
Enterprises struggle with application modernization
According to a new study 93 percent of enterprise IT leaders say the application modernization process is challenging due to staffing, tools, training and other issues.
The survey from Asperitas finds 30 percent of IT leaders say identifying the right tools and technologies is the most difficult part of the process, while 20 percent say it's finding staff with the right experience.

Microsoft 'fixes' language bar problems caused by KB5014666 update
It has not gone unnoticed that Microsoft's quality control for updates for Windows has been found somewhat wanting of late, particularly when it comes to Windows 11. We have reported numerous times about problems caused by updates, and then the subsequent fixes -- and, sometimes, additional issues they cause -- that Microsoft releases.
Windows 10 users are also affected by problematic updates, and the recently released KB5014666 update caused issues with printing. But this was not the only problem caused by this devilish update; it was also found to lead to problems with the Input Indicator and Language Bar. Now Microsoft has issued a fix -- of sorts.

Microsoft releases Windows 11 Build 25174 with new Game Pass widget
Last week, Microsoft’s new Windows 11 flight, Build 25169 for Windows Insiders on the Dev Channel, came with a lockdown feature for IT administrators and a new Windows Spotlight theme.
Today’s release, has one main new feature -- a Game Pass widget -- and a good number of fixes and improvements.

OWC Envoy Pro FX external SSD now available in 4TB capacity
Last year, in the beginning of 2021, we told you about the Envoy Pro FX -- an external solid state drive from OWC. What made this particular SSD special was its use of two chipsets to maximize compatibility with both Thunderbolt and regular USB-C. The drive even comes with a dongle to make it compatible with USB-A.
And now, in 2022, OWC is giving the Envoy Pro FX a capacity boost. While the SSD remains the same in all other ways, as of today, it can now be had with a 4TB capacity option. Previously, the drive was limited to 240GB, 480GB, 1TB, and 2TB sizes. As you can see, 4TB is a pretty significant increase.

Get 'JavaScript from Beginner to Professional' ($28.99 value) FREE for a limited time
This book demonstrates the capabilities of JavaScript for web application development by combining theoretical learning with code exercises and fun projects that you can challenge yourself with.
The guiding principle of the book is to show how straightforward JavaScript techniques can be used to make web apps ranging from dynamic websites to simple browser-based games.

94 percent of companies have had security incidents with production APIs
According to a new report 94 percent of companies have experienced security problems in production APIs in the past year, with 20 percent saying the organization suffered a data breach as a result.
The latest State of API Security Report from Salt Security also finds that found that API attack traffic has more than doubled in the past 12 months with a 117 percent increase. In the same period overall API traffic grew 168 percent, highlighting the continued explosion of enterprise API usage.

Industrial systems under threat from wipers and IoT botnets
The latest OT/IoT security report from Nozomi Networks shows that wiper malware and IoT botnets dominate threats to industrial control systems.
Researchers have observed the robust usage of wiper malware, and seen the emergence of an Industroyer variant, dubbed Industroyer2, developed to misuse the IEC-104 protocol, which is commonly used in industrial environments.

Ransomware contained in typosquat Python scripts
Researchers at Sonatype have identified multiple malicious Python packages that contain ransomware scripts.
The packages are named after a legitimate, widely known library called 'Requests', with names like 'requesys', 'requesrs' and 'requesr', in order to trick developers into installing the wrong version.

Microsoft beefs up Defender security with new Threat Intelligence and External Attack Surface Management tools
Microsoft has launched two new security products, bolstering the capabilities of Microsoft Defender. The company says that the aim of the two tools is to help organizations lock down their infrastructure and reduce their overall attack surface.
The tools, Microsoft says, also provide "deeper context into threat actor activity" making it easier to predict malicious activity and secure resources. Microsoft Defender Threat Intelligence works by mapping the internet every day, so that security teams have the data needed to understand current attack techniques, while with Microsoft Defender External Attack Surface Management lets security teams see their system as attackers do.

Plugable USBC-VAMETER3 is an upgraded USB-C voltage and amperage meter
Last year, we told you about Plugable's second generation USBC-VAMETER -- a dongle with an OLED screen that can monitor USB-C voltage and amperage. The second gen variant was similar to the original, but it added a rotatable screen orientation -- a very welcome addition.
Today, Plugable launches the third generation of its useful dongle. Called "USBC-VAMETER3," it has the same rotatable screen technology found on gen 2, but it gets some power upgrades. The third gen model now supports 48V (4.5V-50V) compared to 20V (4V-20V) on the gen 2 model. The third generation variant also supports 240W compared to just 100W on its predecessor.

ADATA launches LEGEND 960 PCIe Gen4 x4 M.2 2280 SSD for PC and Sony PlayStation 5
M.2 solid state drives are great options for both laptops and desktop PCS. Hell, if you add such a drive to a compatible enclosure (such as this one), you can transform it into a portable SSD too. But did you know you can upgrade the storage of your PlayStation 5 video game console by adding an M.2 drive?
Today, ADATA launches a new M.2 SSD that is designed for both PCs and the PlayStation 5. Called "LEGEND 960," this PCIe Gen4 x4 M.2 2280 SSD offers impressive speeds and will be initially offered in your choice of two capacities -- 1TB and 2TB. ADATA promises a 4TB variant will be available at the end of August.
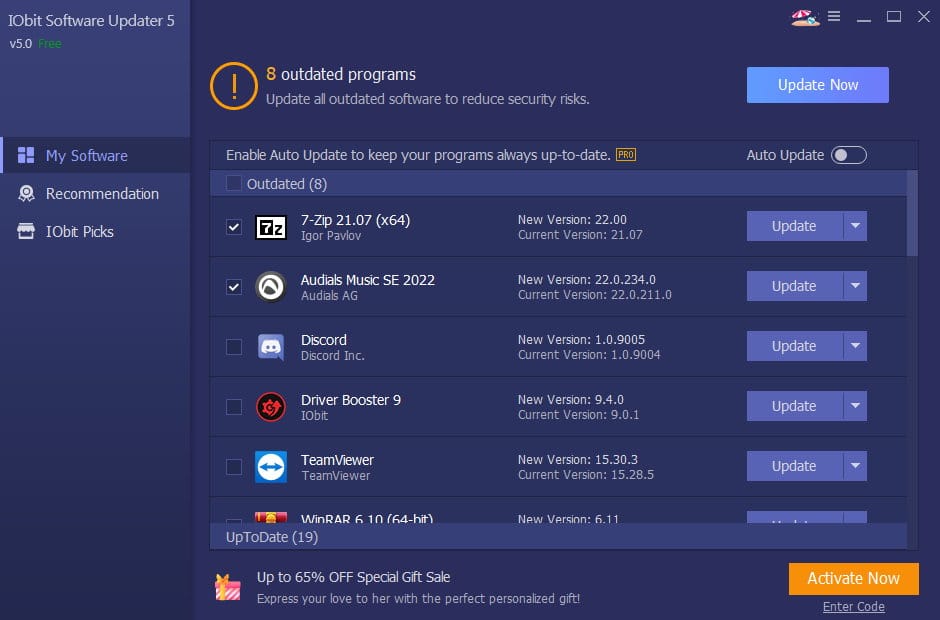
IObit Software Updater 5 keeps your apps updated to boost system security
It is very easy to keep Windows up to date -- so easy, in fact, that you hardly need to do anything. Just make sure that the Automatic Updates feature of Windows Update is enabled, and everything will happen in the background. IObit Software Updater does much the same for the apps you have installed as well.
While there are some apps that will update automatically -- including, but not limited to, those installed from the Microsoft Store -- it is certainly not the case for all software. And this is where IObit Software Updater can help, ensuring that all of the software you have installed is up to date, so you not only benefit from the latest features and options, but also the highest level of security. IObit Software Updater 5.0 is now here, complete with support for scores of additional applications.

Ransomware uses malicious macros to infect target systems
A new study reveals that 87 percent of the ransomware found on the dark web can be delivered via malicious macros in order to infect targeted systems.
The research from Venafi, in partnership with criminal intelligence provider, Forensic Pathways, looked at 35 million dark web URLs and forums to uncover a thriving ransomware community with highly damaging macro-enabled strains readily available.

How to use SIGKILL to rapidly terminate containers in Kubernetes
Originating from Linux, which uses a Unix operating system, SIGKILL is a common command that developers use to terminate absolutely any process. Most commonly, if anything needs to be shut down immediately as it's causing damage to the system itself, then SIGKILL is the go-to signal to use.
Alongside Linux, SIGKILL has also found itself into any developer platform that manages container systems, with the most popular example of this being Kubernetes. As one of the most drastic signals that you can execute, SIGKILL will instantly terminate a process, without giving the system the opportunity to block or ignore the signal. With this, absolutely any processes that are connected to the process you’ve killed will also terminate.

Cyber insurance may be cyberficial, but…
Insurance might be one of the least liked, but most valued purchases within a business when you need to use it. In previous decades, it was needed against fire, theft, and other tangible threats to a business, yet as cyber-attacks are becoming an inevitable, frequent occurrence, the demand for cyber insurance is at an all-time high.
However, qualifying for cyber insurance coverage is easier said than done. Businesses not only have to manage the soaring cost of premiums, but also meet a long list of complex criteria that deems their current security strategy and implementation eligible for financial protection.


