
Majority of leaked records in 2019 came from financial services firms
According to a new report, more than 60 percent of all leaked records in 2019 were exposed by financial services organizations, despite only six percent of breaches affecting these organizations.
The 2019 Financial Breach Report from Bitglass says these figures are at least partially due to the Capital One breach, which compromised more than 100 million records.

New account fraud up 28 percent in 2019
New account fraud -- attempts by an individual to create a new online account by manipulating a government-issued ID -- is up 28 percent this year according to a new report.
Data from trusted identity provider Jumio shows this type of fraud has increased over 100 percent on 2014 levels.

Privacy legislation and the impact of GDPR and CCPA [Q&A]
With the California Consumer Privacy Act (CCPA) coming into force in January and GDPR in Europe having been active for nearly two years, data privacy is something that's being taken more seriously than ever.
But what impact does legislation have on businesses and consumers? And how has GDPR influenced the drafting of CCPA? To find out we spoke to Sophie Stalla-Bourdillon, senior privacy counsel and legal engineer and Dan Wu, privacy counsel and legal engineer, from data governance specialist Immuta.

Amazon is getting free access to NHS medical data
As fear mounts in the UK at the prospect of the NHS being sold in part or in whole to the US, the government has decided to give Amazon access to National Health Service data for free.
The arrangement means that Amazon will be able to access "healthcare information, including ... symptoms, causes, and definitions". The tech giant will be able to use the data in conjunction with Alexa to enable users to get medical help and advice via the digital assistant.

Apple: iPhone 11 Pro handsets check location to comply with regulations
It recently came to light that even with Location Services disabled, iPhone 11 Pro handsets appeared to be checking for location data, sparking concerns about privacy.
Having initially dismissed this as "expected behavior", Apple has now gone into more detail about what's actually happening. Rather than being a sinister case of tracking iPhone users, the company says that location checks are actually required because of the ultra wideband chips found in newer iPhones.

Your iPhone 11 Pro tries to collect location data even when all location services are disabled
Security researcher Brian Krebs has discovered a peculiarity with the iPhone 11 Pro and its collection of location data.
In what is described as a "possible privacy bug", Krebs found that the iPhone 11 Pro seeks location data even when system services and apps are configured to never request this information -- the location arrow icon can be seen popping into view at unexpected times. Curiously, despite seemingly contradicting its privacy policies, Apple says that it is by design.

The US shows a 'concerning lack of regard for the privacy of people's biometric data'
When it comes to the extensive and invasive use of biometric data, the USA is one of the worst offenders in the world, faring only slightly better than China.
According to research conducted by Comparitech, which rated 50 countries according to how, where and why biometrics were taken and how they are stored, the US ranked as the fourth worst country. Topping the list is China, followed by Malaysia and Pakistan.

Facebook faces European probe over data collection
It is not just Google which is coming under the scrutiny of the European Commission – the European antitrust regulator have announced that they are also looking into the data collection practices of Facebook.
Just as with Google, the Commission has sent out preliminary questionnaires as part of an investigation into how Facebook collects and monetizes its data.

Twitter introduces new Privacy Center to give users greater transparency
Conceding that as a company it "is not perfect at privacy and data protection", Twitter has revealed details of a new Privacy Center. This central repository will serve as the portal through which Twitter will keep users informed about how it handles user data.
Twitter is also introducing updates to its privacy policy on January 1, 2020. These will be compliant with the California Consumer Privacy Act (CCPA) which places numerous obligations on large companies, including giving customer greater control and transparency, and the right to have their data deleted on request.
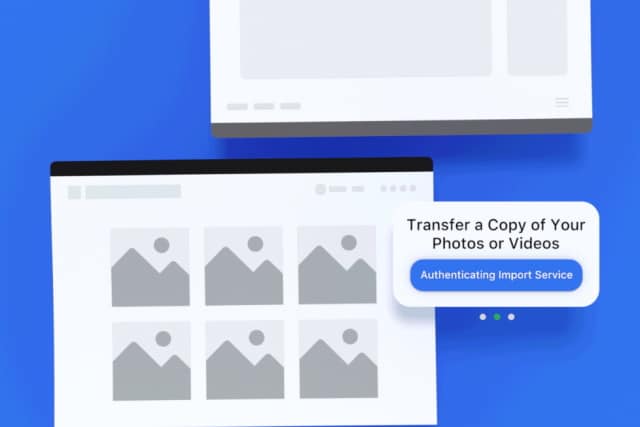
Facebook launches data portability tool to allow users to transfer photos and videos to Google Photos
Embracing the notion of data portability, Facebook has launched a new tool that lets users transfer their photos and videos from Facebook to other online services.
The social network is kicking things off by making it possible to transfer data from Facebook to Google Photos. It comes as part of Facebook's participation in the open-source Data Transfer Project and the ability to transfer to other services will be added soon.

Unencrypted SMS database found online, exposing millions of US text messages
A huge database of text messages and user data has been discovered online, completely unprotected and free for anyone to browse.
Found by researchers from vpnMentor, the database belongs to US communications company, TrueDialog. Among the exposed data are not only tens of millions of SMS messages, but also private information including usernames and passwords.

Google is under investigation over its data collection practices
The European Commission has started an investigation into "practices relating to Google's collection and use of data".
EU antirust regulators have already hit Google with record-breaking fines, but concern remains about how the company collects data about its users as well as how this data is then used. The regulator has contacted several companies to ask about agreements they have with Google to hand over user data and what -- if any -- money was involved.
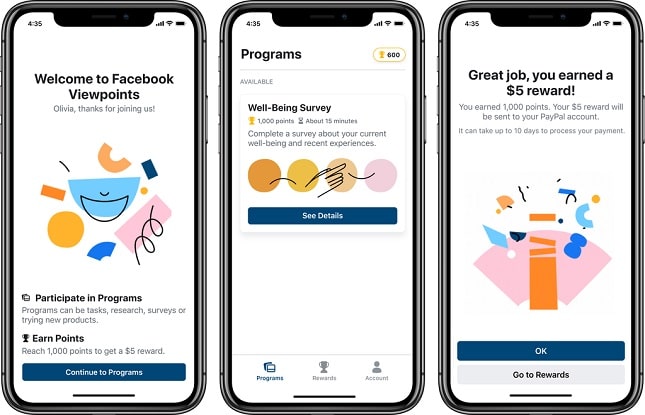
Facebook Viewpoints will pay you money to complete surveys, but you shouldn't do it
I suppose there is nothing inherently wrong with handing over your data to big corporations -- as long as you do so willingly. Look, there are several "free" services online these days, such as Facebook, Gmail, and YouTube that many people use daily. These services aren't really free, however, as your data is largely the price of admission.
For those without actual disposable income, this data is a valuable commodity that they can use to trade for services -- it opens doors to some. With that said, it can be argued that this is essentially taking advantage of low income people. Similarly, this is one of the reasons it is illegal to sell your organs in the USA -- you'd have poor people transferring kidneys to the wealthy just to pay the rent.

OnePlus suffers data breach, exposing personal details of online store customers
OnePlus has issued a security notice to customers that have used its online store, informing them that their order information has been accessed by an unnamed third party in a security breach.
The company is giving away very little in the way of details about the incident. It is not clear when the data breach happened, who may be responsible, or how many customers are affected. OnePlus says that information such as names, phone numbers, email addresses and shipping addresses have been exposed.

Businesses need to get the data privacy balance right
With multiple privacy regulations and laws having gone into effect over the past year or so and more on the way affecting both consumers and business alike, it’s no wonder people are sometimes confused about how their personal data can be used.
Cisco is releasing the findings of its 2019 Consumer Privacy Survey, highlighting the top areas where consumers continue to struggle to understand how companies are handling their personal data, and how far data privacy trust has progressed.
