Virtual reality could attract new talent to security careers

The cyber security industry continues to face a skills crisis, but a new study from security vendor ProtectWise and analyst ESG suggests that the adoption of new technologies could be instrumental in attracting new talent.
The survey of over 500 16 to 24 year-olds finds that 74 percent say that the use of gaming and VR technology in the fight against cyber crime would increase the likelihood of them pursuing a cyber security career.
Cyber criminals turn to messaging apps following dark web crackdown

The recent crackdown on popular dark web markets AlphaBay and Hansa is driving cyber criminals to migrate to messaging apps like Discord, ICQ, Skype, Telegram and Whatsapp, according to a new report.
The study from threat management company IntSights analyzed thousands of black markets, text storage/paste sites, hacking forums, IRC channels, apps and social media pages, and uncovers a steady increase in threat actors inviting cyber crime forum users to join their chat groups.
Bad Rabbit ransomware spreads across Eastern Europe with echoes of WannaCry and Petya

A new strain of ransomware -- dubbed Bad Rabbit -- has struck in Russia, Ukraine and other parts of Eastern Europe. It is thought to be a variation on Petya due to a number of similarities, and it is wreaking havoc with media outlets and transport systems, including an airport in Ukraine, and the underground in Kiev.
Like many other forms of malware, Bad Rabbit was initially spread through a fake Flash installer, but it was then able to spread via networks to hit a larger number of machines. The spread of the ransomware is further facilitated by using the open source Mimikatz for extracting credentials, and DiskCryptor for encrypting data.
CyberScout launches one-stop marketplace for identity management

Recent breaches like that at Equifax have highlighted the importance of supporting victims with identity management services in the aftermath of an attack.
Identity and data defense firm CyberScout is launching a comprehensive marketplace for identity management, privacy, and cyber security education products and services, aimed at providing individuals with a one-stop-shop solution for all services relating to cyber protection.
Industrial and infrastructure networks are prime targets for attackers

Operational technology networks are used with specialized Industrial Control Systems (ICS) to monitor and control physical processes such as assembly lines, mixing tanks, and blast furnaces. These networks are ripe targets for adversaries according to a new study from industrial cyber security company CyberX.
Many of these networks are exposed to the public internet and easy to crack using simple vulnerabilities like plain-text passwords. Lack of even basic protections like antivirus can enable attackers to quietly perform reconnaissance before sabotaging physical processes.
One in three businesses can't keep up with cloud security

Maintaining security in the cloud and container environments is an increasing problem according to a new survey.
The study by intrusion detection platform Threat Stack finds that 31 percent of those interviewed say they are unable to maintain security as their cloud and container environments grow. As a result, 62 percent say that they’re seeking greater visibility into their public cloud workloads.
Consumer group Which? calls for amendments to Data Protection Bill to allow for 'collective redress' after breaches

UK consumer group Which? is calling on the government to make an amendment to the Data Protection Bill that's currently being debated in Parliament. The group is looking for a change in the law that would make it easier for organizations to seek redress for groups of people in the event of a data breach.
Research by Which? suggests that there is confusion surrounding who is responsible for safeguarding data, and little knowledge among consumers about how to go about obtaining compensation.
Google defaults to prompts for two-step authentication
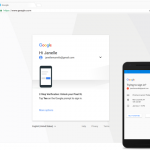
Text messages are often used as a means of implementing two-factor authentication on websites and in apps, but now Google is actively pitching its own alternative, known as Google prompt, to customers.
Traditionally users would receive a one-time code on their mobile device contained within a text message which they would have to enter to gain access. With Google's solution though, they will receive a prompt asking if they are trying to sign in. Users trying to sign in will gain access while those not expecting the login prompt will be denied.
Windows 10 Fall Creators Update offers ransomware protection with Controlled Folder Access

Ransomware is one of the most concerning, and the most prevalent, forms of malware around at the moment. While there are numerous security tools out there that you can install to keep yourself protected, if you have upgraded to Windows 10 Fall Creators Update you have a built-in tool at your disposal.
Called Controlled Folder Access, the feature locks down files and folders to protect them against unwanted changes -- including encryption by ransomware. It's not enabled by default, so here's what you need to do.
Kaspersky: Increased reliance on mobile devices puts consumers at risk

Smartphone users have been urged to ensure their devices are properly protected against cyber threats, in a new report from one of the world's top security firms.
The latest Kaspersky Cybersecurity Index has warned that over-reliance on mobile devices could be putting consumers around the world at risk as they stop using PCs for many everyday tasks.
New endpoint protection platform guards against nation state attacks

Endpoint security company Endgame has become the first protection platform that measures its effectiveness not just against malware but against nation-state level attacks.
It has worked with MITRE Corporation to validate protections against MITRE's ATT&CK Matrix, a framework for adversarial tactics and techniques that enterprises encounter daily.
Kaspersky's new 'global transparency initiative' aims to rebuild trust by submitting source code for review

Kaspersky software was recently banned from US government computers over fears that the security company has links to the Russian government. This is something Kaspersky vehemently denies, and now it has announced a new "global transparency initiative" to try to win back trust.
Part of the newly transparent Kaspersky will see the company submitting source code for current and future software to "the broader information-security community and other stakeholders." It is hoping that the scrutiny will put to bed ideas that it has been engaged in espionage with the Russian authorities.
Google says the majority of Chrome traffic is protected with HTTPS

Google has already used Cybersecurity Awareness Month to announced details of a new bug bounty program for Android apps, as well as a new Advanced Protection Program for G Suite users. Now the company has revealed that most web traffic in its Chrome web browser is protected by HTTPS.
The precise figures vary from platform to platform -- with ChromeOS and macOS faring the best -- but between 64 and 75 percent is now secured. Google humblebrags about the results of its mission to "secure the web, one site at a time," after opting to mark non-encrypted pages as being insecure.
One in five UK businesses don't prepare for cyber attacks

UK companies are unprepared for potential cyber-attacks against their business, with major shortcomings in many areas of security, new research has said.
A report released today by PwC found that a worrying amount of British firms only have adequate security protection in place, or are unaware of how best to prepare against attacks.
Financial services to boost security investment on account of breach risks

Virtually every second global financial services organization was a victim of a data breach sometime in the past, according to a newly released Thales report.
The 2017 Thales Data Threat Report, Financial Edition, says 49 percent of financial services organizations suffered a breach, with a fifth (21 percent) being breached more than once. Nine in ten (90 percent) feel more vulnerable to such incidents.
Recent Headlines
Most Commented Stories
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.