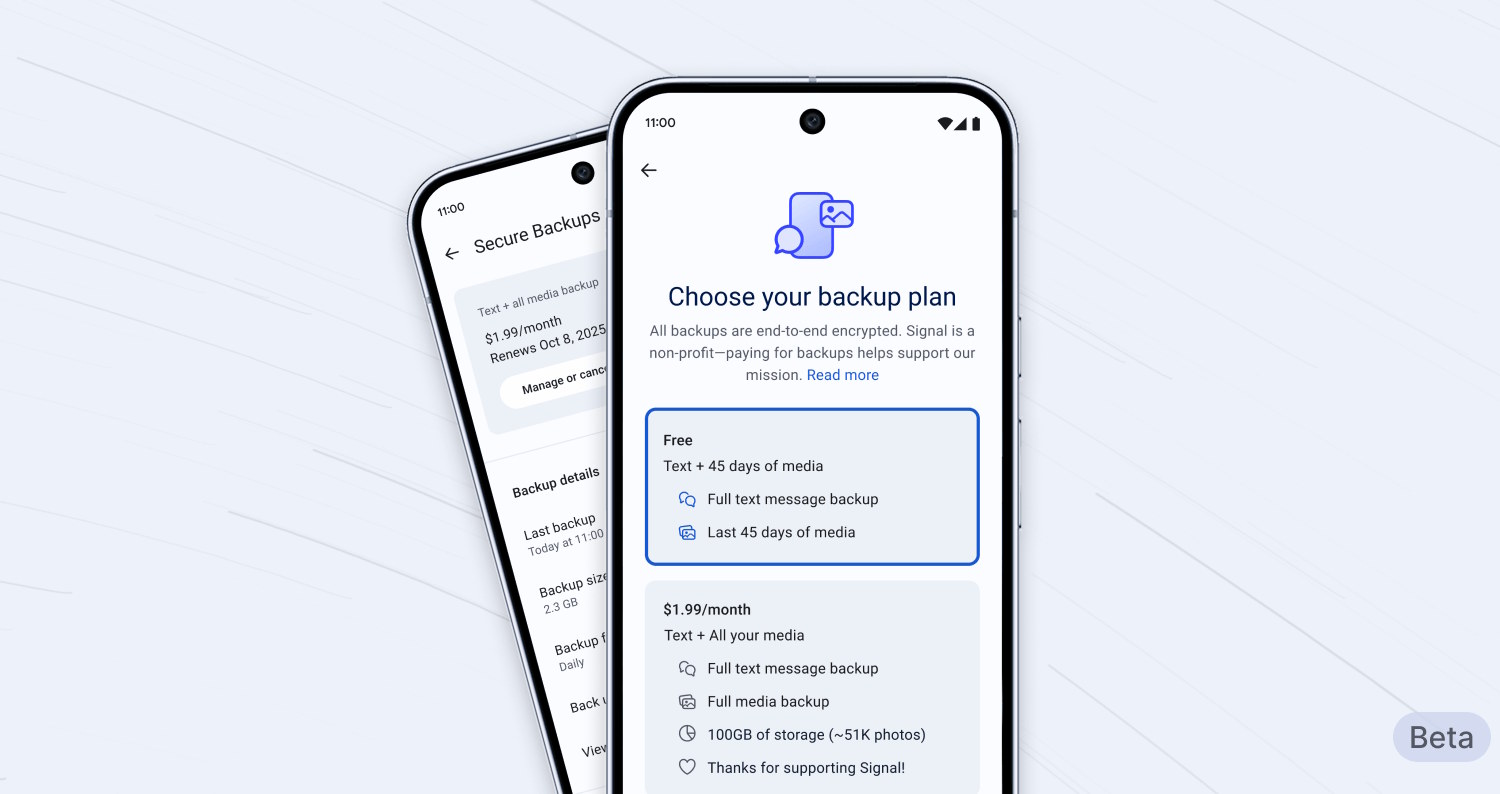
Secure messaging platform Signal introduces chat backup options
In an age where there is increased concern about privacy and security, people are embracing messaging platforms such as Signal. While Signal and other apps of its ilk mean enjoying a security boost, such apps are playing catch-up with mainstream messaging platforms in terms of other features and options.
Signal has just announced the availability of secure backups for chats, promising an easy way to restore your messaging history to a new device. This is something that Signal users have been begging for, and now it is here. As you might expect with a platform associated with security and privacy, backups are not a simple matter with Signal.

The future of encryption in a post-quantum world
As quantum computing speeds edge closer to practical use, the ‘harvest now, decrypt later’ approach is already in motion with adversaries collecting encrypted data today, anticipating they'll be able to crack it tomorrow. But is enough being done to prevent it?
New research from Forescout highlights the urgent need for organizations to prepare for a future where quantum-capable adversaries can break widely used cryptographic protocols.

Encryption adoption up but sensitive data is still at risk
Encryption adoption has soared to 94 percent, but inconsistent application continues to put sensitive data at risk, finds a new survey.
The study from secure storage maker Apricorn shows that 59 percent of IT security decision makers say encryption has increased, allowing them to better protect their data, including on lost/stolen devices.

Elon Musk confirms everyone is getting the 'all new' XChat this week, complete with 'Bitcoin style encryption'
Looking to compete with the likes of Signal, Elon Musk is ready to rollout XChat to all users of his X social platform. Rather than being a separate app for chatting, however, XChat is essentially just direct messaging within X -- so who is it for, and what does it have to offer?
Taking inspiration from numerous sources, Musk says that in addition to text-based messaging, there is also video and audio calling. Other features include vanishing messages, the option to “send any kind of file”, and an undetailed encryption system.

Quantum solution aims to secure communication using satellites
Today is World Quantum Day -- which probably means that it simultaneously both is and isn't. Seriously though, we're used to hearing dire warnings about how quantum computing threatens encryption and private communication, but of course it can also be part of the solution.
A new alliance between Partisia, a leader in multiparty computation (MPC), Squareroot8, a provider of quantum-safe communication solutions and NuSpace, a company specializing in IoT connectivity services and Satellite-As-A-Service wants to place a Quantum Random Number Generator (QRNG) on a satellite in space.

Microsoft’s Majorana 1 quantum chip could break encryption and expose your data to hackers
Microsoft is moving closer to quantum computing supremacy with the arrival of its new Majorana 1 chip, a development which could potentially have a far-reaching impact on cybersecurity. While the Windows-maker touts this as progress, the reality is far more concerning. The encryption that protects banking transactions, government data, and personal communications could soon be worthless.
Microsoft's advancement comes down to Microsoft’s new topoconductor material, which enables a type of quantum computing that scales far beyond anything possible today. “We took a step back and said ‘OK, let’s invent the transistor for the quantum age. What properties does it need to have?’” said Chetan Nayak, Microsoft technical fellow. “And that’s really how we got here -- it’s the particular combination, the quality and the important details in our new materials stack that have enabled a new kind of qubit and ultimately our entire architecture.”
