
Windows 11 development: Chaos is the name of the game
When Microsoft announced that it would release a single feature update per year for its new Windows 11 operating system, one could hear a sigh of relief from many system administrators and also Home users.
The previous strategy of releasing two feature updates per year backfired, as it put a lot of strain on Microsoft but also administrators and users. The gain was not worth talking about usually, as the first feature update of the year did not really include many new features or improvements.
Why enterprises need a complete data strategy [Q&A]
Thanks to eCommerce, IoT devices, social media and more, organizations are collecting larger volumes of data than ever before. But often this is on the basis that they collect everything and work out what to do with it later. An approach that opens them up to risk that data can be misused.
We spoke to open detection and response firm Corelight's CISO Bernard Brantley, who believes organizations can implement a complete data strategy, allowing them to work backward from risk to raw logs and create a supply chain that generates information critical to risk reduction activities.

Riot Games delays release of game updates and patches following security breach
League of Legends publisher Riot Games has announced that it suffered a security breach last week. While it is not clear precisely what was compromised in the social engineering-driven attack, the company says that personal information and player data was not accessed by the hackers.
The impact of the hack is that key updates and patches for numerous titles will be delayed. In addition to League of Legends, games including Teamfight Tactics have also been affected, forcing developers to change the release schedule for hotfixes.

Microsoft Edge 111 adds new Sidebar options, advanced History controls, security features and more
It does not seem all that long since browser version numbers were single digits, but Microsoft Edge has now reached the 111 milestone -- for Insiders on the Dev channel, at least.
Available for Windows, iOS, Android and Linux (with the macOS edition promised "at a later date"), Microsoft Edge 111.0.1619.2 includes a number of interesting new features and settings. Highlights include a new option to personalize top side in the Sidebar, the ability to hide duplicate entries from History, and new protections against unwanted Start page and search engine changes.

It's time to consider the business impact of APIs
APIs need to be discussed in terms of business impact. For too long, the API (application programming interface) has been considered a pure technology topic. But with the need to digitize core business operations and deal with rising security threats, business and technology leaders must elevate API strategic discussions. Meanwhile, organizations need to end the hotchpotch of APIs that act as point solutions and adopt a modern integrated platform approach to APIs that will deliver business optimization and improve the customer experience.
It is essential to look at the effect of APIs on the business, particularly as organizations deal with the three big impacts of war, recession, and inflation, which are putting pressure on all types of business. Moreover, APIs are a central pillar of three trends: digital transformation, improving data access and sharing and enhancing the customer experience, which were identified in a study we recently commissioned with research firm Vanson Bourne.

Netflix will start cracking down on passwords sharing in the coming weeks
At the same time as sharing its Q4 2022 earnings report, Netflix has revealed that its much-hyped crackdown on password sharing will roll out before the end of this quarter.
In a letter to shareholders, the company reveals that more than 100 million households currently share their accounts with others, pointing out that this "undermines our long term ability to invest in and improve Netflix". Having already tested charging for account sharing in Latin America, the plan is to expand this to a much larger proportion of the subscriber base.
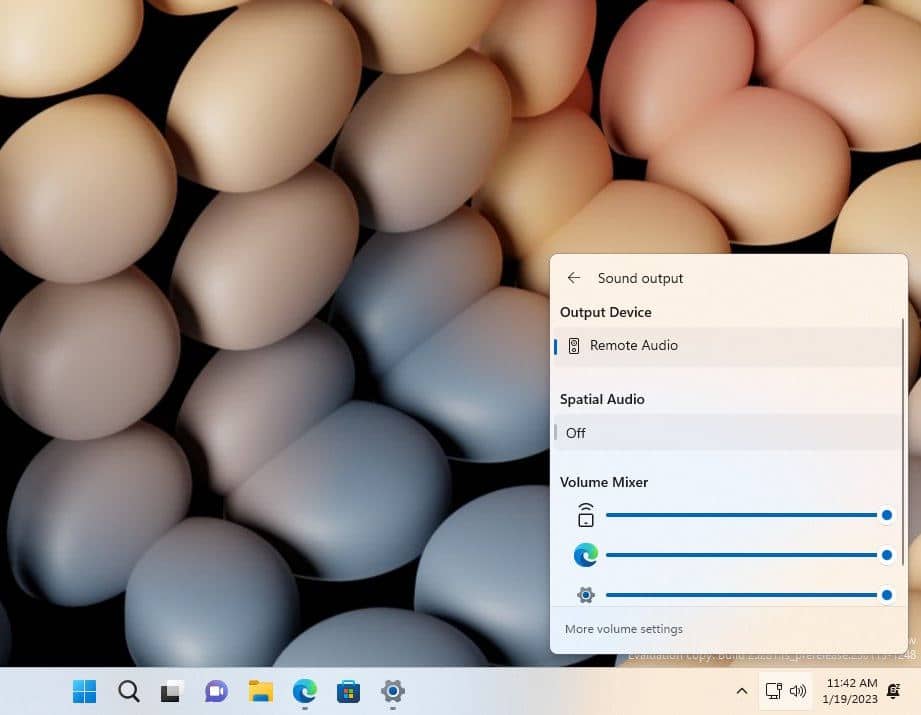
How to activate Windows 11's new, hidden Volume Mixer
If you want to be among the first to try out the latest features and options of Window 11, being part of the Windows Insider program is the place to be. But even if you are signed up to the Dev Channel, there are hidden secrets to unearth, and this is true of the latest release.
For anyone who has Windows 11 Insider Preview Build 25281 installed, there is a new Volume Mixer. While Microsoft has not made it easy to activate the feature, it is possible. Here's what you need to know.

New KB5019274 update for Windows 11 adds new subscription options in Settings and fixes bugs
After taking a month off in December, Microsoft has now released the first preview update of 2023 for Windows 11. The KB5019274 update does not address any security issues, but it does fix various problems and adds new features and options.
The KB5019274 update is available for Windows 11 21H2 and it, among other things, makes it easier to discover and turn on the Windows Spotlight feature. There are important changes in the Settings app, including the arrival of storage alerts for Microsoft OneDrive in the System section and the addition of Xbox subscription information.

The Holy Trinity: Three trends that will take organizations to the next level in 2023
The organizations of today are facing one crisis after another. Whether it’s geopolitical tension or rising inflation, they are being forced to adapt. Faced with squeezed budgets and dwindling resources, these macroeconomic headwinds are causing business leaders to make smarter investments than ever before.
This is causing many enterprises to reassess their strategies and invest more resources in digital transformation, as they seek the ability to do more with less. As this continues to gather pace, we’ll see three key trends emerging, to form a holy trinity of success that will define digital transformation in 2023.

Get 'Windows 11 For Dummies' for FREE!
Windows 11 promises to be the fastest, most secure, and most flexible version of the Microsoft operating system yet. With a promise like that, of course you want to start using it, as quickly as possible!
Windows 11 For Dummies gives you that speed, security, and flexibility by getting you up to date with the latest in Windows. Windows expert and bestselling author Andy Rathbone gives you a helping hand by showing you how to get around the newly updated Windows 11 interface, how to use the new Windows tools like Teams and widgets, and how to use Android apps.
Best Windows apps this week
Five-hundred-and-twenty-six in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft released a new Windows 11 Insider build this week with a tabbed Notepad interface and Windows Spotlight improvements. Windows 11 users may run into "this app can't open" error messages on Windows 11 version 22H2 after system restore operations.

Get 'Learn Python Programming -- Third Edition' ($37.99 value) FREE for a limited time
Learn Python Programming, Third Edition is both a theoretical and practical introduction to Python, an extremely flexible and powerful programming language that can be applied to many disciplines.
This book will make learning Python easy and give you a thorough understanding of the language. You'll learn how to write programs, build modern APIs, and work with data by using renowned Python data science libraries.

4 action items for CIOs in 2023
A CIO's job is to transform the business with technology. That becomes more challenging as the C-Suite tightens the budget with talks of a possible recession in 2023. Add a lack of IT talent and the inability to get the people that you need, and all of the sudden 2023 looks like quite the bootstrapped year. For CIOs, this means it's crucial that we are super-efficient and find innovative ways to save.
So, how do you get efficiency in a market where there's a talent shortage and budgetary restraints, but you still need to get your stuff done? The answers are most likely in adopting cloud managed services, leaning into partner options, AI ops, and automation.

PayPal gets stuffed by large-scale credential attack
Yesterday PayPal began sending out data breach notifications to thousands of its users who have had their accounts accessed via credential stuffing attacks which exposed some personal data.
BleepingComputer reports that almost 35,000 accounts were compromised in the attack which took place between December 6 and December 8, 2022.

Moving Target Defense -- how a military strategy translates to the cybersecurity world [Q&A]
Introduced by the US military in the 1950s, Moving Target Defense (MTD) is the concept of controlling change across multiple system dimensions in order to increase uncertainty and apparent complexity for attackers, reduce their window of opportunity and increase the costs of their probing and attack efforts.
This technique has been translated to the cybersecurity world in recent years, but while the concept is strong, it's a complex strategy that has many drawbacks if not executed properly. We spoke with Avihay Cohen, CTO and co-founder of Seraphic Security, find out more about how this concept is applied to today's cybersecurity strategies, its pitfalls and how to implement it successfully.



