
Enterprises suffer surge in mobile phishing attacks
Cybercriminals are increasingly adopting a 'mobile-first' attack strategy to infiltrate enterprise systems by targeting weak, unsecured, and unmanaged mobile endpoints, recognizing mobile as a major entry point to corporate networks and sensitive data.
A new report from Zimperium zLabs shows a significant rise in mobile phishing -- or 'mishing' -- a technique that employs various tactics specifically designed to exploit vulnerabilities in mobile devices.

Nord Security launches eSIM for businesses
You probably already know about how eSIMs work and their advantages when travelling to different countries.
Of course this functionality is useful for businesses as well as individuals and Nord Security -- the company behind NordVPN -- is launching a new version of its Saily eSIM service aimed specifically at business users.

Enterprise mobile devices see increased attacks
A new report on the mobile threat landscape from Lookout reveals a 40.4 percent jump in mobile phishing attempts and malicious web attacks targeting enterprise organizations.
More than 80,000 malicious apps were detected on enterprise mobile devices. These threats can vary widely, from invasive permissions and riskware that pose significant compliance risks to sophisticated spyware capable of tracking devices, stealing data, eavesdropping on conversations and accessing the user' camera and microphone.

2024 Paris Olympics -- cybersecurity risks and top tips to keep data safe [Q&A]
In recent years, mobile devices have taken center stage and we've become mobile-first users, where mobile devices are our first choice for how we communicate, navigate, work, bank, take photos, shop and stay informed about the world around us. Our increased reliance on mobile phones is not without its risks.
According to Zimperium's Global Mobile Threat Report 2023, 43 percent of all compromised devices were fully exploited (not jailbroken or rooted), an increase of 187 percent year-over-year, a shocking number.

Why mobile connectivity is essential for the enterprise [Q&A]
While enterprise computing was once tied to the desktop, theses days mobile connectivity is essential to the smooth running of any business.
This is partly as a result of changed working patterns -- accelerated by the COVID pandemic -- and partly down to rapidly evolving technology. We spoke to Allwyn Sequeira, CEO of mobile cloud service Highway 9 Networks, to learn more about the enterprise mobile space.

Microsoft is making it possible to access your smartphone from File Explorer in Windows 11
The way Windows 11 interacts with mobile devices -- and, in turn, the way it lets users interact with them -- has been a little odd for some time. The Your Phone / Phone Link app showed that using Windows to use or browse your smartphone was really something of an afterthought for Microsoft.
Continuing the piecemeal approach to mobiles, it looks as though the company is finally about to give File Explorer the ability to browse smartphone contents. The option has been unearthed in Windows 11, although we don't yet know when it will be released properly.

Threats to mobile devices triple over the last year
Almost three times as many phishing, malicious, deny-listed, and offensive links have been delivered to mobile devices than a year ago, according to a new report from Lookout.
The Lookout Mobile Threat Landscape Report is based on data derived from the Lookout Security Cloud that analyzes data from more than 220 million devices, 325 million apps and billions of web items.
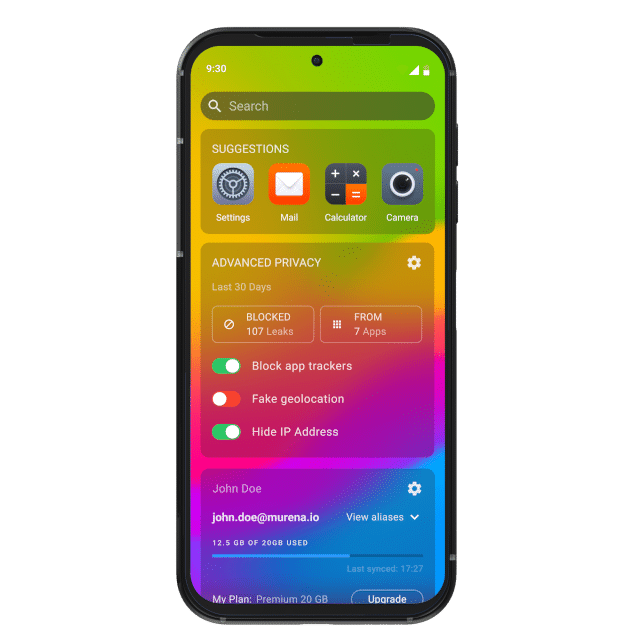
Privacy-focused mobile operating system /e/OS rolls out new version
If you have an Android phone you'll no doubt be aware of the risk that unwanted trackers can access your data while you're using third-party apps or browsing the web.
If you're worried about being tracked though there is an alternative in the form of /e/OS which has a focus on privacy and can be can be flashed on numerous Android devices to replace Google's ubiquitous OS. Today sees the release of V2 of /e/OS which offers further privacy controls, tools and improved user interface.

DDoS attacks shift from mobile to computers
Computers and servers made up 92 percent of DDoS targets in 2013, compared to just eight percent for mobile devices. The split the previous year was 32 percent computers and 68 percent mobile. At the same time the DDoS attack count decreased 55 percent in 2023, but the average attack size grew 233 percent.
The latest DDoS trends report from Nexusguard also finds that shorter attacks lasting 90 minutes increased by 22 percent and made up 81 percent of all DDoS attacks.

Email still the most popular phishing technique even on mobile
Most incidents of phishing or spoofing on smartphones still happen via email, according to MEF's (Mobile Ecosystem Forum) 9th Annual Trust Study.
The report shows 52 percent of users reporting personal experience of data harm via this channel. Surprisingly, 39 percent of those users still took no preventative measures to protect their online data.

Nearly half don't use mobile security solutions
A new report from Bitdefender shows that 45 percent of consumers don't use mobile security solutions, despite the fact that 78 percent conduct sensitive transactions on their devices.
Based on an independent global survey of over 7,000 consumers, the report looks at top security behaviors, practices and concerns across their digital footprint and lifestyle.

Keeper Security introduces passkey support for mobiles
Passkeys, cryptographic keys that lets users log in to accounts and apps without entering a password, have been around for a while but mostly on computers.
Now though Keeper Security has introduced passkey management support for both both Android and iOS mobile devices.

How the use of mobile devices is changing the cybersecurity landscape [Q&A]
As consumers and businesses undergo a sea change shift towards mobile interfaces, embracing everything from retail to human resources management, the landscape of mobile security is experiencing a parallel transformation.
With this surge in reliance on mobile devices, threats have become more sophisticated, spanning network vulnerabilities, the proliferation of malware, and the craftiness of phishing schemes.

21 new malware families for Mac systems discovered in 2023
Apple devices have historically had a reputation for being immune to malware, but a new report from Jamf reveals that it's tracked 300 malware families on macOS and found 21 new ones in 2023.
Jamf's latest Security 360 report examined a sample of 15 million desktop computers, tablets and smartphone devices they protect, across 90 countries and multiple platforms (macOS, iOS/iPad, Android and Windows).

How 5G is set to transform the way businesses connect [Q&A]
The rollout of 5G will speed up mobile communications and also enable more computing tasks to be carried out at the edge.
For businesses it presents the opportunity for a greater understanding of customer patterns and infrastructure needs. We spoke to Chris Gehlen, CEO and co-founder of SaaS/NaaS cloud platform Neutroon, to learn more.
