
Axway brings cloud B2B to Amazon Web Services
Enterprises can be reluctant to move some functions into the cloud because of security and other concerns. So services that can allay these fears have big potential in the market.
Data flow specialist Axway already hosts secure private cloud portfolio solutions with AWS and has now announced that it’s making a Cloud B2B service available.

How to install (and update to) Android 5.0 Lollipop on Nexus 4, 5, 7, 10
After launching alongside Nexus 6 and Nexus 9, Android 5.0 Lollipop is now making its way to the rest of Google's family of smartphones and tablets. So, naturally, you want to get it up and running as soon as possible on your older Nexus devices, now that it is finally ready for prime time. And why wouldn't you? The latest version of Android packs lots of sweet changes, chief among them the new design language dubbed Material Design, the new, faster default runtime called ART, battery life improvements, 64-bit support, beefed-up security, new APIs and much, much more.
There are two ways you get Android 5.0 Lollipop on your Nexus device. You can use the OTA update file to update or the factory image to make a clean install. This article will explain how can leverage both to run the latest version of Android on your Nexus 4, Nexus 5, Nexus 7 and Nexus 10.

Ear-o-Smart: earrings that monitor your fitness levels hit Kickstarter
Developers of ‘the world’s first smart earring’ are hoping to raise over $30,000 on the Kickstarter crowd-funding website as part of a vision to "take fitness monitoring to the next level".
With most fitness and activity tracking devices typically worn on the wrist, developers of the Ear-o-Smart earring believe the wearable electronics market is missing a trick.

Microsoft ships 10 million Xbox One consoles -- should Sony be scared? Absolutely
Today marks a monumental moment for Microsoft -- 10 million Xbox consoles have been shipped to stores. I don't care who you are, you must admit that is an impressive feat. Of course, Sony reached that milestone months earlier, but this should not detract from Microsoft's achievement.
Quite frankly, the video game console race is a jog, not a sprint. In other words, the PlayStation 4's early lead is not guaranteed forever; the Xbox One is still in the game (pun intended). Not only is the Xbox One now $50 less expensive than the PS4, but it has some exclusive titles that will have gamers overlooking its competitor, such as Halo and Sunset Overdrive. Yep, Sony should definitely be worried.

Google wants US Privacy Act extended to Europe
Privacy is in the news more than ever before, and high-profile companies are falling over themselves to show just how much they care about protecting the rights of their users. We've witnessed all of the transparency reports about government data requests after the Snowden revelations. We've seen Facebook trying to create a safer email standard. We've seen privacy violations by government websites, and we've seen how those in positions of power believe that privacy is not an absolute right.
Google -- ever the master of PR -- thinks that it's time more was done to protect the privacy of internet users; specifically those in Europe. Google feels that the US Privacy Act should be extended to cover citizens of the EU. But what does this actually mean?
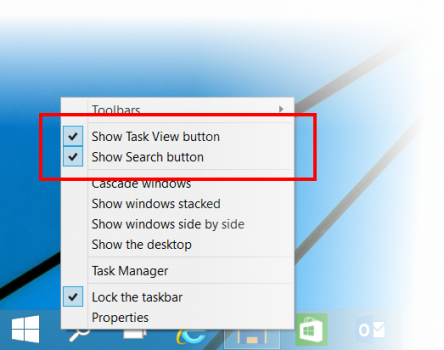
Windows 10 Technical Preview Build 9879 arrives -- here's what's new
If you’re using/testing the preview version of Microsoft’s operating system as one of the million+ "Windows Insiders", get ready for a big update. Build 9879 is arriving today and will be with you shortly, if it isn’t already.
Microsoft's Gabe Aul has provided a handy run through detailing all of the major changes, but one of the big additions is the ability to hide the Search and Task View buttons on the taskbar. That will please my colleague Mark Wilson who hates them. You’ll be able to toggle those off just by right-clicking the taskbar and disabling them in the context menu.
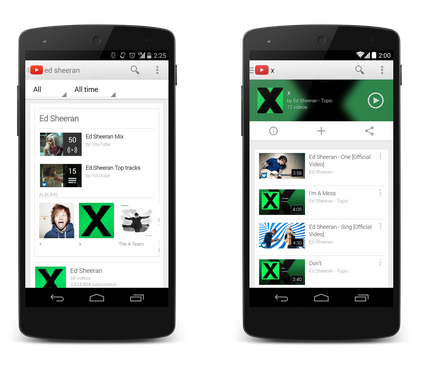
YouTube Music Key joins the streaming battle
The battle for your hard earned money in the music streaming business is heating up, which seems to be a statement I make regularly these days. This time, the offering comes from an unexpected source. While YouTube is a go-to for music videos, it isn't generally thought of for a streaming music source. Or perhaps I'm old.
YouTube is unveiling its new service, Music Key. "You’ve asked us for ways to listen to music without ads, to keep playing music videos even if you lock the screen or start using another app, and to play music even if you’re not connected to the Internet. That’s why today we're introducing YouTube Music Key beta, a monthly subscription service".

Nexus 6: vanilla Android never tasted so good [Review]
One of Android's most attractive aspects is also its greatest weakness. You see, unlike the iPhone and iOS, Google's Linux-based operating system is available to any manufacturer that is interested. This means you can see many Android devices in different shapes, sizes and styles. Hell, hardware aside, even the operating system can be customized. The problem is, with so much different hardware and tweaked software, many phones do not get regular updates -- this is also due to extensive carrier testing. To the average consumer, this is not a huge headache, as app compatibility is generally fine across versions. Where this becomes an issue is when vulnerabilities are discovered -- delays in updates or a total lack of updates can put a user at risk.
Enter the Nexus line of Android devices. Every year, Google hand-selects a manufacturer to build a smartphone running "vanilla" Android, meaning it is pure and not tweaked or customized. These phones (and tablets) are designed to get fast updates directly from Google. This ensures that not only does the user have the latest features, but the safest and newest version of the operating system too. The latest such phone is the Motorola-built Nexus 6 -- named as such for having a 6-inch screen (technically 5.96 inch). Is it the best Nexus yet?

Microsoft makes .NET open source -- brings it to Linux and OS X
They say you can't teach an old dog new tricks, but boy oh boy, don't tell that to Satya Nadella. To many, Microsoft represents a dinosaur in technology, but as the fictional Jurassic Park showed us, dinosaurs can be brought back to life and thrive in modern times. In other words, even though Microsoft never died, its image was in decline, but it has been resurrected by doing and saying all the right things.
Today, Microsoft continues its upwards trajectory by announcing that .NET is going open source. While this isn't Microsoft's first open source rodeo, this is certainly the biggest. Hell, it is even bringing .NET to both Linux and OS X! Competitors beware; Microsoft is a Tyrannosaurus Rex and is showing its teeth.

The true cost of DDoS attacks on business
DDoS attacks can be extremely disruptive to business but it can be hard to quantify that disruption in financial and business terms.
A new report by security company Incapsula collates responses from 270 North American organizations of varying sizes to gauge the true impact of attacks. The findings indicate that DDoS attacks are relatively common with 45 percent of the respondents indicating their organization has been hit at some point. Of these, almost all (91 percent) reported an attack during the last 12 months, and 70 percent were targeted two or more times.

Software producers gear up for 'appification' of the enterprise
As consumers we're used to being able to download apps for just about any purpose. As we come to expect this sort of flexibility in enterprise applications too, a shift is needed in the way software is delivered in order to keep us appy -- sorry!
A new report by Flexera Software in conjunction with IDC suggests that a transformation is under way, paving the way for software vendors and intelligent device makers, including IoT manufacturers, to profit from the 'appification' of the enterprise.
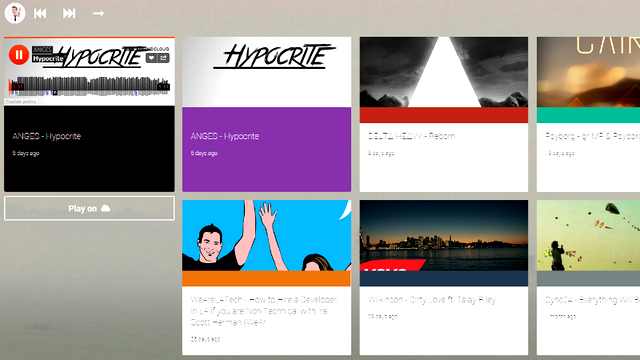
How to play music directly from Gmail
For anyone who has ever been sent MP3 songs or YouTube videos via Email, you may be interested to hear that you can actually play these straight from your Gmail inbox.
It’s also possible to compile all the songs and videos that you’ve ever received into a playlist, meaning you can listen to all your favorite music without having to open another tab or program. Here's how it’s done.

Cloud application security suite protects against DDoS and other attacks
Moving business applications to the cloud doesn't remove the need for securing them, in fact it potentially makes them more vulnerable.
Cloud application delivery service Instart Logic has announced a new Security Suite offering customers multi-layered protection against DDoS attacks and other cybersecurity threats.

Majority of UK businesses still not ready for cloud migration
New research commissioned by technology services firm Reconnix has found that 82 percent of UK IT leaders do not believe they are fully ready to make the move to Infrastructure-as-a-service (IaaS) providers, due to a shortage of in-house skills.
Only 10 percent of the 100 IT decision makers involved believed they were ready, whilst a further 8 percent had already migrated or were in the process of migration.

Companies add more physical security to combat BYOD risks
According to a new survey carried out for security device specialist Kensington, 73 percent of executives recognize that BYOD presents greater risks for the organization.
However, 59 percent still approve the use of personal devices for business use and to address concerns 55 percent are planning to invest more in physical security.



