
Microsoft Translator now supports Yucatec Maya and Querétaro Otomi languages
As an American, I am really only exposed to two languages -- English and Spanish. While I speak the former fluently (it is my native language), my comprehension of the latter is extremely limited. For the most part, I am satisfied in my English-only world, but I do regret not learning other languages as a child.
While I am now too old and set in my ways to learn a new language, technology makes the need to do so less important nowadays. Translation software helps communication barriers melt away. Now, Microsoft Translator is expanding beyond common languages, to the more rare. The company announces that Yucatec Maya and Querétaro Otomi are supported.

Facebook's privacy policy breaks the law in Europe
There are many things that Facebook finds itself accused of on a regular basis. Unfairness to different groups, censorship of content, insensitivity, and endless problems surrounding its attitude to privacy and handling of user data. It seems that concerns about privacy were well-founded as a new report finds that the social network violated European law. Analysis carried out by the Belgian Privacy Commission and ICRI/CIR says that Facebook breaks the law in Europe in a number of ways. As well as placing too many expectations on users to be able to change settings for themselves.
Facebook is also accused of failing to give people the ability opt out of certain privacy-invading features. Back in January, Facebook made some changes to its privacy policies and also introduced simplified documentation. The report found that rather than cleaning up its act, Facebook merely highlighted some of its old, existing practices. The social network is criticized for its "complex web of settings", for failing to explain what is meant when users are told that their data will be used "for advertising purposes", and for not allowing people to opt out of Sponsored Stories and location sharing.
Want the Windows 10 icons in Windows 7/8.x? Here's how
Windows 10 isn't here yet, though in a way it sort of is -- in other words, it's a Preview version meant to test the waters. Microsoft has high hopes of putting version 8.x behind it, even skipping a number to distance itself. But not everyone wants to run a possibly unstable version of an operating system, especially on a production machine. However, you can still get the new icon set without installing the OS.
Packs of the icons have been collected and made available for customers of both Windows 7 and Windows 8x. Getting them on your desktop is just a click or two away. The icons are spread out, encompassing desktop, system tray and Explorer.

Restore files, partitions, broken PCs with Lazesoft Recovery Suite
Install the free version of a commercial program and you expect to find some restrictions, but undelete tools often go a little too far. You might only be able to recover 250 files, perhaps. With a maximum size of 100KB. And only on Tuesdays. You know how it works.
Lazesoft Recovery Suite Home Edition is refreshingly different. Okay, it’s strictly for non-commercial use, but aside from that the only notable missing feature is one you won’t find in most of the competition, anyway (HFS+ file system data recovery).

The billion dollar Carbanak bank heist could have been easily avoided
This month, the $1 billion bank heist affecting up to 100 financial institutions has highlighted a growing gulf of miscommunication between chief executives of large organizations and their IT departments.
Kaspersky Lab reports that, working with international law enforcement agencies Interpol and Europol, it discovered that the gang, dubbed Carbanak, used malware enabling it to see and record everything that happened on staff’s screens. These and other recent high profile cyber-attacks, such as that which recently saw 76 million customer accounts hacked at financial institution JPMorgan Chase, are forcing organizations such as banks to examine why cyber criminals see them as easy pickings. Some are rapidly reaching the conclusion that they need to plug any security holes not only in their own networks but also in those of their advisers and partner companies.

The next Linux kernel is Linux v4.0, codename 'Hurr durr I'ma sheep'
In the spirit of democracy, Linus Torvalds recently started a poll on Google+ to decide on the version number of the next Linux kernel. Should it be Linux v3.20 or Linux v.4.0? Well, the people have spoken, and Torvalds has listened -- albeit somewhat reluctantly.
With 56 percent of the vote, v4.0 came out on top, so that's what the next version will be called. Torvalds made the revelation at the same time as announcing the availability of Linux 4.0-RC1. Oh... and it's codenamed "Hurr durr I'ma sheep".

Old threats still dominate the security landscape
Most of the biggest IT security risks aren't new but are threats that have been around for years or even decades.
This is one of the findings of the latest HP Cyber Risk Report published today which looks at pressing security issues facing enterprises during the previous year and indicating likely trends for 2015.

How to choose an operating system for a virtual private server
Internet technologies have penetrated into all areas of our life and changed it dramatically. With their help, people are able to implement most of their activities from reading favorite books and newspapers, communicating with each other, playing online games to booking tickets and buying particular products and services through their desktops, smart phones and tablets. As the number of online users has increased, plenty of different businessmen and even large companies and corporations have decided to move their ventures into Internet to get additional revenues. This technique appeared to be one of the most effective and lucrative, as it allows to find new customer segments and promote business projects in a short period of time.
Currently, the online business environment is full of various websites, which try to attract client's attention by a pleasant look, useful customer services and loyalty programs. However, website owners forget that a significant part of future success depends on a hosting plan they use for their online business activity. The more powerful your server is, the more high-speed and accessible your website will be, what will help you build strong relationships with your visitors for many years to come.

Despite hack by NSA and GCHQ, Gemalto's SIM cards are safe, says the company
Gemalto, the world’s largest producer of SIM cards, which made headlines last week for reportedly gettings its encryption keys stolen by the mighty NSA and GCHQ spying agencies, says its SIM cards, as well as banking cards, passports and other products are secure, a conclusion it reached after conducting a round of initial investigations.
The Intercept published a detailed report last week based on confidential documents it gleaned from whistleblower Edward Snowden, in which it revealed that America’s NSA and UK’s GCHQ hacked the systems at Gemalto to steal the encryption keys. By getting access to the keys, the agencies were able to directly tap phone calls, and monitor messages, among other things, on millions of mobile phones.

Here's our best look yet at Samsung Galaxy S6
Samsung has not yet officially announced the successor to Galaxy S5, but we all know that the wait is almost over. The unveiling is scheduled for March 1, during the first Unpacked event of 2015. What we do not yet know is what the new device looks like.
So far, teasers have only given us vague details about its appearance, as Samsung has tried to keep as much as possible for the main event. However, T-Mobile has decided to expose more of Galaxy S6, releasing a teaser which shows the side of the upcoming smartphone quite clearly. And it looks awesome.

LG launches mid-range Magna, Spirit, Leon and Joy Android phones
Mobile World Congress (MWC) kicks off next week, but ahead of the big event LG announces a quartet of mid-range Android handsets. Each of the four phones runs Android 5.0 Lollipop and each is available in LTE and 3G variants -- the former has a metal rear cover, and the latter's is plastic.
The Magna, Spirit, Leon and Joy all share something of a similar look and LG describes the range as combining the "perfect balance of style and usability". At the top of the current batch is the LG Magna, which boasts a 5-inch screen, 1.2GHz or 1.3GHz quad core CPU (exact specs are region-dependent), 1GB RAM and 8GB of storage.
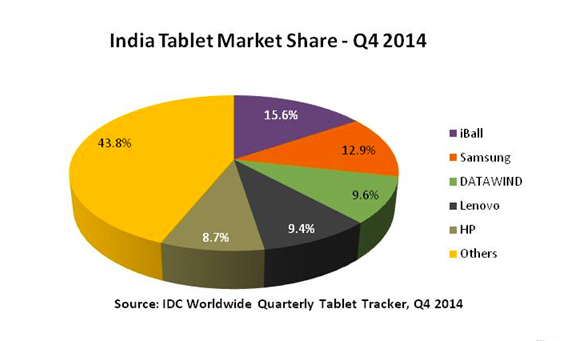
After losing the top spot in India's smartphone market, Samsung gets robbed in the tablet category too
It’s not only the smartphone market in which Samsung has lost the pole position, but tablets as well. The South Korean media conglomerate is no longer the largest tablet vendor in India, the emerging market for digital devices where the tablet share grew by 3.6 percent quarter-on-quarter, reports IDC.
As per the stats provided by the marketing research firm IDC, Indian OEM iBall captured the maximum market share (15.6 percent) in the country last quarter. Samsung managed 12.9 percent share, and was followed by Datawind with 9.6 percent share, Lenovo with 9.4 percent share, and HP with 8.7 percent market share.

Apple's new €1.7 billion European data centers will power cloud services
Colder regions make great places for building data centers. Operators can leverage the colder air outside to cool those hot servers, without relying much on costly tools like air conditioners and the like. When we're talking about thousands of servers all running in the same place, the savings are substantial. And so is the positive impact on the environment, thanks to a healthy decrease in energy requirements and emissions.
It should come as no surprise that Apple has announced Denmark and Ireland as the locations of choice for its two new European data centers. The two countries are also favored by other players in the tech industry, like Google and Microsoft. Apple's new data centers will power online services for European customers.
Windows 10 build 10022 screenshots leak along with 10014 release notes
It has been a few weeks since Microsoft released the Windows 10 Technical Preview Build 9926, and Windows Insiders are now champing at the bit for the next version. Mobile users have been kept happy with the release of Windows 10 Technical Preview for Phones, but desktop and laptop users now have some more snippets to whet their appetites.
Over the weekend, screenshots from a couple of new builds were leaked online by the renowned Wzor. First of all we were treated to a glimpse of build 10014, and shortly afterwards images of Windows 10 Professional Technical Preview Build 10022 appeared. Another revelation is a set of release note relating to build 10014. So what do we have to look forward to?

Lenovo's Superfish fiasco has badly damaged consumer trust
Stories about potentially malicious software emerge practically every day, but it’s not often that a high-profile PC manufacturer admits to deliberately installing harmful files on consumer devices. However, that’s exactly what happened last week, when Lenovo was found to be pre-installing adware on its devices without the owner’s permission.
Superfish, as the adware has been dubbed, is reported to affect Lenovo units purchased between the latter half of 2014 and January this year. While its ability to insert third-party advertisements into Internet Explorer and Google Chrome searches is annoying, the way that it installs its own security certificate is invasive and possibly harmful.