
Automation: How law firms can reach new heights in recruitment and profitability
The legal profession is filled with a number of repeatable tasks that are rife for automation, such as estate planning, bankruptcy filing, IP filings, real estate transactions, and M&A filings. In fact, it’s estimated that nearly a quarter (23 percent) of a lawyer’s daily work could be automated.
The amount of time involved in doing manual tasks can put an immense amount of pressure on legal professionals. In a Gartner survey, 68 percent of corporate lawyers said they struggled to manage their workloads. And over half reported some degree of exhaustion.

From details to big picture: Five approaches to improve security
Improving your organization’s cyber security posture is essential to maintain brand trust. The challenge for the C-suite is to look at both the big picture and the finite details, translating your overall strategy for managing risk into actionable processes and priorities that will, over time, lower your risk exposure.
Qualys’ Threat Research Unit (TRU) looked at trillions of anonymized data points gathered from across our customer base to analyze where the biggest risk areas were for businesses. Based on this data, we can see specific areas where you can help your team increase their performance effectiveness, as well as how these changes add up to a significant improvement in security results overall. Building on these details will improve how you manage risk, reduce your attack surface and maintain trust with your customers.

If you're a Discord user, you're probably going to be forced to change your username very soon
It's a decision that could have been taken years ago, but Discord has finally decided to change its odd policy on usernames.
The gaming-focused social chat platform has long forced users to put up with name that end in a four-digit "discriminator", but this is coming to an end. Discord has announced that the four digits at the end of usernames are to be removed, and this means that many users will be forced to choose new handles.

Google is getting cheeky and annoying with ads in the Gmail inbox
Google and advertising go hand-in-hand, but now the company is treading on dangerous ground with a strategy that has quickly angered Gmail users.
Of course, ads in Gmail are far from new -- they have appeared in various places over the years including in the Promotions inbox. Recently, however, users have noticed that advertising emails and promotional messages are being nestled in between other emails in their inboxes.

Cyberattacks seek to exploit trust in Microsoft and Adobe tech brands
The first quarter of 2023 has seen a significant increase in cyberattacks looking to exploit trust in established tech brands like Microsoft and Adobe.
A new report from Avast also finds a 40 percent rise in the share of phishing and smishing attacks over the previous year. Overall, two out of three threats people encounter online now seek to use social engineering techniques, taking advantage of human weaknesses.
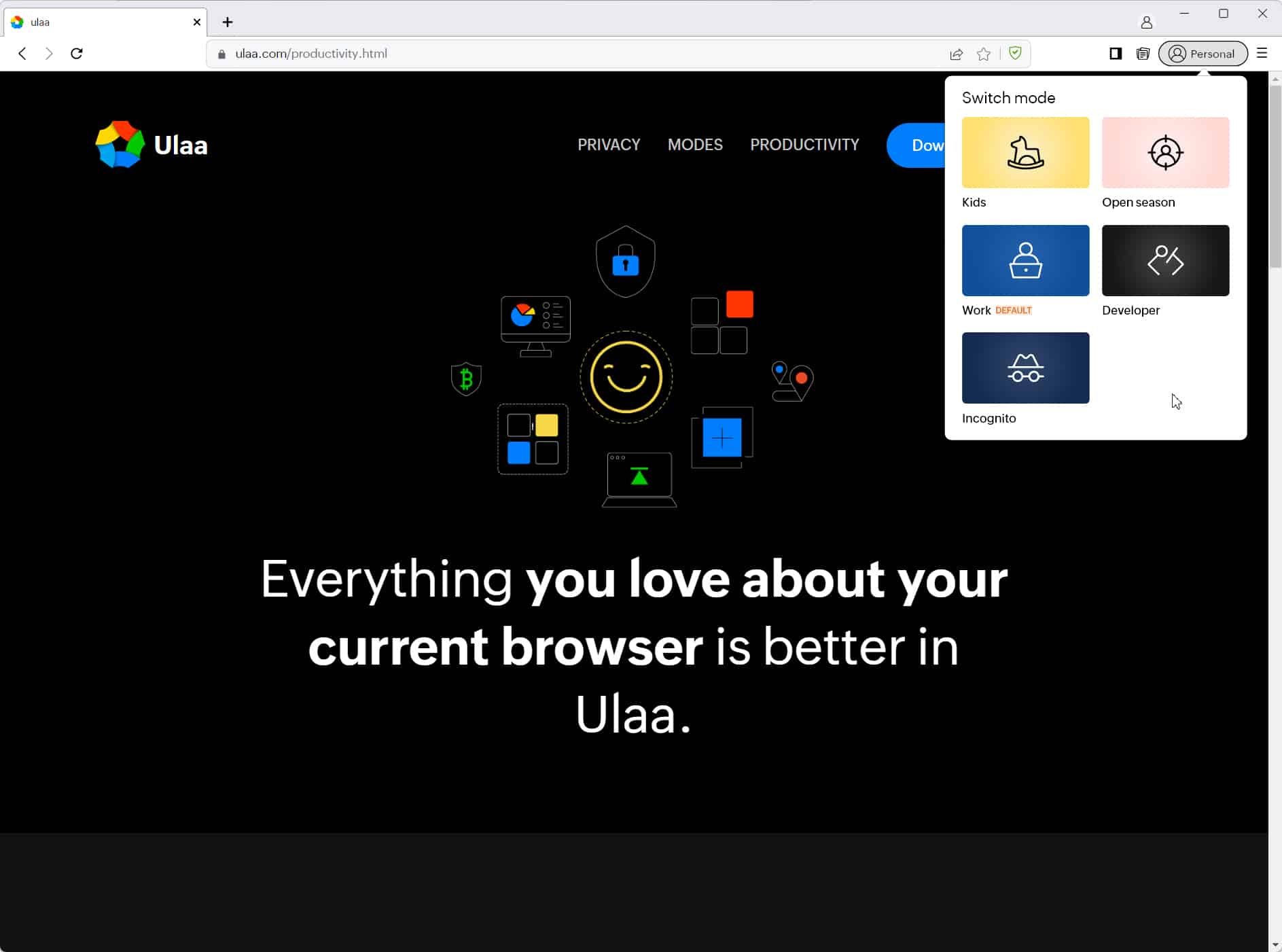
Zoho launches Ulaa, a free privacy-focused web browser for Windows, iOS and Android
Built to specifically address the growing concerns over online privacy, Zoho has launched Ulaa, a privacy-focused browser that comes equipped with pre-installed tools capable of blocking tracking and website surveillance.
Ulaa (a word derived from the Tamil language that means journey or voyage) offers customization options, built-in browser modes, and integrated productivity tools, while ensuring that user data remains confidential. Additionally, users can synchronize their browsing sessions between devices -- whether an entire browser window or a single tab -- enabling seamless use of multiple devices within the same browsing session.
Best Windows apps this week
Five-hundred-and-forty-one in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Windows 12 is still just a rumor, but that is not keeping users from creating Windows 12 wallpapers already. You can check out Wayne's article covering the latest batch of wallpapers here.

Get 'Inflection Points: How to Work and Live with Purpose' (worth $15) for FREE
In Inflection Points: How to Work and Live with Purpose, renowned executive coach and speaker Matt Spielman delivers an energizing and hands-on existential navigational tool that walks you through how to identify what really matters in life and how to achieve it.
Using a powerful life transformation system called the "Game Plan System" -- or GPS -- you will simply use the answers to straightforward questions to reorient your perspective and refocus your efforts on realizing happiness and fulfillment.

Why customers are reluctant to share data online and what you can do about it [Q&A]
Brands are increasingly focussed on providing a good digital experience for their customers, yet many people remain reluctant to share their information with websites.
What are the reasons behind this reluctance? And what can enterprises do to overcome it? We talked to Josh Koenig, co-founder and chief strategy officer at SaaS web platform Pantheon, to find out.

Interest may be growing in Twitter rival Bluesky, but Mozilla is betting on Mastodon
With changes implemented by Elon Musk having disastrous consequences for Twitter, there has been something of an exodus of users. It is "something of an exodus", because while many people are finding new social homes on the likes of T2, Spoutible, Mastodon or -- if they can get their hands on an invite code -- Jack Dorsey's Bluesky, many people are hedging their bets and maintaining something of a presence on Twitter until it becomes a little clearer what the likely successor is to be.
Realistically, the battle seems likely be fought between Mastodon and Bluesky, and Mozilla has just announced an expansion of its investment in the former. The company behind the Firefox web browser has launched its own Mastodon instance, Mozilla.social, in private beta.

Microsoft has broken speech recognition and more with a Windows 11 update
Microsoft has acknowledged that a recent update for Windows 11 is causing "intermittent issues" with speech recognition for some users.
The company says that the problems come after installing the KB5022913 update or later for Windows 11 22H2. As well as affecting speech recognition, the update is also causing issues with expressive input and handwriting. Microsoft has provided details of a workaround, but there is no fix currently available.
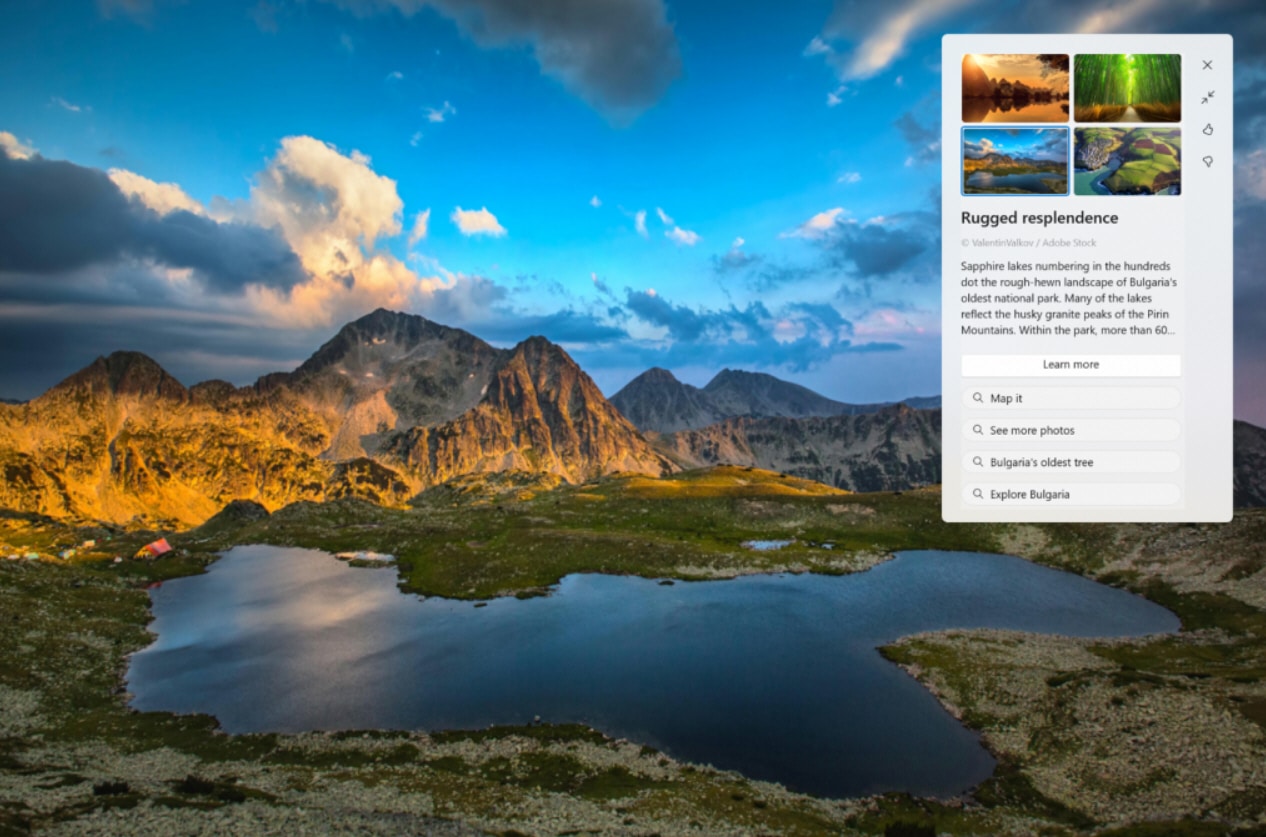
Microsoft releases Windows 11 Build 23451 with new looks for Windows Spotlight
Good news for Windows Insiders in the Dev Channel as Microsoft today releases a new Windows 11 build with some welcome tweaks and new features.
Additions in Build 23451 include a Modernized Details Pane in File Explorer and improvements to Windows Spotlight.
Developing AI models ethically: Ensuring copyright compliance and factual validation
When constructing large language models (LLMs), developers require immense amounts of training data, often measured in hundreds of terabytes or even petabytes. The challenge lies in obtaining this data without violating copyright laws or using inaccurate information and avoiding potential lawsuits.
Some AI developers have been discovered collecting pirated ebooks, proprietary code, or personal data from online sources without consent. This stems from a competitive push to develop the largest possible models, increasing the likelihood of using copyrighted training data, causing environmental damage, and producing inaccurate results. A more effective approach would be to develop smart language models (SLMs) with a horizontal knowledge base, using ethically-sourced training data and fine-tuning to address specific business challenges.
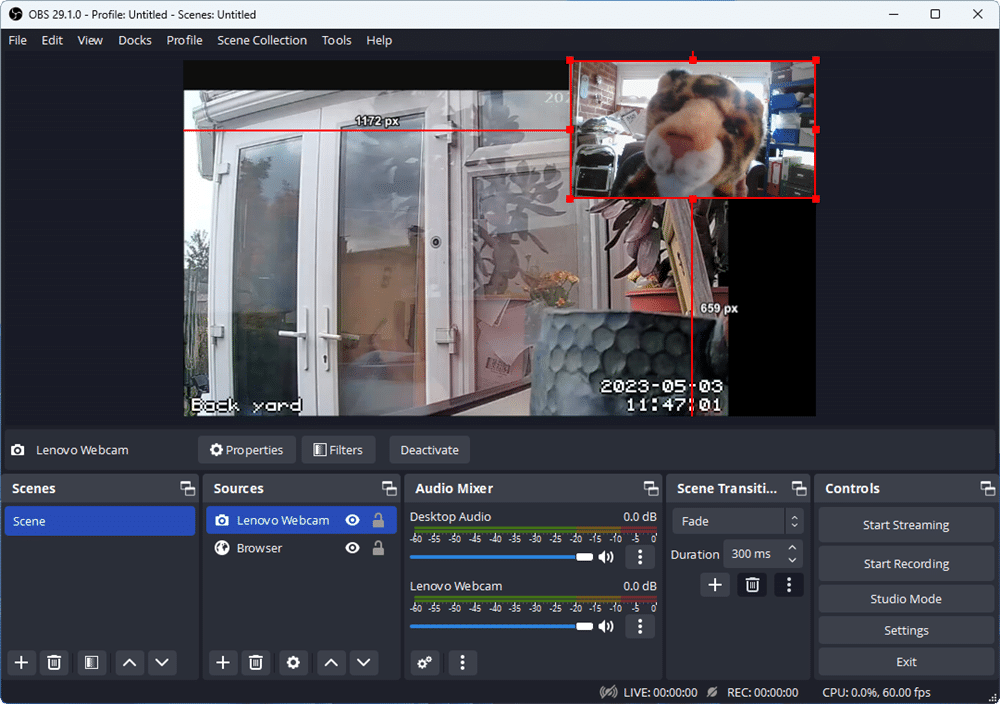
OBS Studio 29.1 expands support for next-generation AV1 and HEVC codecs with YouTube streaming support
Open-source video broadcasting, recording and streaming tool OBS Studio 29.1 has been released for Windows, macOS and Linux.
The chief highlight is added support to allow users to livestream on YouTube using AV1/HEVC over Enhanced RTMP, resulting in lower bandwidth requirements and widening access to 4K60 streaming. The app also makes several improvements to the program’s preferences.

Is it time to make World Password Day a thing of the past?
As another World Password Day rolls around there’s the inevitable debate about whether the days of the password at the front line of security are numbered.
In recent years it has seemed that reports of the password's death have been greatly exaggerated. But as Google extends its rollout of passkey technology it seems that passwords may finally have had their day.


