
US companies dominate as banks race to adopt AI
The leading banks for AI maturity have pulled away from their peers in 2025, consolidating earlier gains and increasingly realizing ROI for their AI investments.
The latest AI Index from intelligence and benchmarking platform for AI adoption in financial services, Evident, shows JPMorganChase, Capital One and Royal Bank of Canada are the three leading banks in AI adoption.

Qualcomm is acquiring Arduino to help speed up developer access to AI
Chipmaker Qualcomm has announced that it is acquiring Arduino. Best known for its Arduino boards, the Italian firm is getting a new owner for an undisclosed sum of money.
Qualcomm says that its own products will be combined with Arduino’s ecosystem, and has announced the launch of the new Arduino UNO Q, powered by the Qualcomm Dragonwing platform. This is being promoted as a joining of forces, as well as a way of speeding up developers’ access to key technologies.

Is artificial intelligence about to steal your job? [Q&A]
With artificial intelligence becoming more powerful and completing more complex tasks, the natural question being asked in the industry is if and when AI will steal human jobs.
Myths abound about AI working autonomously and eliminating the human workforce, starting with entry-level jobs. In reality, however, AI makes workers better and it works best when paired with humans -- their strategic thinking, specialized judgment, and adaptability remain irreplaceable.
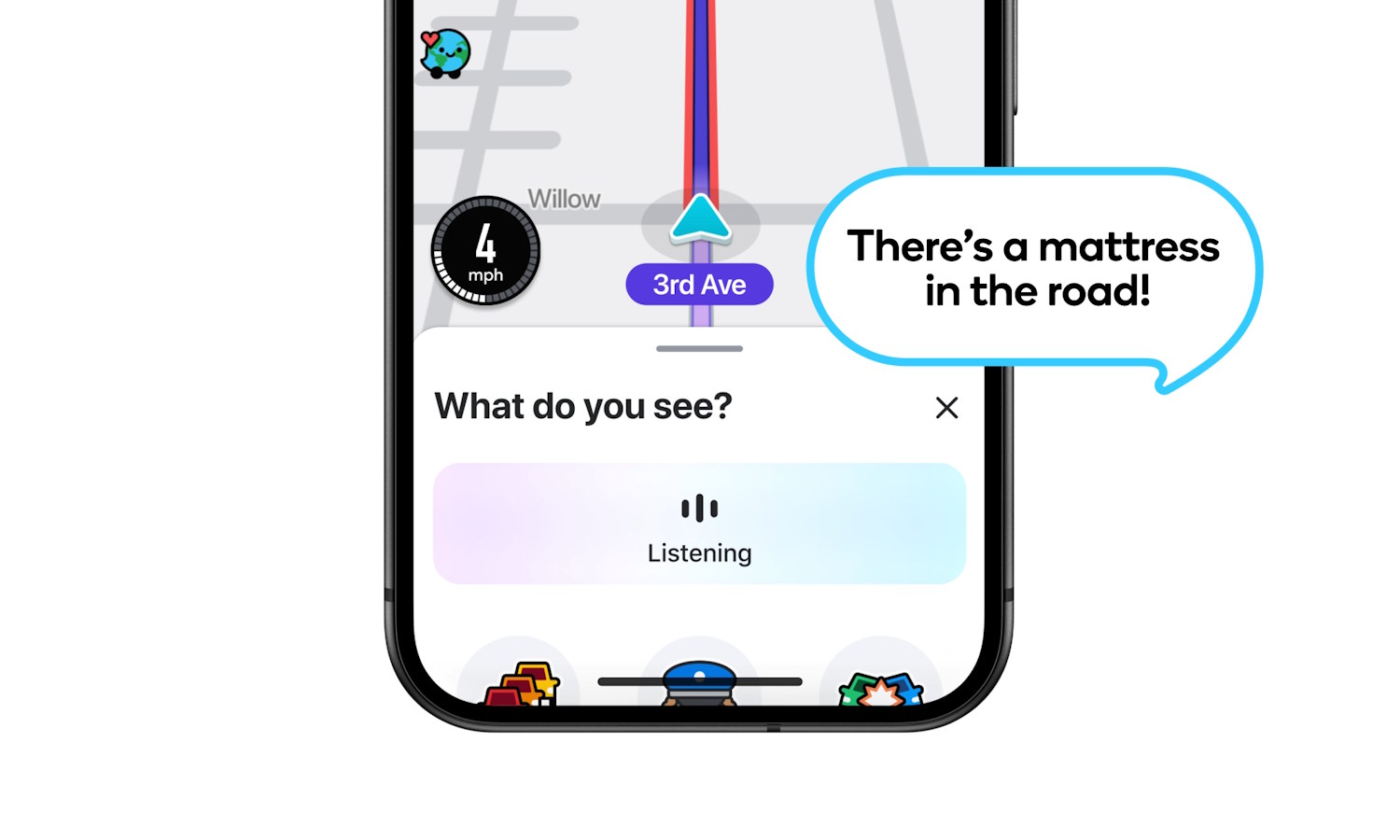
Waze is rolling out voice-controlled Conversational Reporting of hazards
Navigation tools such as Waze and Google Maps not only help you find a route from A to B, but also provide information about road closure, vehicle breakdowns, police in the area, and hazards on the road. With this last item being reliant on reports from road users, Waze has been investigating ways to make do so easier.
When you spot a hazard on the road and want to warn others, you have had to wait until you are able to stop to do so (safely, at least). Now Waze is rolling out a feature called Conversational Reporting which lets you use your voice – and a dash of AI – to let other road users know about what you have spotted.
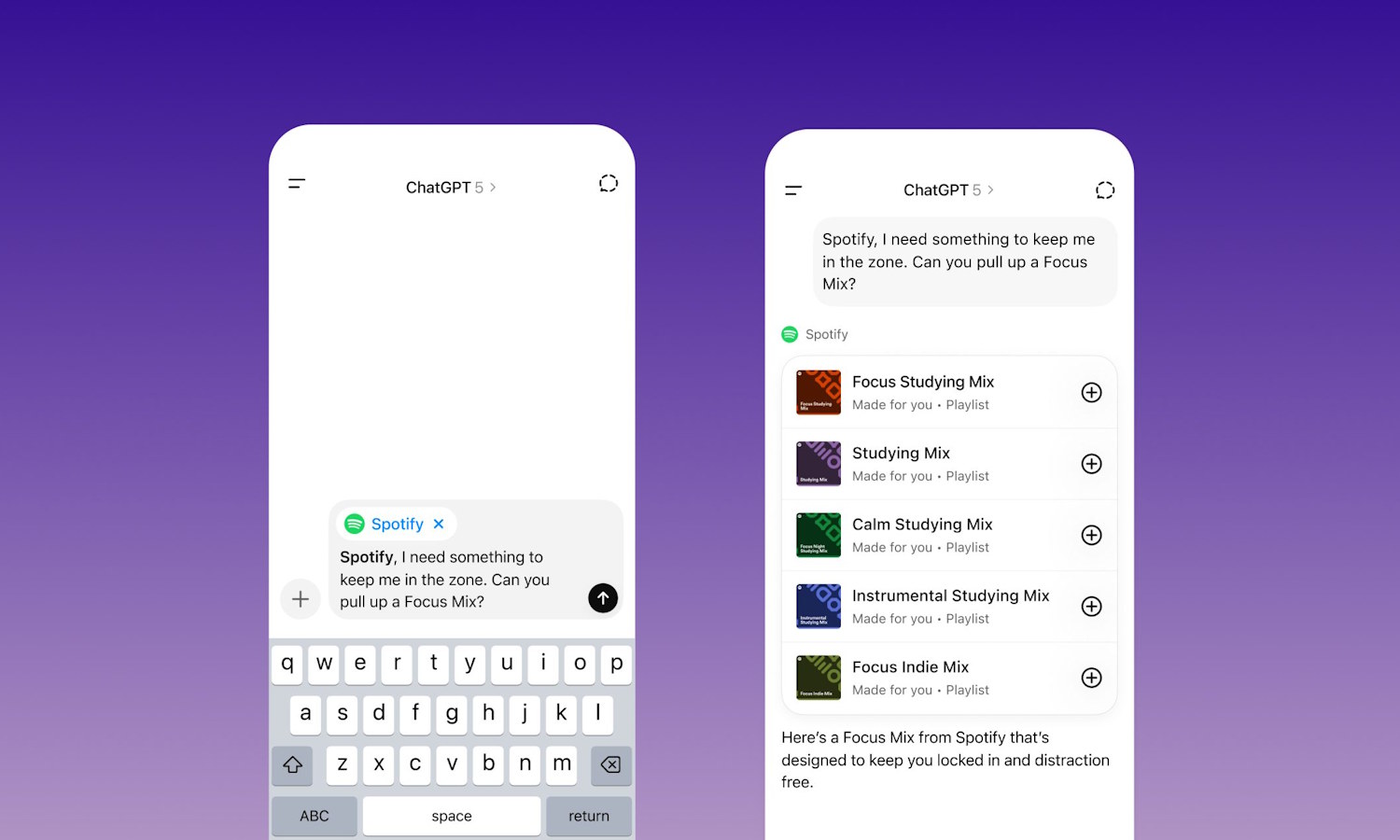
Spotify lands in ChatGPT
Thanks to what will seem like a somewhat unlikely pairing to many, it is now possible to access Spotify in ChatGPT. With the two services having partnered, you can now use tracks and podcasts to achieve things with the AI chat bot.
There are various possibilities here – from asking ChatGPT to create new playlists based on the tracks you like to receive recommendations about podcasts you may enjoy. While the ability to use Spotify in conjunction with ChatGPT is free, there are more options available to Spotify Premium subscribers.
Meta is changing Facebook’s algorithms to improve the surfacing of Reels
Meta has announced an update to Facebook algorithms which may achieve something quite rare – actually surfacing content that people genuinely want to see. The change affects Reels specifically, and users are being given far greater control over what they see in their feeds.
As well as making it easier to indicate a preference for a particular type of video – or, indeed, express a dislike for others – the update makes it possible to prioritize displaying new content. This is not the end of the story; there are also new “friend bubbles” which Meta hopes will encourage users to engage in conversations about content on the platform.

be quiet! expands its lineup with the Light Base 500 range -- sleek, quieter cases for modern PC builds
be quiet!, the German manufacturer known for making high-quality whisper silent PC components, has added two new mid-tower cases to its lineup: the Light Base 500 LX and Light Base 500.
The Light Base 500 LX offers subtle LED illumination and includes four preinstalled Light Wings LX 120mm PWM fans, three of which feature reversed blades for efficient side intake airflow. The angled slide-out fan frame directs air toward the graphics card, while additional fans can be mounted in the lowered fan bay to improve cooling.
Malwarebytes shifts to people-based protection with new security plans
Malwarebytes has introduced a new range of security packages designed to protect individuals and families based on the number of people in a household rather than the number of devices.
Malwarebytes says its research shows most users now own at least two devices, often including a smartphone, increasing the number of potential entry points for cybercriminals.

Lexar unveils ES5 Magnetic Portable SSD with MagSafe compatibility and 2000MB/s speeds
Lexar has launched a compact external drive designed for creators who need fast, reliable, and easily accessible storage. The ES5 Magnetic Portable SSD offers read and write speeds of up to 2000MB/s and attaches directly to MagSafe-compatible iPhones or other magnetic surfaces.
The ES5 comes in capacities of up to 4TB and allows users to record in Apple ProRes at 4K 120FPS and Samsung Pro Video at 8K 30FPS.
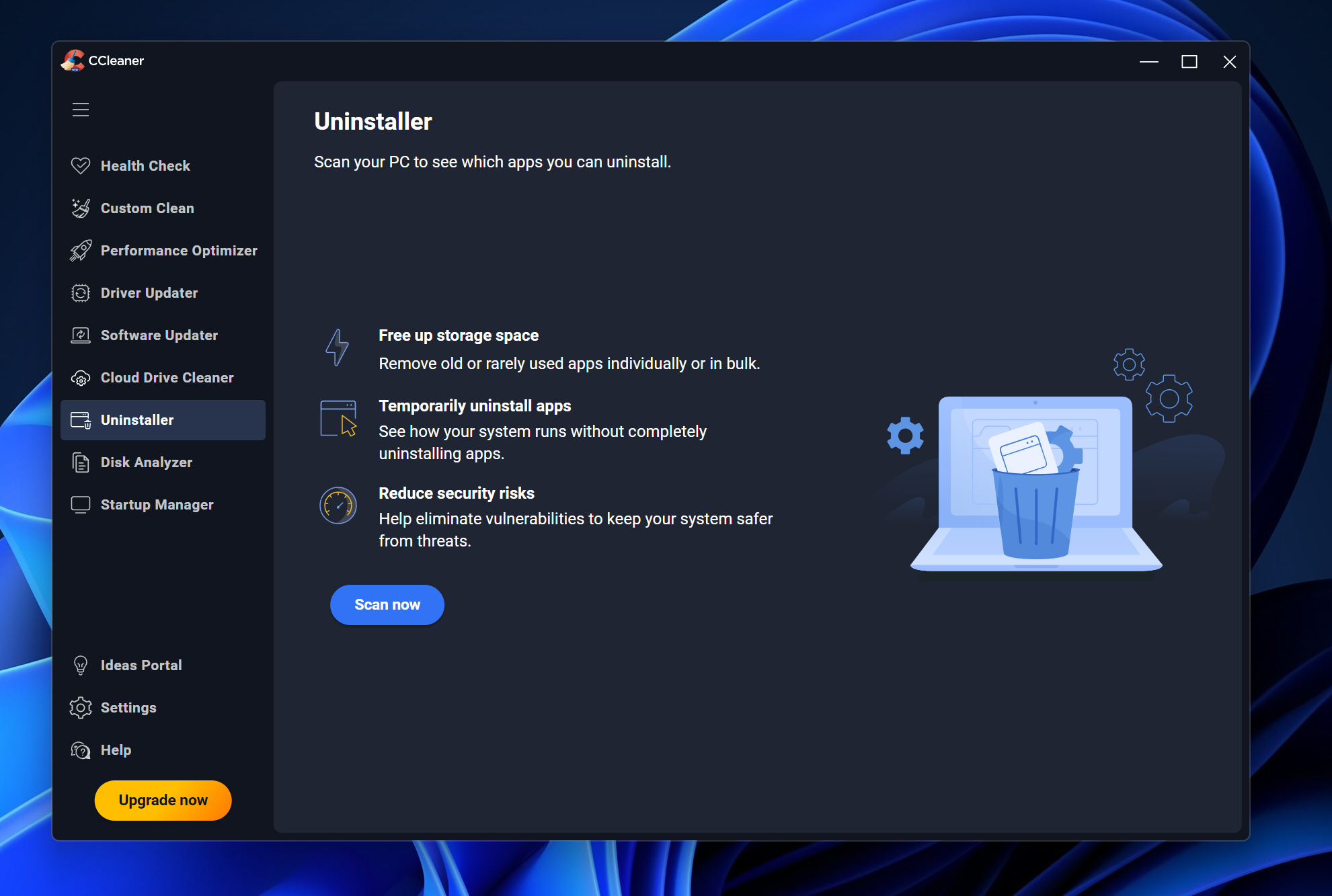
CCleaner 7 debuts with redesigned interface and smarter cleanup tools
Piriform has released CCleaner 7, the latest version of its popular PC maintenance software. Key features of this update include a streamlined interface, dark mode options, and improved cleanup tools designed to give users better control over performance and storage.
The redesigned layout offers a cleaner and more responsive experience and users can now choose between light, dark, or automatic themes.

AI assistance delivers gains for SOC analysts
Security Operations Centers are inundated with thousands of alerts each day, most of which are false positives or low-severity issues. This flood of noise leads to alert fatigue, forcing SOC analysts to waste valuable time on false alarms instead of focusing on genuine threats.
A new study from Dropzone AI looking at SOC analyst performance across 148 security analysts shows that AI can improve effectiveness. AI assisted investigations were 22–29 percent more accurate than those in the unassisted control group.

Enterprises face increasing challenges with certificate management
A report released today finds that approximately 60 percent of businesses are using three
or more secure sockets layer (SSL) providers and suggests a lack of centralized processes for SSL certificate management.
The study from domain security company CSC analyzed usage trends and patterns for more than 802,000 digital certificates linked to 2.4 million domains. It finds domain validated (DV) certificates account for three-quarters (73.4 percent) of certificates while organization validation (OV) certificates represent nearly a quarter (24.6 percent). Extended validation (EV) certificates account for less than two percent (1.9 percent).

Browsing the web with Wave Browser could help remove plastic from the ocean -- but you don't want to do that
Wave Browser, a web browser developed by Eightpoint, is introducing a new way for users to contribute to ocean conservation without changing their daily habits (beyond, you know, changing their browser).
Through a partnership with ocean cleanup company 4ocean, Eightpoint says it will fund the removal of 100,000 pounds of plastic and trash from oceans and coastlines over the next year.

Only 11 percent of US consumers trust their first search result
According to a survey of over 1,000 US consumers conducted on behalf of brand visibility platform Yext, just 11 percent trust the first tool they use when searching online, meaning nearly nine out of 10 double-check or expand their results elsewhere.
The research suggests the age of one-stop search and shop is ending and Americans are increasingly blending traditional search engines with AI tools, social media, and review sites to make purchase decisions.
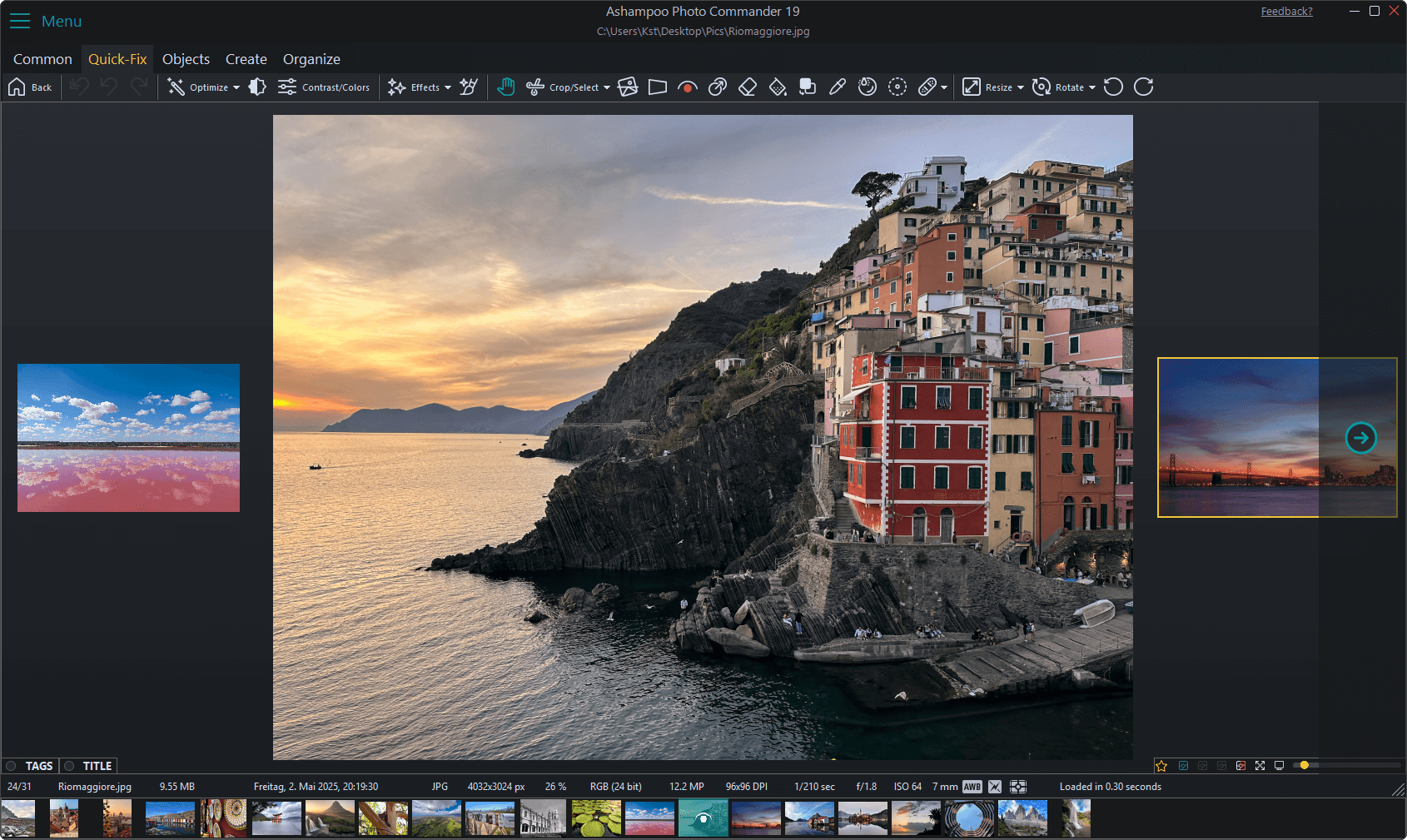
Ashampoo Photo Commander 19 arrives with improved security and format support
Ashampoo has launched Photo Commander 19, the newest version of its photo management and editing software. The update focuses on data protection, compatibility with a greater range of modern formats, and improved reliability.
Photo Commander 19 adds automatic encryption for databases, backups, and registry entries to help protect stored information. There’s also an optional screenshot protection feature to prevent unauthorized capture by external software.
