
Stop ransomware infecting your MBR with MBRFilter
Cisco’s Talos Group has released MBRFilter, a Windows disk filter which prevents malware overwriting a drive’s Master Boot Record (MBR).
This can stop some ransomware variants -- Petya, Satana -- from installing and taking full control of your PC. Installation is straightforward. Well, mostly. Download the 32 or 64-bit version as appropriate for your PC, unzip the file, right-click MBRFilter.inf and select Install. Reboot when you’re asked.

Adding facial recognition to mobile helps reduce fraud
Doing more of our day to day transactions online increases the risk of falling victim to some kind of fraud. Increasingly therefore companies are turning towards biometrics to ensure users are who they say they are.
Digital verification company Jumio is adding biometric facial recognition to its Netverify product to verify users on mobile devices.
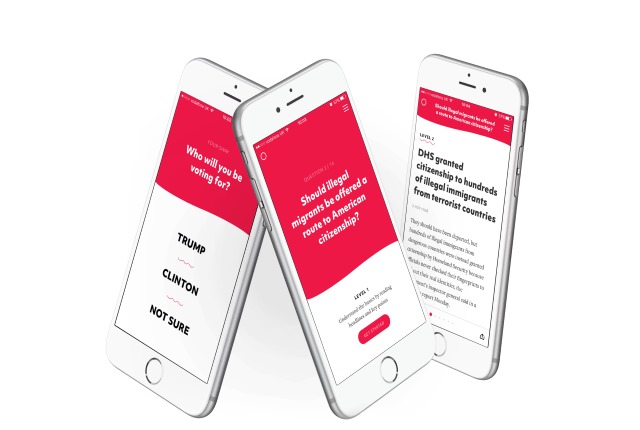
New Sway Democracy app wants to help you choose between Trump and Clinton
You've probably noticed that there's an election just around the corner. As Trump and Clinton battle it out there have been accusations that Russia is trying to interfere with the result, Julian Assange has been cut off from the internet to prevent him meddling, and Google has released a fact checker to help separate political fact from fiction.
There's no denying that this is one of the most important US elections ever, and the balance of power could be tipped by an important demographic -- millennials. With this in mind, a new app aims to help educate younger voters so no matter who they vote for, they are doing so in an informed way. Enter Sway Democracy.

Lock down any PC with Simple Software Restriction Policy
Simple Software Restriction Policy (SSRP) is a free tool which gives complete control over the folders where software can be executed.
Program Files, System and other folders are allowed by default. But commonly-exploited locations like your desktop and temporary folders are blocked, instantly protecting you from a host of potential threats.

Children are at risk from online predators as UK government fails to implement sexual grooming laws
The UK government has failed to implement promised laws that would help to protect vulnerable children from online predators in England and Wales. Back in 2014, the then-Prime Minister David Cameron said he would introduce a new criminal offense of sexual communication with a child, effectively ensnaring paedolphiles.
The law would help to reduce the problem of "grooming", the practice of luring in a child and gaining their trust with a view to later abusing that trust. Cameron's announcement more than 18 months ago was welcomed as it eliminated a legal loophole, but now children's charities are unhappy that laws that could prevent sex abuse have not been written onto the statute.

Few UK banks offer two factor authentication
According to new research from the consumers' association Which?, a number of major UK banks have failed to protect their customers online by not adopting two-factor security, which greatly protects against online banking fraud.
The association tested the customer-side security of 11 banks, revealing that over half had failed to implement two-factor ID checks on customers when they logged into their accounts. Lloyds Banking Group, Lloyds, Halifax, Bank of Scotland, Santander and TSB were the banks which scored the lowest on the tests conducted by Which?.

Google's updated privacy policy means personally identifiable ad tracking is now go, go, go!
That Google encroaches on user privacy is not a startling revelation by any stretch of the imagination. But a recent change to the company's Privacy Policy means that information from DoubleClick ads can now be used to identify individuals and track them online.
The changes to the policy have not been hidden -- the details and alterations are visible in an archived copy of the document -- but it has not been advertised either. The implications of the change are huge. Since purchasing DoubleClick back in 2007, Google kept identifiable user data separate from anonymized ad tracking. This is no longer the case.

Falling pound forces Microsoft to raise software and cloud prices
The post-Brexit fallout continues. The UK has already seen price hikes from a number of countries across a range of sectors, and the latest announcement comes from Microsoft.
The technology giant warns that starting in January 2017, prices of enterprise software and cloud services will rise for anyone paying in pounds sterling. The UK's decision to leave the EU has seen the value of the pound plummet, and Microsoft is going to increase prices by up to 22 percent to make up for this.
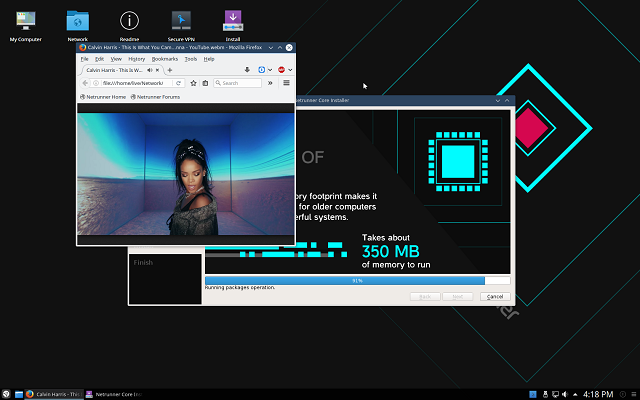
Netrunner Core 16.09 'Avalon' Debian-based KDE Linux distro now available for download
The gift and curse of desktop Linux-based operating systems is the ability to change the desktop environment. On one hand, having the choice to pick your favorite user interface, such as Unity, GNOME, or KDE Plasma, can be a huge positive. On the other, this also creates fragmented experiences between Linux users.
If you are a fan of KDE Plasma, there are plenty of quality distributions available. The overall best for home users, however, is the wonderful Netrunner. You'd be hard-pressed to find another KDE-focused distro with such care and focus on the user experience. Today, a specialized version of the Debian-based operating system, called Netrunner Core, becomes available for download. This pared-down OS is designed for lower-end systems, and there are images for both x86 and ARM.

Serious Dirty COW bug leaves millions of Linux users vulnerable to attack
A vulnerability discovered in the Linux kernel has been present for nine years, and users are being advised to seek out and install a patch as soon as they possibly can. Dubbed Dirty COW, the bug is a privilege escalation vulnerability which can be found in just about every Linux distro out there.
Discovered by security expert Phil Oester, Dirty COW is described as one of the most serious bugs of its type ever found in Linux. Assigned the code CVE-2016-5195, there is evidence that the vulnerability has been exploited and a website set up to alert people to the problem advises that the "security community should deploy honeypots that entrap attackers and to alert about exploitation attempts".

76 percent of all Windows 10 users have installed Windows 10 Anniversary Update
Even after a staggered roll out of Windows 10 Anniversary Update, Microsoft has managed to push the major operating system update to more than three-quarters of Windows 10 users.
The latest figures from AdDuplex show that uptake of Windows 10 Anniversary Update has accelerated dramatically. The latest version of Windows 10 is now installed on no less than 76.6 percent of Windows 10 PCs.

Amnesty International ranks message apps according to privacy -- Facebook wins!
Despite a desire to be more connected than ever before, people are simultaneously more concerned than ever about their security and privacy. This is certainly true when it comes to messaging tools, and the privacy features offered by a particular app or service can be what sways your decision to use it one way or the other.
Justice group Amnesty International has spent some time analyzing the privacy and encryption found in a number of popular messaging tools and compiled results in a ranked list. The findings make for interesting reading, not least because Facebook is ranked the most highly.

Warning: Mark Zuckerberg decides what's newsworthy, making him the world's most powerful editor
Facebook has stated time and time and time again that it is not a media company, despite appearing to act very much like one. The company's protestations become all the more difficult to swallow when one looks at the way it handles news. In reality, Facebook wields far more power and influence that it's willing to admit.
There have been countless instances of Facebook censoring posts from individuals, groups and organizations. Facebook appears to have an unwritten (or largely unpublished) set of rules defining what can be posted on the social network, and just this week Facebook staff wanted to censor posts by Donald Trump because they were considered hate speech. Zuckerberg disagreed, overruled his employees and allowed them to go ahead. One rule for us, another rule for them.

What you need to know about software as a service
Software-as-a-service (SaaS) is a new distribution model that is rapidly gaining popularity with businesses all over the world. A branch of cloud computing, SaaS lets businesses and consumers lease a particular piece of software from a third-party supplier, who delivers it over a network connection -- most commonly the Internet.
As with other examples of cloud computing, this provides a number of benefits in terms of flexibility, scalability and affordability, which is why it is hardly surprising that many businesses have been willing to embrace SaaS. In fact, global SaaS revenues are expected to grow 21 percent year over year to $106 billion in 2016.

Stephen Hawking believes AI could be mankind's last accomplishment
According to Stephen Hawking, artificial Intelligence (AI) and its possible implementations need to be managed with the utmost care in order to prevent its power from falling into the wrong hands or being used in a way that does not benefit mankind as a whole.
The renowned physicist stressed the point that AI could be used to commit deplorable acts in the form of powerful autonomous weapons and other ways in which people in power could use the technology to oppress and control a majority of the population.


