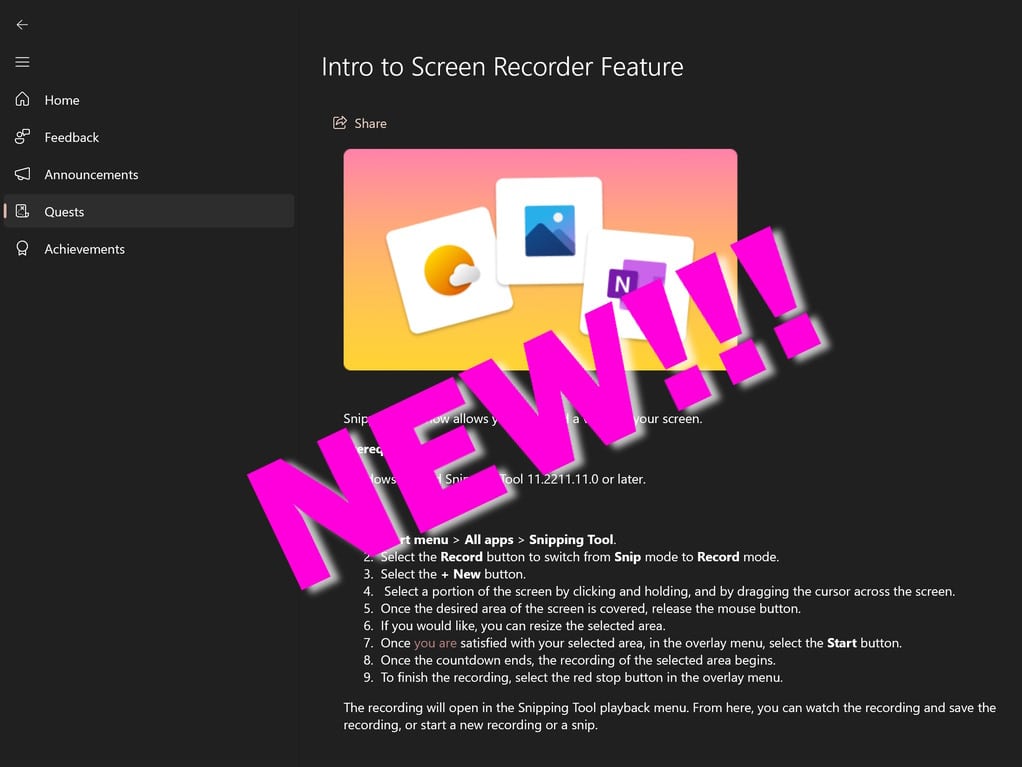
Microsoft gives some Windows 11 users early access to the new Snipping Tool screen recorder
Back in October, Microsoft -- possibly inadvertently -- revealed that Windows 11's Snipping Tool screen capture utility was getting a significant update with the addition of a screen recording option.
After the Surface event at which the news was seemingly leaked, there has been no news about the Windows 11 screen recorder. But now Microsoft has made the new capability available to a select group of users, signalling that a wider roll-out could be just around the corner.

Sling is experiencing a strange sort of outage [Updated]
Online live TV is here to stay, but like its ancestors cable and satellite, it has occasional problems. Nothing is perfect, so you’ll always have a hiccup here and there. This may be one of the stranger problems I’ve encountered though.
Sling, one of the leaders in this new online TV market, is currently roughly half down. No, that doesn’t mean a portion of subscribers lost service, it’s a bit more odd than that.

TP-Link launches Kasa KS200/KS220 smart light switches and EP40A outdoor plug
A smart home is a happy home as far I am concerned. Since going all-in on smart devices in my house, my life has been much improved. I can control my thermostat without getting out of bed, and when I leave a room, I can tell Google to turn off the light. If I hear a bump in the night, I can pull out my phone or tablet to monitor my Wi-Fi cameras. We are living in the future, and it is great.
Today, popular company TP-Link launches a trio of new smart home products under its Kasa branding. The Kasa EP40A is a smart outdoor outlet adapter (perfect for Christmas lights), while the KS220 and KS200 are indoor light switches. All three devices are Apple HomeKit compatible.

Get 'Start With a Win: Tools and Lessons to Create Personal and Business Success' ($15 value) FREE for a limited time
Strengthen your leadership skills and achieve success at work and at home with advice from a proven business leader.
In Start with a Win, CEO of RE/MAX Holdings Adam Contos delivers a powerful exploration of how leaders process information and lead boldly, especially (or even) during times of crisis. Packed with the practical lessons he learned as the leader of one of the most recognized real estate brands in the world, the book shows you how leaders recognize emotion, chaos, and fear and transform those negatives into opportunity.
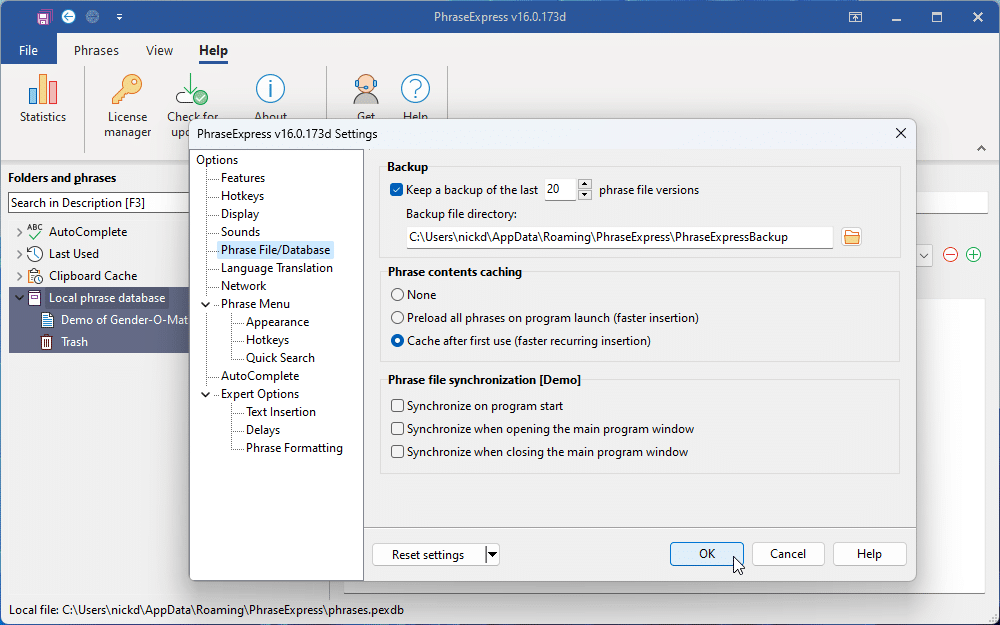
PhraseExpress 16 unveils new look and trigger system to celebrate its 20th anniversary
Bartels Media GmbH has unveiled a major new version of its freemium cross-platform text expander tool with the launch of PhraseExpress 16 for Windows. The new release, which coincides with the software’s 20th anniversary, boasts a fresh new look, new trigger system, improved Edit History feature as well as a new unified phrase file format for using with Mac and iOS builds -- both of which are currently in beta.
The first major change sees the user interface updated with new high-resolution icons to match Windows 11’s more modernized look. Bartels is keen to highlight that the UI has been 'carefully updated' to ensure existing users aren’t left floundering looking for their favorite tools.

Fraud and ransomware dominate cyber insurance claims
Ransomware accounts for 23 percent of cyber insurance claims, while while fraudulent funds transfer (FFT) accounts for 28 percent according to insurance specialist Corvus, which has released its latest Risk Insights Index.
The impact and consistency of FFT is growing, accounting for 36 percent of all claims in the last quarter (Q3 2022), an all-time high. Indeed this metric has not dropped below 25 percent for the past six quarters.

Health workers kept from patient care by tech
An overwhelming 99 percent of healthcare professionals want to be free to focus on patient care, but an abundance of technology is taking time and energy away from their core tasks.
This startling statistic is from a new study by Zivver which interviewed over 6,000 employees across the US and Europe, more than 400 of them in healthcare organizations, about their digital communications and workplace productivity.

Security and access are top issues for data engineers
More than half (54 percent) of respondents to a new survey say securing data with appropriate access rights is one of their biggest hurdles. While almost 60 percent believe their organizations should be placing extra emphasis on data security.
The third annual State of Data Engineering Survey from Immuta also finds that that 89 percent of organizations report missing business opportunities because of data access bottlenecks.

AI-powered gardening app wins IBM Call for Code
This year's annual Call for Code Global Challenge, backed by IBM and the Linux Foundation, invited innovators across the world to help accelerate sustainability and combat climate change with open source-powered technology.
It's been won by GardenMate for creating an app that uses the IBM Watson AI platform to connect gardeners with excess produce to people in need.

The perfect defense: How to stop cyber criminals from scoring
Data is more plentiful, valuable and interconnected than ever before. Unfortunately, this has led to a cyber threat landscape that is increasingly dynamic and costly to business.
Cybercrime inflicted approximately $6 trillion in damages globally in 2021, an annual figure that is set to reach $10.5 trillion by 2025. This is equivalent to the world’s third-largest GDP after the U.S. and China. It is a threat that requires a comprehensive approach to defending, protecting, and recovering data, avoiding vulnerabilities and maintaining business continuity.

Why SaaS needs a holistic approach to security [Q&A]
As organizations move more of their systems to the cloud they face a new range of threats. This combined with a shortage of cybersecurity skills makes securing SaaS systems a challenge.
Galit Lubetzky Sharon, co-founder and CTO of Wing Security, believes that a new more holistic approach, involving employees across the organization, is needed. We spoke to her to learn more.
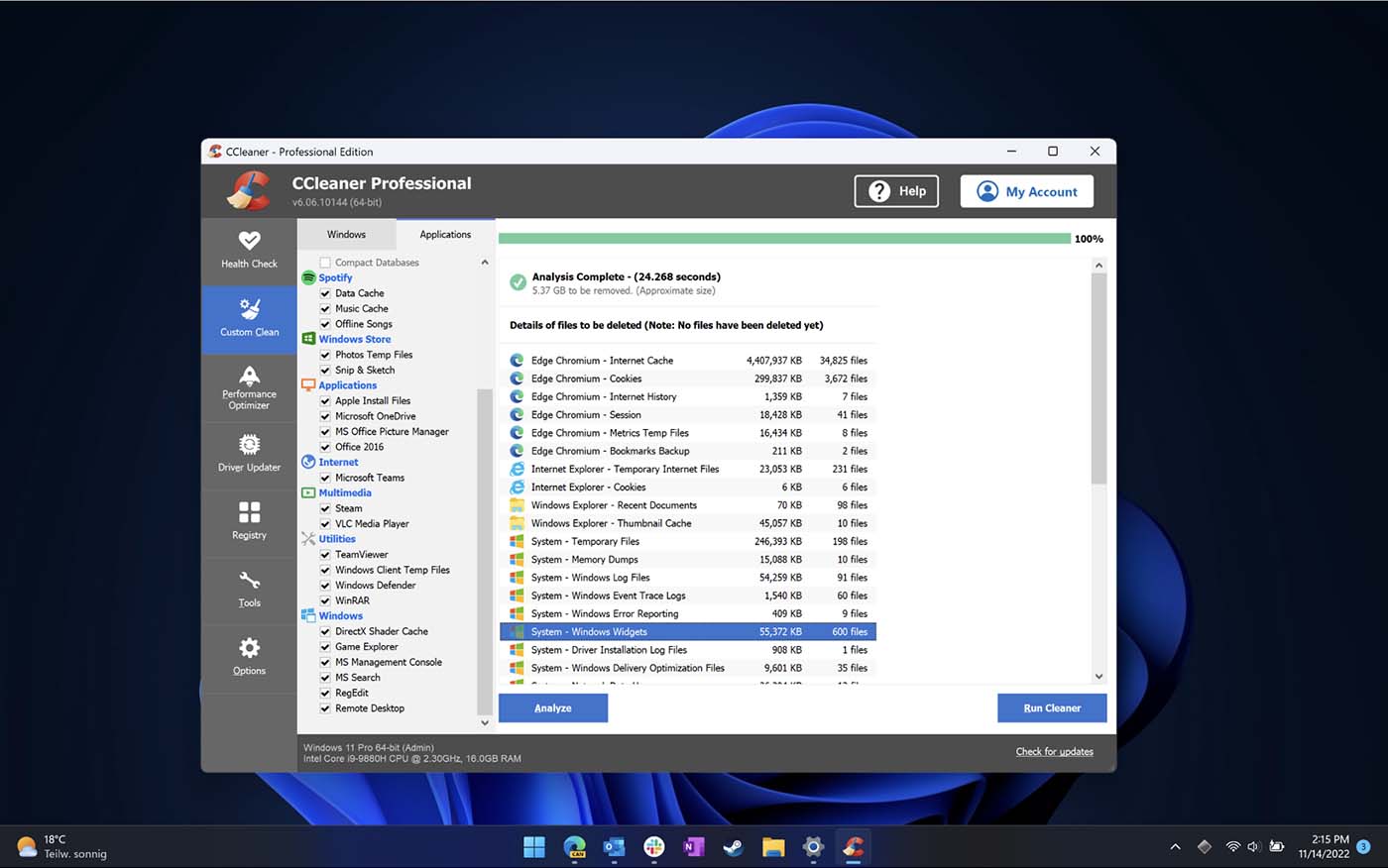
CCleaner's new cleaning rules help optimize Windows 11
Piriform has added some new cleaning rules to CCleaner that help to detect and remove surplus files generated by new Windows 11 features including Widgets, Microsoft Teams, Skype, Microsoft News, Windows Defender, OneDrive, File Explorer, and Microsoft Family Safety.
The update also adds more apps to CCleaner’s cleaning list and improves cleaning in Slack.

Google now lets you search tabs, bookmarks and browsing history from the address bar in Chrome
Google is, of course, best known for its search engine but in a significant update to Chrome, the company has introduced a powerful new way to search tabs, bookmarks and browsing history in the browser.
It has been possible to conduct each of these types of search for some time, but now Google has simplified things dramatically. The change means that Chrome's address bar can now be used for much more than just to search the web; all it takes is the addition of an @.
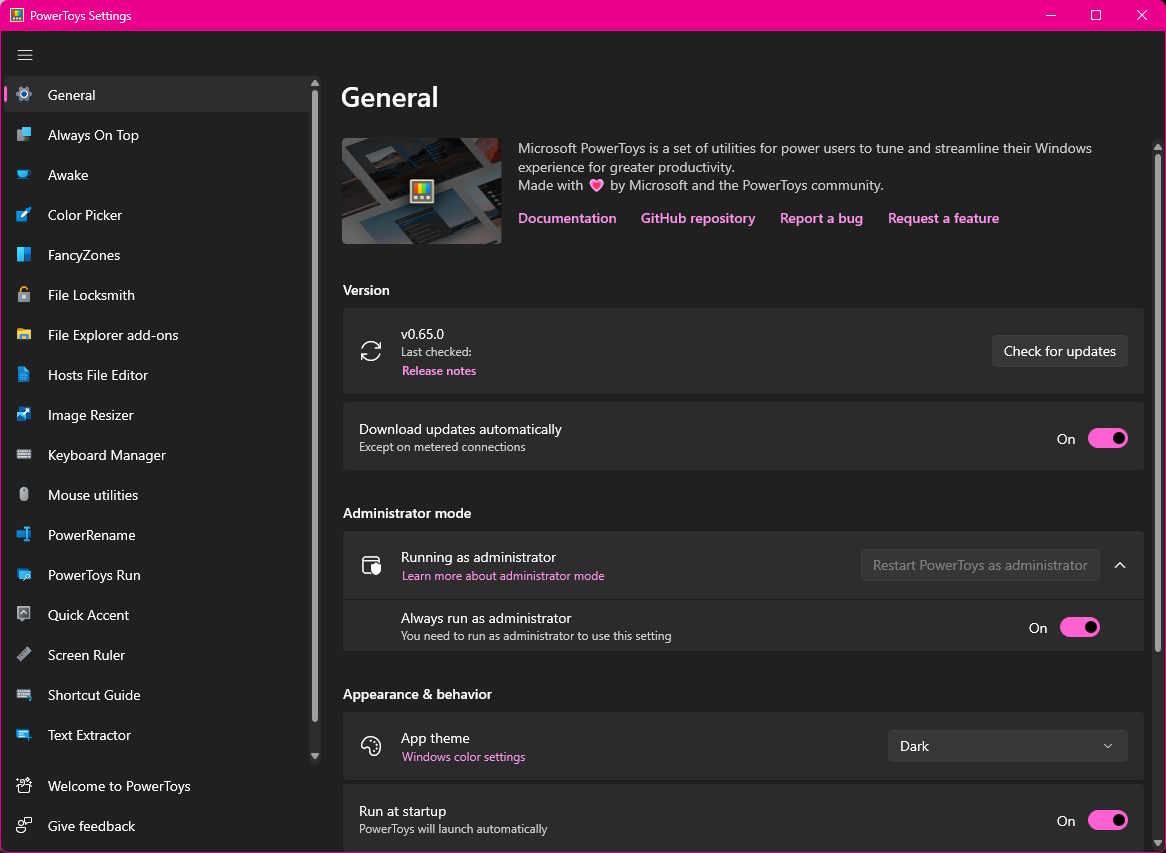
Microsoft releases epic PowerToys v0.65 update with .NET 7 support
PowerToys gets quite a lot of coverage here on BetaNews, and that's because it's one of the most useful and exciting pieces of software out there. We already know that there are plans for a great new quick launcher utility, and while we wait for development to finish, we have the newly released PowerToys v0.65 update to explore.
Although this update does not include any new utilities, it is still an important upgrade because of the number of tweaks and new features that have been added to individual modules. On top of this, the entire codebase has been upgraded to work with .NET 7.

Ubuntu-based Linux Mint 21.1 'Vera' BETA ready for testing
The Linux Mint developers are targeting Christmas as the release date for version 21.1 of the operating system. Before Santa Claus delivers the stable version, however, we will first need a BETA to test for bugs. And so, today, that is exactly what we get.
Code-named "Vera," Linux Mint 21.1 BETA can be downloaded immediately for testing with your choice of three desktop environments - Cinnamon (5.6), MATE (1.26), and Xfce (4.16). Vera is based on the rock-solid Ubuntu 22.04 and comes with Linux kernel 5.15. The stable version will be supported until 2027.



