
Tech investments often driven by fear of missing out
New research shows that 61 percent of CIOs say their investments are often driven by the fear of missing out. What's more, 79 percent say they have to take risks on emerging technologies or they will 'go the way of the dinosaurs'.
The study, from SaaS company Ardoq, of 700 CIOs and other senior IT leaders in enterprises of more than 2,000 employees, finds 91 percent of CIOs say that if successful, emerging technology research can put them at the forefront of their market -- but 99 percent say the success rate tends to be much lower than for established technologies.

Google issues urgent Chrome update to patch zero-day vulnerability
Google has released an emergency security update for the Chrome browser for Windows, Mac, and Linux, and is urging all users of the browser to install it immediately.
The update is to fix CVE-2024-4671 which could allow remote access to data and Google confirms in Chrome's update notes that it is actively being exploited and therefore represents threat to your online security.

With the new GPT-4o model OpenAI takes its ChatGPT to the next level
Pioneering AI firm OpenAI has launched the latest edition of its LLM, GPT-4o. The flagship model is being made available to all ChatGPT users free of charge, although paying users will get faster access to it.
There is a lot to this update, but OpenAI highlights improvements to capabilities across text, voice and vision, and well as faster performance. Oh, and if you were curious, the "o" in GPT-4o stands for "omni".
OpenAI launches a ChatGPT app for macOS; Windows users will have to wait
In a bid to make its AI chatbot more accessible, OpenAI has announced a new desktop ChatGPT app. There are already third-party desktop apps, but now there is an official option too.
It joins the existing mobile apps that are available for iOS and Android and, unusually, it is macOS users who get their hands on the desktop app before Windows users.

Google partners with HP to commercialize Project Starline for realistic virtual meetings
Google has announced its collaboration with HP to commercialize Project Starline, a technology designed to make people feel as if they're together even when miles apart. This partnership aims to bring the experience out of the lab and into the workplace, revolutionizing how distributed teams and individuals connect.
First introduced in 2021, Project Starline uses advancements in AI, 3D imaging, and other technologies to create an immersive communication experience. It functions like a "magic window," allowing users to talk, gesture, and make eye contact as if they were in the same room. After extensive testing across Google offices and with enterprise partners, the technology has demonstrated that it can transform meetings, enhancing attentiveness, memory recall, and the overall sense of presence.

Google and Apple team up to enhance privacy with new Bluetooth tracker alerts
Google and Apple have developed a new industry specification aimed at enhancing user privacy and safety across mobile platforms. The specification, named "Detecting Unwanted Location Trackers," is designed to alert users on both Android and iOS devices if a Bluetooth tracking device is potentially being used to track them without their knowledge.
This initiative is a response to the growing concern over the misuse of Bluetooth tracking devices, which are primarily intended for locating personal belongings. With the new specification, Google has rolled out this feature to Android devices running version 6.0 and above, while Apple has incorporated it into iOS 17.5.

TCL launches 2024 TV and sound bar lineup with advanced QD-Mini LED technology and Dolby Atmos
TCL today unveiled a significant expansion to its product lineup, introducing cutting-edge QD-Mini LED TVs across its QM7 and QM8 series and launching new sound bars equipped with Dolby Atmos technology.
TCL's 2024 lineup features the advanced QD-Mini LED technology, offering an unprecedented viewing experience with high-performance features across multiple models:

Transcend unveils new CFast memory cards for high-demand industries
Transcend has expanded its lineup with two new CFast memory cards, the CFX730 and CFX610, designed to cater to the rigorous demands of 24/7 operations in gaming & entertainment, medical equipment, and transportation systems. These cards boast top-tier transfer speeds and enhanced durability.
Meeting the CFast 2.0 standards, the CFX730 and CFX610 utilize advanced 112-layer 3D NAND flash technology combined with a SATA III 6Gb/s interface. They offer substantial storage options up to 1TB. Notably, both models are available in Wide Temperature variants, which can operate in extreme conditions ranging from -40°C to 85°C, ensuring reliability across various environments.

Cyber anxiety on the rise in the UK
A new study reveals that 56 percent of UK adults are more worried over potential cyberattacks since Russia's invasion of Ukraine.
The study from Illumio surveyed 2,000 people to understand their attitudes towards cybersecurity and finds only 47 percent are confident in central government's capabilities to ward off digital threats effectively and just 35 percent have confidence in local government.

The role of data governance in developing AI [Q&A]
The term 'prompt engineer' has become a bit of a buzz word for future-of-work topics. What isn't discussed as much, and is arguably more important to AI models, is the role of the data governance architect.
Satish Jayanthi, CTO & co-founder of Coalesce believes that without good data governance, organizations will go nowhere in extracting value from AI and ML models. We talked to him to find out more.

Microsoft is still facing EU antitrust charges despite unbundling Teams from Office
It seems that Microsoft’s attempts to sidestep anticompetition legal action over its Teams software has failed. Although Teams has been -- begrudgingly -- unbundled from Office, the European Commission is believed to be forging ahead with antitrust charges.
Many rivals to Teams, including the likes of Slack, have expressed concern about what they believe to be anticompetitive behavior by Microsoft. Despite Microsoft decoupling Teams from Office and other software, EU officials are of the opinion that the company has not gone far enough to level the playing field.

Linux Daddy Linus Torvalds releases kernel 6.9
Linus Torvalds, the pioneer behind the Linux kernel, has released version 6.9, opting not to delay despite a few unresolved regression fixes. According to Torvalds, the remaining issues are minor and will be addressed via backports in subsequent updates. This version is characterized by its stability, with Torvalds noting that the release process appeared “pretty normal.”
This iteration brings notable updates, particularly to GPU and networking drivers, which dominate the change log, although Torvalds mentioned that these are relatively small in scope. The release also includes several critical filesystem fixes, with enhancements to bcachefs and adjustments in ksmbd, alongside late-stage selftest fixes and core networking amendments.

Windows 10 21H2: end of support for Enterprise and Education
Next month, the Enterprise and Education editions of Windows 10 version 21H2 will reach end of servicing. Microsoft stopped supporting the consumer editions in June 2023 already.
Enterprise, Education and IoT editions of Windows 10 version 21H2 reach end of support on June 11, 2024. Only Windows 10 Enterprise LTSC 2021 and Windows 10 IoT Enterprise LTSC 2021 continue to receive support until January 12, 2027.
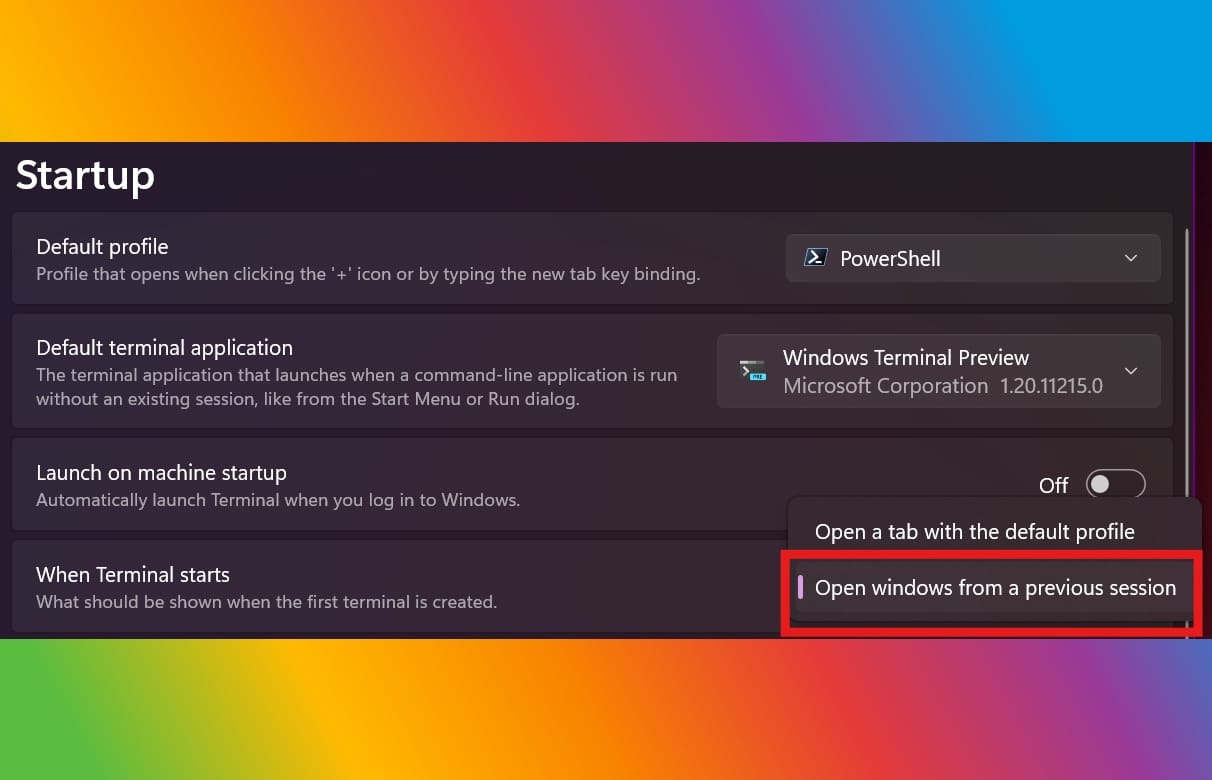
Microsoft powers up Windows Terminal with session restoration and experimental scratchpad features
Microsoft has released Windows Terminal Preview 1.21 and, despite the small version number increase, it is home to a large number of changes.
Possibly the most interesting -- and useful -- addition is Buffer Restore which will load the windows from the previous session if you want. There are new font options, rendering changes, new settings, and new support for Custom Action by JSON Fragment Extensions.
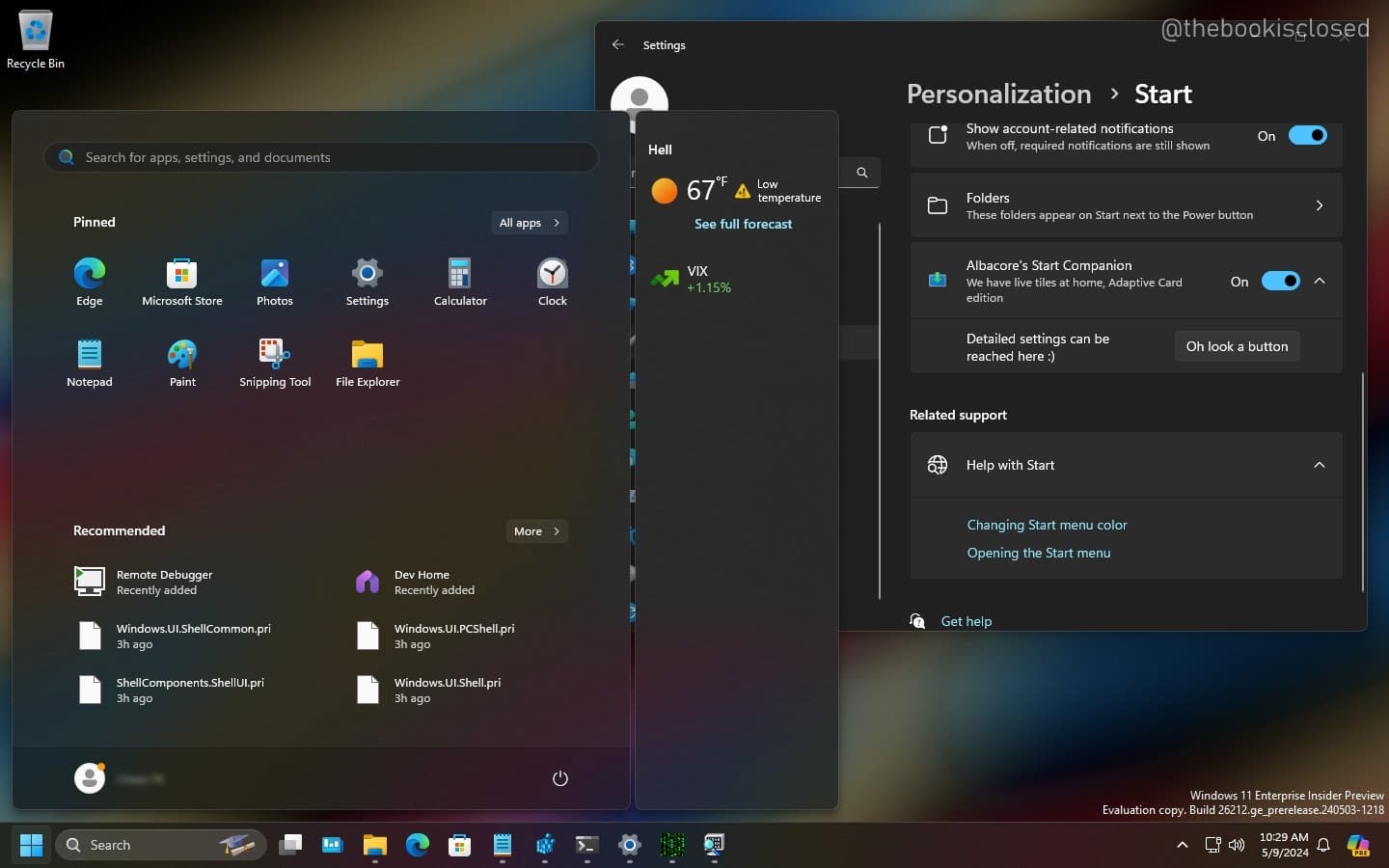
Microsoft makes the Windows 11 Start Menu expandable with Start Menu Companions
Microsoft has made a lot of controversial decisions when it comes to the Start menu in Windows 11, not least of which is the plan to introduce ads. In the latest beta build of Windows 11. However, there are some interesting changes afoot -- notably Start Menu Companions.
While not yet fully operational, Companions are essentially plugins or extensions for the Start menu. The display information -- such as weather or stock prices in a floating panel to the side of the Start menu, will blend the ideas of Live Tiles and Widgets into something new.



