
Why third-party email filters may be ineffective in Microsoft 365 environments
Because email is the primary source of initial entry in many breaches, many organizations pay for sophisticated, third-party email filtering solutions on top of the protections afforded by Microsoft 365. This is a wise investment; having layers of protection by different vendors helps eliminate blind spots found in any one vendor solution and provides complexity that can foil attack attempts.
Yet, few know that threat actors can easily bypass these third-party filtering products by directing emails to onmicrosoft.com domains that are an inherent part of the Microsoft 365 configuration.
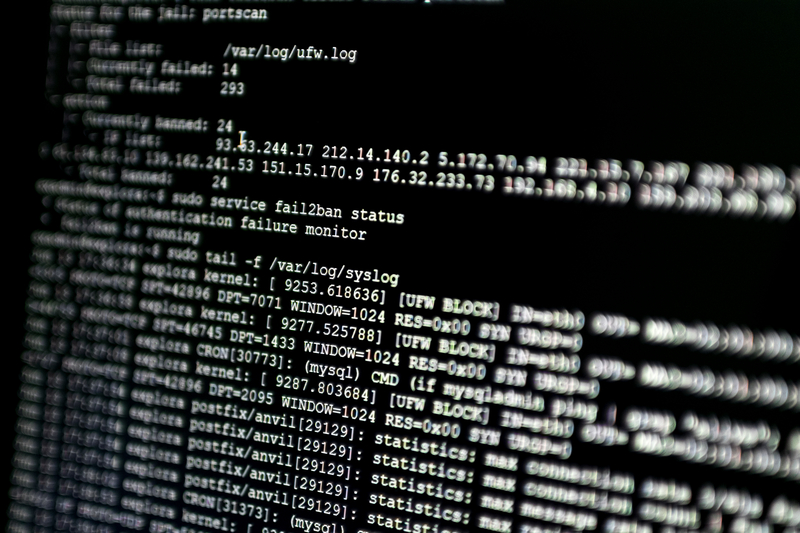
Log files: What are they, why do they matter and how to protect them?
Log files come with many challenges. Firstly, they exist as enormous volumes of data. Almost everything that a user does is recorded, meaning that they quickly pile up, and not all of them are useful.
Secondly, they aren’t all uniform as they come in various shapes and sizes, serving various purposes. Event logs, system logs, access logs and server logs are just some of the various types that are collected and stored. This large volume of data means that processing and analyzing logs for use can be time-consuming and complex.

Old habits, new threats -- Why more phishing attacks are bypassing outdated perimeter detection
Perimeter solutions such as Secure Email Gateways (SEGs) have long been a cornerstone of email security, historically serving as the primary line of defence against malicious emails entering an organization. Utilizing legacy technology such as signature and reputation-based detection, SEGs have provided pre-delivery intervention by quarantining malicious attacks before they reach the end recipient.
Why, then, are 91 percent of cybersecurity leaders frustrated with their SEGs, and 87 percent considering a replacement?
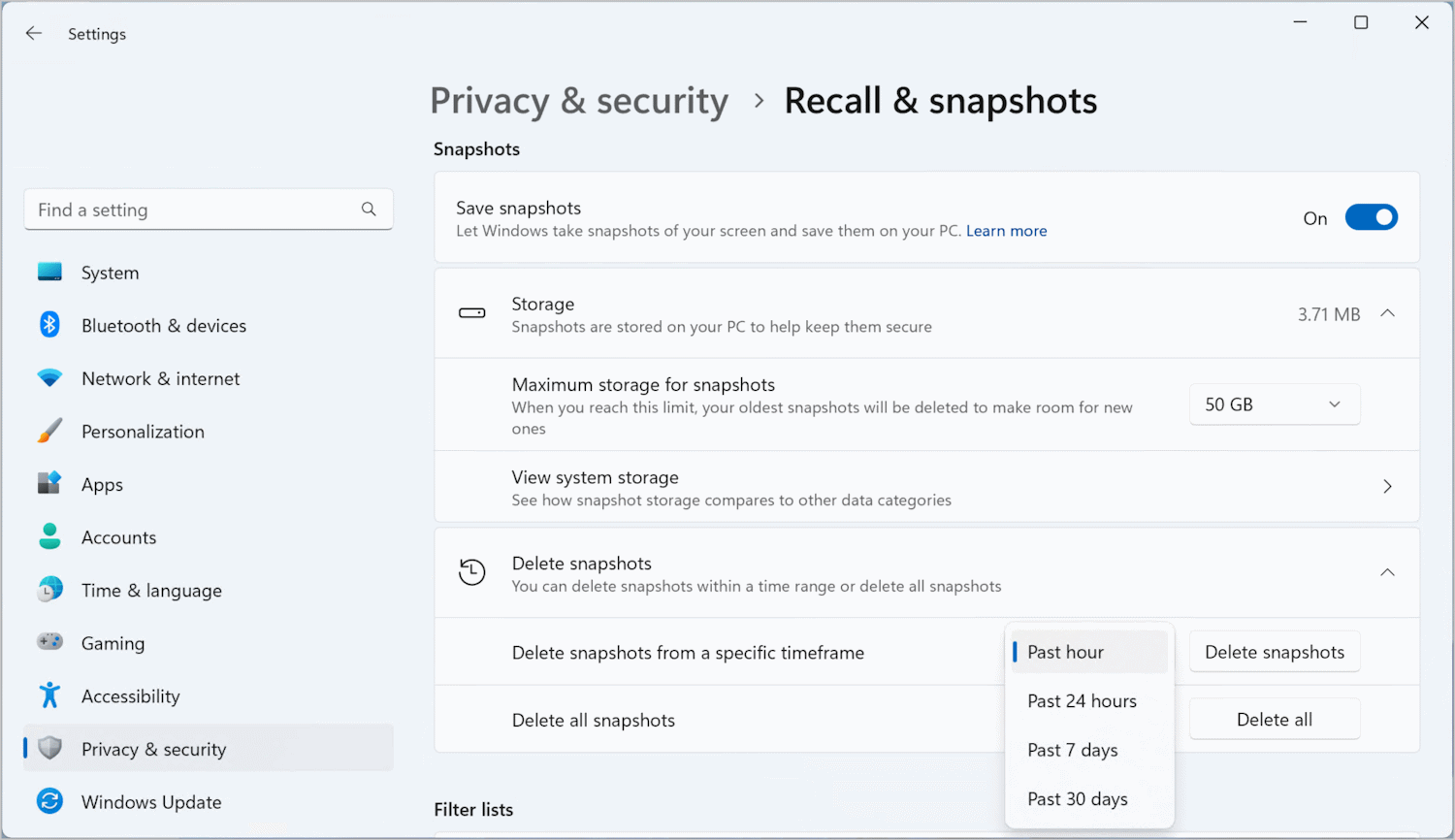
If you're worried about privacy and security, you'll be able to uninstall Recall from Windows 11
The Recall feature of Windows 11 has not even launched yet, but it has proved endlessly controversial since it was first announced a few months back. Microsoft says that Recall will help users retrace their steps by taking snapshots of activity every few seconds, providing a way to step back in time and jump to an earlier activity.
Such was the uproar about the security and privacy implications of the feature, Microsoft has already made concessions. The company first pulled the feature from preview builds of Windows 11 to do further work on it, and then announced that it would be opt-in rather than enabled by default. Now it turns out that it will be possible to uninstall it completely.

What does cybersecurity tool sprawl look like today?
Cybersecurity has become an increasingly important concern in the business world. After all, reports have found that 41 percent of businesses fell victim to a cyberattack in 2023. As the technology cyber attackers use to conduct their nefarious activities becomes more complex, so is the technology that IT professionals use to protect organizations and their data. However, with this also comes a unique new challenge: tool sprawl.
Tool sprawl occurs when a company utilizes an unnecessary number of IT tools, usually because it implements separate solutions for each use case. Although it may seem most efficient to address needs as they arise or present themselves, adopting a comprehensive approach is often more efficient -- particularly in a case where proactivity is vital, such as cybersecurity.

Save $39.99! Get 'Cybersecurity Strategies and Best Practices' for FREE
If you are a cybersecurity professional looking for practical and actionable guidance to strengthen your organization’s security, then this is the book for you. Cybersecurity Strategies and Best Practices is a comprehensive guide that offers pragmatic insights through real-world case studies.
Written by a cybersecurity expert with extensive experience in advising global organizations, this guide will help you align security measures with business objectives while tackling the ever-changing threat landscape.

Business security: Advancements in on-premise and online tech solutions
Biometric access control, video surveillance, and intrusion alarms enhance on-site protection by promptly addressing unauthorized access -- these advanced systems monitor who enters your facilities and allow for real-time responses to incidents.
Meanwhile, cybersecurity remains a key aspect of business demanding great attention. The emergence of generative AI and automation technologies can evaluate threats and make decisions significantly faster, heightening the effect of your defense mechanisms.

Enhancing availability, even when high availability is not required
Providing high availability (HA) protection for critical applications is a standard IT best practice. However, broader downtime protection best practices -- and options for delivering this protection -- are not as clearly defined. As a result, applications that are not considered mission critical are often left with minimal protection. Yet downtime for these non-mission critical applications can be more than a nuisance. It can impose a costly and disruptive burden on IT teams that must devote time and resources to bringing those applications back online.
Downtime can also be frustrating to end users whose work may be interrupted and put on hold. It may have downstream consequences for customer satisfaction as well.

How radical transparency paves the way to more effective vulnerability management
Vulnerability management is one of the most painful challenges of cybersecurity. The lack of transparency in our industry isn’t helping matters. Vendors often work behind the curtain to fix the identified security flaws without effective communication or -- if they do communicate -- with significant delays in reporting.
However, there are signs of positive steps toward this much-needed transparency. In July, for example, the Microsoft Security Response Center announced that it will start issuing Common Vulnerabilities and Exposures (CVEs) for critical cloud service vulnerabilities. There have also been moves from legislators to ensure greater rigor in reporting, such as the EU's Cyber Resilience Act, which mandates that manufacturers of all connected and IoT devices report serious cyber incidents and unpatched vulnerabilities. This is essential for building trust among vendors, businesses, and stakeholders alike. Greater resilience starts with a common understanding.
AI's rapid development is a security disaster waiting to happen
No matter how you look at it, AI is currently booming. The AI market is on track to reach $407 billion by 2027 (compared to $86.9 billion in 2024). Last year, ChatGPT became the fastest-growing consumer application in history when it reached 100 million monthly active users just two months post launch. McKinsey declared 2023 as Generative AI’s breakout year, and a follow-up 2024 survey found that the percentage of organizations using Generative AI jumped from approximately 50 percent to 72 percent from 2023 and 2024. Meanwhile, a culture shift within tech and business has accelerated AI adoption seemingly overnight.
Long before Generative AI entered the scene, tech C-suites were concerned about being left behind. AI’s disruptive potential has only exacerbated this. Companies with the bandwidth to do so are developing their own AI systems or converting existing ones over to AI. Such behavior is motivated primarily by reputation management. No major player wants to look like they were left behind as their competitors innovated to newer heights.

Pool your cybersecurity resources to build the perfect security ecosystem
Cybersecurity has never been something to set once and leave running in the background -- it is a constantly evolving landscape. While the migration of data and applications to the cloud provides numerous business benefits, many organisations struggle to secure their networks against rapidly changing cyber threats. Ransomware attackers have understood the value of targeting smaller organisations and tailoring attacks to take advantage of businesses they believe will pay up immediately (and often with the backing of cyber insurance) rather than invest in defences.
Tight security for data and resources is now the difference between operations running smoothly or being disrupted to the point that businesses are forced to close entirely. But how can SMBs achieve comprehensive security management and threat intelligence on a budget? Partnerships and alliances provide the solution.

Get 'Cybersecurity For Dummies, 2nd Edition' FREE for a limited time
Every day it seems we read another story about one company or another being targeted by cybercriminals. It makes some of us wonder: am I safe online? The good news is that we can all be cybersecure -- and it doesn’t take a degree in computer science to make it happen!
Cybersecurity For Dummies is the down-to-earth guide you need to secure your own data (and your company’s, too).

Microsoft reveals Office security flaw that has not yet been patched
Various versions of Microsoft Office have a serious security vulnerability which could expose sensitive data to an attacker. Worryingly, while disclosing the flaw, Microsoft has also conceded that there is no patch available.
The issue is being tracked as CVE-2024-38200 and it affects a variety of edition of the office suite -- namely the 32- and 64-bit versions of Microsoft Office 2016, Microsoft Office 2019, Microsoft Office LTSC 2021, and Microsoft 365 Apps for Enterprise. While there is no fix available right now, one is expected in the coming days.

Devs beware: Apple announces Gatekeeper security enhancements in macOS Sequoia
Working much like Microsoft's Smart App Control tool that is part of Windows, Apple has Gatekeeper for macOS. It is a security feature which is designed to ensure that only trusted software runs on a user's Mac.
In the upcoming macOS Sequoia, Gatekeeper is being updated to help boost security. While this runtime protection change may be welcomed by many, the approach Apple has taken is also likely to irritate some users as it makes it more awkward to run unsigned software.

Security firm warns that 'design weaknesses' in Windows Smart App Control mean it can be easily bypassed
Smart App Control is just one of various security features Microsoft has built into Windows 11. But while many users place faith in the tool to block malicious apps, Elastic Security Labs warns that it is fundamentally flawed.
The company says that Windows Smart App Control and its predecessor SmartScreen "have several design weaknesses that allow attackers to gain initial access with no security warnings or popups". In an investigatory report, Elastic Security Labs details numerous types of attack that can be used to bypass Windows Smart Control as well as revealing a bug in the handling of .lnk files which can be used to get around security.
