Email is scammers' favorite platform

Email is still the number one cybercrime infection vector, but it's far from being the only one you should be paying attention to. A new whitepaper from Symantec, entitled ISTR, says business email compromise as well as spam are also dangerous players in the game.
Here are the numbers: email is the most popular platform among scammers. One in nine email users have had a malicious email sent to them in the first six months of this year. And that's just the global average. In the Wholesale Trade industry, that figure jumps to one in every four users.
PornHub users hit by sustained, targeted malvertising campaign

Millions of PornHub users in the US, UK, Canada and Australia were targeted by a malicious advertising campaign lasting for more than a year. The malvertising attack tried to trick users of the world's most popular porn site into installing fake browser updates.
Security researchers from Proofpoint found that PornHub users had been exposed to Kovter ad fraud malware for over a year. The KovCoreG group is believed to be responsible for distributing the Kovter ad fraud malware, so if you've visited PornHub recently, it might be a good idea to check your system for signs of infection.
How to check that you're using the real Adblock Plus Chrome extension

News broke recently that a fake version of the Adblock Plus browser extension had made its way into the Chrome Web store. It is thought that 37,000 people installed the phony version, and now Adblock Plus -- the real one -- has responded to the news.
While acknowledging that the fake extension was removed from the store fairly quickly, Adblock Plus questions how it got there in the first place. It also provides instructions for anyone who is concerned that they may have a malicious version of the extension installed.
Microsoft invites you to report malicious and phishing websites as it crowdsources security

Microsoft is opening itself up to submissions from the public, making it possible for people to provide information about malicious websites. A new page on the Windows Defender Security Intelligence (WDSI) website gives anyone the opportunity to pass on details of phishing sites and other malicious pages directly to Microsoft.
The WDSI portal is described by Microsoft as being in preview, so it's possible that what you see now may change over time.
Banks targeted in hybrid debit card scam

Researchers at SpiderLabs, the research arm of Trustwave have released results of their investigations into a major attack targeting Eastern European banks.
The attack uses mules to open new accounts with minimal deposits and, crucially, request a debit card. When the new card is delivered it's shipped elsewhere and hackers then use stolen credentials to manipulate the bank's systems and raise the overdraft limit, allowing cash to be drawn from ATMs.
Enterprises expect AI investment to pay off in two years

Businesses are putting increasing amounts of investment into artificial intelligence, and 64 percent of decision makers expect to see a return on investment from their AI in under two years.
This is one of the findings of a new report by cyber security company Cylance which surveyed 652 IT decision makers in the US, UK, Germany and France, and finds optimism about the value of AI-powered solutions in the enterprise is high with widespread plans to continue investment in the technology.
Cyber attacks are as serious as terrorism, says UK's GCHQ

Cyber-attacks are as serious of a threat as terrorism, the head of UK security body GCHQ has said.
Writing in the Daily Telegraph, Jeremy Fleming said extra funds the institution is getting are being spent on making GCHQ a "cyber-organization" as much as a counter-terrorism, or intelligence one.
Fake Adblock Plus extension fools thousands of Chrome users
The proliferation of online ads means that more and more people are turning to ad blockers, and Adblock Plus remains one of the most popular. Taking advantage of this, fraudulent developers pushed a fake version of the Adblock Plus extension into the Chrome Web Store, bypassing Google's checks and filters.
In all, 37,000 people were tricked into downloading the fake version of Adblock Plus. Google has now acted and removed the fake listing from the store.
What's keeping security experts up at night?

Some of Europe’s top cybersecurity minds have revealed their fears about the future of technology -- with autonomous weapons at the top of their list.
At a panel entitled "the future of cyber security" at this week’s IP Expo event in London, the threat of self-aware AI that can write sophisticated malware and smart weaponry that could be hijacked by cybercriminals were highlighted as major concerns for the coming years.
EFF criticizes iOS 11's 'misleading' Bluetooth and Wi-Fi toggles for being a privacy and security risk
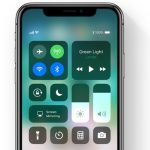
The strange, unintuitive way Bluetooth and Wi-Fi toggles work in iOS 11 has drawn ire from many quarters. The latest voice is that of digital rights group the Electronic Frontier Foundation (EFF) which says that the "off-ish" setting now offered is misleading.
As we have covered in a previous story, Apple has changed the behaviour of the two toggles so that when they are flicked to the off position, the Bluetooth and wireless radios are not actually switched off. EFF says that this is "bad for user security" and calls for greater clarity from Apple.
Google: By only patching Windows 10, Microsoft is putting Windows 7 and 8.x users in danger

We all know that Microsoft’s focus is on Windows 10. The software giant wants users to upgrade to its new operating system, and has regularly spoken about how that OS keeps users safe.
However, according to Google Project Zero researcher Mateusz Jurczyk, by focusing on patching Windows 10, and not applying the same fixes to Windows 7 and 8.x, Microsoft is actually putting users of those two older operating systems at risk.
Disqus hacked!

So, Disqus has been hacked. Yeah, it is what we at BetaNews -- plus many other websites -- use for commenting. Should you be worried? Probably not. You see, this hack happened all the way back in July of 2012. If you joined Disqus after that, you have nothing to worry about. Even if you are using the same login credentials from 5+ years ago, the hackers have only obtained hashed passwords. In other words, they probably haven't decrypted your password.
But OK, even though it is unlikely that your password has been exposed, Disqus is forcing a password reset for all impacted users. Heck, even if you signed up after the hack, it can't hurt to manually change your password, y'all. After all, Disqus didn't even discover the hack on its own, which is worrying. The company was alerted to the breach by the great security researcher Troy Hunt, who found the database floating around the dark web. If you aren't familiar with Hunt, he maintains the excellent haveibeenpwned.com.
IT departments and users are out of step on password security

A new survey reveals that 76 percent of employees say they experience regular password usage problems and more than a third need password-related help desk support at least once every month.
According to the study from password manager LastPass and business intelligence company Ovum nearly three-quarters say they would want to use a tool to help store and access passwords without needing to remember each one if their company offered such a solution.
Report: Russian hackers stole NSA files after identifying them using Kaspersky software

A report by the Wall Street Journal suggests that Russian hackers used Kaspersky software to identify sensitive NSA files -- which they then stole.
The security breach dates back to 2015, and it was made possible when a National Security Agency contractor copied sensitive files to his own computer. Hackers were then able to identify these files because of the contractor's use of Kaspersky software.
Apple makes macOS High Sierra 10.13 safe again with emergency 'Supplemental Update'

Since macOS is a Unix-based operating system, it is often seen as being stable and secure. For the most part, the OS is. With that said, it is not perfect, and certainly not infallible. Quite frankly, no operating system is impervious to security issues.
Unfortunately for Apple, its latest and greatest desktop operating system, macOS High Sierra 10.13, has some very serious flaws. First, it was discovered that the supposedly secure keychain password system could be easily infiltrated by malware. Arguably worse, it was then discovered that encrypted APFS disks had their passwords erroneously saved in plain text in the "hint" field. Yeah, that is not only bad, but embarrassing too. Both of these issues were patched today, however, with the emergency "Supplemental Update."
Recent Headlines
Most Commented Stories
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.