
Google makes Linux more secure
Google has taken a proactive step to bolster Linux security with the introduction of the counted_by attribute for flexible array members. This enhancement addresses a critical vulnerability in C programming related to buffer overflows, particularly those involving flexible array members whose sizes are determined at runtime.
Buffer overflows have long been a notorious source of security issues in software development. While sanitizers have mitigated some of these vulnerabilities by automatically inserting bounds checking, flexible array members have remained a challenging exception. The size of these arrays is typically opaque to the compiler, making it difficult to perform bounds checking outside the allocation function.
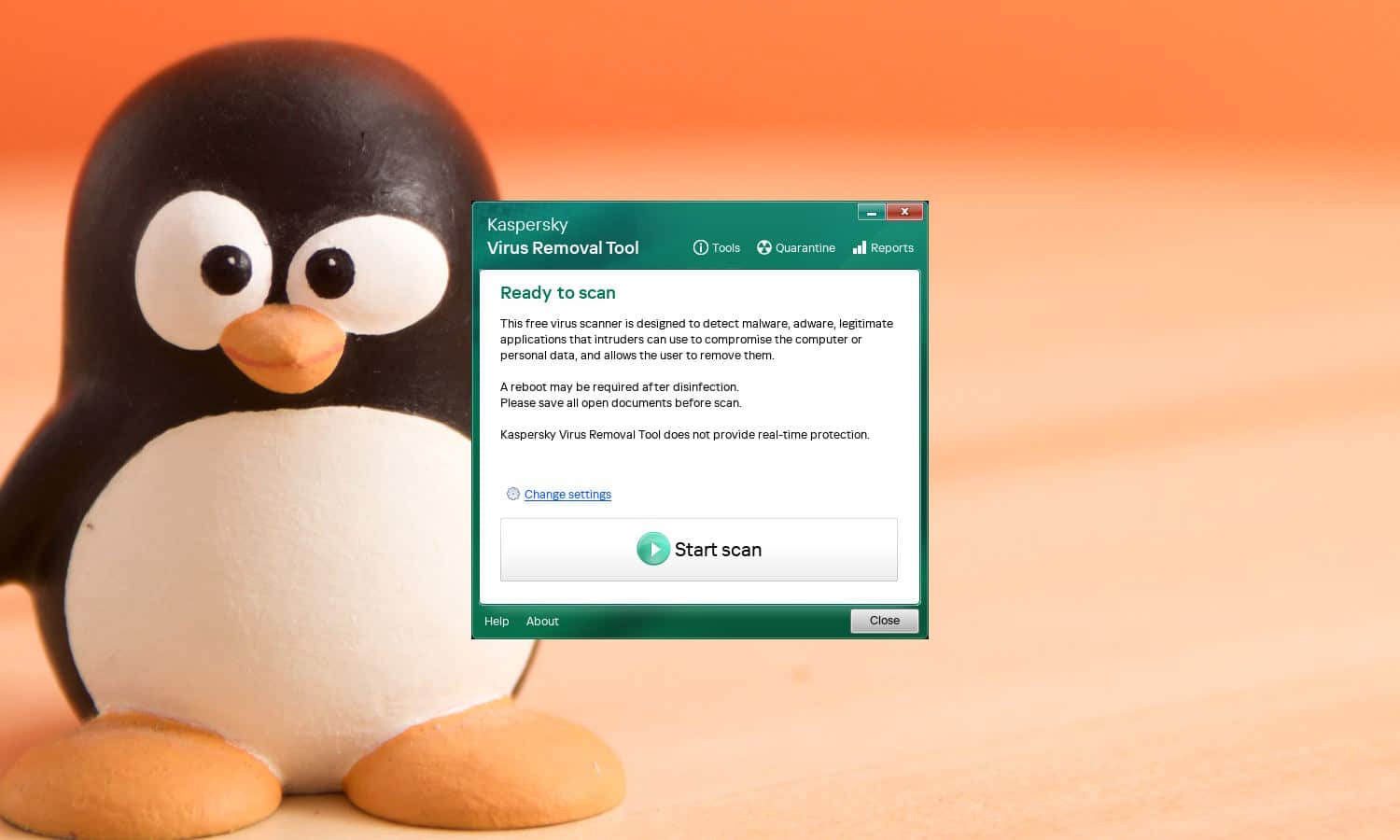
Kaspersky releases a free virus removal tool for Linux-based systems, KVRT
An urban myth used to suggest that Linux was immune to viruses and malware, and is totally secure. This is, of course, nonsense, even if the comparatively low usage makes Linux-based system less likely to be attacked than Windows or macOS.
Highlighting the fact that there is no such thing as a completely secure operating system, Kaspersky has released a new malware scanner for Linux systems. Kaspersky Virus Removal Tool (KVRT) for Linux is a free tool that, although it fails to offer real-time protection, can be used to scan for and remove various forms of malware... albeit with a slight caveat.

Ditch Microsoft Windows 11 for a fresh start: Switch to SparkyLinux 2024.05
Are you tired of the limitations and restrictions of Microsoft Windows 11? Perhaps it's time to consider an alternative that offers more control and freedom. Enter SparkyLinux 2024.05 (download here), a robust option for those looking to dive into the world of open-source operating systems.
SparkyLinux, based on the Debian testing line, is known for its stability and flexibility. The latest semi-rolling release, SparkyLinux 2024.05, brings exciting updates and features that make it an appealing choice for both new and experienced Linux users. This update includes all packages upgraded from both Debian and Sparky's testing repositories.

Native Spectre v2 exploit puts Intel systems running Linux at risk
It's been some time since we discussed the initial Spectre security flaw that impacted numerous CPUs, and which was subsequently followed by the Spectre v2 vulnerability. Now there are new concerns following the discovery of the first native Spectre v2 exploit against the Linux kernel.
Researchers from the Systems and Network Security Group at Vrije Universiteit Amsterdam (VUSec) have demonstrated that Intel CPUs running Linux are vulnerable to Native Branch History Injection (BHI). VUSec says its InSpectre Gadget tool can be used to "not only uncover new (unconventionally) exploitable gadgets in the Linux kernel, but that those gadgets are sufficient to bypass all deployed Intel mitigations".

Linux users beware: New Bifrost malware variant poses imminent threat
Security researchers at Palo Alto Networks have uncovered a new variant of the notorious Bifrost malware, now targeting Linux systems with a cunning twist. This latest iteration employs a deceptive domain, download.vmfare[.]com, to masquerade as a legitimate VMware site, thereby bypassing security measures and compromising unsuspecting users.
Bifrost, a remote access Trojan (RAT) first identified in 2004, has been a persistent threat, enabling attackers to pilfer sensitive information such as hostnames and IP addresses. The recent surge in Linux variants of Bifrost has sent ripples of concern through the cybersecurity community, signaling a potential uptick in attacks on Linux-based systems.

Escape the death grip of Windows 11 and embrace Linux: Nitrux 3.3.0 unveils a world beyond Microsoft's boundaries
Fan favorite Nitrux has reached version 3.3.0 (download ISO here), a significant jump for the Linux-based operating system. Dubbed "ab," the new distro features software updates, bug fixes, performance enhancements, and comprehensive hardware support. If you're looking for an alternative to Microsoft’s Windows 11, this is the perfect choice.
The core of Nitrux 3.3.0 runs on Linux 6.7.3-3 (Liquorix), ensuring a solid and responsive foundation. Software upgrades are abundant, with Firefox reaching version 122.0, OpenRC at 0.53, AMD Open Source Driver for Vulkan at v-2024.Q1.1, and the Nitrux Update Tool System advancing to version 2.1.2 from its previous 2.0.2 iteration.

New Linux malware up 50 percent in 2022
Although it has a reputation as a safe and secure operating system, Linux is not immune to malware. Indeed it's become an attractive target as increasing numbers of servers and other devices run Linux-based OSes.
Data analyzed by the Atlas VPN team, based on malware threat statistics from AV-ATLAS, shows new Linux malware threats hit record numbers in 2022, increasing by 50 percent to 1.9 million.

Symbiote is an extremely dangerous, 'nearly-impossible-to-detect' Linux malware
Fans of Linux-based operating systems often cite greater security as the basis for the love of their chosen distro. Whether Linux distros have better security track records than the likes of Windows 11 and macOS because they are inherently more secure or because they are simply not targeted as much as very much open to debate, but Linux remains fallible, nonetheless.
Going some way to prove this is the Symbiote malware discovered by security researchers from BlackBerry and Intezer Labs. Symbiote is worrying for a number of reasons including the fact that it is described as "nearly-impossible-to-detect". It is also extremely dangerous piece of malware that "parasitically infects" systems, infecting all running processes and giving threat actors rootkit functionality, remote access and more.

Linux and Raspberry Pi machines become top targets for credential hacking
New research shows that hackers are regularly gaining access to servers with the same commonly used -- often default -- passwords.
The data from Bulletproof also reveals that default Raspberry Pi usernames and logins feature prominently on the list of top default credentials used by hackers.

Ubuntu and other Linux distros at risk from Oh Snap! More Lemmings security exploit
Security researchers from Qualys have issued a warning about a Local Privilege Escalation Vulnerability Discovered in the snap-confine function of Canonical's Snap package manager.
Known as Oh Snap! More Lemmings and tracked as CVE-2021-44731, the collection of security flaws can be exploited to gain root privileges.

Linux-based systems targeted with ransomware and cryptojacking
Thanks to its use on many cloud servers, Linux is a core part of the digital infrastructure. It's not surprising therefore that it's increasingly being targeted by attacks.
A new report from the Threat Analysis Unit at VMware finds malware targeting Linux-based operating systems is increasing in both volume and complexity amid a rapidly changing threat landscape,

Every major Linux distro has a PwnKit flaw that is easily exploited to gain root access
Linux-based operating systems are frequently touted as being far more secure than the likes of Windows or macOS. More secure they may be, but they are not completely infallible.
A great example of this is the recently discovered PwnKit vulnerability in the pkexec component of Polkit. The flaw can be exploited to gain root access to a system and it has been a security hole in pretty much all major Linux distros for over 12 years, including Debian, Fedora and Ubuntu.

CronRAT is a new Linux malware set to strike on February 31st
Yes, you did read the headline correctly; security researchers have discovered a stealthy new remote access trojan (RAT) designed to attack Linux systems. Named CronRAT, the malware hides as a scheduled task and is configured to run on a non-existent date – February 31st.
Researchers from Sansec warn that CronRAT "enables server-side Magecart data theft which bypasses browser-based security solutions". This is something that is particularly concerning this Black Friday.

Sequoia: Linux kernel security flaw gives unprivileged users root access
A vulnerability has been discovered in the Linux kernel that makes it possible to gain root access on a number of popular distributions, including Ubuntu, Debian and Fedora. The flaw has been named Sequoia, and it exists in the filesystem layer.
The security issue is thought to affect all versions of the Linux kernel released since 2014, meaning that a large number of distros are vulnerable. Specifically, the flaw is a size_t-to-int type conversion vulnerability that can be exploited to elevate privileges.

System76 begins shipping Linux computers to Mexico, including ones made in the USA
When you live in the USA, you get used to buying things that are made in other countries. It is just very common to see things stamped with "Made in China" or "Made in Mexico." Some Americans take issue with this, actively trying to buy products made in the USA, but this can be quite hard. Even American car companies, like Ford, outsource labor to foreign counties, such as Mexico.
System76 is a company that sells computers preloaded with Linux-based operating systems, including laptops and desktops. While its laptops are not yet manufactured in the USA, its beautiful Thelio desktops are handcrafted here. And now, in an interesting twist, System76 has begun shipping its computers to customers in Mexico.
