
Why robust KYC procedures are crucial for all SaaS companies [Q&A]
For banks, know-your-customer (KYC) measures amount to 40 percent of all anti money laundering (AML) compliance costs, totaling $5.7 million each year. This sum is tiny, however, compared to what is paid for non-compliance. In 2022, global fines for inadequate AML grew by 50 percent, almost reaching $5 billion.
We spoke to Vaidotas Šedys, head of risk management at web intelligence platform Oxylabs, to discover that KYC-related challenges are not just faced by banks but are an issue for proxy and web scraping service providers too.

Microsoft PC Manager utility warns Windows 11 users switching from Bing that they need to 'repair' their PC
The Microsoft PC Manager app -- a free and official tweaking and optimization utility available from the Microsoft Store -- is the latest software from the company to offer up questionable and controversial advice.
We've already seen the appearance of ads (or recommendations as Microsoft prefers to call them) in Windows itself, Office and Edge. Now users of the Microsoft PC Manager who have changed Edge's search engine to something other than Bing are being told that this is something that needs to be repaired.

Western Digital unveils world's first 2.5-inch 6TB portable hard drives
In a world where digital content is rapidly expanding, the need for larger and more robust storage solutions has never been greater. Western Digital has stepped up to meet this demand with the introduction of a groundbreaking portable HDD expansion across its WD, WD_BLACK, and SanDisk Professional product lines. These new additions boast the world’s highest storage capacity in a 2.5” portable HDD, bringing 6TB capacities to the WD My Passport portable HDD line, WD_BLACK P10 Game Drive, and SanDisk Professional G-DRIVE ArmorATD.
“Expanding our portfolio with the world’s first 2.5” 6TB portable hard drive is an incredible technological achievement, and it enables us to continue pushing the boundaries of what's possible,” said Nitin Kachhwaha, Director of Product Management at Western Digital. “Offering up to 6TB in such a small form factor and accessible price point gives everyone—from students, gamers, professional videographers, and more—greater flexibility to create and keep even more of their essential content in one portable drive.”

Opera goes native for Windows on Arm
Opera has announced the release of an Arm-optimized version of its web browser, supported by Microsoft's App Assure team and Qualcomm Technologies, Inc. This new build is designed for Arm-based Windows systems, delivering over twice the speed compared to previous versions. The timing of this release aligns with the anticipated arrival of products powered by Qualcomm's Snapdragon X Elite Platform.
The Arm-optimized version of Opera is expected to deliver exceptional performance on the fastest machines available, thanks to the efficiency of Arm architecture. Snapdragon-powered devices are known for better battery life, which results from the power-efficient design of these processors. The reduced instruction set (RISC) architecture is optimized for streamlined performance, offering longer battery life and cooler operating temperatures.
Privacy-focused mobile operating system /e/OS rolls out new version
If you have an Android phone you'll no doubt be aware of the risk that unwanted trackers can access your data while you're using third-party apps or browsing the web.
If you're worried about being tracked though there is an alternative in the form of /e/OS which has a focus on privacy and can be can be flashed on numerous Android devices to replace Google's ubiquitous OS. Today sees the release of V2 of /e/OS which offers further privacy controls, tools and improved user interface.

PDP launches Victrix Gambit Prime Wired Tournament Controller for Xbox and PC
Not a fan of wireless controllers? Well, there is some great news for you! You see, Performance Designed Products LLC (a Turtle Beach company) has launched the Victrix Gambit Prime Wired Tournament Controller for Xbox Series X|S, Xbox One, and PC.
The standout feature of the Victrix Gambit Prime is its patented Dual Core Technology, which promises up to eight times faster input responses. This reduction in lag is crucial for gamers looking to maximize their speed and performance. Additionally, the controller comes with 12 swappable components, allowing users to customize it to fit their play style perfectly. A convenient case is included to store any spare parts.

Last year's cybersecurity issues could still be this year's nightmares
It can seem like securing systems is all about new threats and zero-day issues. But research from exposure management platform CyCognito shows that older issues can still be a problem.
It shows two percent of organizations have assets still vulnerable to Log4j. What's more over 50 percent of attempted patches require multiple rounds of validation before the patch is successful, often because of incomplete or inaccurately followed remediation instructions -- effectively prolonging the exposure window.
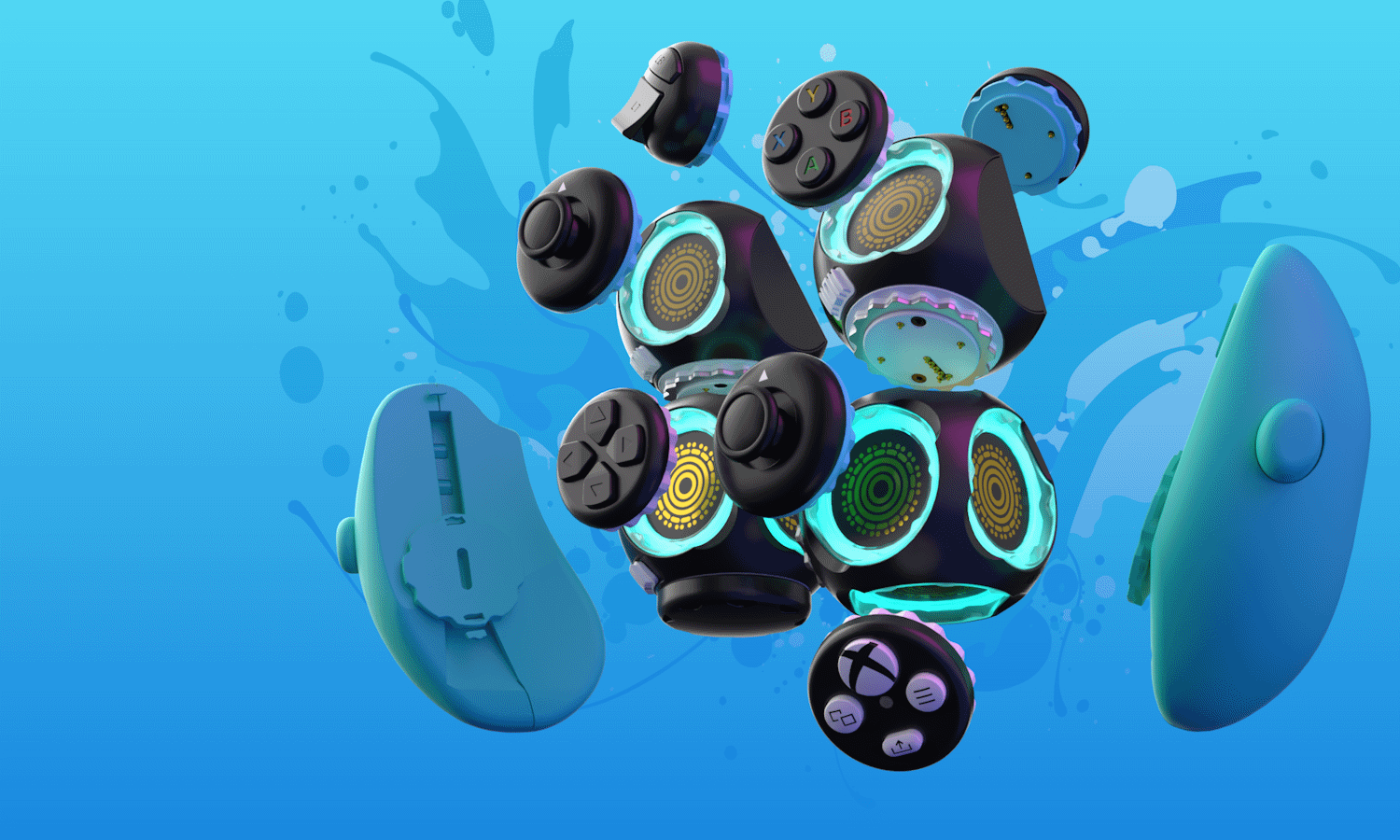
Microsoft launches modular Proteus Controller to make PC and Xbox gaming more accessible
Microsoft has teamed up with Byowave to produce a highly customizable, modular controller designed for those who find traditional gamepad-style controllers difficult or impossible to use.
The announcement coincides with Global Accessibility Awareness Day, which falls on the third Thursday of May each year. Comprising cube-like modules and interchangeable faceplates that allow for dozens of configurations, the Proteus Controller lets users create a completely personalized gaming experience.

CISOs confident about security and gen AI risks
Over half of CISOs believe generative AI is a force for good and a security enabler, whereas only 25 percent think it presents a risk to their organizational security according to a new survey.
The survey of the ClubCISO community, in collaboration with Telstra Purple, highlights CISOs' confidence in generative AI in their organizations.

Google search has a new 'web' filter to help you find long-form articles while avoiding images and videos
It's not often that Google makes a change to its search engine that proves almost universally popular, but with the introduction of a new Web filter, the company seems to have achieved just that.
Eliciting reactions such as "Holy shit are they making the search engine useful again", the Web filter joins existing filters such as Videos, Images and Shopping that are already found at the top of search results. Rolling out right now, the only complaint so far appears to be that there is (currently) no way to set this as the default view.

Get 'Build Your Own Programming Language -- Second Edition' (worth $39.99) for FREE
There are many reasons to build a programming language: out of necessity, as a learning exercise, or just for fun.
Whatever your reasons, Build Your Own Programming Language gives you the tools to succeed. You’ll build the frontend of a compiler for your language and generate a lexical analyzer and parser using Lex and YACC tools. Then you’ll explore a series of syntax tree traversals before looking at code generation for a bytecode virtual machine or native code.

VMware Fusion and Workstation Pro now FREE for personal use
VMware’s Fusion and Workstation products have been go-to solutions for millions, allowing users to create local virtual environments on Windows, Linux, and Mac computers. These tools are essential for installing other operating systems, learning about technology, and developing and testing software. Now, there’s exciting news for the VMware community.
As VMware integrates Fusion and Workstation into Broadcom, they are making a HUGE change: Fusion Pro and Workstation Pro are now free for personal use. Yes, you read that right – free! This is a game-changer for tech enthusiasts and developers who want to run virtual machines on their personal devices without breaking the bank. You can download these from the new portal at support.broadcom.com.
How RAG completes the generative AI puzzle
Generative AI entered the global consciousness with a bang at the close of 2022 (cue: ChatGPT), but making it work in the enterprise has amounted to little more than a series of stumbles. Shadow AI use in the enterprise is sky high as employees are making day-to-day task companions out of AI chat tools. But for the knowledge-intensive workflows that are core to an organization’s mission, generative AI has yet to deliver on its lofty promise to transform the way we work.
Don’t bet on this trough of disillusionment to last very long, however. A process called retrieval augmented generation (RAG) is unlocking the kinds of enterprise generative AI use cases that previously were not viable. Companies such as Meta, Google, Amazon, Microsoft, OpenAI and a number of AI startups have been aggressively rolling out enterprise-focused RAG-based solutions.

Walking the AI tightrope in IAM: finding the right balance for your organization
Identity and access management (IAM) is the foundation for control and productivity in today’s digital business environments. Ensuring the right people have the right level of access to the resources they need whenever they need them -- and that the wrong people don’t -- is a core responsibility for administrators and security teams. In a typical hybrid, distributed, multi-cloud environment, with thousands of identities to manage dynamically as the business evolves, the scale of the challenge is considerable. Enter Artificial Intelligence (AI), the seductive solution to all large-scale data-intensive challenges. AI has enormous potential for streamlining the many workloads associated with IAM and lifting the burden on stretched administrative and security teams.
We are undoubtedly experiencing an AI gold rush, but there are tensions in this brave new world. Our recent SME IT Trends report reflects this reality; while 87 percent of UK IT administrator respondents plan to implement AI initiatives in the next two years and 70 percent believe that their organization should be investing in AI, a significant minority (15 percent) say their organization is moving too fast on AI. They are in conflict with the 22 percent who think their business is moving too slowly. That amounts to well over a third of SME IT administrators who are uncomfortable with their company’s AI adoption rate.

Google Rankings dropped after Google's core update: What should you do?
The goal of Google Search's Core Updates is to enhance user experience and optimize its algorithms; nonetheless, many sites may face major changes in search ranks as a result. Any website owner must be aware of these adjustments as they have a direct impact on their capacity to preserve or improve their search engine rankings. Today, we'll explore the reasons for these rankings dropping, how to identify the changes, and practical actions you can take in this situation.
A Google Core Update refers to broad changes made to the overall ranking algorithms and systems that affect how websites are evaluated and ranked in search results. These updates aim to enhance the quality of search results by better assessing page content and its relevance to user queries. While Google continuously updates its algorithms, core updates are less frequent and more impactful, typically announced publicly by Google due to their significant effects on the search landscape.



