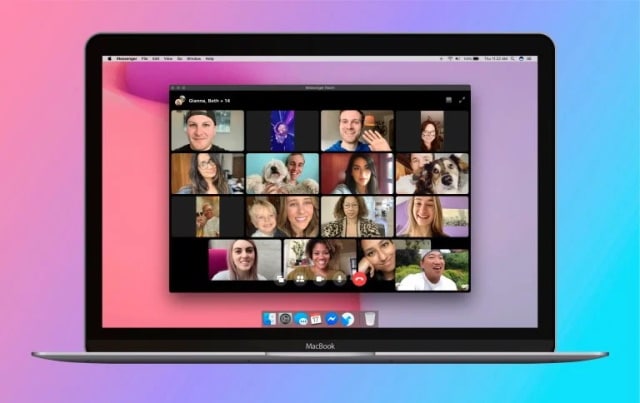
Facebook launches Messenger Rooms as an alternative to Zoom
While Zoom has been taking numerous steps to address various security and privacy concerns that have arisen in recent weeks, there are still plenty of people seeking alternatives to the video conferencing platform. Now Facebook is trying to make its Messenger tool a viable option.
With Facebook Messenger Rooms, the social media giant is giving people the option of conducting video chats with up to 50 people at a time. Unlike the free version of Zoom, there is no time limit on chats in Messenger Rooms, and as an added bonus there is no need to have a Facebook account to use it.

Audio-Technica launches QuietPoint ATH-ANC300TW Bluetooth headphones
Bluetooth headphones are no longer the future of portable audio — they are the present. Since Apple courageously killed the 3.5mm audio jack on the iPhone, and many Android manufacturers followed suit, wireless headphones have exploded in popularity. And yes, Apple AirPods are leading the trend.
The thing is, while AirPods are very popular, they aren’t necessarily the best. In fact, if you are an Android user, you should absolutely look elsewhere. Today, Audio-Technica launches its newest in-ear Bluetooth headphones, and they put Apple AirPods to shame. Called “QuietPoint ATH-ANC300TW,” they feature 4.5 hours of listening time, but the USB-C charging case adds 13.5 more. You even get replaceable tips so you can find the most comfortable fit.

IBM Cloud boosts security and productivity with Red Hat OpenShift enhancements
As businesses move to the cloud, they want choice, flexibility, and the ability to easily manage and migrate their critical workloads securely across public clouds, private clouds, and on-premise environments.
To help them achieve this IBM is enhancing the Red Hat OpenShift container platform on IBM Cloud by making OpenShift 4.3 generally available as part of its fully managed service.

Apple Music comes to Samsung TVs
Apple Music and Spotify are both great streaming music services, but the former is just a bit better than the latter. Apple’s offering has a much more intuitive user interface, and its curated playlists are second to none. Apple Music is now available on most platforms too, such as iOS, Android, Mac, Windows, and Linux — thanks to the new web client.
Starting today, Apple Music is now available on many newer Samsung smart televisions as well. This is quite remarkable, as Apple and Samsung are fierce competitors in the smartphone market. As Apple becomes more and more focused on services, however, the company is apparently becoming more open to working with former “enemies.”

Malwarebytes launches its own VPN
Well known for its endpoint protection and malware removal solutions, Malwarebytes is now moving into the online privacy space with the launch of its own VPN.
Malwarebytes Privacy aims to offer best-in-class encryption without compromising on performance. It doesn't log the user's online activities and it offers a choice of virtual servers from over 30 countries in order to protect their real location.

New platform allows sharing of cybersecurity resources
The ever changing landscape of cybersecurity means it can be hard for any one organization to stay on top of all the latest threats.
To address this problem, Trustwave is expanding its cybersecurity collaboration platform to help businesses around the world meet security challenges.

ProtonMail and ProtonVPN apps are now open source across all platforms
It is a little while since Proton Technologies announced that ProtonVPN was being open sourced to help build trust in the service. Now the company has done the same for the Android version of ProtonMail, and this means that all ProtonMail and ProtonVPN apps are now open source
Just as with ProtonVPN, the open sourcing of ProtonMail opens it up not only to the scrutiny of anyone who cares to trawl through the source code, but it has also been subjected to a third-party security audit.
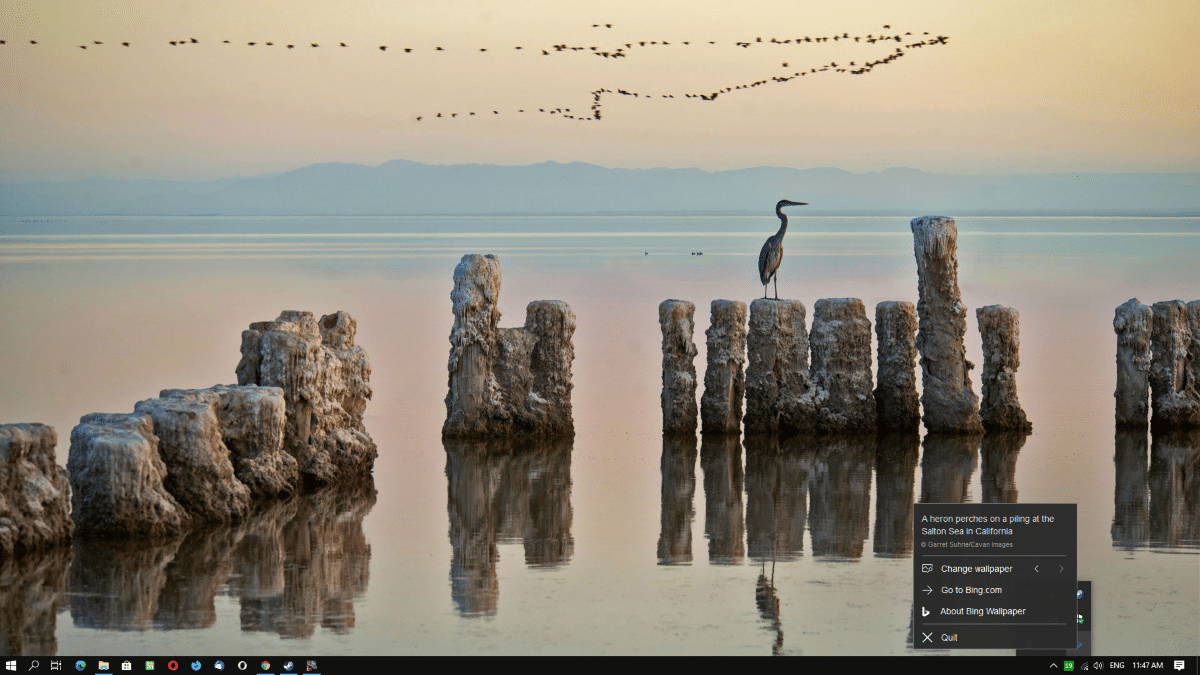
Microsoft's new Bing Wallpaper application is now available
Microsoft released a new application for Windows devices this week called Bing Wallpaper. Windows users may install the application to automatically download Bing wallpapers and have them set as the system's background image.
The application has not been released as a Microsoft Store app but as a desktop program. Users should not confuse it with the open source program Bing Wallpaper which Mike reviewed in 2017 here on BetaNews.
Ubuntu Linux 20.04 LTS 'Focal Fossa' now available for download
There are many desktop Linux distributions these days, but only a handful are significant enough to cause widespread excitement. None have the mainstream attention that Ubuntu does, however -- it is undoubtedly the most popular desktop Linux-based operating system on the planet. Hell, what other distro got mentioned on the wildly popular TV show The Big Bang Theory?
But why is Ubuntu so popular? Despite what some critics may say, Ubuntu's popularity and admiration are absolutely warranted -- there's a reason the distro has been trusted by so many people over the years. Not only is the operating system beautiful, easy to use, and very stable, but there are countless packages and repos available for it, making it a wise choice for both beginners and experts alike. Not to mention, it has a very large online community, making it is easy to find help if needed. Plus, these days, it uses the overall best desktop environment -- GNOME.

'Florentine Banker' email attack steals thousands from private equity funds
Researchers at Check Point have revealed how a sophisticated cybercrime gang managed to trick three UK private equity firms to steal hundreds of thousands of pounds.
The gang, named 'The Florentine Banker,' got away with over £500,000 following a complex business email compromise (BEC) attack.

Another Windows 10 update is causing serious problems, reducing performance, crashing and deleting files
If you were hoping that a spate of problematic updates for Windows 10 might have caused Microsoft to up its game and improve quality control, think again; the KB4549951 update is just the latest to cause issues for users.
And this time around, the problems are pretty serious. In addition to BSoD crashes and connectivity issues, users are also reporting that their settings are being removed and files deleted.

Zero-day vulnerabilities in iOS Mail are being actively exploited to target high-profile users
Security firm ZecOps has published research about security vulnerabilities affecting iPhones and iPads. The critical flaws are yet to patched by Apple and are said to be actively used to target high-profile users such as journalists, employees of Fortune 500 companies and VIPs.
What's particularly worrying about the flaws is that they can be exploited by sending a message that appears to be blank. Opened in iOS Mail, the message can be used to run code and spy on activity without the need for any interaction from the victim. There is a suggestion that a nation-state could be involved.

PATRIOT PXD is a PCIe USB-C SSD
Back in the day, external storage drives were great for portability, but were typically very slow compared to internal storage drives. Nowadays, however, thanks to PCIe solid state drives that interface with either USB 3.2 or Thunderbolt 3, the convenience of external storage doesn’t mean having to sacrifice performance. There are some very fast portable SSDs out there, and they are typically quite small too.
Today, Patriot launches its latest external SSD, and it is a fast little beast. It is essentially an internal M.2 PCIe NVMe drive housed in a sleek enclosure. The diminutive drive connects via USB-C and provides both read and write performance up to 1,000MB/s. Its aluminum body doesn't just look good, but should lend to extra durability too. It even comes with both USB-C to USB-C and USB-C to USB-A cables in the box.

Microsoft updates Cortana for Windows Insiders
Cortana hasn’t been the essential addition to Windows 10 that Microsoft was hoping for. While the digital service has its fans, for many it’s simply a button on the taskbar that they ignore.
Microsoft has been working to change that by creating a new Cortana experience with a chat-based UI. While the digital assistant was originally baked into Windows 10, it’s now available as an app you can download from the Microsoft Store, meaning it can be updated more frequently.

Microsoft releases Windows 10 Insider Build 19613 to the Fast ring
Microsoft is busy readying the Windows 10 May 2020 Update (20H1) for release next month, but it’s still hard at work producing builds for future Windows 10 versions.
Today the software giant rolls out Build 19613 to Windows Insiders on the Fast ring. This doesn’t come with any major new features, but it does introduce a number of fixes and improvements.
