
Apple appoints new vice president of AI as John Giannandrea steps down
Apple has announced that its senior vice president for Machine Learning and AI Strategy, John Giannandrea, plans to retire. Having been with the company since 2018, he will serve as an advisor for a short time before moving on in spring next year.
While no reason has been publicly given for the departure, it is widely thought that there was a degree of discontent at Giannandrea’s management of Siri. The product was blighted by a series of delays and problems that did not reflect well on Apple.
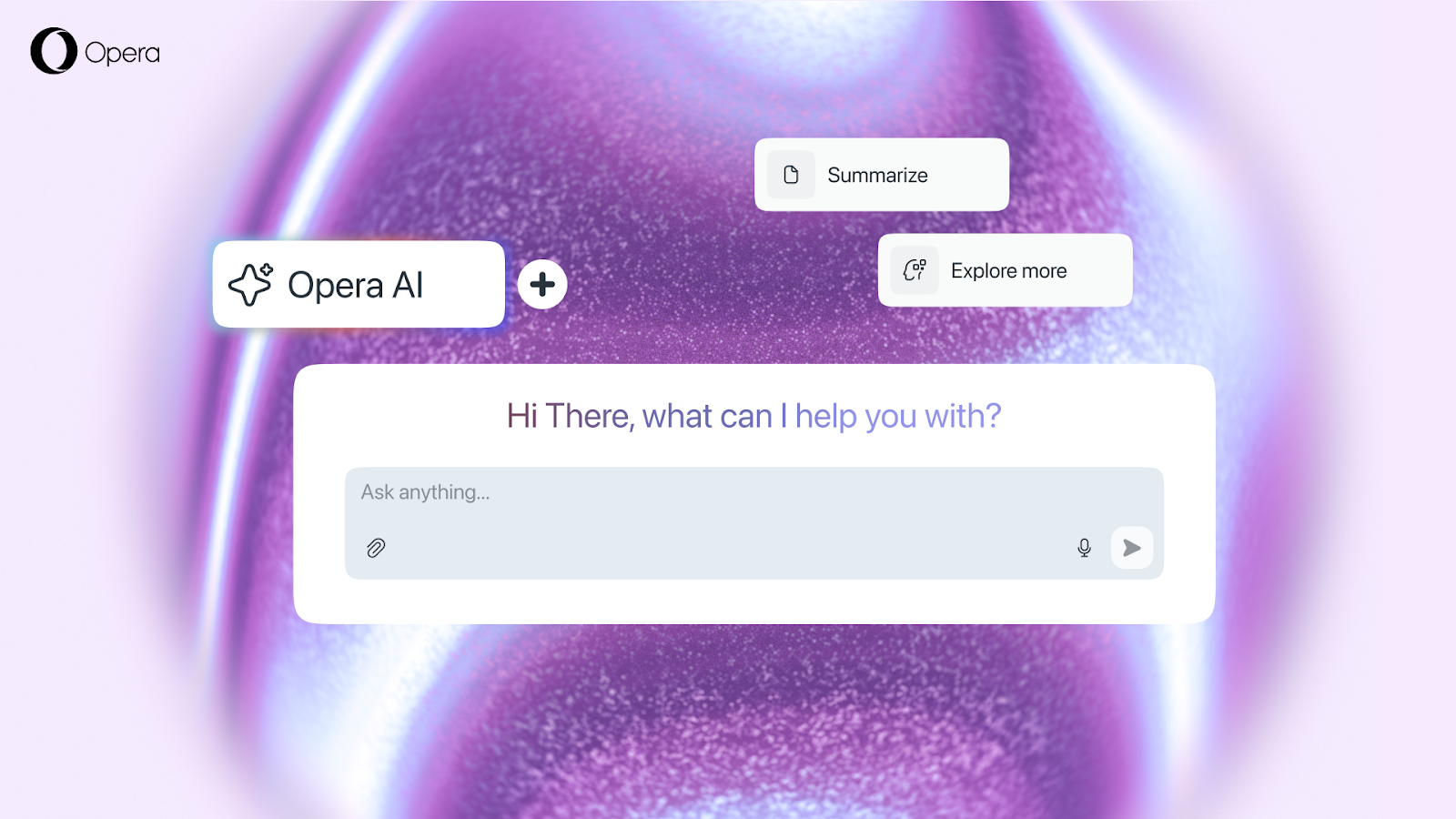
Opera brings upgraded Google AI to its browsers
Opera is rolling out new Google AI features across its Opera One, Opera GX and Opera Neon browsers. This is the result of the browser maker's long running partnership with the search giant, and now includes support for the latest Gemini models.
The new Opera AI appears as a side panel that users can open alongside any webpage, set of tabs, or even playing videos. It will respond within the context of the page, allowing tasks such as research, summaries and tab comparisons. It also supports voice input and output, along with file analysis on images and video.

Sumo Logic brings agentic AI to cybersecurity investigations
Modern security operations centers (SOCs) face a perfect storm of complexity: growing alert volumes, fragmented tools, and pressure to respond faster than ever.
Intelligent operations platform Sumo Logic is announcing new advancements to Dojo AI, its enterprise-grade agentic AI platform for security operations to help security teams reduce alert fatigue, accelerate investigations, and streamline security workflows.

Desktop web traffic overtakes mobile for the first time in 5 years
Global web traffic has done something unexpected, with desktop devices overtaking smartphones for the first time in five years. Data presented by Jemlit shows desktops claimed a 49.7 percent share of worldwide browsing in October, placing them just ahead of smartphones on 48.98 percent.
Mobile phones have held more than 60 percent of global browser traffic for much of the past three years, supported by faster networks and the way people increasingly use their phones for news, shopping, search, and entertainment. Even so, new StatCounter figures show the change began several months earlier, with desktop traffic showing a steady rise from June.
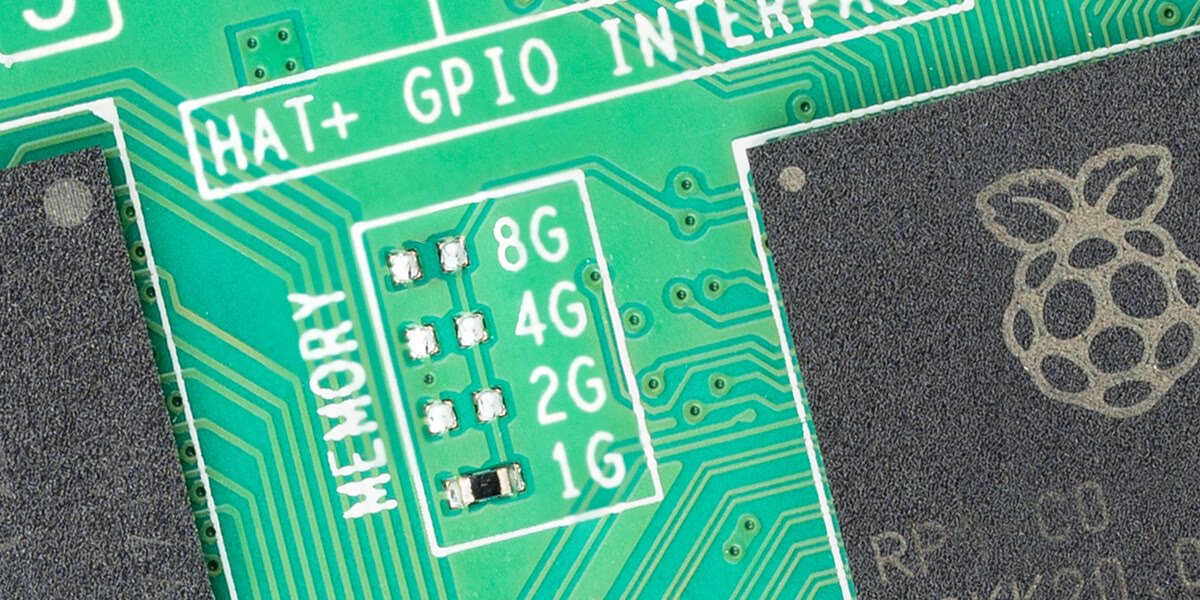
Raspberry Pi launches 1GB Raspberry Pi 5 at $45, raises the price of other models
Raspberry Pi has launched a 1GB Raspberry Pi 5 for low-memory projects and simple electronics, and confirmed price rises across parts of the Raspberry Pi 4 and 5 ranges.
Eben Upton, Chief Executive Raspberry Pi Trading, said the pricing adjustments follow an unusual rise in LPDDR4 memory costs. He noted that supply has constricted across the wider industry as AI infrastructure builders continue to secure large volumes of memory. Raspberry Pi previously announced increases for its Compute Module products in October, and the new changes now bring the single-board line into the same pattern.

Netflix quietly kills off casting from phones
To little fanfare, Netflix has made changes that make it harder to cast content from a phone to another device, such as a TV.
The general rule of thumb that now applies is that if a device has its own remote control, it will not be possible to cast to it. With this covering pretty much every television in existence, this is something that will affect a lot of people.

Why offensive security is the future of cybersecurity [Q&A]
In an era where cyber threats are evolving faster than ever, organizations can no longer rely solely on reactive defences. Offensive security, once a niche practice, is now a strategic imperative.
To better understand this shift, we spoke with Scott Reininga, CEO of Reversec, a cybersecurity firm at the forefront of offensive security innovation. He explains why offensive security is becoming essential, how it differs from traditional methods, and what organizations can do to adopt a more proactive stance.

Google has dropped its antitrust complaint against Microsoft in the EU
Just last year, Google lodged an antitrust complaint against Microsoft in the EU. Now, a week into the probe by investigators, Google has had a change of heart and has withdrawn the complaint.
The 2024 complaint was filed by Google Cloud, with Microsoft accused of trying to lock users into its Azure product through licensing of Windows, Office and other software. Just last week, the European Commission launched a series of investigations, and this has been the catalyst for Google’s complaint withdrawal.

Get ready for ads in ChatGPT
Like death and taxes, ads are an inevitability. This is something that applies to the world of technology, but particularly anything even remotely connected to the internet.
Proving the above, as well as the old adage that there is no such things as a free lunch, OpenAI is planning to bring advertising into ChatGPT. This is not something that the organization has officially announced, evidence that ads are coming has been uncovered.
Microsoft confirms KB5064081 update hides Windows 11 lock screen password icon
If you have suddenly found it more difficult to log into Windows 11, you should know that you are not alone. Microsoft has just confirmed that a recent update had the unwanted side effect of hiding the password sign-in option from the lock screen.
This was not something that all users of Windows 11 will have been affected by as there are various factors to consider. Nonetheless, this is a worrying problem that has caused a good deal of confusion and is still yet to be resolved.

Learning to spot the AI phone scammers
Scam phone calls are a fact of life these days, whether it’s home improvement grants or someone pretending to be your bank. UK mobile network O2 recently blocked 50 million dodgy calls monthly using its defense system.
But now they’re often being made using AI rather than real people in distant call centers. Naveed Janmohamed, CEO and founder of the AI research assistant Anara, says learning to spot artificial voices during phone calls might save thousands of people from sophisticated cons that have already stolen millions from unsuspecting consumers.

Brit’s fear privacy breaches despite Online Safety Act
Although the UK's Online Safety Act has made significant strides in holding online platforms accountable for harmful content, new research reveals a concerning gap in personal cybersecurity awareness among British internet users.
The study from AstrillVPN analysed search data from Google Keyword Planner to identify the privacy concerns most frequently searched by Britons. The results show password security and anonymous browsing are currently dominating the public’s attention.

How biometrics are reshaping authentication [Q&A]
The death of the password has been predicted for a very long time, though other methods are now gaining significant traction.
Perhaps the most successful of these is the use of biometrics. We talked to David Stauffer, director of sales North America at Veridas, about how biometrics is transforming authentication across financial services and telcos, and how voice-based verification enhances security against fraud, user experience and operational efficiency.
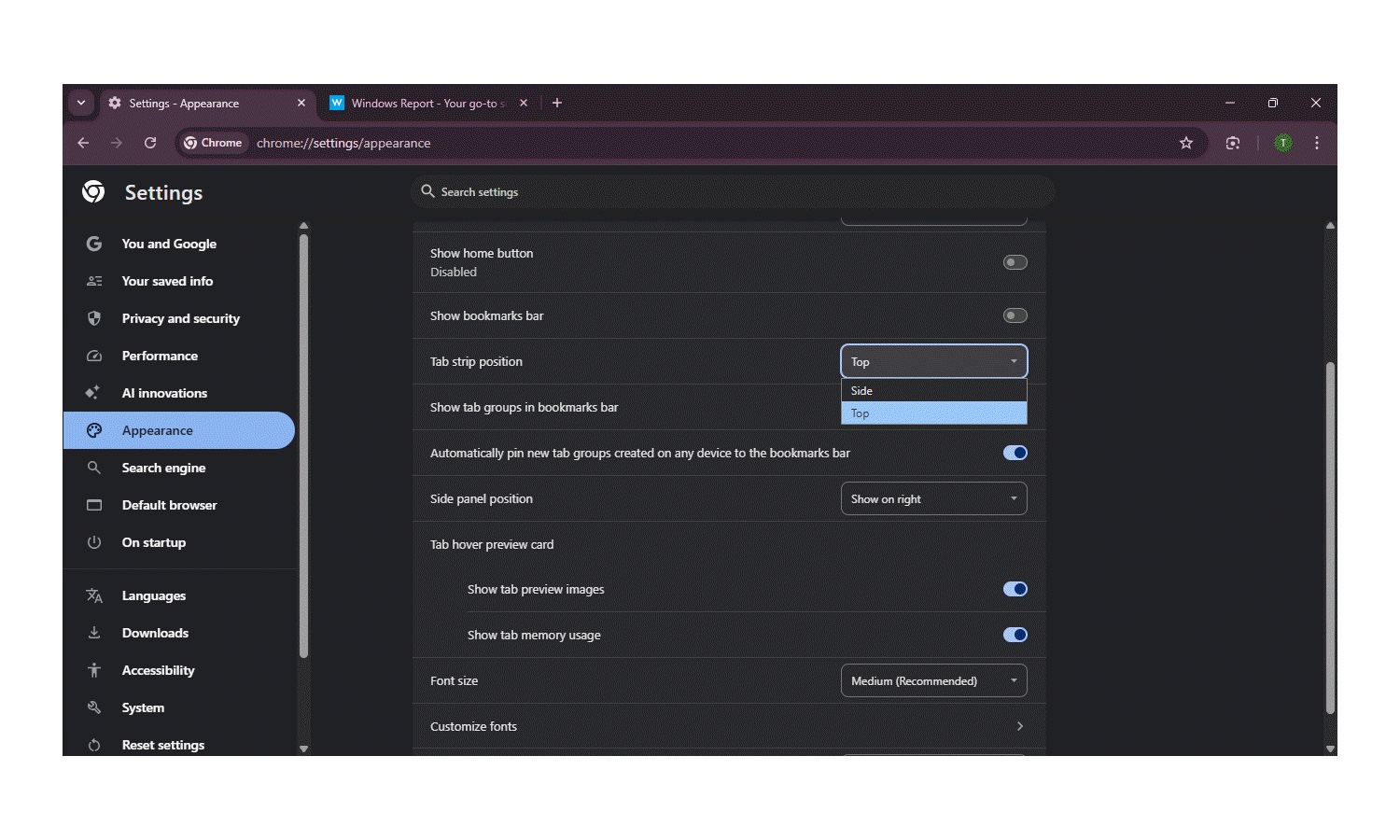
Google will make it easy to switch to vertical tabs in Chrome
Browser tabs have been positioned in a horizontal strip in just about every browser since they first appeared, Chrome included. There have been various attempts to disrupt this – and to cater to different tastes and needs – by introducing vertical tabs, and Google is still working on this feature.
As is so often the case, the preview builds of Chrome give a very good sign of things to come, and this is where we have already seen vertical positioning of the tab strip. While this is still very much a work in progress, details have emerged about changes that have already been made.

Dell has some terrible news for Microsoft about Windows 10
With the end of mainstream support for Windows 10 having reached us over a month ago, Microsoft will have been hoping that users will feel forced into upgrading to Windows 11. Has this happened? Not really.
Dell has revealed that there are millions upon millions of PCs out there that are still running Windows 10 and simply cannot run Windows 11. The company also used its Q3 earnings call to share the news that PC sales are slowing – something it predicts will continue into 2026.


