
Chinese smartphone maker vivo takes aim at Apple and Meta with its first mixed reality headset
vivo has entered the mixed reality market with the launch of its first headset, the vivo Vision Discovery Edition. The headset enters a field dominated by Meta, Apple, and other global players, but is the first mixed reality device from a Chinese smartphone maker.
The device has been in development for four years and vivo says it is for “everyday use” rather than short demos or niche applications.
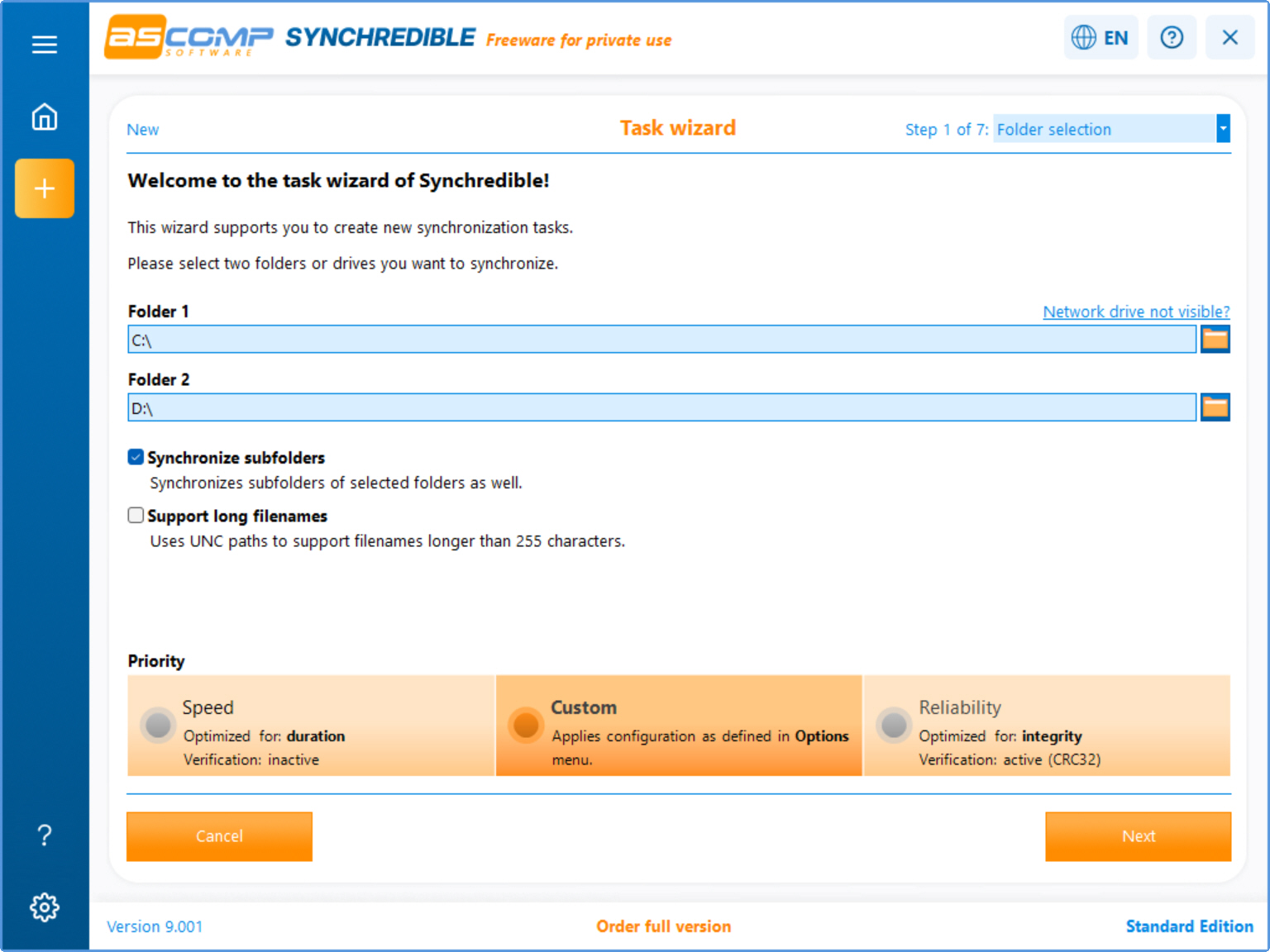
Free Windows backup and sync tool Synchredible 9 offers speed and design upgrades
Synchredible 9 is the latest version of the popular free Windows backup and synchronization tool that aims to make managing files and folders less of a chore.
The program has long been known for its flexible scheduling and detailed sync options, and this latest release brings a series of updates designed to improve speed, usability, and reliability.

Chatbots account for over 58 percent of all AI tool traffic
Over the year from August 2024 to July 2025 the top 10 AI chatbots collectively pulled in 55.88 billion visits, accounting for 58.8 percent of all AI tool traffic.
Within this group, ChatGPT is the undisputed leader, drawing 46.6 billion visits (up 106 percent year-on-year) and holding 48.36 percent of the entire AI tools market share.

Boards should bear ultimate responsibility for cybersecurity
A new State of the Security Profession survey from The Chartered Institute of Information Security (CIISec) shows that 91 percent of the profession believe ultimate responsibility for cybersecurity lies with the board and not security managers or CISOs (just 31 percent).
The survey focused on regulation in the light of a wave of major regulations either recently passed or coming into force -- including the EU AI Act, DORA, NIS2 and the UK’s Data (Use and Access) Bill.

Microsoft is still slowly chipping away at the Control Panel in Windows 11
The death of the Control Panel has been slow and painful. The long and drawn out move from the Control Panel to the Settings app started years ago, and it is still an ongoing process in Insider Builds of Windows 11.
It is not really clear why Microsoft is taking so long to migrate options across from the Control Panel to Settings, other than factoring in the idea that it is really not considered a priority. But with the release of Windows 11 Insider Preview Build 27928 to the Canary Channel this week, the Control Panel continues to be subjected to a death by a thousand cuts.
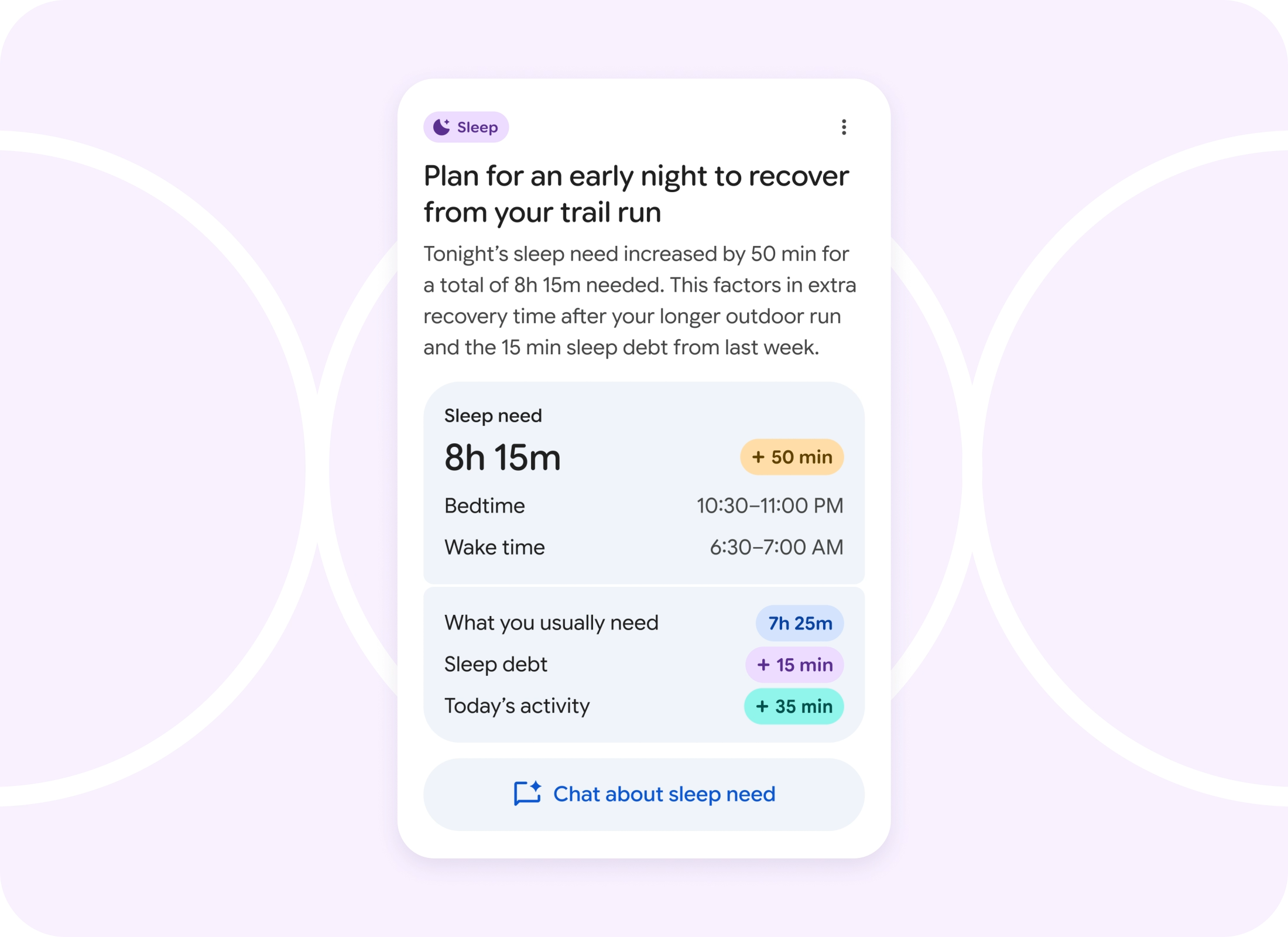
Google is bringing an AI fitness coach to Fitbit thanks to Gemini
There is nothing that technology companies will not try to enhance with AI. Google is no stranger to this with Gemini, and the company has announced an AI-powered fitness coach for the Fitbit platform.
But this is more than just a fitness coach. Google describes it as a “a fitness trainer, a sleep coach and a health and wellness advisor” all rolled into one. The aim is to be the AI coach that is suitable for everyone, so what can it do?

The challenge of moving AI from prototype to production [Q&A]
More organizations are turning to AI to assist in their digital transformation efforts, but many projects get stuck in the pilot phase.
That’s not necessarily a sign of failure though. Rather, it reflects that AI is still in its formative stage, with its most transformative impact still ahead. We spoke to Nadav Eiron, SVP of cloud engineering at Crusoe to learn more about how AI can transition from experimentation to integration, and from potential to permanence.
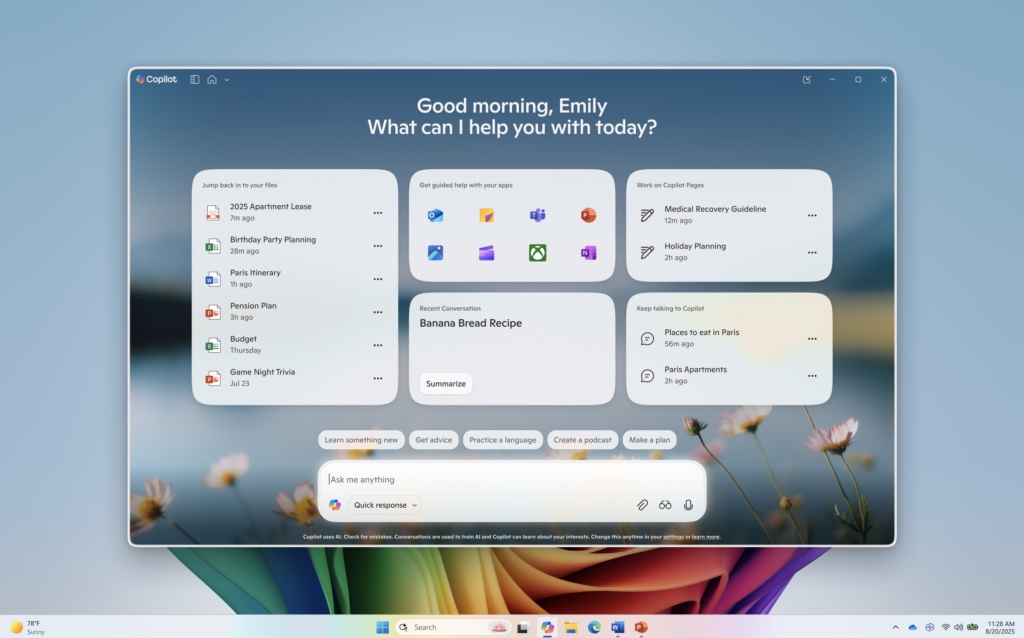
Microsoft gives Copilot on Windows another new look
Microsoft could be accused of many things in relation to Copilot on Windows, but standing still is not one of them.
Both in terms of functionality and design, the company seems to be constantly at work and this is something that is evident in the latest Insider build of Windows 11. Microsoft is rolling out new features such as Semantic Search, and also a completely redesign home page for Copilot on Windows.

Google releases Password Manager app
Whether you have been waiting for it or not, Google Password Manager is now available as a standalone app for Android users.
Breaking the Password Manager component out of the Chrome browser is an interesting move. There is no real reason for Google doing so other than making it slightly easier to access saved passwords and usernames.

Insider threats become more effective thanks to AI
Artificial intelligence is making insider threats more effective according to a new report which also shows that 53 percent of respondents have seen a measurable increase in insider incidents in the past year.
The survey, of over 1,000 cybersecurity professionals, from Exabeam finds 64 percent of respondents now view insiders, whether malicious or compromised, as a greater risk than external actors. Generative AI is a major driver of this, making attacks faster, stealthier, and more difficult to detect.

87 percent of organizations are turning to AI-powered SOC tools
A new survey from Gurucul in collaboration with Cybersecurity Insiders finds that 87 percent of respondents are deploying, piloting or evaluating AI-powered SOC tools, but only 31 percent are using them across core detection and response workflows.
The study, based on responses from over 700 cybersecurity leaders around the world, finds human and identity risks are still a major concern. 78 percent of security leaders identify social engineering and phishing as their top threat, followed closely by identity-based attacks (73 percent). However, 67 percent say they still lack visibility into access behavior and lateral movement.

Employee distraction is a bigger risk than attack sophistication
Cybersecurity professionals are sounding the alarm, not about increasingly sophisticated cyber threats, but about something far more human -- distraction.
New research from KnowBe4 shows distraction (43 percent) and lack of security awareness training (41 percent) are identified as the primary reasons employees fall victim to cyberattacks, rather than sophistication of the attacks themselves.
OtterBox launches new Pixel 10 case lineup with Pixelsnap charging support
OtterBox has introduced a lineup of cases designed for the newly launched Google Pixel 10 family, announced yesterday.
The range includes the Symmetry Series, Defender Series Pro XT and Thin Flex Series, each built with integrated magnets to support Google’s new Pixelsnap wireless charging system.
Forget Windows 11, Windows 12.2 is the 'next evolution' of Microsoft's OS
Windows 10 is set to reach its end of life in just a couple of short months, which means Microsoft will stop providing free security updates and official support for the beloved operating system. Although extended security updates will be available for a fee, most users will soon be faced with a stark choice: upgrade to Windows 11, switch to Linux, or wait for the long-rumored Windows 12.
The retirement of Windows 10 unquestionably marks a major shift in the PC landscape. Microsoft is pushing its customer base towards a newer, AI-enhanced Windows experience -- whether they are fully ready for it or not.
Pixel Buds 2a debut with active noise cancellation and Gemini AI
The final new launch from Google today, following the Pixel 10, Pixel 10 Pro Fold and Pixel Watch 4, is Pixel Buds 2a. These new A-series earbuds bring Active Noise Cancellation, immersive audio, longer battery life and Gemini AI at a more affordable price. Preorders start today, with general availability on October 9.
Google says the Pixel Buds 2a have been redesigned for comfort and stability. They are smaller and lighter than the previous A-series and take inspiration from the Pixel Buds Pro 2 design.
