
DoubleAgent exploit uses Windows' Microsoft Application Verifier to hijack antivirus software
Security researchers at Cybellum have revealed details of a zero-day exploit that makes it possible for an attacker to take full control of antivirus software. The technique can be used to take control of just about any application, but by focusing on antivirus tools, the illusion of safety offered to victims means they are likely to be completely unaware of what is happening.
The attack works by exploiting the Microsoft Application Verifier that's built into Windows. It is possible to replace the tool with a custom verifier which can then be used to inject malicious code into any chosen application. A number of well-known antivirus tools -- including Avast, BitDefender, ESET, Kaspersky, and F-Secure -- are vulnerable, while patches have been released for others.

Google discloses actively exploited Windows vulnerability before Microsoft patch is ready
Google has shared details of a 0-day vulnerability in Windows a mere 10 days after informing Microsoft of the problem. In Google's own words, "this vulnerability is particularly serious because we know it is being actively exploited", but the company is accused of putting users at risk.
Microsoft is yet to produce a patch for the security problem, and it's not clear when one will be released.

Comodo offers companies free forensic analysis to fight zero-day malware
Because it isn't detected by traditional, signature based anti-virus solutions, zero-day malware has the potential to wreak havoc in businesses of all sizes.
Cyber security company Comodo is launching a new, free forensic analysis service to help enterprises discover previously unknown and undetected malware that could cause serious security issues or data breaches.

CheckPoint launches real-time zero day browser protection
The most common way for malware to get onto a PC is via files downloaded from the web. According to Exploits at the Endpoint: SANS 2016 Threat Landscape Study, 41 percent of people suffered their worst security events from drive by downloads and 80 percent suffered phishing attacks.
Threat protection specialist CheckPoint is launching a new anti-malware and anti-phishing extension for web browsers to address this growth in web-based malware and social engineering attacks.

Zero-day flaw leaves LastPass vulnerable to attack [UPDATE: it's fixed]
A Google Project Zero hacker has discovered a zero-day vulnerability in the password manager LastPass that could lead to accounts being completely compromised.
The security flaw can be triggered by visiting a malicious website, and it has been confirmed to be an issue by white hat security researcher Tavis Ormandy. He has filed a full report to LastPass with a view to getting the vulnerability patched.

Newly-discovered zero-day vulnerability affects all versions of Windows
Security firm Trustwave has discovered a zero-day exploit for Windows for sale on an underground Russian hacking forum. A user going by the name BuggiCorp says the vulnerability affects all versions of Microsoft's operating system, from Windows XP and 2000 upwards, including both 32- and 64-bit versions.
The source code for the exploit is offered for upwards of $90,000, and the seller explains that it can be used to elevate the privileges of any software process to SYSTEM level -- the highest there is. Payment is requested in Bitcoin, but while the exploit is considered serious, experts suggest that the asking price is a little high.

Dell launches zero-day protection for thin clients and virtual desktops
Endpoint protection is still vital for enterprises of all sizes. Dell is launching new security products aimed at giving businesses advanced threat prevention for Windows Embedded thin clients and virtual desktops.
Using IP from its award-winning Dell Data Protection portfolio of security solutions, Dell is applying its endpoint security expertise beyond the PC to the thin client and virtual machines. The company claims this will give customers an industry-first approach to comprehensively securing their data.

Zero day OS X flaw can bypass System Integrity Protection
Security company SentinelOne has released news of a major flaw in Apple OS X systems that can allow the bypassing of the latest System Integrity Protection security feature.
This zero day vulnerability is present in all versions of Apple's OS X operating system. It has been reported to Apple and patches will be available soon. SentinelOne’s lead OS X security expert, Pedro Vilaça, is presenting the full findings on this vulnerability today at SysCan360 2016 in Singapore.
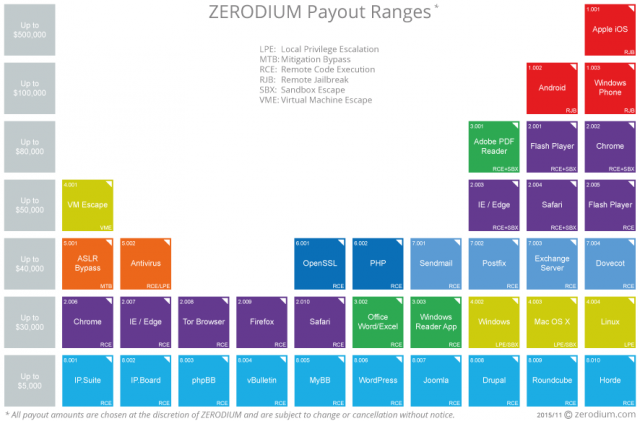
Zerodium reveals price list for zero-day exploits
Exploit acquisition platform Zerodium has just published a price chart for different classes of digital intrusion techniques and software targets that it buys from hackers and later resells in a subscription service to its clients.
This is important as it is the first time someone has publically put a price tag on hacking.

Adobe Flash zero-day vulnerability surfaces one day after security updates
Yesterday Adobe rolled out its monthly security patches, something all users should pay attention to given past history. Flash, Reader and Acrobat all received fixes, presumably remedying the current batch of problems plaguing the software. The problem is, nothing ever seems fixed in the world of Adobe.
To that end, a zero-day exploit has already been discovered by the folks at security firm Trend Micro. Yes, that didn't take long and Adobe didn't fix this one.

Zero-day vulnerabilities increase over 2014
Danish security company Secunia is using the Black Hat conference to reveal an early look at the vulnerability trends to date for 2015.
One of the main findings is that 15 zero-day vulnerabilites have been discovered so far in 2015, making it likely that the total for the year will exceed the 25 discovered in 2014. The 2015 zero-days were all discovered in popular Adobe and Microsoft products widely in use across both personal and professional IT systems.

Second zero-day flaw found in Adobe Flash thanks to Hacking Team
Earlier this week an exploit for Adobe Flash was revealed -- a shock, I know. Now a second is in the wild and already being used. Known by the catchy name CVE-2015-5122, security firm FireEye discovered the flaw buried in the Hacking Team leak and alerted Adobe to it.
Adobe has released a security bulletin stating "Critical vulnerabilities (CVE-2015-5122, CVE-2015-5123) have been identified in Adobe Flash Player 18.0.0.204 and earlier versions for Windows, Macintosh and Linux. Successful exploitation could cause a crash and potentially allow an attacker to take control of the affected system".
AVG AntiVirus Free 2015 debuts zero-day protection, redesigned user interface
AVG Technologies has updated its entire range of PC products, launching AVG AntiVirus Free 2015, AVG AntiVirus 2015, AVG Internet Security 2015 and AVG PC TuneUp 2015.
After the relatively major changes introduced in the 2014 versions, this year’s updates are restricted to a redesigned user interface and new Outbreak Detection feature, which helps block zero-day malware exploits.
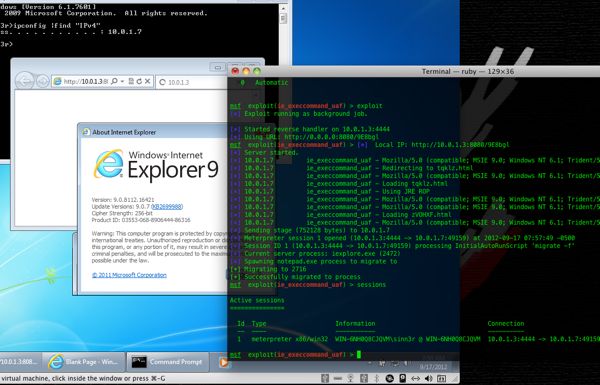
Internet Explorer zero-day exploit threatens huge chunk of IE users
Security researchers this week uncovered a bug in Microsoft's Internet Explorer that is actively being exploited in targeted attacks and remote code execution. Microsoft responded by launching its own investigation of the vulnerability, but has no solution yet.
The vulnerability has been observed in Internet Explorer 6 through Internet Explorer 9 on Windows XP SP3, Vista, and Windows 7, and users can be infected simply by visiting a malicious website.

Adobe patches critical zero-day Flash flaw
Adobe has issued an out-of-cycle patch for its Flash, Reader, and Acrobat applications which it recommends all users upgrade to immediately. The fix will close a security hole in the Authplay component, which allows for the use of Flash within PDF files.
Code to exploit the vulnerability was out in the wild, Adobe has disclosed. It had initially believed that the vulnerability was only being exploited through malformed Flash .swf files within Excel spreadsheets, but it was discovered that attackers could also possibly exploit the vulnerability through holes in the PDF file format.
