SEGA is buying Angry Birds-maker Rovio

Following days of rumors, SEGA has confirmed plans to acquires mobile game firm Rovio.
Best known for its Angry Birds range of title, the Finnish firm is being snapped up by SEGA in a $776.2 million (€706 million) deal. The tender offer from the company behind Sonic the Hedgehog is due to start next month, and the acquisition is expected to close in Q2 of FY2024/3.
Install this emergency update from Google to patch an actively exploited Chrome security flaw

Google has issued an emergency update for Chrome which should be installed as soon as possible to plug a vulnerability known to be under active exploitation. The update is available for Windows, macOS and Linux.
In releasing Chrome v112.0.5615.121 for desktop to the stable channel, Google addresses the high severity CVE-2023-2033 as well as issuing other fixes. Described as a "type confusion in V8 in Google Chrome", CVE-2023-2033 is being exploited in the wild, hence the need for the emergency patch.
From a hacker's cheat sheet to malware… to bio weapons? ChatGPT is easily abused, and that's a big problem

There's probably no one who hasn't heard of ChatGPT, an AI-powered chatbot that can generate human-like responses to text prompts. While it's not without its flaws, ChatGPT is scarily good at being a jack-of-all-trades: it can write software, a film script and everything in between. ChatGPT was built on top of GPT-3.5, OpenAI’s large language model, which was the most advanced at the time of the chatbot's release last November.
Fast forward to March, and OpenAI unveiled GPT-4, an upgrade to GPT-3.5. The new language model is larger and more versatile than its predecessor. Although its capabilities have yet to be fully explored, it is already showing great promise. For example, GPT-4 can suggest new compounds, potentially aiding drug discovery, and create a working website from just a notebook sketch.
Microsoft warns of compatibility issues with new Windows LAPS and Legacy LAPS

Microsoft has issued a warning about compatibility issues that can interfere with the new Windows LAPS and Legacy LAPS.
A few days ago, the company released the KB5025239 update for Windows 11 which, among other things, saw the arrival of the new Windows Local Administrator Password Solution (LAPS). The introduction of a new LAPS means that the previous system is now referred to as legacy LAPS.
Spotify is killing Heardle after less than a year

There can be few internet users who are not aware of Wordle, the outrageously popular word-guessing game that is now owned by the New York Times. The game has a huge number of fans all over the world, and it has served as inspiration for many derivatives.
One such Wordle-inspired game is one for music fans, developed by Spotify. Bursting onto the scene in the middle of 2022, the music-guessing game Heardle earned itself an eager following. But disappointment is on the horizon; Spotify has announced that Heardle is closing down.
Defense in the cloud: Embracing technology for a competitive edge

The UK Defense sector is poised for a significant shift towards cloud services in 2023, aimed at unlocking the potential of data and attracting top talent to drive the initiative.
Over the past few years, the Ministry of Defense (MoD) has made great strides in cloud adoption through its MODCloud program, resulting in cost savings and improved data accessibility and security. However, the true value lies in the 24/7 cloud services on offer. The recently published Cloud Strategic Roadmap for Defense sets out the ambition.
Microsoft is testing Windows 11 Start menu ads to push Microsoft 365 and Microsoft accounts
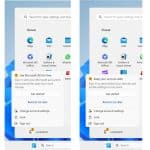
In the latest Windows 11 Dev build, there is a new Gallery in File Explorer for browsing your photos. This is something that is likely to prove popular, but the same build also include some rather more controversial changes.
In Windows 11 build 23435, Microsoft is tinkering further with the Start menu bringing ads to the heart of the operating system. The company likes to refer to this advertising as "badging", but the latest attempt to promote Windows 365 and Microsoft accounts is more likely to be seen as badgering.
Install the latest Microsoft Edge and get two taskbars in Windows!

For anyone who has made the jump from Windows 10 to Window 11, there is a lot of disappointment with the taskbar -- primarily that it is immovable. But whether you have upgraded to Windows 11 or stuck with Windows 10, there is a way to double the number of taskbars available to you. Sort of.
With the very Canary build of Microsoft Edge, there is a new optional sidebar that can be detached from the browser and pinned to the desktop. So if you feel like getting taskbar double vision, here's what you need to know.
Silicon Power launches incredibly versatile USB 3.2 Gen 1 All-in-One Card Reader

Are you tired of constantly switching between different card readers to access data from your various devices? If so, look no further than Silicon Power's All-in-One Card Reader.
This versatile card reader supports many commonly used memory card formats, including SD, microSD, MMC, CF, and MS. With just one device, you can access data from numerous sources, whether it's from your camera, phone, drone, or other digital device. The card reader is capable of reading and writing on up to four cards simultaneously.
Microsoft adds a new photo gallery to File Explorer in Windows 11

Arriving just in time for the weekend, the latest Windows 11 flight for Insiders in the Dev Channel comes with a new feature which will be appreciated by a lot of users.
Build 23435 introduces Gallery, a new addition to File Explorer, which is designed to make it easier to browse your photo collection.
The value of a partner in bridging the gap between organizational IT strategy, implementation, and management

The most important aspect of identifying an IT strategy is gaining an understanding of common strategic goals across the organization while simultaneously keeping the participating business units top of mind. When bridging the gap between organizational IT strategy, implementation and management efforts, legacy IT applications will undoubtedly be impacted. Because of this, there must be a vital analysis of the "AS-IS" state and the "TO-BE" state to ensure comprehension from a technology and process perspective. By engaging stakeholders, organizations can ensure that necessary resource allocations have been made to meet strategic IT goals. This type of tactical partnership helps keep the company's vision at the forefront, even amid a complex and large-scale digital transformation.
Once the implementation stage begins, the deployed technologies should seamlessly align with the organization’s top business objectives. Whether strategic goals fall under the tier of scalability, performance or customer experience, the proper partner can help to identify and achieve business-driven results. The organization also needs to ensure all siloed legacy applications are factored in and shifted into the "TO-BE" state along with any data migration viewpoints. This means that movement strategy must be defined as being big-bank or incremental implementation from application delivery all the way to data migration.
Windows 8 2023 Edition could be the perfect Microsoft operating system
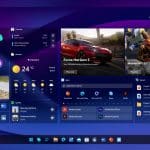
In 2012, Microsoft introduced Windows 8, an operating system conceived as a response to the rise of mobile computing and the increasing popularity of tablets and smartphones. The aim was to provide a unified operating system that would offer a seamless experience across devices, with a focus on touch-based interactions.
It flopped badly, and will forever be remembered as an ambitious but flawed attempt to redefine the user experience in the age of portable computing. But what if it was simply ahead of its time? If you’ve wondered what the tiled OS might look like if it was released today, Windows 8 2023 Edition is the answer.
Convergence of OT and IT systems sees moves to improve security
Best Windows apps this week
Five-hundred-and-thirty-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft is working on integrating a few usability improvements into its Windows 11 operating system. There is a new End Task option when right-clicking on open apps in the Windows taskbar, and a remapped Print Screen key, which will open the Snipping Tool in the future.
Why have cloud when you can have supercloud? [Q&A]

There's been a lot of talk about 'supercloud' recently, but what exactly does it mean? And is it the next big thing that's set to disrupt the technology landscape?
We talked to Amir Khan, CEO and co-founder of Alkira, to find out more about supercloud and what it means for the industry.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.





