
Malware goes global with every nation affected
Malware is a worldwide problem affecting every nation state on the planet according to the latest Comodo Threat Research Labs report.
Comodo detected almost 400 million malware incidents around the globe in the third quarter of this year, with even the tiny island nation of Kiribati in the central Pacific being affected. The top five malware hit countries are, Russia, the US, Poland, the UK and Germany.

Traditional antivirus fails to protect 40 percent of users
Conventional antivirus solutions are failing to protect users from attacks according to a Malwarebytes report.
The study is based on real-world clean up scans performed by Malwarebytes. Nearly 40 percent (39.18percent) of all malware attacks cleaned on endpoints with an AV installed occurred on endpoints that had two or more traditional AV solutions registered.

How to protect yourself against Bad Rabbit ransomware
News broke earlier about the spread of a new form of ransomware going by the name of Bad Rabbit. It name drops Game of Thrones and bears more than a passing resemblance to WannaCry and Petya.
While the main impact of Bad Rabbit has been felt in Eastern Europe, some instances of the ransomware have also been detected in the US. Thankfully, it's relatively easy -- and free -- to protect your computer. By simply tweaking a couple of files, you can stop the ransomware in its tracks.

Bad Rabbit ransomware spreads across Eastern Europe with echoes of WannaCry and Petya
A new strain of ransomware -- dubbed Bad Rabbit -- has struck in Russia, Ukraine and other parts of Eastern Europe. It is thought to be a variation on Petya due to a number of similarities, and it is wreaking havoc with media outlets and transport systems, including an airport in Ukraine, and the underground in Kiev.
Like many other forms of malware, Bad Rabbit was initially spread through a fake Flash installer, but it was then able to spread via networks to hit a larger number of machines. The spread of the ransomware is further facilitated by using the open source Mimikatz for extracting credentials, and DiskCryptor for encrypting data.

Android: DoubleLocker ransomware encrypts data and changes PINs
A new breed of Android ransomware has been discovered that hits victims with a double whammy. DoubleLocker not only encrypts data as all ransomware does, it also changes the PIN on the target device.
DoubleLocker was discovered by security researchers at ESET. They say that the ransomware abuses Android accessibility settings, and is the first to use a double-lock approach. Based on previously released banking malware, it is though that a test version of DoubleLocker could have been in the wild since as early as May.

FormBook malware attacks target US and South Korea
High-volume FormBook malware distribution campaigns have targeted businesses in the aerospace, defense contractor and manufacturing sectors according to new research from cybersecurity company FireEye.
The attackers behind these campaigns employed a variety of delivery methods to distribute this information stealing malware including PDFs with download links, DOC and XLS files which contained malicious macros and ZIP, RAR, ACE and ISO archive files containing executable payloads.
PornHub users hit by sustained, targeted malvertising campaign
Millions of PornHub users in the US, UK, Canada and Australia were targeted by a malicious advertising campaign lasting for more than a year. The malvertising attack tried to trick users of the world's most popular porn site into installing fake browser updates.
Security researchers from Proofpoint found that PornHub users had been exposed to Kovter ad fraud malware for over a year. The KovCoreG group is believed to be responsible for distributing the Kovter ad fraud malware, so if you've visited PornHub recently, it might be a good idea to check your system for signs of infection.

Cloudflare ditches sites that use Coinhive mining code after classing it as malware
Bitcoin has been in the news for some time now as its value climbs and drops, but most recently interest turned to mining code embedded in websites. The Pirate Bay was one of the first sites to be seen using Coinhive code to secretly mine using visitors' CPU time, and then we saw similar activity from the SafeBrowse extension for Chrome.
The discovery of the code was a little distressing for visitors to the affected sites, and internet security and content delivery network (CDN) firm Cloudflare is taking action to clamp down on what it is describing as malware.

Dirty COW Linux vulnerability reappears as ZNIU malware threat to Android users
It has been quite some time -- nearly a year in fact -- since we were talking about the Dirty COW vulnerability affecting the Linux kernel. Now the vulnerability is back, but this time it is Android users who need to be concerned.
The privilege escalation vulnerability has been exploited by a piece of malware by the name of ZNIU, or AndroidOS_ZNIU. The malware uses the Dirty COW exploit to root devices and install a backdoor which can then be used to collect data and also generate profit for the attackers through a premium rate phone number.

Ransomware attacks affect five percent of SMBs
Five percent of all small and medium-sized companies in the entire world were victims of a ransomware attack in 2016 alone, with the money paid out to reclaim data reaching new highs, new research has revealed.
Datto's new State of the Channel Ransomware Report found that an estimated $301 million (£222 million) was paid to ransomware hackers from 2016-2017.

Security warning: Hackers compromised CCleaner and installed a backdoor
Users of cleanup, privacy and optimization tool CCleaner are being warned to update their software after it emerged the tool was compromised by hackers. Security researchers at Cisco Talos say that there are a "vast number of machines at risk."
CCleaner is produced by Piriform, now a subsidiary of security firm Avast, making the compromise not only serious, but also embarrassing. With 2 billion downloads -- a number that's rising at a rate of 5 million per week -- the software was targeted by hackers who added a backdoor that could be used to download malware, ransomware and keyloggers. The problem is being compared to the NotPetya ransomware threat.

Hurricanes lead to drop in malware infections
An interesting side effect of the recent hurricanes Harvey and Irma is that malware infections in the Florida and Texas areas have seen a dramatic fall.
Data released by Enigma Software Group, makers of the SpyHunter anti-malware software, shows that infections in the Houston area showed a 52.5 percent drop from the average on August 29th.
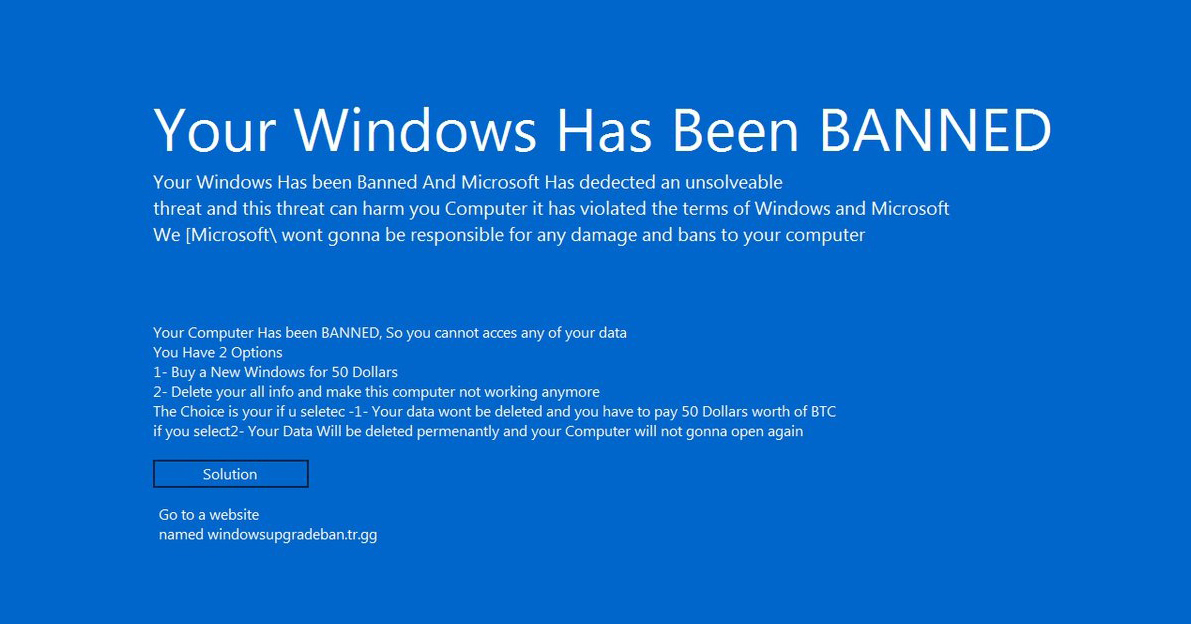
'Your Windows Has Been Banned' malware makes an unwelcome return
"Your Windows Has Been Banned" is a nasty piece of malware that first surfaced in 2016. It locks your computer screen and displays a message stating "This PC has been banned for terms of use violations."
It doesn’t go into specifics for the ban -- because, obviously, it’s not a real ban -- but simply says that your PC has been locked in order to "protect the Windows service and its members," adding "Microsoft does not provide details about specific PC bans."

Bashware attack makes Linux a security threat to Windows 10
While many people welcomed the arrival of Windows Subsystem for Linux (WSL) in Windows 10, it has been found to be a potential security issue. A new technique known as a Bashware has been discovered by security researchers that makes it possible for malware to use the Linux shell to bypass security software.
While administrator access is needed to execute a Bashware attack, this is fairly easily obtained, and the technique can be used to disguise malicious operations from antivirus software and other security tools. Researchers from Check Point Research point out that the danger stems from the fact that "existing security solutions are still not adapted to monitor processes of Linux executables running on Windows."

TheShadowBrokers group returns with NSA UNITEDRAKE hacking malware and promises more leaks
It feels as though it has been a while since we heard anything from the hacking group TheShadowBrokers. The group's latest data dump sees the release of the NSA's UNITEDRAKE exploit tool, and there's also a promise of two data dumps a month moving forward.
UNITEDRAKE is a remote access hacking tool that can be used to target Windows machines. Modular in nature, the malware can be expanded through the use of plugins to increase its capabilities so it can capture footage from webcams, tap into microphones, capture keystrokes, and more.
