
Microsoft announces DirectX 12 Ultimate with improved raytracing
Proclaiming that "it is time for DirectX to evolve once again", Microsoft has revealed DirectX 12 Ultimate which unifies the graphics technology for Xbox Series X and PC gaming.
There are a number of graphic hardware features for developers to take advantage of, including DirectX Raytracing 1.1, Variable Rate Shading, Mesh Shaders and Sampler Feedback. But Microsoft stresses that the new API will not reduce compatibility. DirectX 12 Ultimate is described as an "additive initiative"; hardware that does not support it will still be able to run next-generation games, but without some of the visual enhancements.
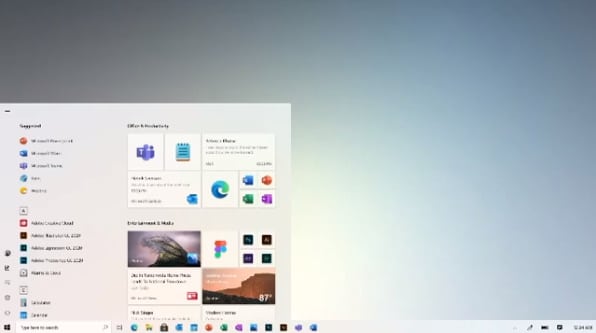
Microsoft teases new Windows 10 UI including updated Start menu
Microsoft recently announced that Windows 10 had hit the milestone of running on a billion devices. To mark this, the operating system team created a celebratory video. What's interesting about this video is the fact that it gives us a glimpse of new features coming to Windows 10, as well as changes to the UI.
We've already had a hint of the direction Microsoft is going in aesthetically with the roll-out of new icons, but this new video also shows off the redesigned Start menu, wider adoption of Fluid UI, and an updated version of File Explorer

Microsoft is delaying end of service for Windows 10 version 1709 because of coronavirus
The coronavirus pandemic is having all manner of consequences around the world, both predicted and unforeseen. With Google having announced that Chrome and Chrome OS will only be receiving security updates as a result of a revised development schedule, Microsoft has now announced that it is extending the end of service date for Windows 10 version 1709.
End of service for the Fall Creators Update was due on April 14 this year, but in light of the current public health situation the company now says that the date has been extended by six months to October 13. But the extension does not apply to all editions of Windows 10 version 1709.

MacBook Air (2020) is the Apple laptop most folks should buy
Some people love Windows, while others prefer Mac. There are even some wacky folks (such as yours truly) that enjoy using Linux. Hey, you should use whatever makes you happy. Believe it or not, macOS is quite good -- it is a joy to use and absolutely beautiful. Of course, the big problem with Apple computers -- other than their notoriously unreliable keyboards, lately -- is they are wildly expensive. And so, consumers that desire owning a Mac are often unable to realize that dream. True, there is the affordable Mac mini, but it hasn't received a meaningful update since 2018. The base model mini is woefully under-powered too.
Well, Apple has finally done something right with the MacBook line. You see, the company has released the all-new MacBook Air (2020) and it seems to be rather impressive. Long gone is the much-maligned butterfly keyboard, as this new Mac uses traditional scissor switches for the keys -- the same as the 16-inch MacBook Pro. In other words, the keyboard should prove to be more reliable and durable. Best of all, the price starts at a mere $999 ($899 with an education discount -- wink, wink), making it the new "Everyman's Mac." That price gets you an impossibly thin laptop with an enormous trackpad, T2 Security Chip, Touch ID, Thunderbolt 3, more storage capacity (NVMe SSD starting at 256GB), speedy 3733MHz LPDDR4X RAM, and of course, Apple's legendary Retina display.

New decentralized cloud storage service set to take on AWS
Cloud storage company Storj Labs is launching a new decentralized service aimed at storing data more efficiently and providing additional revenue-generating opportunities for storage node operators.
Called Tardigrade -- in case you were wondering a tardigrade is an eight-legged water dwelling micro animal (or if you've watched 'Star Trek: Discovery' a sort of massive space-travelling flea) -- it offers cloud object storage that's S3 compatible, high performing, easily implemented, exceptionally durable, and with high availability.

Get 'Hands-On Dark Web Analysis' ($23.99 value) FREE for a limited time
The overall World Wide Web is divided into three main areas -- the Surface Web, the Deep Web, and the Dark Web. The Deep Web and Dark Web are the two areas which are not accessible through standard search engines or browsers. It becomes extremely important for security professionals to have control over these areas to analyze the security of your organization.
Hands-On Dark Web Analysis will initially introduce you to the concept of the Deep Web and the Dark Web and their significance in the security sector. Then it will deep dive into installing operating systems and Tor Browser for privacy, security and anonymity while accessing them. During the course of the book, you will learn some best practices which will be useful in using the tools for best effect.

Watch Netflix with friends while you self-isolate from coronavirus with this handy extension
If you're home-working or self-isolating because of COVID-19, you might be starting to feel a little lonely. You may be used to getting together with a group of friends for a Netflix session, but such get-togethers are on hold for the time being.
But with a brilliant Chrome extension, you can still get together with friends and family online and watch Netflix together.

Google says that updates to Chrome and Chrome OS are the latest coronavirus victims
The impact of the coronavirus is being felt around the world in many ways. The pandemic is forcing people to work from home, impacting on deliveries and production in addition to being a health threat to many.
Now Google has announced that updates for both Chrome and Chrome OS are currently on pause. While the company does not say that this is a direct consequence of the spread of COVID-19, it says that the delay comes because of "adjusted work schedules at this time".

How new performance trends in JavaScript are driving an ever-faster web [Q&A]
'Write once, run anywhere' was the promise that Sun Microsystems made for Java in the mid '90s. But front-end development trends suggest that it's really JavaScript -- and its fast-evolving libraries and frameworks -- that are executing on that promise today.
To learn more about the JavaScript trends that are delivering an ever-faster, device and browser-agnostic web experience to users, we spoke with Guillermo Rauch, co-creator of the popular Next.js web framework.

Hackers using COVID-19 specials to drum up business on the dark web
We all know that hackers and cybercriminals are keen to cash in on any opportunity to spread their wares. Researchers at Check Point have uncovered that hackers are using COVID-19 to offer specials and discounts on the dark net.
In similar fashion to Black Friday or Cyber Monday discounts, hackers are using the coronavirus pandemic as a special promotion to sell their malicious goods to hungry cyber attackers.

Logitech Combo Touch Case for iPad has detachable keyboard and integrated trackpad
Earlier today, Apple shocked the world with its newest iPad Pro. While that tablet is very nice, it was an accessory for it that caused true excitement. You see, the all new Magic Keyboard has an integrated trackpad, meaning the iPad can do double duty as a tablet and a laptop. It's like a Microsoft Surface, only much better. Unfortunately, both the new iPad Pro and Magic Keyboard are quite expensive, making the combo nothing more than a dream for many consumers.
Thankfully, this trackpad support is not limited to any specific iPad, meaning it can work with a non-Pro model too. In fact, any iPad that gets the upgrade to iPadOS 13.4 will also get the compatibility. If you are someone like me that owns a meager 7th generation iPad (which will get iPadOS 13.4), I have some really great news -- Logitech has announced a keyboard case with trackpad that works with the lower-end Apple tablet. Called "Combo Touch Case," it isn't just compatible with the the 7th-gen iPad -- there is also a model for the older iPad Pro 10.5 and the 3rd-gen iPad Air. The keyboard is detachable too, offering a more comfortable experience when using the iPad as a tablet. There is even a holder for the first-generation iPad Pencil. Best of all, it will protect against drops and bumps.

Wireless charging is at an inflection point
When wireless charging went mainstream a few years back, it was expected to usher in a new era of convenience for consumers. It sounded irresistibly cool -- one of those things you just HAD to try. But when people finally did get their hands on a wireless charger, opened the box, and gave it a shot, the sparks just didn’t fly. This prophesied technology had finally arrived … and it was a letdown.
Before we go any further, let’s get one thing straight: wireless charging itself was not the problem. The concept wasn’t flawed, but the implementation was. We had been promised unparalleled convenience, but what we got was a solution with a fairly large margin of error.

Microsoft releases Windows 10 Insider Preview Build 19587 with Narrator and volume improvements
The past few Windows 10 Insider builds haven’t been hugely exciting, but that’s probably no surprise given the state of the world at the moment and the number of people switching to working from home.
Today’s new Insider release for those on the Fast ring, Build 19587, is no exception, but it does come with a number of improvements and fixes.

In a world of deepfakes, who can you trust?
Though they seem like something out of a futuristic sci-fi movie, deepfakes are very much a reality. In fact, developers have been experimenting with deepfake technology as far back as the late 1990s. Today, deepfakes have become so advanced and believable that they can cause some serious damage in the wrong hands.
"Deepfake" is a term used for the process of replacing someone in an existing image or video with someone else’s likeness. If you’ve watched Former U.S. President Barack Obama giving a lecture about cybercrime or follow the hilarious thread of videos in which various actors have their faces replaced with that of Nicolas Cage, you’ve seen a deepfake. As entertaining as they are, deepfake algorithms are getting more sophisticated every day. When we stop being able to differentiate this synthetic media from reality, a real problem arises.

The surprising state of social media background checks in 2020
Your friends and followers aren't the only ones looking at what you Like. In 2017, CareerBuilder revealed that 70 percent of employers review social media during the hiring process. Today that number may be even higher: one survey by First Advantage found that nearly two-thirds of employers choose to screen all employees and applicants for "red flag" behavior on websites such as Facebook and Twitter.
The primary peril of vetting candidates by examining their online profiles remains the same as when this trend first rose to prominence: employers performing "social media background checks" may inadvertently uncover sensitive or protected information which compromises their ability to make an unbiased hiring decision. Not hiring a candidate based on such information, from sexual orientation to religion to race, could expose a business to accusations of unfair or discriminatory hiring practices.
