
The impact of evolving AI in cybercrime [Q&A]
Artificial intelligence (AI) has been an evolving trend at the very center of cybersecurity in recent years. However, the release of a wave of new tools such as ChatGPT and Microsoft's Jasper chatbot have sparked fresh concerns about the potential for cybercriminals to leverage increasingly sophisticated technologies for nefarious purposes.
We spoke to Zach Fleming, principal architect at Integrity360, to explore whether AI can be used to create sophisticated malware and hacking tools capable of bringing down entire networks. We'll consider which concerns are valid by highlighting the current state of AI, and we'll explore how security teams can best combat the use of AI in cybercrime.

Why every company should include threat intelligence in their cybersecurity strategy
In the fast-evolving digital landscape, the prevalence of cyber threats has become a stark reality for businesses and individuals. While essential, conventional cybersecurity measures are often reactive and inadequate against sophisticated attacks. This is where Cyber Threat Intelligence (CTI) emerges as a proactive and complementary approach to cybersecurity.
Utilizing CTI helps organizations to protect their systems from potential hazards. It provides a way to cut through the noise and focus on threats relevant to that specific company and industry. However, CTI is more than just a product. It's a program that needs to be evaluated constantly to ensure the correct tools, processes, and people are being leveraged as threats evolve and the company changes over time.

Apple blames iPhone 15 overheating on 'a few conditions' including iOS 17 bug
Since the release of the iPhone 15 range there have been numerous reports of the handset overheating -- sometimes to the point of being too hot to hold. There has been widespread speculation that a new design, as well as the use of new materials, is to blame for not only the temperature issues, but also greater fragility compared to older models.
While Apple is yet to comment on numerous reports that iPhone 15 handsets break more easily when dropped, the company has acknowledged the overheating issue. A bug in iOS 17 has been identified as a cause, but Apple also points to third-party apps including Instagram as being to blame.

The quantum leap: Quantum computing breakthroughs to watch
The classical computer has been the bedrock of computing for over 50 years. That’s going to change soon. quantum computing, which was once a concept limited to fringe scientific papers, is now becoming a mainstream topic.
We’re seeing significant breakthroughs in the headlines which are stoking the flames of conjecture. The truth is, that this technology will bring with it much more than hype and opportunities to breathe life into sci-fi creations. In this article, we’re going to dive into some of the milestones of quantum computing, future goals and, of course, the challenges that we still have to overcome.

How can startups ace their vendor negotiations?
Many startup founders dread negotiations with vendors, especially when they have lean or no procurement teams. Unlike enterprises, startups feel they lack the leverage to secure favorable deals. In this economic environment, everybody is trying to conserve cash. Software expenses are the next big expense after employee expenses for startups.
During COVID, most startups spent a lot on software, and now they are trying to figure out how to cut costs by at least 10-30 percent. The CloudEagle team and I have helped several enterprises and startups negotiate with SaaS vendors. In this dynamic era of innovation and agility, startups are not just the underdogs but the disruptors, visionaries, and change-makers. They bring fresh perspectives, growth potential, and a penchant for rapid decision-making.
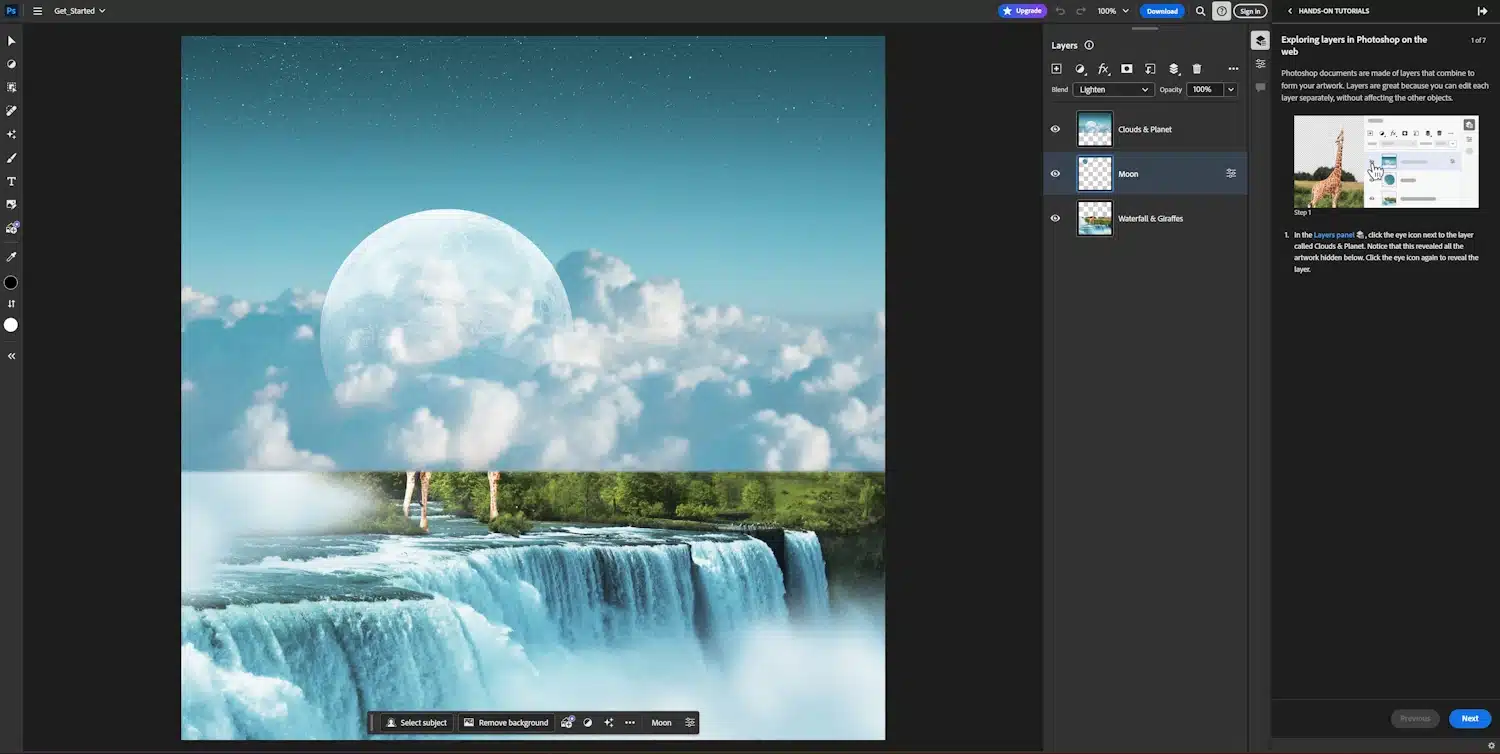
Adobe finally launches the AI-heavy online version of Photoshop
Photoshop on the web is here. Adobe is a name synonymous with photo editing and professional graphic work. So popular is its flagship product, that the name Photoshop has joined the ranks of Google in becoming a verb in everyday language. Home to ever more advanced editing and creative tools, Photoshop has been lacking in one area -- an online version.
But now this changes. Adobe has, at long last, launched its web-based version of Photoshop. A previous version of Photoshop has been available to testers for a little while, but now Photoshop on the web has been made available to everyone. This means that professional-level image editing is now available in your web browser without the need to download Photoshop.

Linux users at risk? Canonical uncovers possible security issue in Snap Store!
When it comes to Linux-based operating systems, users don’t have to worry about security, right? Umm, no. Linux distributions are not infallible. For instance, according to a forum post, Canonical's Snap Store recently hit a big security snag when users discovered some new snaps that might contain harmful code. This scary moment shows how even trusted places like app stores can have problems that could hurt users.
Reacting quickly, the Snap Store team removed these bad snaps from the platform, making sure no one else could find or install them. But they didn't stop there.

Rectify11 is Windows 11 as it should be
Microsoft is actively working to improve Windows 11, and this week it released a big new update to add a wealth of new features to the operating system, including Copilot, its AI-powered personal assistant.
That said, Windows 11 is still far from perfect, and has a lot of design inconsistencies that annoy and frustrate users daily. Rectify11 is a third-party tool that fixes those problems and makes the OS more usable, and it’s just received a notable update of its own.
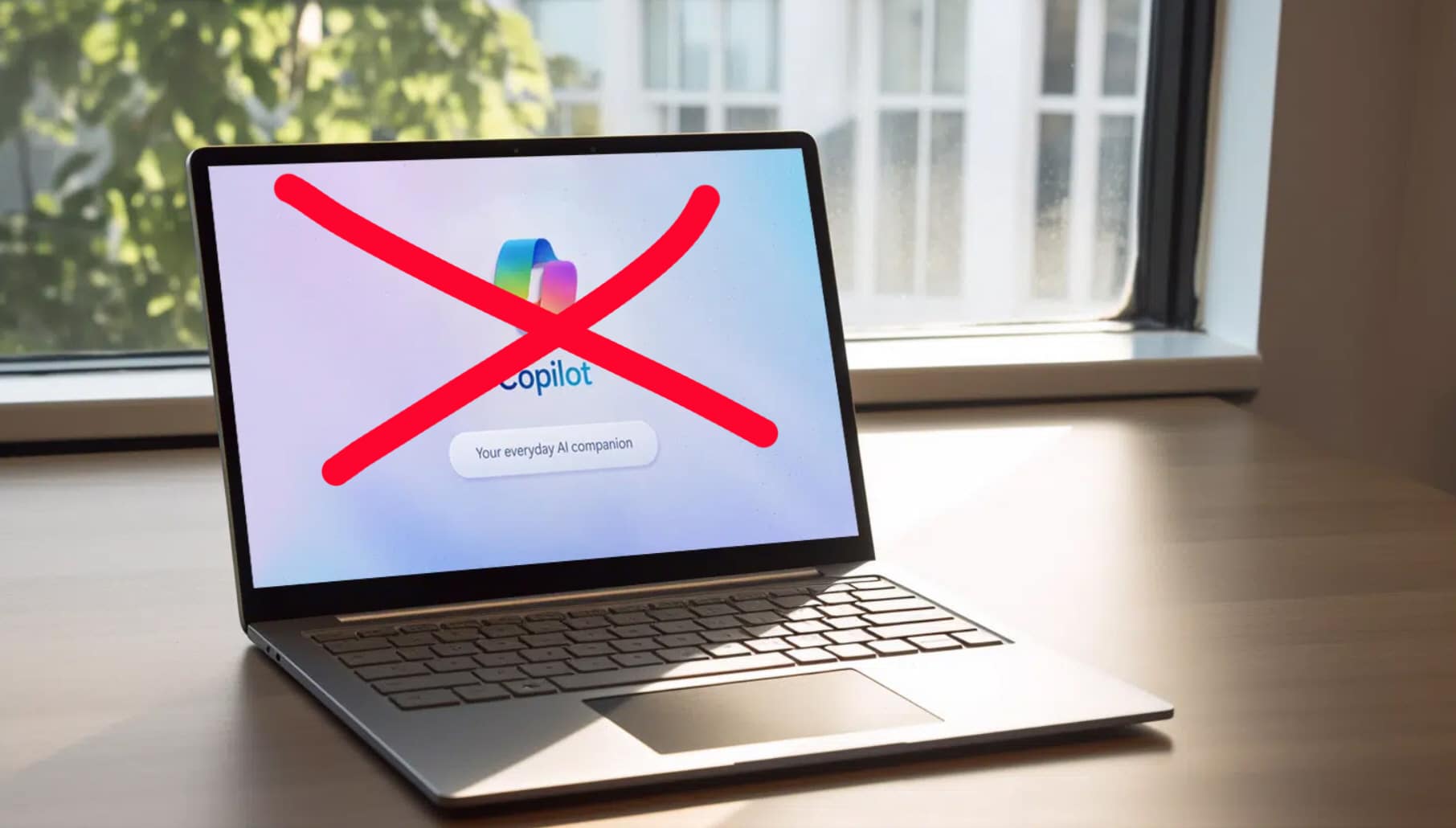
How to remove Microsoft's new Copilot AI from Windows 11
Microsoft began to roll out its latest update for Windows 11 earlier in the week, and although this update comes with over 150 changes, the biggest addition is Copilot, the software giant’s AI-powered assistant.
While this is a handy feature that promises to be everything Cortana wasn’t, not everyone wants AI invading their copy of Windows. Thankfully, it’s easy to remove Copilot from your system.

How to budget for an Agile environment
There are often conversations within Agile communities, about how to accurately predict how much it costs to deliver a software product in an Agile environment.
Budgeting in an Agile environment, where product delivery is incremental and the journey is shaped by feedback, that can be difficult. This is especially the case, when organizations are deep-rooted in fixed time, cost and scope -- and there may be certain conditions where this is still very relevant. Nevertheless, if it’s end user value that you’re seeking (and why wouldn’t you be?) it’s advocated to adopt the following practices and mindsets as alternatives when considering putting a cost on the deliverable.

AI for the good guys: Practical lessons for AI and cyber risk
Threat actors are early adopters. Cyber defense is brimming with uncertainties, but one dynamic you can be confident about is that threat actors will leverage everything available to exploit a target. In 2023, this means the rise of artificial intelligence-enabled attacks, from AI-generated social engineering scripts to powerful automation designed to find and exploit vulnerabilities and spread laterally through systems and networks.
Security teams, therefore need to be prepared to meet the challenge of cloud scale threats on both a technical level and an organizational level. It requires anticipating threats that exist beyond technical vulnerabilities, including, for example, social engineering and DDoS. This is part of the challenge of modern cyber security -- the attack surface comprises not just the entirety of IT infrastructure, its endpoints, and all the data it uses and stores, but also its users. It is too large to be effectively managed manually.
Best Windows apps this week
Five-hundred-and-sixty-two in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft released the fourth Moment update alongside the optional non-security preview update for Windows 11 version 22H2. It includes a preview of Windows Copilot, the new Windows Backup app, and many other changes. While it may be tempting to install it right away, most users may want to wait until the official release in October (at the very least).

What's driving the need for cybersecurity in ESG [Q&A]
Environmental social and governance (ESG) policy sees businesses seek to implement ethical practices to safeguard, not just the business, but its ecosystem of partners and customers and the wider world.
We spoke to Tim Wallen, regional director for the UK, US and emerging markets at Logpoint, to discuss the reasons why cybersecurity needs to be incorporated into ESG reporting, and how this can be achieved.

Mozilla says Firefox Android beta and nightly testers can now try out browser extensions
Mozilla has announced the availability of a limited number of browser extensions for the Android version of its Firefox web browser. The news comes several weeks after the company advised extension developers of the imminent launch of "support for an open ecosystem of extensions" for Firefox on Android.
Now testers who are running the Beta or Nightly builds of Firefox Android are being invited to try out dozens of extensions. At the moment, this is low-key launch as Mozilla is seeking feedback so the system can be tweaked and optimized ahead of a full launch further down the line.
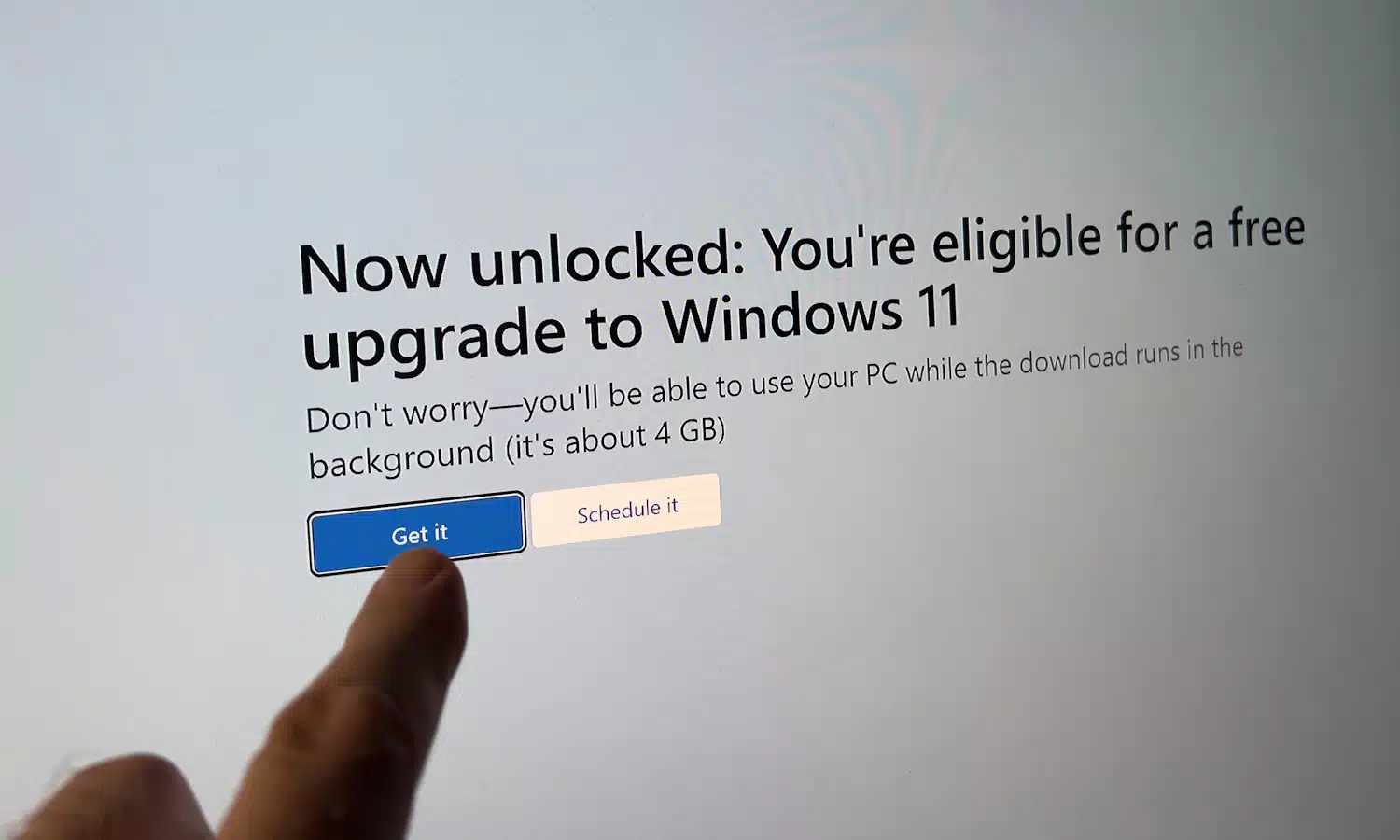
Microsoft ends free upgrades from Windows 7 and 8 to Windows 11
The number of paths for upgrading to Windows 11 for free has just been reduced. Microsoft has officially removed the option to upgrade from both Windows 7 and Windows 8 to Windows 11 without paying.
This should not really come as a surprise, as the ability to upgrade from Windows 7 and 8 to Windows 10 and then 11 free of charge is not something that was meant to last. Microsoft originally said that these upgrade routes would remain available until mid-2016, but the company either "forgot" to disable the option or decided to leave it open to get as many people onto its newer operating systems as possible. But now this changes as explained in a sneakily quiet announcement by Microsoft.


