
Acer Connect Vero W6m is an eco-friendly Tri-band Wi-Fi 6E mesh router
In a world where technology and sustainability are becoming increasingly intertwined, Acer takes a significant step forward by introducing the Acer Connect Vero W6m, its first eco-friendly Wi-Fi 6E mesh router. This innovative networking solution not only offers impressive speeds and enhanced connectivity but also incorporates post-consumer recycled (PCR) materials in its construction. With a dedicated Eco mode for efficient energy consumption, Acer demonstrates its commitment to minimizing carbon footprint and fulfilling its environmental responsibility.
With Wi-Fi 6E Tri-Band AXE7800 throughput, the Acer Connect Vero W6m delivers speeds of up to 7.8 Gbps, ensuring fast and stable internet connections for all users. Furthermore, the Vero W6m can be paired with up to four units, providing impressive network ranges of up to 465m² on a dual mesh system and up to 930m² on a quad mesh system. These capabilities effectively eliminate dead spots, ensuring seamless coverage in larger areas.

Cybercriminals increasingly using legitimate websites to hide malicious payloads
A new report shows a 121 percent increase in cybercriminals using legitimate websites to obfuscate malicious payloads.
The report from Egress, based on data from its Egress Defend cloud email security solution, shows YouTube, Amazon AWS, Google Docs, Firebase Storage, and DocuSign to be the top 10 most frequently used sites.

Advanced phishing attacks grow 365 percent
A new report has identified a 356 percent growth in the number of advanced phishing attacks attempted by threat actors in 2022.
The study from threat detection specialist Perception Point also shows that the overall number of attacks increased by 87 percent.

ESG risk management: More than just a 'nice to have'
Today it seems that the issue of Environmental, Social and Governance (ESG) is being talked about everywhere and has become a key focus for enterprise management teams, especially those responsible for risk management. But is this something new, or should it be viewed as part and parcel of a mature enterprise risk management infrastructure?
One thing is for sure. ESG has important implications for a wide range of stakeholders that includes directors, investors, employees, suppliers, and employees for whom performance against ESG objectives counts.

Two-thirds of UK IT leaders think GDPR has harmed consumer trust
Five years on from the introduction of the EU's General Data Protection Regulation (GDPR), 66 percent of UK IT leaders polled in a new survey from Macro4 say the regulation has made customers less willing to trust businesses with their personal information.
On its introduction the landmark legislation was hailed as raising awareness of the need to protect personal information. Indeed a year after its introduction 36 percent of adults said it made them trust organizations more with their data.

Microsoft releases new Windows Backup app for Windows 11
Microsoft has unveiled a new backup app for Windows 11 designed to make it easier to move to a new computer, as well as speed up the process of resetting an existing PC.
Called simply Windows Backup, the app goes far beyond merely creating a backup of files. The new utility also backs up and restores system settings as well as maintaining pinned apps in the Start menu and taskbar.

Microsoft warns of intermittent failures when copying and saving files in Windows 10 and Windows 11
Microsoft has issued a warning to Windows users that saving or copying files might intermittently fail. The problem affects both Windows 10 and Windows 11, and Microsoft draws particular attention to "Document not saved" error messages in Microsoft Office apps.
While the save and copy issues are more prevalent in commercial and enterprise environments, the problems can affect all users of Windows 10 and Windows 11. There is currently no fix available, but Microsoft has offered up a slightly laughable workaround.

Thunderbird unveils a magnificent new logo
Oh, my feathery friends, have you heard the news? Thunderbird, the beloved open source email client that has weathered the storms of time, is undergoing a glorious transformation. The winds of change are blowing, and with them comes a revitalized sense of purpose and energy. As the software evolves into a more modern marvel, it's only fitting that its loyal emblem follows suit.
For years, the Thunderbird logo has stood as a symbol of reliability and familiarity, receiving small updates along the way like a fine bird preening its feathers. But now, as Thunderbird soars to new heights, it demands a logo that captures its essence and announces to the world that it's no ordinary bird.

Onboarding remote employees: Lessons learned and seven tips for success
With the arrival of COVID-19, the evolution of remote and hybrid work environments hit hyper drive, advancing to a point that many imagined would take decades to reach. For a distributed company with many offices, the chance to virtually "work where you live" had been a very attractive message. Today, what entices candidates and retains talent is being able to "work anywhere," virtually.
Yet, many CIOs, IT and engineering leaders are still sorting through lessons learned in recent years in order to adjust to this new normal -- and critical areas like onboarding technical staffers remains challenging. For me, being a year into the pandemic and noticing that not feeling that new remote engineers had a true connection to the product was a sign our processes needed updating. So, my team and I surveyed recent hires on common issues they faced when getting up to speed and how these were handled.

Introducing the Logitech G PRO X 2 LIGHTSPEED Wireless Gaming Headset
Logitech G, the gaming brand under Logitech, has just unveiled their latest creation for esports enthusiasts -- the Logitech G PRO X 2 LIGHTSPEED Wireless Gaming Headset. Crafted in collaboration with top esports athletes, this headset is poised to revolutionize gaming audio and become a must-have accessory for competitive players.
When it comes to esports, sound clarity and effective communication can be the difference between victory and defeat. The PRO-G GRAPHENE Audio Driver boasts a meticulously engineered 50 mm graphene diaphragm with a live edge suspension, delivering immersive soundscapes like never before. The improved sound reproduction accuracy, time to signal accuracy, and distortion reduction allow players to identify audio cues with exceptional precision and swiftly locate objects in relation to their position.
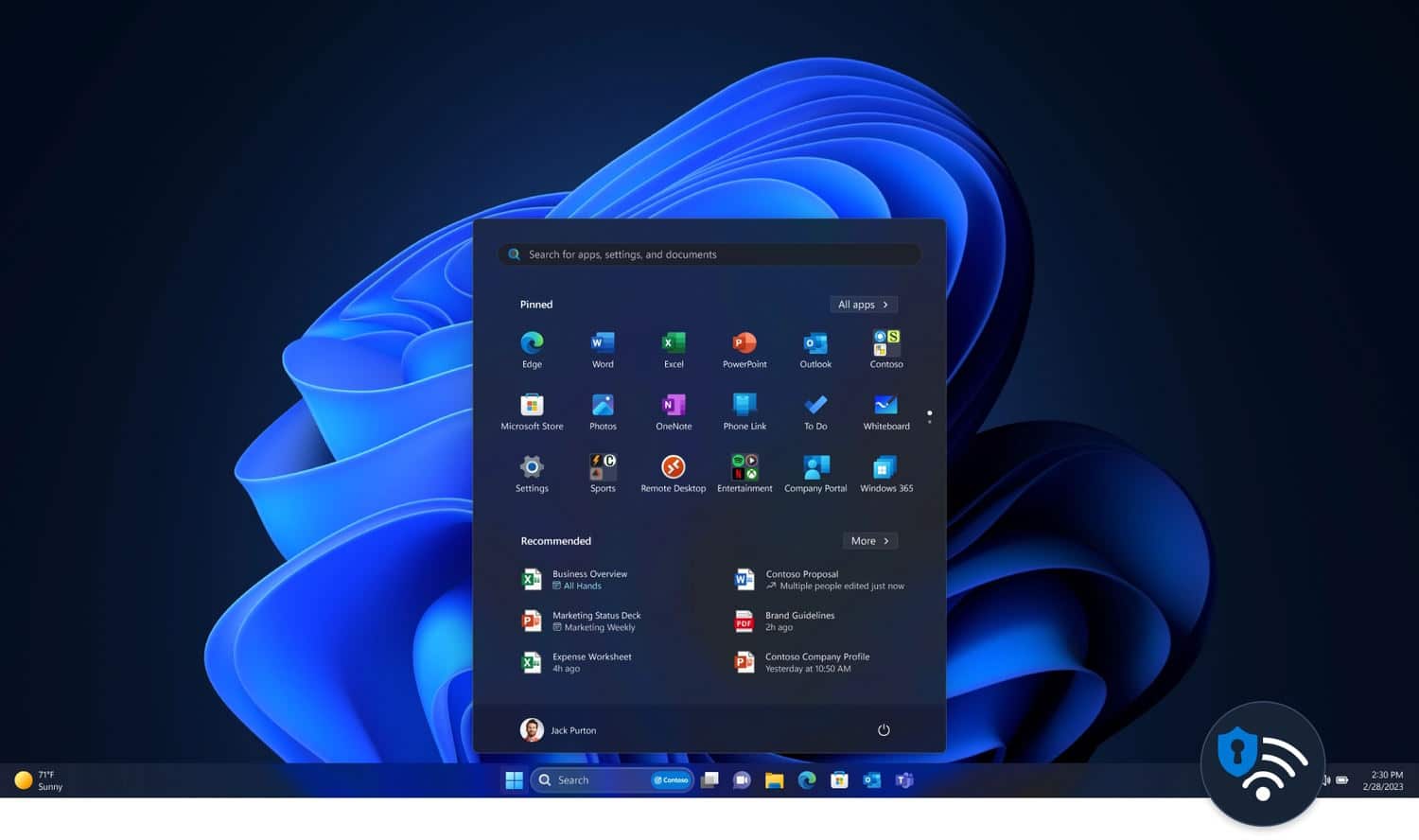
Microsoft starts the roll out of Moment 3 update to Windows 11 users
The wait for the next big update to Windows 11 is over; Microsoft is commencing the rollout of Moment 3 today -- but only for those who seek it out.
The company is making this significant update to the operating system available as part of its monthly update previews, and Moment 3 sees the arrival of an impressive number of new features and options. The update also makes significant improvements to privacy, security and accessibility options. Here's what you need to know.

Cyber insurance gets more expensive as ransomware attacks target backup storage
A new report reveals that 93 percent of ransomware attacks are now targeting backup storage as a way of ensuring payment.
The report from Veeam also shows that the success of attacks is having an impact on enterprises' ability to get insurance cover. 21 percent of organizations say that ransomware is now specifically excluded from their policies.

Half of organizations fell victim to spear phishing in 2022
The latest spear phishing trends report from Barracuda Networks shows that 50 percent of organizations studied were victims of spear-phishing in 2022, with 24 percent having at least one email account compromised through account takeover.
The report draws on a data set that comprises 50 billion emails across 3.5 million mailboxes, including nearly 30 million spear-phishing emails, as well as a survey by Vanson Bourne of IT professionals from frontline to the most senior roles at 1,350 companies.

Why AI still needs human intervention [Q&A]
There have been a number of instances lately where the line between artificial intelligence and artificial stupidity has been a pretty thin one. Microsoft's Bing insisting that we're still in 2022, or Google's Bard serving up factual errors, for example.
These problems show that human intervention is still key to getting the best from AI/ML models. We spoke to chief product officer at Tamr, Anthony Deighton, to discuss how organizations can leverage AI/ML while also keeping the key human component of the process.
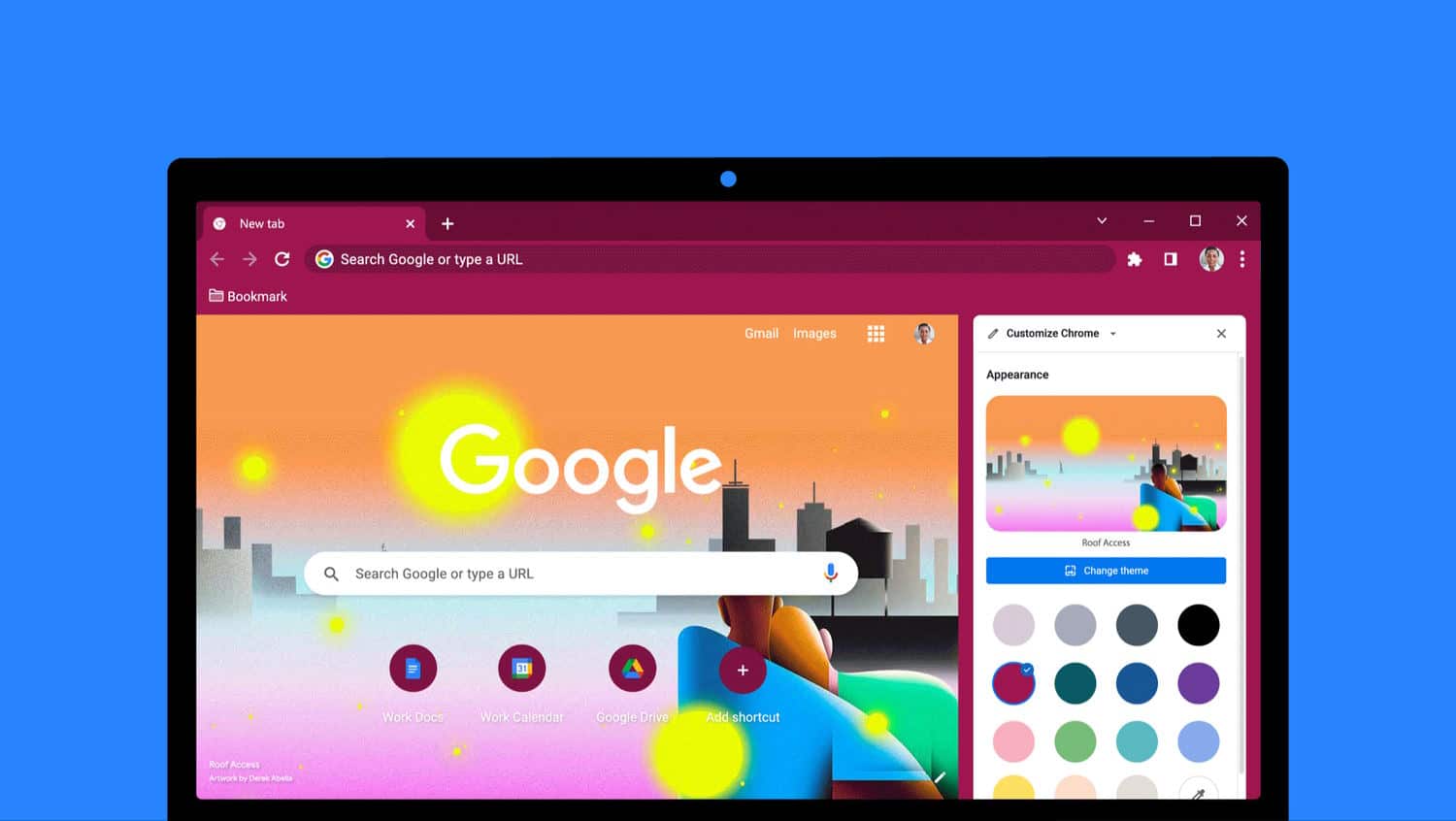
Google brings new options to Chrome so you can change the look of the browser
Google has used the latest version of Chrome to give users new ways to personalize the browser with backgrounds, themes and color schemes.
While some options, such as themes and colors, affect the entire browser, others are only visible on the New Tab page -- such as background images. Google says that it I has a wide range of "special artist collections commissioned by Asian & Pacific Islander, LGBTQ+, Latino, Black and Native American artists", and promises that more are coming later this year.
