
Check your privacy settings -- Facebook is (probably) sharing your employment history
Somewhat out of the blue, Facebook has decided to change the way it displays certain information on your profile. Not content with showing your current place of work -- whether this is real, or some clever pun you've engineered -- it now also shows your employment history.
This is not a direct change to privacy settings as it does not make public anything that had been previously set to be private. It does, however, broadcast your previous places of work to people looking at your profile. You might not like this. You might want to do something about it.

A win for privacy: Senate blocks FBI from gaining warrantless access to browsing histories
A Senate amendment brought forward by John McCain that would have given the FBI the right to browse suspects' phone and internet records without a warrant has been narrowly defeated.
The vote very nearly went the other way -- there were just two votes in it when the counting was over. McCain had hoped that pushing the amendment as a counter-terrorism tool (particularly against "non-U.S. citizen 'lone wolf' attackers") would be enough to get the required 60 votes. But it seems that the Orlando shooting that McCain cited as an incentive for the changes was not enough to convince others.

Mark Zuckerberg is so concerned about his privacy that he tapes over his webcam and microphone
Facebook and privacy are not words usually associated with one another, and it seems this holds true even for the man at the top. Only recently we learned that Mark Zuckerberg uses terrible passwords, making it easy to hack his accounts, but now it turns out he's also quite paranoid.
As Instagram popped champagne corks for reaching the milestone of half a billion users, Zuckerberg posted a celebratory picture. Eagle-eyed people soon pointed out that both the mic and camera of his laptop were taped over.

Most UK workers don't want company-issued wearables
Despite the fact that three million Britons bought wearables during 2015, the majority of UK office workers are unwilling to wear them at work. After conducting a survey of 2,000 workers across the UK, PwC found that only 46 percent of respondents would accept a free wearable device from their company if their employer had access to the data it recorded.
In the past few years, wearables from companies like Fitbit and Jawbone have taken the consumer market by storm as a means of tracking one’s health and fitness. PwC’s survey found that two-thirds of those surveyed want their employer to take a more active role in their health and well being, and a company-issued wearable would be a good first step at doing just that.

Apple: Developers must use App Transport Security by 2017
Apple has announced that the deadline by which app developers must enable App Transport Security (ATS) in all apps is 1 January 2017. ATS is not a new feature of iOS 10, having been introduced in iOS 9 and it increases the security of data transferred over the web by apps.
With ATS enabled, apps are forced to use the far more secure HTTPS rather than HTTP, and this is something we've become accustomed to looking out for when browsing the web. At the moment, developers are able to disable ATS, but from the end of the year this will no longer be possible.
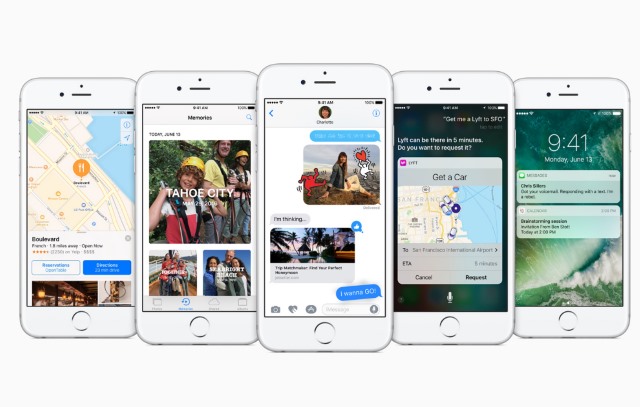
Apple focuses on new features and privacy in iOS 10, while opening up to developers
It's what Apple is describing as 'the biggest iOS release ever'. Whether everyone else agrees remains to be seen, but today the company took the wraps off iOS 10 -- and there's certainly a lot to take in. Perhaps the most notable change, for developers at least, is the fact that Siri has been opened up so that it can be used by third party apps.
Messaging has become more important than ever in recent years, and this is something that Apple recognizes with iOS 10. Taking design cues from the likes of Facebook and WhatsApp, the Messages app now includes full screen animations, and there's a neat new feature that means you can handwrite messages.

Julian Assange's WikiLeaks poised to release more Hillary Clinton emails
In a move that could boost Donald Trump's election campaign, WikiLeaks is on the verge of releasing more of Hillary Clinton's emails from her stint as US secretary of state. Clinton's use of a homebrew email server and a private email address for sending classified information has dogged her presidential campaign -- and Julian Assange is happy for that to continue.
The WikiLeaks founder, currently in exile in the Ecuadorian embassy in London, has made no secret of his loathing for Clinton. She is the subject of a federal investigation, and Assange is happy to add fuel to the fire by publicly releasing another batch of emails.

Snowden: Scotland has its own NSA conducting mass surveillance of phone and internet activity
Documents leaked by Edward Snowden reveal that Scottish authorities have been engaged in gathering data about phone and internet usage in much the same way as the NSA and GCHQ. The Scottish Recording Centre (SRC) accessed information gathered as part of a bulk data collection program called MILKWHITE.
Scottish newspaper The National, in conjunction with the website CommonSpace, have exposed Scotland's role in the UK's mass surveillance programs. Police and tax authorities in Scotland -- devolved from UK forces -- were given accessed to what the Intercept describes as 'huge troves of metadata' gathered by spy agencies.

Even threatening to circulate revenge porn could be criminalized across Britain
New laws have been proposed for England and Wales that would criminalize not only the circulation of revenge porn, but also threatening to circulate it. The definition of what constitutes revenge porn could also be expanded.
This level of criminalization is already in force in Scotland, and Liberal Democrat MP Alistair Carmichael believes that the rest of Britain should follow suit. If adopted, the proposed change would see revenge porn threats seen in much the same light as other forms of blackmail.

It's not just Windows 10 that has telemetry issues -- Microsoft has done the same with Visual Studio 2015 C++ compiler
An eagle-eyed Reddit user has noticed that code run through Visual Studio 2015 C++ compiler make calls to Microsoft's telemetry services. Microsoft has already upset a large number of people with the privacy and telemetry issues in Windows 10, and there is now a busy thread on Reddit discussing the company's thinking behind including this 'feature'.
Coders have expressed concerns that Microsoft appears to be inserting calls to its telemetry service into binaries as they are compiled. Calls to telemetry_main_invoke_trigger and telemetry_main_return_trigger raised a few eyebrows having been found in both debug and release versions of the software. The good news -- maybe -- is that telemetry can be disabled.

How to remove location data from your photos
Saving the location in photos you take with your smartphone, tablet or camera is a good idea if you want to keep track of where you've captured those moments. Some services, like Google Photos, will do that for you automatically, showing a history of places you've been based on their coordinates. However, when it comes time to share your photos online, you may want to remove the location data.
The location data, alongside other types of identifiable information, will also be shared alongside them, potentially exposing you and your loved ones to all sorts of complications as a result. Fortunately, you can remove the location data from your photos. Here is how you can do that.

India blocks Google's plans for Street View in the country amid security concerns
Google's plans to gather Street View data in India have hit a brick wall after the country rejected the company's proposals.
Indian security agencies expressed concerns about plans to send Google Street View cars around the country, taking 360-degree photos along roadways. This is certainly not the first time Google Street View has faced problems, with numerous cases relating to privacy resulting in changes being made to the service.

European workers use cloud services for whistle blowing
Wait until you hear what employees in Europe are using cloud services for. Oh, boy.
Blue Coat Systems has polled more than 3,000 workers in France, Germany and the UK, asking them about their cloud usage habits, and, as it turns out, some employees use such services (Dropbox, Box, Office 365, Slack, LinkedIn, Facebook, Gmail, etc.) to store data before starting a new job, for corporate espionage, whistle-blowing and even "personal protection".

One in five UK businesses would keep a data breach secret
Almost a fifth (19 percent) of companies in the UK wouldn’t notify their customers in case of a data breach, a new report highlights.
As the EU GDPR draws closer, Trend Micro investigated if companies have formal processes in place to notify data protection authorities (within 72 hours), and the public, in case of a data breach, as will be enforced by the Regulation.

Snooper's Charter, aka the Investigatory Powers Bill, voted into UK law
The controversial Snooper's Charter -- or the Investigatory Powers Bill as it is officially known -- has been voted into law by UK MPs. An overwhelming majority of politicians (444 to 69) voted in favor of the bill which has been roundly criticized by both the public and technology companies.
The Investigatory Powers Bill grants the UK government, security, and intelligence agencies greater powers for monitoring internet usage, as well as permitting bulk data collection and remote hacking of smartphones. The law allows for the kind of mass surveillance that Edward Snowden warned about, and while the bill may have passed a majority vote, there are still those who fear not enough has been done to safeguard individuals' privacy.
