
Hardware manufacturer recommends not upgrading to Windows 11 because of printer problems
There was a spate of printer problems affecting Windows over the last few months, and with the release of Windows 11 the situation does not seem to be improving. Microsoft has already acknowledged various issues with the latest version of the operating system, and now another problem has reared its head.
Some printer owners have found that that Windows 11 throws up an error message when they connect the peripheral via USB. While Microsoft is yet to say anything about the issue, there is advice from printer manufacturer Brother -- including avoiding Windows 11.

Microsoft releases KB5006674 update for Windows 11 to fix networking problems and more
It's now a week since Microsoft started the rollout of Windows 11, and the latest version of the operating system has just received its first cumulative patch.
With the release of the KB5006674 update, Microsoft is addressing one of the compatibility issues that was preventing some people from upgrading to Windows 11. Taking the Windows 11 version number up to 22000.258, the update fixes issues found between the operating system and some Intel networking software.

The changing face of digital identity verification [Q&A]
As we've grown more and more reliant on the internet to carry out everyday transactions, proving who we are has become a major issue.
We are still heavily dependent on IDs, passwords and supplementary security questions, but all of these are open to abuse leading to the risk of identity theft.
Microsoft releases PowerToys v0.47.1, fixing bugs in FancyZones and more
With the current PowerToys release cycle, Microsoft had vowed to work on stability and optimization, and the company is making good on this promise.
It is only a couple of weeks since the release of v0.47.0 of the utility collection, but now there is another update to install. This time around, there are fixes for PowerToys Run, FancyZones and Shortcut Guide.

NETGEAR AXE11000 Orbi Quad-Band Wi-Fi 6E Mesh System (RBKE963) is expensive AF
Regular Wi-Fi 6 (802.11ax) is great, but Wi-Fi 6E is even better -- that's why many consumers wisely skipped Wi-Fi 6 and stuck with Wi-Fi 5 (802.11ac) a bit longer. But wait, what exactly is the difference? Does that letter "E" really matter? Actually, yes, because it indicates the use of a 6GHz band -- a much-less crowded frequency compared to 2.4GHz or 5GHz. This extra bandwidth, lower latency, and reduced congestion is why Wi-Fi 6E is so exciting.
To truly take advantage of this new standard, you will need both a router and clients with the capability. Today, NETGEAR announces the most exciting Wi-Fi 6E system yet. Called "AXE11000 Orbi WiFi Mesh System (RBKE963)," it is a quad-band system consisting of a Wi-Fi 6E router and two 6E satellite access points. It is designed to blanket even excessively large homes with cutting-edge wireless networking. Sadly, it carries a shockingly high price tag -- this mesh system is expensive AF!

StarTech.com launches Bluetooth 5.0 Audio Receiver with NFC
If your stereo receiver or speaker system lacks Bluetooth connectivity, what should you do? Throw your existing stereo gear in the trash and buy something new with the wireless standard? I mean, I suppose you could, but that would be idiotic. Instead, you can simply add Bluetooth with a dongle.
Yes, such adapters exist, allowing you to add Bluetooth connectivity to wired speakers and stereos. Best of all, they are typically very simple to use. Today, StarTech.com launches a new such dongle, and it looks to be rather premium. Called "Bluetooth 5.0 Audio Receiver with NFC," not only does it offer analog connectivity, but optical output too. It even features 48KHz/24 bit sample rate support.
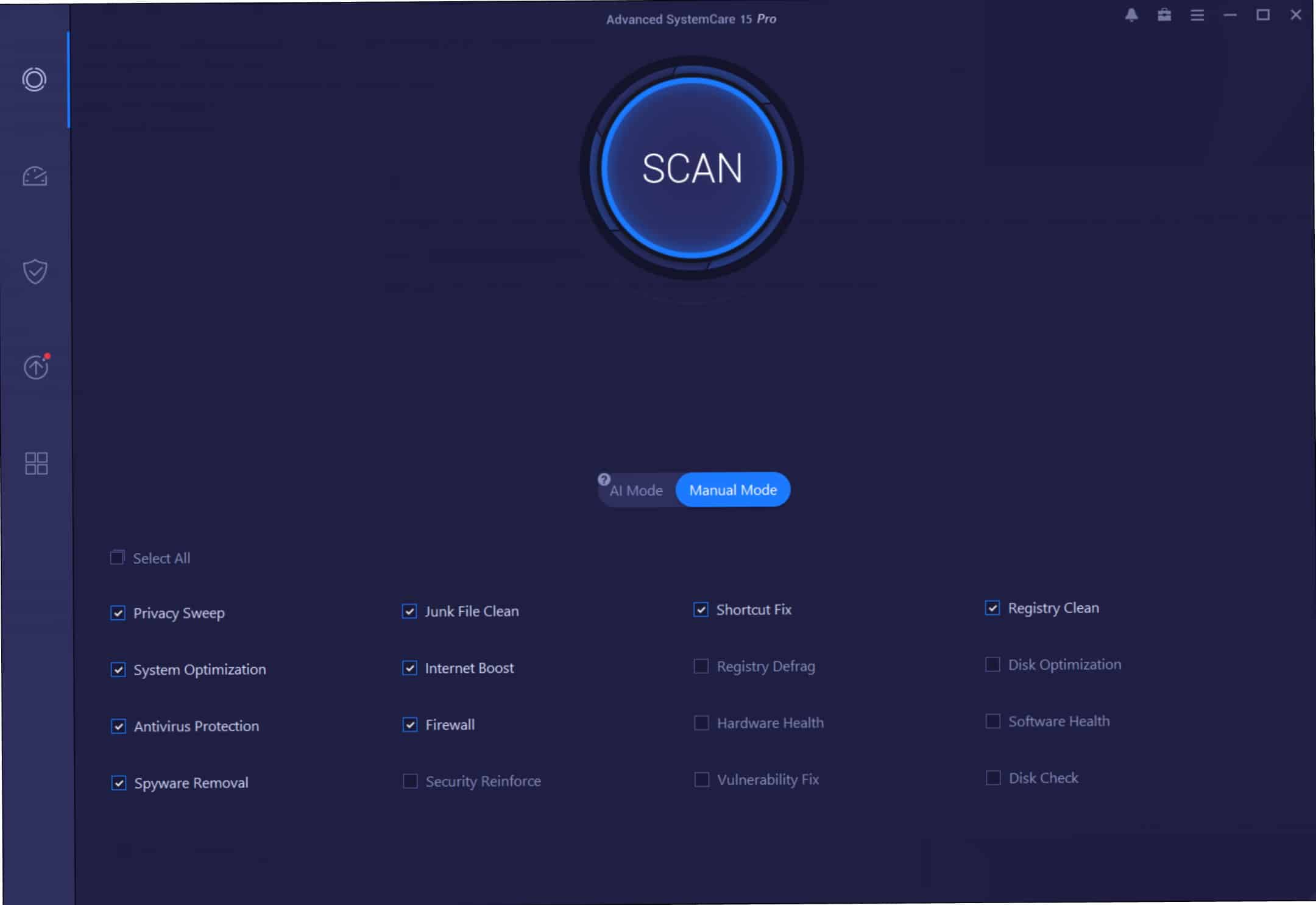
IObit Advanced SystemCare 15 is here to clean and optimize Windows 11
There is a lot to think about when it comes to maintaining the performance of your computer -- so much so that it can become an all-consuming task. If you would rather spend your time using and enjoying your PC, you should delegate the job of optimization and cleanup to a third party. And this is precisely where IObit Advanced SystemCare 15 can help you out.
The latest version of this incredible free collection of utilities adds support for Windows 11, but this release is about more than just working with the latest version of Microsoft's operating system, There is an improved cleanup component that can tidy up after a larger number of applications than ever before. There is also smart AI that not only makes the software faster and more efficient than ever, but also means that it is incredibly easy to jump into and start using straight away.
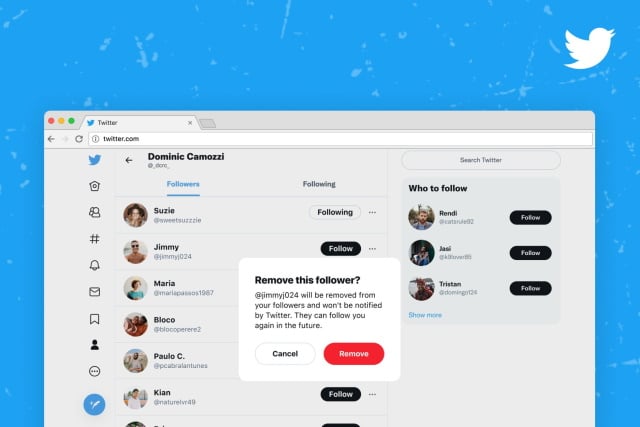
Now you can ditch your irritating Twitter followers without blocking them
A problem that has long troubled social media users is the etiquette surrounding blocking people. While there are certainly some people you would have no qualms about blocking in a heartbeat, there are times when this could be, well... awkward.
And so Twitter has come up with a solution. Known as a "soft block", the option makes it possible to get rid of a follower without either blocking them or notifying them that you have done anything.

93 percent of businesses experience breaches caused by third-party vendors
A new study reveals that 97 percent of firms surveyed have been negatively impacted by a cybersecurity breach that occurred in their supply chain and 93 percent have suffered a direct cybersecurity breach.
The third-party cyber risk survey form BlueVoyant also shows the average number of breaches experienced in the last 12 months grew from 2.7 in 2020 to 3.7 in 2021 -- a 37 percent year-on-year increase.

Enterprises move to software-defined storage as data volumes increase
A new report from the Linux Foundation looks at enterprise use of data and storage relating to cloud services and workloads.
The 2021 Data and Storage Trends Report, produced by the SODA Foundation and Linux Foundation Research, shows rapidly growing data volumes and a shift in how they're being handled.

Google Cloud and Cybereason team up to fight cyberattacks
As the IT landscape has evolved, securing hybrid and cloud environments has become a more complex and challenging process.
To improve Extended Detection and Response (XDR) across endpoints, networks, cloud and workspaces, operation-centric cyber attack protection specialist Cybereason, and Google Cloud have today announced a collaboration.

Kubuntu Focus XE is the perfect laptop for Windows-switchers and Linux beginners [Review]
All Linux distributions are not created equally. In other words, it is absolutely not correct to say "Linux is Linux." Not only are there differences under the hood with things like package managers and kernel versions, but more user-focused variations too, such as the actual desktop environment. Unlike Windows that only offers one interface, there are several for Linux-based operating systems. Ultimately, a user's Linux experience can vary wildly based on distro.
But what Linux distribution is best for a beginner? This is an impossible question to answer definitively, but to attempt to do so, it is important to first define what a "beginner" actually is. Are they a first-time computer user or more likely, a longtime Windows user looking to switch to Linux? While the former is a blank canvas, the latter has many existing computing habits and expectations. And so, looking for something that doesn't deviate far from the traditional Windows user interface.

Get 'DearMob iPhone Manager' for Windows/macOS ($69.95 value) FREE for a limited time
DearMob iPhone Manager, from Digiarty (WinXDVD), is an easy to use program that lets you transfer, manage, backup and restore your iPhone or iPad.
If you’re always running out of space on your Apple device, you can use this tool to quickly manage your storage, and it’s available for both Windows and Mac.

OpenSilver picks up where Silverlight leaves off
Let us pause for a moment to remember Microsoft Silverlight. The web application framework and alternative to Flash and Java reaches the end of its support life today.
Whilst it never had the market penetration of the others, Silverlight had a 15-year lifespan and in 2010 the plug-in was on over 53 percent of browsers.
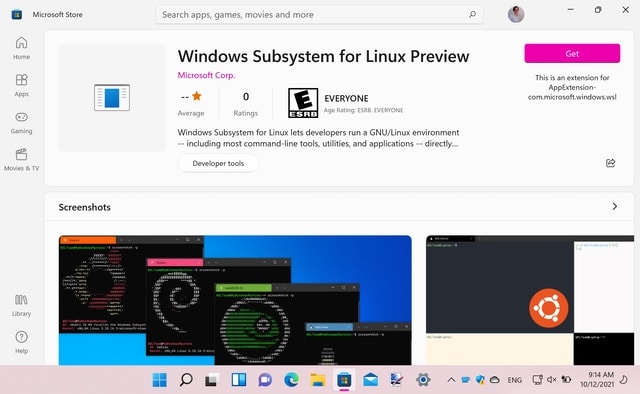
Download Windows Subsystem for Linux app from the Windows 11 Microsoft Store
Microsoft's embracing of Linux has been slow but steady, and nowhere is this more evident than with Window Subsystem for Linux -- or WSL. Now, a new WSL app has just been released to the Microsoft Store for Windows 11 users.
With this latest release, the company is bringing Windows Subsystem for Linux to a much wider audience. Previously only available as an optional component of Windows itself, in launching a separate WSL app, Microsoft is massively increasing the visibility of the much-loved tool.
