First look at iOS 9 and OS X 10.11 El Capitan public betas
Apple has released the first public betas of iOS 9 and OS X 10.11 El Capitan, allowing anyone with a compatible device -- iPhone and/or Mac -- to become a tester. Having signed up for the beta program last month, I immediately wanted to experience what is new in the upcoming versions of the two operating systems.
There is huge demand for the first public betas, proof being that Apple's servers were quickly overloaded during the first hours of availability. You can thank the media frenzy for this. Nonetheless, I have managed to install the iOS 9 and OS X 10.11 El Capitan public betas on my iPhone 6 Plus and 13-inch MacBook Air, respectively. And here are my first impressions.

Xolo Black with 5.5-inch FHD, Snapdragon 615 chipset, launches at Rs 12,999 ($200)
The smartphone market is becoming increasingly competitive in India. Over the past few months, we have seen a number of Indian and international companies launch some of the most exciting phones in the country. Today, Indian smartphone vendor Xolo is taking the opportunity to launch its latest flagship, the Xolo Black.
Competing with the likes of Xiaomi’s Mi 4i, Meizu’s M1 Note, and Lenovo’s K3 Note, the Xolo Black is not only putting up a fight on paper (specs sheet), but also trying to beat rival phones in the looks department. With a waistline of 7.3mm, both sides of the phone come protected by Gorilla Glass 3, a feature Xolo has seemingly picked from Samsung’s Galaxy S6. In addition, the back of the phone also has an oleophobic coating, which the company says, makes the handset resilient against smudges and stains.

The history of Windows
Windows 10 is just around the corner, with Microsoft confirming a 29 July release date for its new operating system.
The general opinion appears to be positive for Windows 10, with 73 percent of IT pros saying they will deploy it within the first two years, despite there still being a few kinks to sort out.

The man who cared about your online privacy has died
Caspar Bowden, the privacy advocate who was warning about the activities of the NSA before Edward Snowden, has died. The co-founder of the Foundation for Information Policy Research lost his battle with cancer, and tributes have been paid by the world of technology.
Bowden, the former head of privacy at Microsoft, had long-warned about potential backdoors in software and services. He campaigned passionately for the privacy of the individual and voiced grave concerns about the NSA and the FISA Amendment Act. He sat on the board of Tor and was one of the most knowledgeable and well-loved figures on the privacy scene.

PC market still sinking -- can Microsoft's Windows 10 save it from drowning?
"The PC is dead". "Tablets are the future". Blah, blah, blah. Total bullsh*t. Now that many apparent tech "experts" have tired of proclaiming the PC to be dead, we can finally enjoy our Windows, Linux and OS X personal computers in peace.
While PCs are still alive, not all is well in the market. According to IDC, shipments of these computers in Q215 were down once again, even lower than expected -- an 11.8 percent decrease, year over year -- ouch. While I am sure many OEMs are hurting, there is some good news on the horizon -- a new version of Windows coming July 29! While the much maligned tile-heavy Windows 8 did nothing to jump-start PC sales, Windows 10 may have that ability. Can Windows 10 be the PC market savior?

Google updates Android M Developer Preview
It's not long since we first learned about Android M at Google I/O and today Google launches Android M Developer Preview 2. As the name would suggest, this is a build aimed primarily at developers, giving them an opportunity to ensure their apps are ready to take full advantage of everything the latest version of the operating system has to offer.
Two key changes between Lollipop and Android M are improvements to security and battery life. The second developer preview includes more improvements to permission settings such as how fingerprint authentication works and changes to the way permissions are handled for external storage.

Google launches Gmail Postmaster Tools to eliminate spam
Spam is a problem that is not going away for anyone who receives email -- and who doesn't? Over the years Google has taken steps to try to reduce the amount of junk that reaches Gmail inboxes and today the company is taking things a step further with Gmail Postmaster Tools and enhanced filter training for Gmail.
Part of the problem with spam -- aside from the sheer volume of it -- is that the detection of it is something of an art rather than a science. It is all too easy for legitimate email to get consigned to the junk folder, and this is what Gmail Postmaster Tools aims to help with. Rather than helping recipients banish spam, it helps senders ensure that their messages are delivered to inboxes rather than filtered out.

BlackBerry partners with Google to make Android more secure for enterprise users
Hot on the heels of rumors of an Android-powered phone by BlackBerry, the Canadian smartphone manufacturer announces its partnership with Google to do something cool together. As part of the collaboration, BlackBerry -- known for its highly sophisticated and secure enterprise security suites -- will be working with Google to create a more enterprise-ready version of Android operating system.
The deal makes perfect sense for both of the companies. Google’s Android is the most popular mobile operating system on the planet. However, the infamous Edward Snowden revelations have affected Google's as well as other companies’ reputations. Moreover, Google has a long way to go to entice enterprise users to pick its operating system over others'. For BlackBerry, which once held a large market share but has lost most of it since, this partnership could help the company find a reliable revenue channel. But most importantly, enterprise users are the biggest winners here.

Microsoft Lumia 735 now available to buy in Verizon Wireless stores
The Lumia 735 was added to Verizon Wireless’s line up last month, but was only available to purchase online. Today, that changes and you can now pick up the smartphone from any of Big Red’s brick and mortar stores.
If you’ve had your eye on the phone for a while, there are some incentives being offered to help push you into making the move.

Swiss Post testing drone deliveries
Switzerland’s postal service started testing drone parcel deliveries, the company said in a statement on Tuesday.
The testing, done together with Swiss WorldCargo and Matternet, will investigate the technology and determine the cost-effectiveness of such a business idea, although flying postmen are not expected to be widely used for the next five years.

Google's now testing self-driving car in Texas
This week has been a particularly exciting week for Google, as the company has started testing its self-driving car in Austin, Texas. The car in question is a specially equipped Lexus prototype, and with the new change of scenery the company is hoping that with it will learn more about the car’s performance in a different environment and road conditions, and how it reacts.
They have been testing self-driving cars since 2009, but most of the testing was done within Silicon Valley. Outside of Silicon Valley, Mountain View in California has been the primary testing ground, but with the ramping up of testing Google hopes that the self-driving technology should be ready for commercial use by 2020.
Windows 10 Insider Preview Build 10166 now available on the Fast ring
Last week, Windows Insiders on the Fast ring were treated to three new builds of Windows 10. As you’d expect, with the launch date getting ever nearer, things are seriously accelerating. New ISOs of the latest build, 10162, were pushed out soon after, followed by the same build becoming available to Insiders on the Slow ring.
Today, after a short wait, the new releases continue, with Windows 10 Build 10166 arriving on the Fast ring. As you’d expect, there are no major changes. It is, as Microsoft describes it, all about "bug fixing and fit-and-finish" from here on. One big change is that the Xbox Music app has been rebranded, and now appears as Groove Music.
Microsoft Band and Health get Web Tiles and Cloud API Previews with developer focus
When I bought my Microsoft Band, I had very lofty goals of losing weight and getting in shape. The reality, however, is that such a device is not magic -- you still have to put in the work. While I am still a fat guy, Band has certainly been a motivator and useful companion -- I am still determined to have my body Speedo-ready eventually.
Unfortunately, besides fitness, its usefulness is a bit limited; I use it for alerts and Starbucks payments, but not much else. Luckily, Microsoft seems to be committed to the platform and making it better over time. Today, Microsoft announces new Web Tiles and Cloud APIs. How will this improve Band? By wisely focusing on -- allow me to quote the beloved Steve Ballmer -- "developers, developers, developers, developers". Yes, developers are the key.
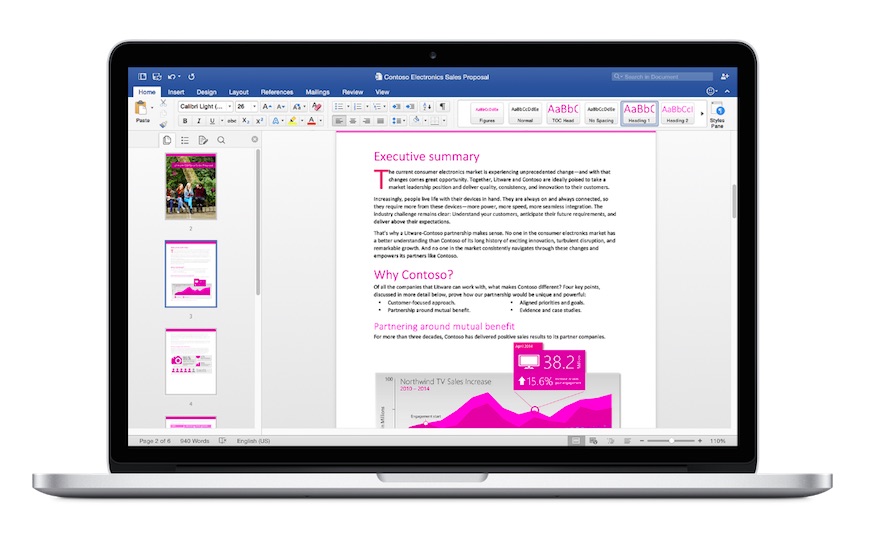
Microsoft releases Office 2016 for Mac for Office 365 subscribers; standalone version releases in September
After testing its productivity suite for more than four months and pushing seven updates to it, Microsoft today announces that it is releasing Office 2016 for Mac users. Available in 139 countries and in 16 languages, the productivity suite is now ready for Office 365 subscribers to snag. Those who want a standalone version of it will have to wait till September, however.
In its latest version of Office, the company is betting on the cloud power and integration. It says that with Office 2016, users will be able to access their documents "anytime, anywhere, and on any device". Office 2016 integrates with a number of popular services including Office 365, of course, as well as OneDrive, OneDrive for Business, and SharePoint.

Enterprise-class Wi-Fi for the SMB: 15 best practices from the field
Pitiful Wi-Fi implementation is so prevalent these days that people take it for granted. From the hotels we visit, to the cafes we frequent, down to the offices we call home 9-5 daily. And that's unfortunate, because when done right, Wi-Fi is an enabler for connecting us wherever, whenever.
Why can't most organizations get Wi-Fi right?



