
Digital cold war and other emerging threats we'll face in the next two years
A new report from the Information Security Forum looks at the threats organizations can expect to face over the next two years as a result of increasing developments in technology.
The Threat Horizon 2021 report highlights three major themes that will present particularly difficult cyber security challenges for businesses.

Next generation cyber defense driven by analytics and machine learning
The biggest problem for security teams is often too much data and many are addressing this by turning to analytics and machine learning, according to a new report.
The study from CyberEdge Group surveyed 1,200 IT security decision makers and practitioners and finds 47 percent intend to deploy advanced analytics solutions in the next year.

ASUS Live Update Utility hacked to deliver ShadowHammer backdoor malware to a million systems
Kaspersky Lab reports that the software update system used by ASUS was hijacked by hackers and used to deliver a backdoor-laden piece of malware to users. The company estimates that around a million users may have been affected by what it describes as "one of the biggest supply-chain incidents ever".
Back in January, the security firm discovered that a threat actor interfered with the ASUS Live Update Utility, adding a backdoor to it. Signed with an official ASUS certificate and carefully crafted to be precisely the same size as the official tool, the malware -- dubbed ShadowHammer -- went unnoticed for some time.

61 percent of CISOs believe employees have leaked data maliciously
A new study reveals that 79 percent of IT leaders believe that employees have put company data at risk accidentally in the last 12 months, and 61 percent believe they have done so maliciously.
The research from data security company Egress also explores how employees and executives differ in their views of what constitutes a data breach and what is acceptable behavior when sharing data.
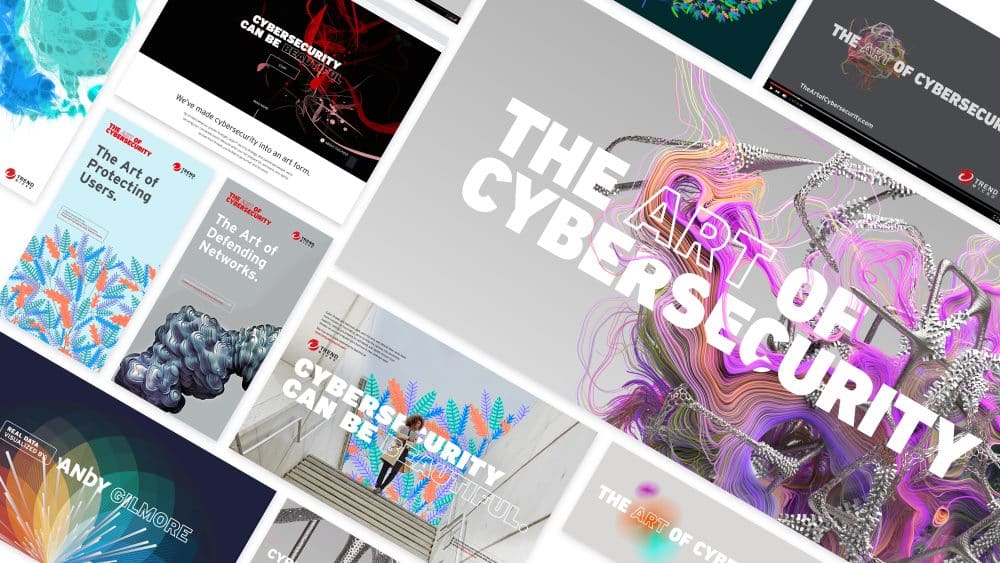
Trend micro calls in artists to make cybersecurity beautiful
When you think of cybersecurity, art and beauty probably aren't the first things that come to mind. But if Trend Micro has its way that could be about to change.
The company has commissioned a number of artists to create what it calls The Art of Cybersecurity. This is a series of works based on security data, with the idea of shifting the perception of protecting systems from a burden, to something beautiful.

Panic Button secures data -- by destroying it
One of the biggest worries about someone gaining unauthorized access to your computer is that they can view and steal your data.
The CyberYozh security group has launched a product that protects your sensitive files, browser data and more, by taking the nuclear option of destroying it.

Facebook stored millions of users' passwords in searchable plain text for years
Just when you think things couldn't get any worse with Facebook, something else comes along to lower your opinion of the social network even further. The latest security slip-up relates to passwords: it turns out that for up to six years, millions of user passwords were stored in plain text.
As well as being stored in plain text, passwords were searchable by thousands of Facebook employees. An investigation by Facebook suggests that somewhere between 200 million and 600 million user accounts were affected, some as far back as 2012.

New vulnerability reporting platform aims to make open source safer
Vulnerabilities in open source code represent a risk for businesses, but the process of reporting them is cumbersome and that can leave software open to risk.
Without a standard for responsible disclosure, even those who want to disclose vulnerabilities responsibly can get frustrated with the process and turn to public lists or social media, where bad actors can easily find the details before fixes are created.

Microsoft brings its Windows Defender antivirus software to Mac
In February, Microsoft announced Microsoft Threat Experts, a new service within Microsoft 365 Security designed to better protect businesses.
Today, the software giant extends its endpoint protection platform to Mac, and in keeping with that move renames the Windows Defender ATP platform to Microsoft Defender ATP.
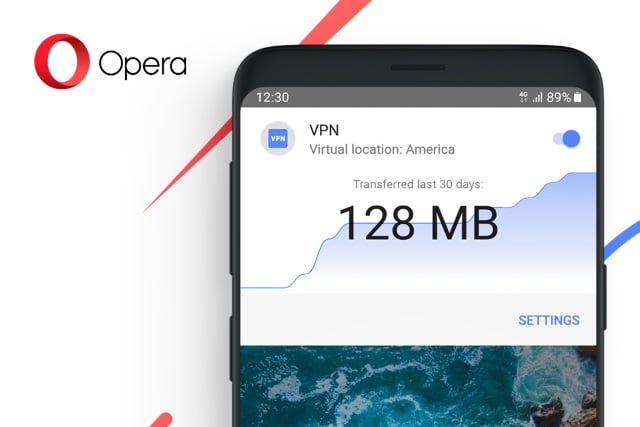
Opera for Android now includes a free and unlimited VPN
Opera has added a free VPN service to the Android version of its mobile web browser. Opera 51's newly-added VPN is not only free from charges, it is also free from limitations.
The feature has been added as the Norwegian software developer seeks to improve the security and privacy of web browsing for its users. The company says that it "marks a new standard for privacy and security in mobile browsing".

SoftNAS vulnerability lets attackers bypass authentication
Researchers have uncovered a vulnerability in the SoftNAS Cloud data storage platform that could be used to gain access to the webadmin interface without valid user credentials.
Security technology company Digital Defense found the previously undisclosed vulnerability which arises if customers have not followed SoftNAS deployment best practices and have openly exposed SoftNAS StorageCenter ports directly to the internet.

Free tool protects businesses against ransomware and other threats
Ransomware and other threats like adware and cryptominers are still a major threat to businesses. But smaller companies may be struggling to find the resources to combat them.
To address this problem Kaspersky Lab is today releasing the next generation of its free Kaspersky Anti-Ransomware Tool for Business.

Insider threats pose the biggest security risk
According to a new study 91 percent of IT and security professionals feel vulnerable to insider threats, and 75 percent believe the biggest risks lie in cloud applications like popular file storage and email solutions including Google Drive, Gmail and Dropbox.
The report from SaaS operations management specialist BetterCloud also shows 62 percent of respondents believe the biggest security threat comes from the well-meaning but negligent end user.

8 out of 10 top vulnerabilities target Microsoft products
Prioritizing vulnerabilities can be difficult if you don't know which ones are being actively exploited. The latest annual research from Recorded Future looks at the top vulnerabilities and which products they are targeting.
In 2018, the company observed more exploits targeting Microsoft products compared to Adobe ones. Eight out of 10 vulnerabilities exploited via phishing attacks, exploit kits, or RATs were targeting Microsoft products.

Addressing the skills gap with advanced web attack training now available online
There is a shortage of cybersecurity professionals and coupled with the exponential growth in web applications used within businesses and by consumers around the world, there's a growing risk of flaws being exploited.
To combat this problem penetration testing specialist Offensive Security is making its Advanced Web Attacks and Exploitation (AWAE) training available as an online course.
