
AlmaLinux 9.4 Beta 'Seafoam Ocelot' now available
The AlmaLinux OS Foundation has officially released the beta version of AlmaLinux 9.4, codenamed “Seafoam Ocelot,” available for various hardware architectures including Intel/AMD (x86_64), ARM64 (aarch64), IBM PowerPC (ppc64le), and IBM Z (s390x). Enthusiasts and developers can access the beta ISOs here.
As with any beta software, the Foundation advises against using this release in production environments. It is essential to follow this guidance, especially when considering upgrades from previous versions, as beta versions can lead to unexpected issues that could disrupt operational systems.

Samsung launches DU9000 98-inch Crystal UHD TV
Samsung has introduced a new giant television to its lineup with the launch of the 98” Crystal 4K TV (DU9000), now available here for $3,999.99. This model joins Samsung’s existing range of 98-inch models, which includes the Neo QLED 8K, Neo QLED 4K, and QLED 4K options, catering to a growing consumer demand for larger screen sizes.
James Fishler, Senior Vice President of Home Entertainment at Samsung Electronics America, noted the shift in consumer preferences, stating, “Just a few years ago, 65” TVs were considered ‘big.’ Today, people want even bigger screens.” He revealed that sales of 98-inch TVs have surged nearly 15-fold over the past year, underscoring a significant trend toward super-sized home entertainment options.

How AI is having an impact on software testing [Q&A]
Artificial intelligence is making its way into many areas of the tech industry, with the introduction of large language models making it much more accessible.
One of the areas where it's having a big impact is software testing, where it allows companies to provide better support to existing software teams and refocus their efforts on development.

More people can now upgrade to Windows 11 after Microsoft lifts Intel Smart Sound Technology compatibility block
After almost two-and-a-half years, an issue that prevented some people with Intel 11th Gen Core processors from upgrading to Windows 11 has finally been addressed.
Microsoft has quietly announced that compatibility issues with Intel Smart Sound Technology drivers and Windows 11 have been "resolved externally". Until now, there has been a compatibility hold in place for devices with both an Intel 11th Gen Core processor and certain versions of the Intel SST driver, but now this has been lifted, it is possible for owners of such systems to upgrade to Windows 11.

Lakka 5.0 retro gaming Linux-based operating system now available with updated LibreELEC and RetroArch
Lakka has announced the release of version 5.0, which includes a series of enhancements designed to improve the retro gaming experience. This new version of the Linux-based operating system is built on the robust LibreELEC 11.0 and introduces a significant update to RetroArch, now at version 1.17.0, which offers a smoother and more versatile gaming interface.
The update brings numerous core updates and additions, enhancing stability and functionality across the platform. Notable new cores include dirksimple for playing Dragon’s Lair, dosbox-core for experiencing classic DOS games, and ep128emu, which emulates several classic computers like the Enterprise 64/128 and Amstrad CPC.

Winning the race against the threat of emerging vulnerabilities
Zero-day vulnerabilities are frequently reported on, but remain a major challenge for organizations, especially when it comes to quantifying the real threat posed by an unpatched instance of a vulnerability.
In 2023 the number of disclosed zero-days, or emerging vulnerabilities (EVs), increased from the previous year, rising from 55 in 2022 to 69 in 2023. While this wasn’t as high as the record in 2021 (with 81 disclosures) the prevalence of zero-day vulnerabilities has been rapidly trending upwards over the last 5 years. To stay ahead of the potentially devastating impact of being breached via an emerging vulnerability, organizations must be aware of how to stay ahead of attackers.

Cloud computing -- The first step to an effective data modernization strategy
Many organizations realize the benefits that lie within the data they collect daily. This modern approach to data empowers businesses to leverage data for innovation and monetization while at the same time enhancing security and privacy. While this may seem like a conundrum as companies have traditionally buried their data deep into IT architecture to prevent it from being accessible, even by the employees, today it is possible to have the best of both. This process starts with the cloud.
The healthcare sector is witnessing a swift surge in cloud adoption. By 2028, it is expected to grow at a Compound Annual Growth Rate (CAGR) of 18.74 percent. This trend of rapid adoption can be seen in the financial services sector too, where organizations are moving to the cloud at an accelerated pace.
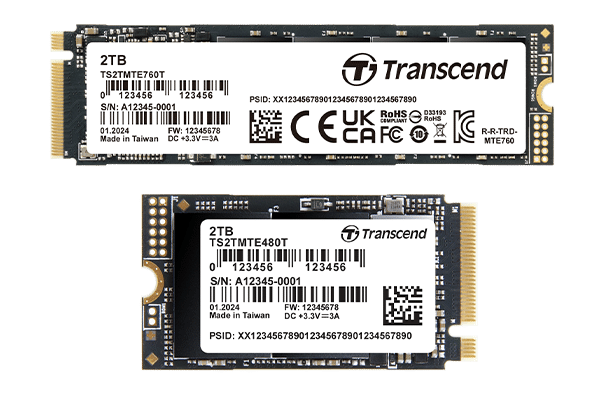
Transcend unveils trio of PCIe 4.0 M.2 SSDs
Transcend has introduced a new lineup of PCIe 4.0 M.2 SSDs, designed to meet the requirements of various industries including AIoT, edge computing, and smart retail. The new models -- MTE760T, MTE480T, and MTE380T -- offer impressive speed, durability, and security.
All three SSD models feature the latest 112-layer 3D NAND technology and utilize the PCIe 4x4 interface, pushing data transfer speeds up to 5,000MB/s. These SSDs are not just fast; they are also equipped with features like LDPC ECC, Power Shield, and Dynamic Thermal Throttling to ensure top-notch stability and reliability across different use cases.
Microsoft 'improves' Windows 11 by bringing ads to the Start menu in the US
In a move which is likely to be greeted with a hostile reception, Microsoft is continuing its obsession with injecting advertising into Windows. The company is using Windows Insiders signed up for Beta Channel to test the controversial addition of ads in the Windows 11 Start menu.
For now, this is a trial which is limited to beta testers in the US, but even if the most negative feedback is forthcoming, it is hard to imagine that Microsoft will back down and not roll out Start menu ads to all Windows 11 users.
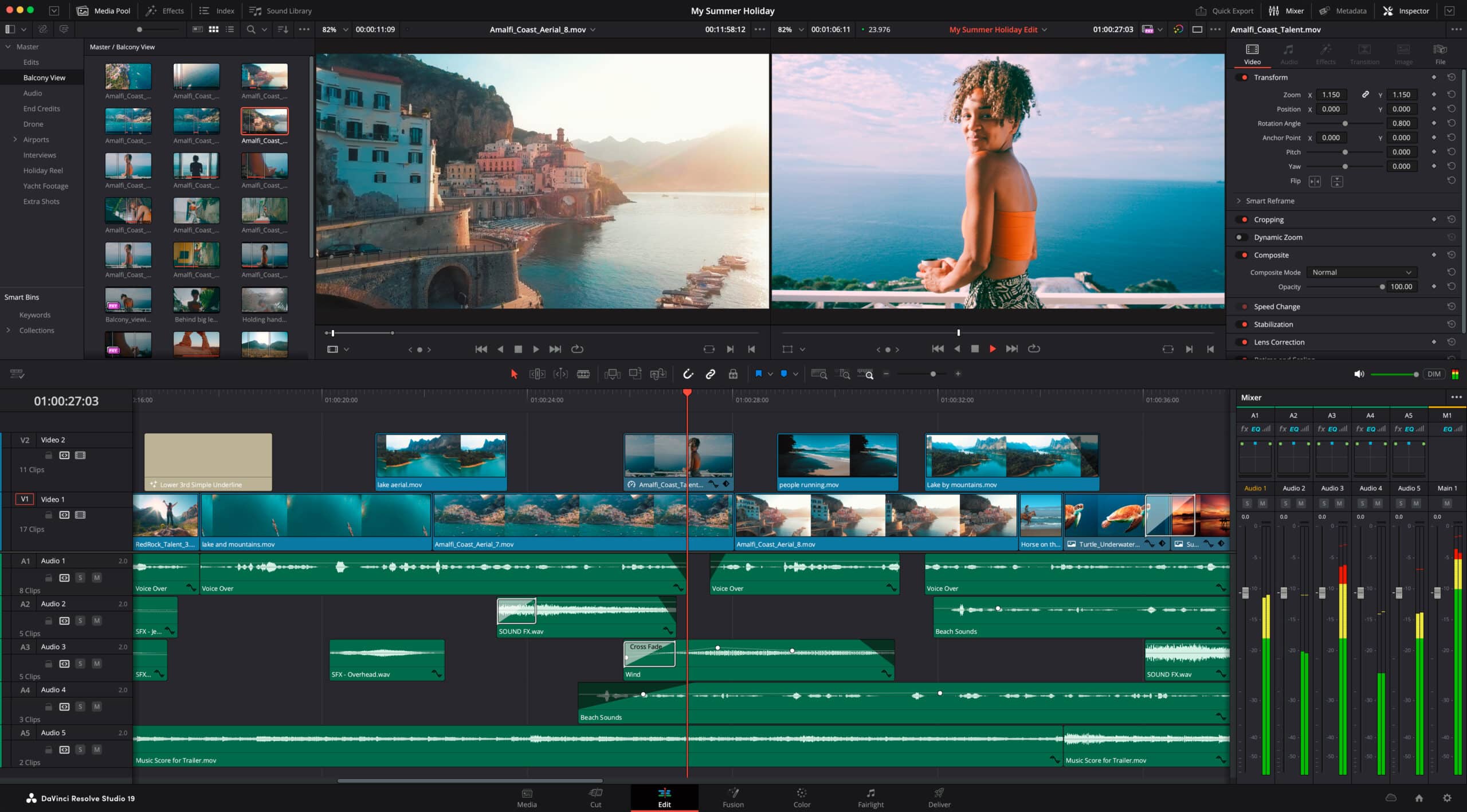
DaVinci Resolve 19 Public Beta now available for Windows, macOS, and Linux with new AI tools
Blackmagic Design has unveiled DaVinci Resolve 19, a massive upgrade introducing new AI-driven features and over 100 enhancements to benefit users across Windows, macOS, and Linux platforms. Available now as a public beta, this latest version brings advanced tools tailored for high-end digital film production and integrates new functionalities for better collaboration within large organizations through Blackmagic Cloud.
Grant Petty, CEO of Blackmagic Design, expressed his enthusiasm for the release, noting, “The new tools in DaVinci Resolve 19 are designed not just to enhance the creative possibilities for filmmakers but also to integrate these advancements smoothly into live production workflows.”

Roku security breach: Over half a million user accounts impacted
In a shocking revelation from Roku, more than 591,000 user accounts have been compromised through credential stuffing attacks, leveraging login details stolen from other platforms. This startling security breach, first detected earlier this year, marks a significant threat as malicious actors accessed 15,000 accounts initially and a staggering 576,000 more in a subsequent incident.
Roku’s investigations have clarified that these unauthorized accesses were orchestrated using credentials obtained from external sources, not from within Roku’s own systems. Surprisingly, no direct compromise of Roku’s systems was identified. Nevertheless, in a handful of cases—less than 400—the attackers made unauthorized purchases of streaming services and Roku hardware using the stored payment methods of the affected accounts. Fortunately, they did not gain access to sensitive payment information like full credit card numbers.

Co-managed IT services -- why your team needs an independent provider
In-house IT teams across every industry can face all manner of challenges and disruptions in their day-to-day processes. While technology is becoming more accessible and demystified, it is important to ensure that you have a team that understands emerging technology. Research from Sharp found that 63 percent of businesses lack critical technology knowledge that could help push their evolution further.
This is where co-managed IT services, which offer a collaborative approach to supporting your organization, can act as a solution. Offering a collaborative approach to IT support with external resources and expertise for managed IT, co-managed IT services can remove some of the strain your in-house team experiences. But what exactly can they assist with?

Ubuntu Linux 24.04 LTS Beta released
Ubuntu enthusiasts and the Linux community at large have a reason to be excited, as Canonical announces the Beta release of Ubuntu 24.04 LTS. Codenamed "Noble Numbat," this release continues Ubuntu's legacy of blending cutting-edge open source technologies into a user-friendly, high-quality distribution.
This latest iteration includes a broad spectrum of Ubuntu products, ranging from the Desktop, Server, and Cloud platforms to various community-driven flavors like Kubuntu, Lubuntu, and Ubuntu Budgie, among others. Aimed at delivering a snapshot of the robust features expected in the final release scheduled for April 25, 2024, the Beta images promise stability and minimal critical bugs.
Best Windows apps this week
Five-hundred-and-ninety in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
The Moment Update 5 for Windows 11 is finally here for most users. It is included in the April 2024 cumulative security update for the operating system.

Why the cybersecurity industry needs to re-frame the AI debate [Q&A]
Conversations around artificial intelligence and the threat it poses to humanity have been building for years. The launch of ChatGPT (or generative AI) nearly a year ago thrust the issue to the forefront of the global agenda.
Discussions have reached such a fever pitch that in April this year, technologists including Elon Musk signed an open letter begging AI teams to pause development. Despite it being widely condemned, the letter underscored how seriously the world is considering AI risks.



