
Disclosing vulnerabilities improves security for everyone
According to a new study 90 percent of IT professionals believe disclosing vulnerabilities serves a broader purpose of improving how software is developed, used and fixed.
The survey from application security testing specialist Veracode finds more than a third of companies received an unsolicited vulnerability disclosure report in the past 12 months, representing an opportunity to work together with the reporting party to fix the vulnerability and then disclose it, improving overall security.

Five vendors account for nearly a quarter of all vulnerabilities
Just five major vendors account for 24.1 percent of disclosed vulnerabilities in 2019 so far, according to a new report from Risk Based Security.
The report also reveals that 54 percent of 2019 vulnerabilities are web-related, 34 percent have public exploits, 53 percent can be exploited remotely and that 34 percent of 2019 vulnerabilities don't yet have a documented solution.
Microsoft quietly fixes SWAPGS processor vulnerability to protect Windows users
It has been revealed that Microsoft silently pushed out a patch to Windows users to fix a vulnerability that affected Intel CPUs produced since 2012 -- which means everything post Ivy Bridge chips.
The SWAPGS vulnerability is similar to the now-famous Spectre and Meltdown chip flaws, and was discovered by security firm Bitdefender a year ago; the fact that it has now been patched was only revealed at the BlackHat security conference. Red Hat says that an update to the Linux kernel is needed to protect against the flaw which it says affects both Intel and AMD chips, although Bitdefender has not been able to find any issues with AMD's processors.

New solution uses backup data to find vulnerabilities
Finding and addressing vulnerabilities is a major headache for businesses, left unattended they can lead to cyberattacks and data breaches.
Data management company Cohesity is looking to make detection easier with a new application that uses backup data to assess the vulnerabilities, or risk posture, of an enterprise's IT environment.

Flexera helps businesses tackle vulnerabilities more quickly
In the modern world it's vital for businesses to know what software they have, and where vulnerabilities lie. Flexera already assists IT and security teams to do this with its Software Vulnerability Manager, and it's now launching new modules to help address threats.
It's produced two new modules for SVM. The first of these is the Vendor Patch Module, which allows organizations to take advantage of insights and mitigate them more quickly, by using comprehensive patch coverage -- with more than 1,000 out-of-the-box patches. Additionally, the Vendor Patch Module delivers details to help companies more easily create over 1,000 additional patches.
Alleged critical VLC flaw is nothing to worry about -- and is nothing to do with VLC
There has been a degree of confusion over the last few days after news spread of a supposed vulnerability in the media player VLC. Despite being labelled by security experts as "critical", VLC's developers, VideoLAN, denied there was a problem at all.
And they were right. While there is a vulnerability, it was in a third-party library, not VLC itself. On top of this, it is nowhere near as severe as first suggested. Oh -- and it was fixed over a year ago. An older version of Ubuntu Linux was to blame for the confusion.

Cyber hygiene is at an all-time low
Well-known attacks and attack vectors remained successful because security personnel did not address vulnerabilities and apply patches according to a new report from cybersecurity and visibility business Ixia.
IT vendors created code or configurations that led to many successful security breaches in 2018, but IT operations and security personnel shared the blame due to ignorance of the latest patches and challenges in deploying patches in a timely manner.

New vulnerability reporting platform aims to make open source safer
Vulnerabilities in open source code represent a risk for businesses, but the process of reporting them is cumbersome and that can leave software open to risk.
Without a standard for responsible disclosure, even those who want to disclose vulnerabilities responsibly can get frustrated with the process and turn to public lists or social media, where bad actors can easily find the details before fixes are created.
Security researchers reveal details of serious bug in compression tool WinRAR
If you're a user of WinRAR -- a staple tool for decompressing files whose popularity stems from not only its support for RAR files, but also its never-ending trial period -- it's time to ensure you have the latest security patch installed.
Security experts from Check Point Research have revealed details of a serious bug that has been present in the software for at least 14 years. The archiving tool was found to have a vulnerability in one of its .dll files, which could be exploited by simply opening a compressed file, and allows an attacker to "gain full control over a victim's computer".

Machine learning tool helps prioritize vulnerabilities
One of the keys to keeping systems secure is to effectively prioritize vulnerabilities. Given the volume, with 16,500 new vulnerabilities disclosed in 2018 alone, though this is a tough task.
To help businesses focus on the highest risks, Tenable is launching a new Predictive Prioritization tool that uses machine learning to zoom in on the three percent of vulnerabilities with the greatest likelihood of being exploited in the next 28 days.
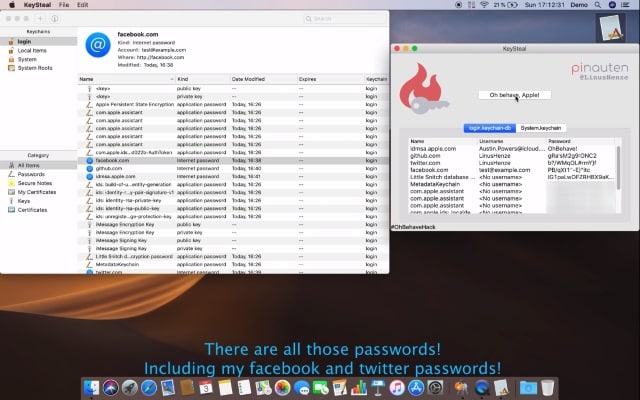
KeySteal: huge macOS vulnerability can be exploited to reveal keychain passwords
A disgruntled security researcher has revealed a one-click exploit that takes advantage of a macOS vulnerability to reveal all of the passwords stored in a Mac's keychain.
Linus Henze developed an exploit tool called KeySteal that uses a 0-day bug to extract keychain passwords on macOS Mojave and older. He stresses that neither root access nor administrator privileges are required, and no password prompts are generated by the tool. Henze is not going to help Apple to fix the problem because the company does not offer a bug bounty program for macOS.

New Fortnite vulnerabilities put users' privacy at risk
Researchers at security firm Check Point have uncovered vulnerabilities in the popular online game Fortnite that would allow attackers to intercept and steal Fortnite users’ login credentials without them being aware of the theft.
The attack manipulates Fortnite's login process to capture usernames and passwords. Armed with these details attackers could view any data stored in the game, buy more V-Bucks in-game currency at users' expense, and access all the user’s in-game contacts as well as listen in on and record conversations taking place during game play.

Windows 10 bug could allow files to be overwritten, researcher shows
A security researcher has released proof-of-concept code for a zero-day exploit in Windows 10. The bug was revealed by SandboxEscaper, a researcher who has exposed Windows vulnerabilities in the past.
The latest bug makes it possible to overwrite files with arbitrary data, and while there are numerous criteria that must be met in order for the vulnerability to be exploited, it is still potentially serious. SandboxEscaper warned Microsoft about the problem on Christmas day, before publishing the PoC a couple of days later.

Almost a quarter of reported vulnerabilities have no known solution
The number of reported vulnerabilities in 2018 is seven percent down on the same period last year, according to a new report from Risk Based Security.
It's not all good news though, as 24.9 percent of 2018's reported vulnerabilities currently have no known solution which is a reminder that, while patching is very important, it can't be relied on exclusively as a remedy.

Exploit developer discovers security vulnerability in VirtualBox and publishes a full guide to exploiting it
A security researcher has not only discovered a vulnerability in the virtualization tool VirtualBox, but has released details of the exploit and a step-by-step guide to the zero-day vulnerability.
Russian exploit developer Sergey Zelenyuk found a way to break out of VirtualBox's virtual environment and he chose to go public with the vulnerability because of his displeasure at the "contemporary state of infosec, especially of security research and bug bounty". Having told Oracle about the problem, he also tired of the "delusion of grandeur and marketing bullshit" he experienced in the infosec community.
