
How cloud computing turned security on its head
When an organization migrates its IT systems to the cloud -- and builds new applications in the cloud -- it relieves its security team of the responsibility of building and maintaining physical IT infrastructure. The shared security model of cloud dictates that cloud service providers (CSPs) such as Amazon Web Services (AWS), Google Cloud, and Microsoft Azure are responsible for the security of the physical infrastructure. Their customers are responsible for the secure use of cloud resources.
But embracing the cloud for building and managing new applications means security teams cannot deploy the traditional security technologies and processes they’ve long relied on to thwart cyberattacks. Cloud computing represents a paradigm shift in their roles and responsibilities and their approach to protecting sensitive data against falling into the wrong hands.
Microsoft releases KB5016688 update to fix a slew of Windows 10 problems
Microsoft's focus may well be Windows 11 and the upcoming Windows 12, but that does not mean that people who have opted to stick with Windows 10 have been forgotten. Having released a preview of the KB5016691 update for Windows 11, the company has also released KB5016688 update for Windows 10.
Available for Windows 10 versions 20H2, 21H1 and 21H2, the KB5016688 update is a preview of the cumulative update that will be released next Patch Tuesday. Although this is a non-security update, it fixes a large number of issues with Windows 10

YouTube TV let me watch New York Mets games from the middle of the Atlantic Ocean while on a Royal Caribbean cruise
With COVID-19 pretty much over now, I decided to take my first vacation since the pandemic started (I am vaccinated and double-boosted). And so, I booked a Royal Caribbean cruise to Bermuda (Enchantment of the Seas) that left from Baltimore. I returned from that vacation this week -- the trip was quite lovely, as is typical with Royal Caribbean.
Believe it or not, this was my 10th Royal Caribbean cruise! Normally, I would use it as an opportunity to unplug from the internet and relax offline. This time, however, things were a bit different. You see, I adopted a chihuahua from a shelter a few years back, and I wanted to keep an eye on her by way of Wi-Fi cameras. She's a great dog, but very scared and skittish -- I needed to know she was OK at all times.

Know the benefits of becoming a sustainable business
In business, sustainability refers to doing business without negatively impacting the environment, community, or society. Sustainability in an industry generally addresses two main categories: The effect business has on the environment and the effect business has on society.
Making environmentally conscious decisions is unavoidable for business and sustainability because it can impact the environment.

How to ensure a smooth transition as a new CTO
Beginning a CTO role can be a daunting prospect, especially if you’re completely new to the company. There are lots of plates to spin, people to meet and ways of working to get used to, so it’s crucial you’re on top of your game from the outset.
In effect, those first few months in the position are about learning as much as possible in a short space of time. This learning process should encompass all elements of the business, including the company itself, its culture and your colleagues. Below, we have outlined six key areas that new CTOs can focus on, to make your transition into the role as smooth as possible.

Google to clearly label healthcare facilities that offer abortions
In the wake of the overturning of Roe v Wade earlier in the year which made it much more difficult for many people to access abortions in the US, numerous tech company leapt to offer help and support to their customers and employees. Having already introduced a feature that automatically deletes abortion clinic visits from location history, Google is now taking things a step further.
In both Google Search and Google Maps in the US, the company is adding labels that make it clear that particular medical facilities provide abortion services.

TP-Link Deco XE75 Pro Wi-Fi 6E tri-band mesh system has Multi-Gig Ethernet
Back in April, we told you about the Deco XE75 -- an affordable Wi-Fi 6E tri-band mesh system. TP-Link's AXE5400 wireless networking system comes with two 802.11ax access points, each with three Gigabit Ethernet ports. At just $299.99, it is quite a great value.
Today, TP-Link launches a "Pro" version of the Deco XE75. Yes, the name of this product is "Deco XE75 Pro." Why exactly does this new product get a "Pro" moniker? Well, it has one significant upgrade over the non-Pro variant -- a multi-gig port. You see, rather than have three Gigabit ports, each access point features two Gigabit LAN ports and one 2.5G WAN/LAN port.
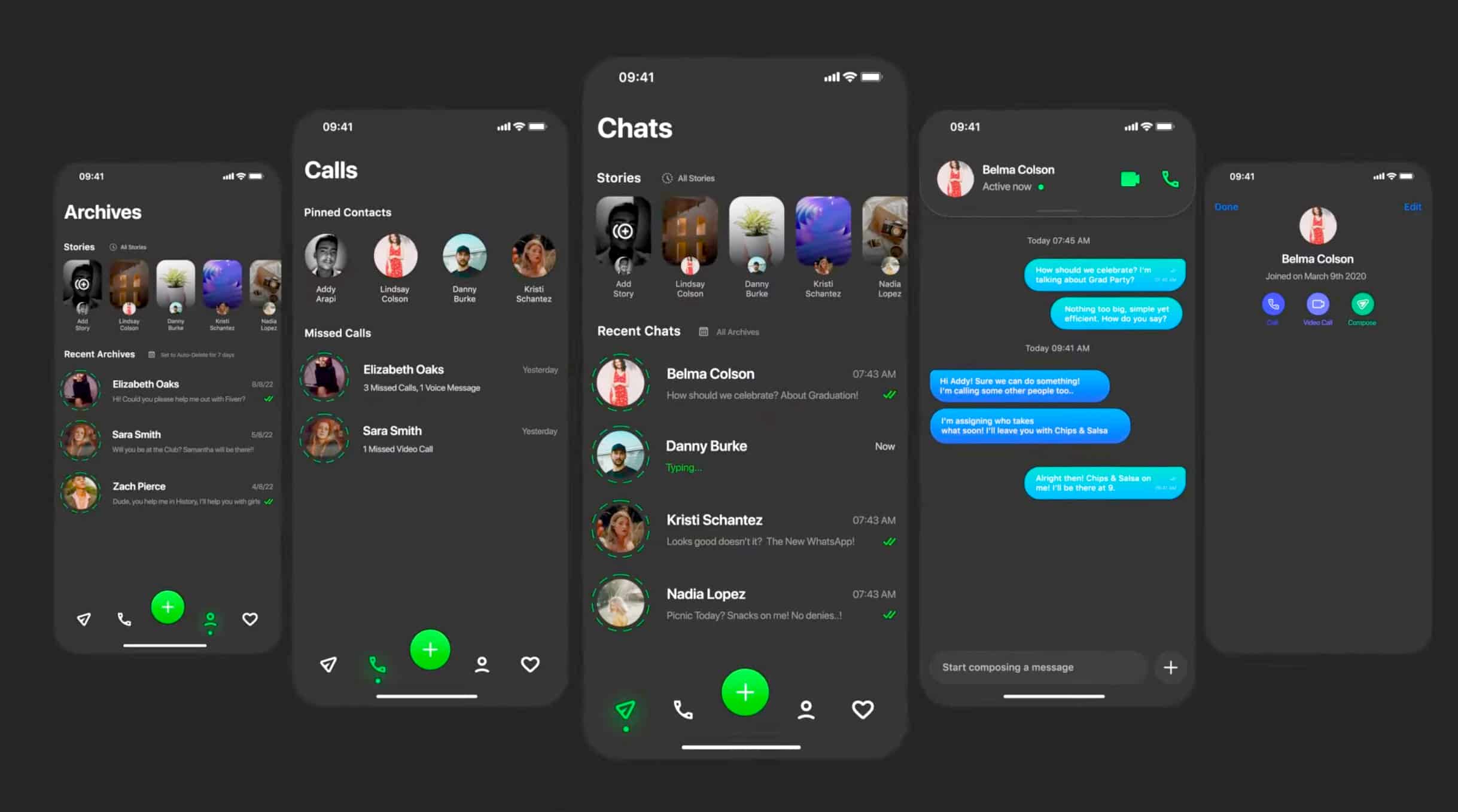
This is the redesign WhatsApp desperately needs
WhatsApp is a great messaging tool, and one that I use daily, both for individual and group chats. Meta has added new features to it over time, with yet more welcome additions on the way, but it’s long overdue a full redesign.
If you’ve ever wondered what kind of makeover the service could benefit from, we have the answer for you right here.
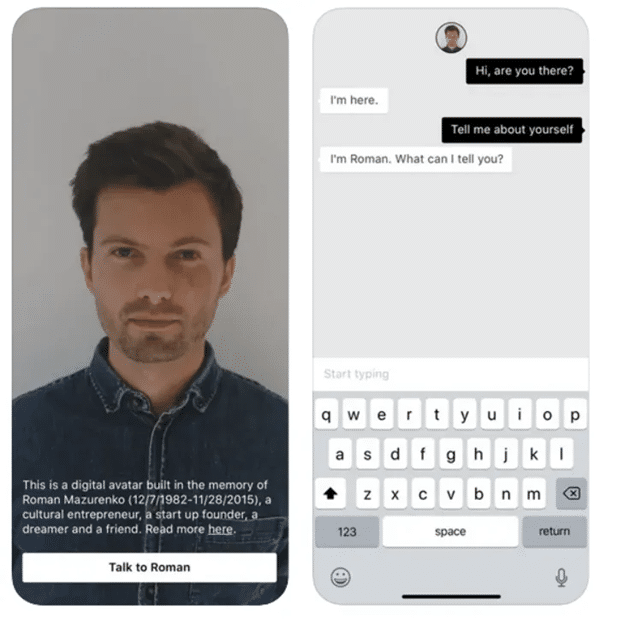
Digital afterlife: A chance to live forever or never rest in peace?
Have you ever thought about what happens after your physical shell expires? What legacy will you leave and what becomes of it with time? We can give our tangible belongings to friends and family. If the work is copyrighted, the protection will usually extend well beyond the author’s lifespan.
The law has, however, yet to catch up with the times as we also share, store and use tons of information online. That encompasses our digital identity, which is often left unattended after death, lingering at the digital graveyard at the mercy of tech giants.

Should you invest in the tech industry in a recession?
What makes a good investment during a recession? Is investing in the tech industry safe when the economy is low? Read on to learn how to use what previous recessions have taught us to choose your tech investments wisely.
If we want to know how the tech industry stands to weather the future, the first step is to look to the past. Let’s take a look at the last three U.S. recessions and their effects.

Nextcloud works with governments to create MS Office rival for the EU
The European Union's relationship with big tech companies has long been a fractious one. Its Digital Markets Act is aimed at reigning in their power and, among other things, it's credited with forcing Apple to adopt the USB-C standard.
In the latest development a number of European governments are working with Nextcloud to create a 'digitally sovereign' office platform, the aim being to help governments regain their independence from a small number of tech giants and allow them to confidently roll out digitization efforts.

Three steps to making a cloud smart investment
Today, many businesses are transitioning to cloud to modernize environments, improve system reliability, advance their digital business initiatives, and support the new realities compelled by the pandemic, such as working from home. According to Gartner, "cloud is the powerhouse that drives today’s digital organizations". In fact, its growth has been little short of meteoric, with a staggering $494.7 billion spend and 20.4 Percent predicted growth in 2022.
Cloud is driving increased security, increased performance, better customer experience and better value for money in tech investment, and it continues to be widely adopted by global business. But organizations are becoming more prudent and strategic in their cloud investments, centering desired business and technical outcomes when selecting the cloud model that best fits their individual needs.
Best Windows apps this week
Five-hundred-and-five in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
The first feature update for Windows 11 is likely called the Windows 11 2022 Update. Whether that is Microsoft's new naming scheme for future Windows 11 updates remains to be seen though.

Ransomware attacks top 1.2 million per month
A new report from Barracuda finds the volume of ransomware threats detected spiked between January and June of this year to more than 1.2 million per month.
Researchers have also seen a spike in the number of service providers that have been hit with a ransomware attack. The main targets, however, are still five key industries: education, municipalities, healthcare, infrastructure, and financial.

Tackling cybercrime and the threat of 'script kiddies' [Q&A]
Major cyberattacks still have the power to make headline news, yet reporting and indeed conviction rates for cybercrime remain low. It's perhaps not surprising then that rising numbers of young people are getting involved in these illegal activities.
We spoke to Simon Newman, International Cyber Expo Advisory Council member and CEO of the Cyber Resilience Centre for London, to get his views on what needs to be done to improve reporting and change the mindset of 'script kiddies' for the better.



