
Web application security -- five ways to improve your approach
Web applications remain one of the most targeted areas for threat actors. According to Verizon’s Data Breach Investigations Report, web application attacks were behind 26 percent of all successful attacks during the twelve months covered. Yet while the methods for attacking web applications are well known and understood, as evidenced by the work that the Open Web Application Security Project (OWASP) has done on their Top Ten list over the years, many companies still find hardening their applications challenging.
Authorization and access control describe the biggest set of challenges identified by OWASP in their most recent Top 10 list (2021) -- three out of the top five issues were around broken authorization, while broken authentication and improper access to resources were also common problems. The OWASP Top 10 for 2021 also includes attacks that work on unrestricted access to sensitive business flows, which covers areas like creating fake accounts, and server side request forgery where APIs can send resources to the wrong locations.

Open to attack: The risks of open-source software attacks
Open-source software (OSS) is now so widely used that it is incredibly difficult to find an organization that doesn’t incorporate OSS in some form or another -- whether that be in a standalone open-source product, or more commonly, in the form of OSS packages. Though its usefulness cannot be doubted, the prevalence of this software is exactly what makes it a major target for cyber-attacks.
A prime example of this is Log4j, a popular logging utility used by scores of organizations for recording events such as status reports and errors. In a situation which came to be known as 'Log4shell', a zero-day vulnerability allowed threat actors to compromise systems using malicious code and take control all while remaining undetected. At the time, its impact was described as "enormous" and the implications of its implementation into countless commercial products underlined the inherent vulnerabilities of some open-source technologies when weak points are exposed.

Microsoft releases KB5033375 update for Windows 11 fixing Copilot problems and more
With the release of the KB5033375 update, Microsoft has delivered not only a series of security patches to Windows 11, but also an important upgrade to Copilot.
The AI-powered digital assistant has proved problematic for many users, and now Microsoft has taken steps to fix things. There are also fixes for lots of non-Copilot related issues, and a power consumption reducing update for Dynamic Lighting.

Microsoft releases mandatory KB5033372 update, pushing Copilot on Windows 10 users
The time of the month for Microsoft to release its security updates for Windows has rolled around again. The company has released the KB5033372 update for Windows 10, bringing not only security fixes, but other improvements and new features -- including Copilot.
As the KB5033372 update includes security fixes, it is rolling out to all Windows 10 users automatically. This means that everyone will be given access to a preview version of Microsoft's AI-powered digital assistant.

Microsoft opens up Extended Security Updates to consumers so everyone can pay for Windows 10 support
With support for Windows 10 coming to an end in under two years, Microsoft has been trying to encourage everyone to upgrade to Windows 11. The reality is that this is not something that all Windows 10 users want to do, and it is not possible for many because of hardware requirements.
Now Microsoft has relented. The company has made a somewhat surprising move in giving all Windows 10 users the chance to pay for Extended Security Updates (ESU) when Windows 10 reaches end of service. Until now, the ESU program has only been available to larger organizations and enterprise customers. In opening it up to home users, Microsoft is effectively admitting that it foresees large numbers of people continuing to stick with Windows 10 -- so the company has decided to try to profit from this fact.

Elevating enterprise resilience with real-time ransomware detection
2023 looks set to be yet another record-breaking year for ransomware attacks. According to Statista, over 72 percent of businesses worldwide have already been affected by ransomware attacks this year, with LockBit3.0 and CI0p Ransomware claiming the bulk of victims last quarter.
The scourge of modern digital businesses everywhere, the proliferation of ransomware shows no sign of slowing down thanks to the rise of ransomware-as-a-service (RaaS) platforms -- so much so that it has become the most prevalent issue confronting organizations today.
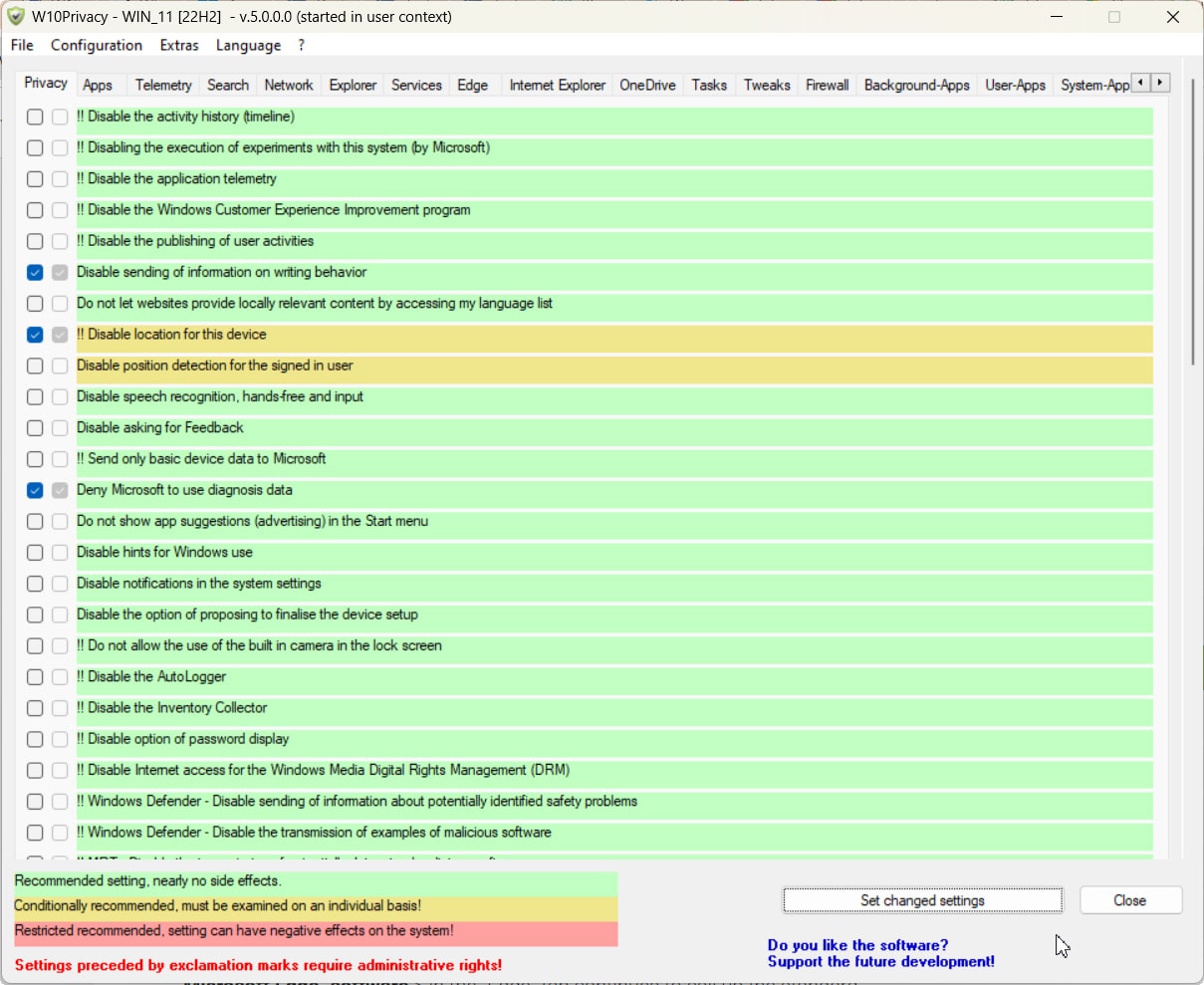
Win10Privacy 5.0 gives you complete control over your privacy in Windows 10 and Windows 11
When it was first released, Windows 10 famously spied on users and shared all sorts of information with Microsoft. Over the years, the software giant has reigned in this behavior and introduced a wealth of privacy controls to let you manage what you share.
That said, these controls are scattered throughout the OS and finding them isn’t always easy. This is where Win10Privacy can help.

Get 'Cybersecurity All-in-One For Dummies' (worth $30) for FREE
Cybersecurity All-in-One For Dummies covers a lot of ground in the world of keeping computer systems safe from those who want to break in.
This book offers a one-stop resource on cybersecurity basics, personal security, business security, cloud security, security testing, and security awareness. Filled with content to help with both personal and business cybersecurity needs, this book shows you how to lock down your computers, devices, and systems -- and explains why doing so is more important now than ever.

Will Quantum Computing change the way we use encryption?
Today, encryption is a cornerstone of our cybersecurity practices. It protects everything from cell phones and SMS messages to financial transactions and intellectual property.
However, a new challenge in the complex landscape of encryption has recently emerged, thanks to the advancement of quantum computing. What challenges lay ahead? Here is the breakdown:

The CISO view: Navigating the promise and pitfalls of cybersecurity automation
Cybersecurity automation has steadily gained traction as organizations seek to improve efficiency, address talent gaps, and keep up with escalating threats. However, our latest State of Cybersecurity Automation research shows that while more businesses are utilizing automation, they continue to grapple with obstacles that prevent them from fully capitalizing on its benefits.
In our recent study surveying over 700 cybersecurity professionals, we uncovered several persistent pain points in implementing automation. The research found that a lack of trust in automated outcomes, insufficient expertise among users, and poor communication between teams have hampered automation success. As a result, organizations are struggling to build confidence in automation and maximize its effectiveness.

Why good cyber hygiene is a strategic imperative for UK SMEs
No company is immune from a cyber-attack, with large and small being targeted. As technologies advance and cybercriminals hone their skills, evolve their tactics, and find new vulnerabilities to exploit, companies can no longer ask the question of if a cyber attack will occur but when and how it will happen.
While the number of data breaches is cause for concern, the cost associated with them is equally alarming. According to Cybersecurity Ventures, the global average cost of a cyberattack has ballooned to $4.45 million, increasing by 15 percent over the past three years. Even more sobering is that it shows no signs of easing, as global cybercrime costs are projected to reach $10.5 trillion annually by 2025.

Microsoft launches Defender Bounty Program to find bugs in its security software
Microsoft has added yet another bug bounty program to its growing portfolio. With the launch of the Microsoft Defender Bounty Program, the company is offering financial rewards to researchers who "uncover significant vulnerabilities" in its range of security products and services.
The program is focused solely on vulnerabilities of Critical or Important severity, and Microsoft is putting up rewards of between $500 to $20,000 for eligible submissions. Starting off somewhat limited in focus, the aim is to open up the program to have a wider scope further down the line.

The human element -- cybersecurity's greatest challenge
The stark reality of cybersecurity today isn't merely a question of advanced software or strategic counterattacks. It's about people.
The financial impact is undeniable with cybercrime costs projected to reach an astonishing $10.5 trillion annually by 2025. Yet, beneath these figures lies a more pressing issue: the exploitation of human psychology.

Get 'Python for Security and Networking -- Third Edition' (worth $39.99) for FREE
Python’s latest updates add numerous libraries that can be used to perform critical security-related missions, including detecting vulnerabilities in web applications, taking care of attacks, and helping to build secure and robust networks that are resilient to them.
This fully updated third edition of Python for Security and Networking will show you how to make the most of them and improve your security posture.

People, process, technology: How to shift security testing left successfully
The benefits of shift-left security are clear. It puts security testing in the hands of the engineers who write the code, enabling vulnerability fixes to occur before software hit production. This provides fixers with faster feedback loops on vulnerabilities found, as well as ensuring more efficient time to feature delivery and cohesive teamwork between security and development teams. With all the benefits that come with shifting API and web application security left, it’s no wonder that 57 percent of security team members have either already shifted their security strategy left or are planning to do so this year, according to a GitLab survey.
So, how do organizations implement a shift-left security strategy successfully? The answer lies in the popular three-legged stool analogy: assessing the process, people, and technology behind this major organizational change, and how they all can work together interdependently.
