
Existing security tools struggle with public clouds
The security of public clouds continues to be a major challenge, with 75 percent of respondents to a new survey saying they are 'very' or 'extremely' concerned about it.
The study from Check Point and Cybersecurity Insiders shows 68 percent say their organizations used two or more different public cloud providers, which means that security teams often have to use multiple security tools and management consoles to try to enforce security and compliance across the different environments.

Mageia 8 Beta 1 Linux distro now available with KDE Plasma, GNOME, and Xfce
Development of Mageia 8 seems to be progressing nicely, which is good news for fans of the Linux-based operating system. Last month, we shared that the first Alpha of the distribution was available for testing, and now today, the first Beta arrives.
As with the Alpha, the Beta is available with your choice of three desktop environments -- KDE Plasma, GNOME, and Xfce. All three are available in 64-bit Live ISO images, but the 32-bit variant of the operating system is limited to Xfce only. This makes sense, as 32-bit-only computers in 2020 are quite ancient and under-powered, while Xfce is the most lightweight DE of the bunch.

Have I Been Pwned will finally open source its code base
Have I Been Pwned is unquestionably the best way to discover if your email address has been leaked in a data breach. The site can also check any passwords you use to see if they appear on the web and it can be fun entering some common choices to reveal how often they’ve been leaked. "Password", for example, has appeared in data breaches 3.7 million times, while "123456" crops up a whopping 23.5 million times.
The service is used in numerous third-party tools too, including Spybot Identity Monitor and 1Password. Have I Been Pwned is the work of Troy Hunt, and after failing to sell it earlier in the year, he has decided to take the step of opening source the code base in a quest for a more sustainable future.

OWC Rover Pro is a more affordable set of wheels for Apple Mac Pro
Apple's Mac Pro (2019) desktop computer is beautiful, elegant, powerful... and very expensive. For the Apple faithful, overpaying for hardware is par for the course. After all, if you love macOS, you don't really have much of a choice beyond building a Hackintosh. But even some of the biggest Mac fans balked at the $700 asking price for the Apple Mac Pro Wheels Kit -- a set of four wheels to make the desktop more portable in an office setting. Seriously, folks, the company charges $175 per wheel!
Thankfully, popular Apple-focused third-party seller OWC has decided to roll out (pun intended) a more affordable set of wheels. Called "Rover Pro," it is currently just $199. That is only $50 per wheel, which is much more reasonable. Best of all, unlike the Apple Mac Pro Wheels Kit which requires a special flexible screwdriver (that you must buy separately), OWC's offering utilizes a toolless design.

What's small, blue and protects your network? Firewalla! [Review]
The current shift towards remote working has shone a spotlight on the security of home networks and the potential risk they present to corporate information.
While there are various software options you can employ to offer more protection, Firewalla has a different solution in the form of a tiny box that you plug into your router.

Windows 10 has a dangerous print spooler bug, and there is no fix
An unpatched vulnerability in the Windows Print Spooler exists that could be exploited by an attacker to run malicious software with elevated system privileges.
The issue affects Windows 7, Windows 8.x, Windows 10 as well as versions of Windows Server. It is being tracked as CVE-2020-1048 and CVE-2020-1337 and has a severity rating of "Important". Despite having been acknowledged by Microsoft back in May, a working patch is yet to be rolled out.

Emotet returns to top the malware charts after a five month break
Following a five month absence, Emotet has returned to number one spot in the malware charts in the latest Global Threat Index for July from Check Point Research.
Since February 2020, Emotet's activities -- primarily sending waves of malspam campaigns -- started to slow down and eventually stopped, until re-emerging in July. This pattern echoes 2019 when the Emotet botnet ceased activity during the summer months but resumed in September.

How a software company has innovated its way out of lockdown [Q&A]
Lockdowns have presented a challenge for all businesses and it's clear that some have handled the situation better than others.
We sat down with Neil Everatt, CEO of Selenity to discuss how the business has been coping during lockdown and what changes to productivity and innovation he’s seen.

Linux in education: ViewSonic donates 300 Raspberry Pi devices to students
There is a lot of negativity in the world these days such as the COVID-19 pandemic, record unemployment, and the massive explosion in Beirut, Lebanon. Sometimes it can feel like positive news doesn't exist anymore. The truth is, good news is always happening, but it isn't always reported.
Well, today we are happy to report a feel-good story. Popular company Viewsonic, known for manufacturing high-quality computer displays, is donating 300 Raspberry Pi thin clients to the Los Angeles County Alliance for Boys and Girls Clubs. These little computers are a great tool for teaching kids about Linux.

COVID-19 has minimal impact on software quality assurance teams
The pandemic hasn't caused too much disruption for quality assurance teams according to a survey from software testing company Kobiton.
There have been issues though ranging from team collaboration and communication to alignment with other DevOps teams. 40 percent of respondents report minor disruptions to their QA processes, and 33 percent say they’ve experienced minor delays in their product release cycles.

Attackers bypass multi-factor authentication to hijack email accounts
Researchers at Abnormal Security have detected an increase in business email compromise attacks that successfully compromise email accounts despite the use of multi-factor authentication (MFA) and Conditional Access.
This is possible because legacy email protocols, including IMAP, SMTP, MAPI and POP, don't support MFA. In addition many common applications -- such as those used by mobile email clients (for example, iOS Mail for iOS 10 and older) -- don't support modern authentication.
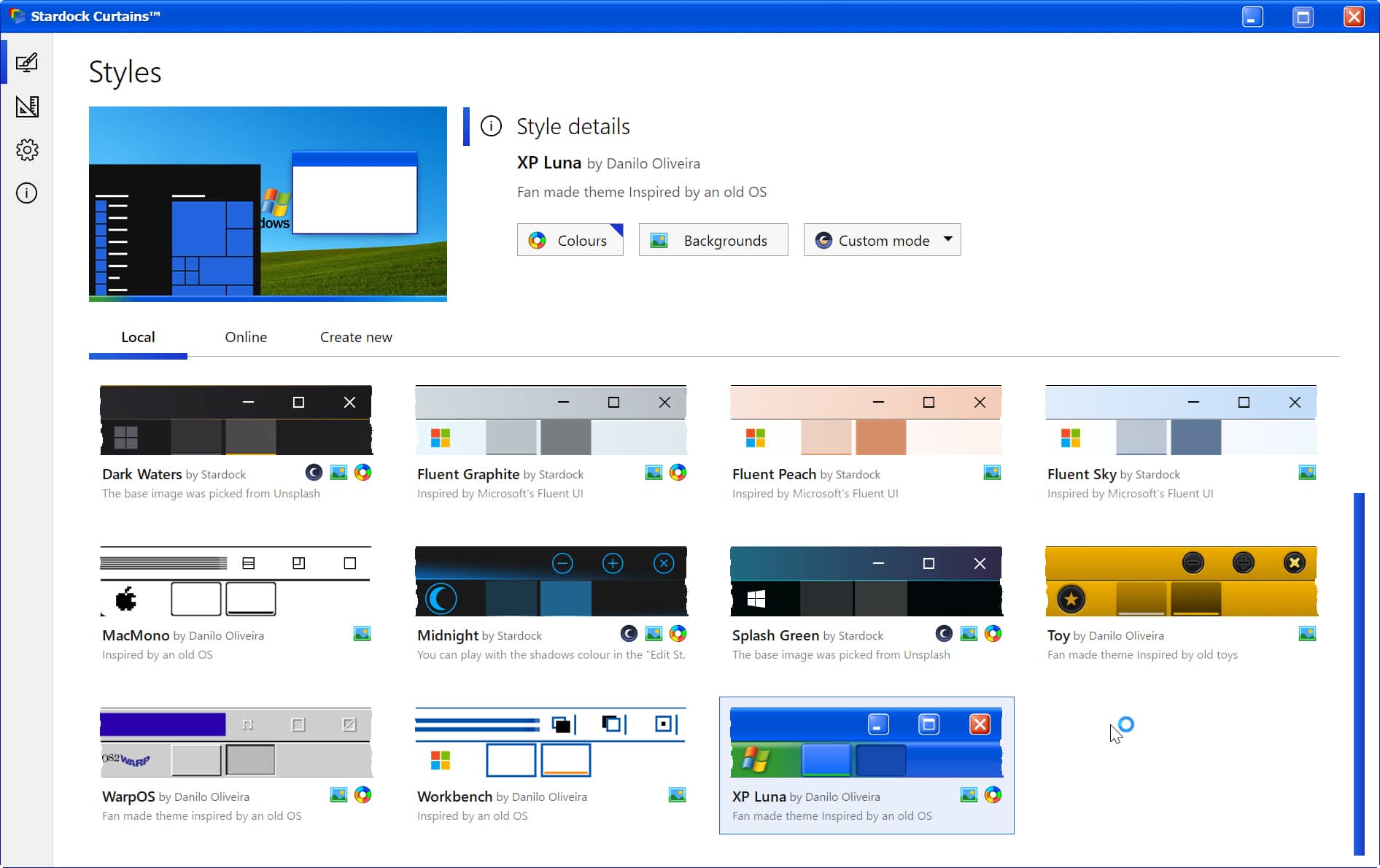
Add new style modes to Windows 10 and give it a Windows XP or Mac OS makeover
Windows 10 currently lets you choose from two styles -- Dark Mode and Light Mode -- which you can enable and switch between in the Settings > Personalization section of the OS.
If you’ve ever wished for access to more style modes than that, then you’ll be interested in a new app which lets you customize Windows with additional styles, and can even give Windows 10 a convincing retro makeover.

The future of endpoint management [Q&A]
It's frequently the case that the weakest part of any business network is the endpoints used to access it. A problem that's only been exaggerated by the shift to remote working driven by the coronavirus pandemic.
What can businesses do to improve their endpoint management and keep their data secure? We spoke to senior technical product manager Richard Melick at cloud-based device management specialist Automox to find out.

Microsoft releases Windows 10 Build 20185 to the Dev Channel with improved DNS configuration
Microsoft has been introducing a few new and interesting features to its preview builds lately, including a new Start menu and improved alt-tab experience, which you can now also get on your non-Insider version of Windows 10, if you follow our instructions.
Today the software giant rolls out to Windows 10 Build 20185 to the Dev Channel (what used to be the Fast ring).

Samsung Galaxy Tab S7 and S7+ are premium Android tablets with 5G
For a while, it felt like tablets were the future of computing. Hell, Microsoft almost destroyed Windows entirely by wrongly transforming it into a tablet-first operating system with Windows 8. As we learned over time, however, laptops and desktops were not going anywhere. Microsoft thankfully righted the ship (mostly) with Windows 10. While iPad remains a popular device, Android tablets have largely dried up. Long gone are the good ol' days when Nexus 7 reigned supreme. Now, quality Android tablets are few and far between.
Thankfully, Samsung has not yet abandoned the Android tablet market. Today, in addition to new Note20 smartphones, the company revealed two new tablets -- Galaxy Tab S7 and S7+. The former has an 11-inch (2560 x 1600 120Hz LCD) screen, while the latter has a 12.4-inch (2800 x 1752 SuperAMOLED 120Hz) display.
