
Donald Trump, UEFA European Championship, and Inside Out 2: there are no surprises in Google’s top trending searches of 2024
We’ve reached that point of the year. Spotify Wrapped has happened, and now it’s time for endless ‘year in review’ and ‘best of 2024’ outpourings. Not wanting to miss out, Google has revealed the top trending searches of 2024.
The very nature of listing the top trends is that they are popular, and therefore predictable. As such, the appearance of searches relating to the US election was to be expected, as was people looking up the meaning of “demure”. So what else does Google have to share with us?

Willow: Google reveals new quantum chip offering incomprehensibly fast processing
For all of the focus on AI, for many people, the future lives in quantum computing. Google is among those who agree, and the company has just unveiled its latest advancements in the field -- its quantum chip, Willow. Like quantum physics and quantum mechanics, the numbers and concepts involved in quantum computing are extraordinarily difficult to imagine.
Revealing its advancements, Google says that its quantum chip took less than five minutes to perform tasks that would take even the fastest supercomputers 10 septillion years. Providing some sense of perspective, Google points out that this is “a number that vastly exceeds the age of the Universe”. So what is it that makes Willow so special -- and so fast?

Microsoft blocks Windows 11 24H2 upgrades for some Google Workspace and Outlook users
The number of roadblocks standing in the way of updating to the latest version of Windows 11 seems never-ending. The latest issue affects people using certain versions of Google Workspace Sync.
Following the appearance of error messages and problems between Outlook and Google Workspace Sync, Microsoft has taken the decision to block the availability of the Windows 11 2024 Update. There is good news, however. The fix is easy to implement, so updating to Windows 11 24H2 is far from being an impossibility.

Macally launches versatile iPad case with backlit keyboard and trackpad
Macally has launched its latest accessory for iPad users, a versatile iPad Case with Keyboard designed for productivity and protection. Compatible with the latest iPad Air and iPad Pro models, this new case combines a detachable backlit keyboard, a multi-touch trackpad, and a fully adjustable stand, making it ideal for work, study, or entertainment.
According to Joey Ang, General Manager at Macally, “The iPad Case with Keyboard enhances productivity and flexibility. It’s the smart solution for work, play, and everything in between.”

From ordinary to extraordinary: Seelen UI transforms Windows 10/11 into the OS you've always wanted -- download it now!
For many users, Windows 10 and 11 feel like missed opportunities in design evolution. The look is functional but unremarkable, dominated by flat icons and muted colors that lack character or charm. While simplicity can be effective, the current design comes across as a bit sterile, offering little of the warmth or personality that once defined Windows. The result is an OS that sadly feels more clinical than engaging.
Seelen UI is a free tool that reimagines what a Windows desktop can be, giving users the tools to break free from this monotony. With an array of customization features designed to prioritize both style and practicality, it allows users to craft a unique workspace.

Reddit Answers tool uses AI to enhance search experience
Reddit is diving deeper into AI with the introduction of Reddit Answers, an AI-powered tool designed to provide curated insights, recommendations, and discussions on virtually any topic. This new feature, currently in testing, aims to make it easier for users to tap into the platform’s wealth of community-generated knowledge.
With Reddit Answers, users can ask questions via an AI-powered conversational interface. The tool delivers curated summaries of relevant discussions, complete with links to related communities and posts. Users can skim snippets and answers directly or explore deeper by engaging in full conversations or asking follow-up questions, either their own or suggested by the platform.

IBM brings optics into the data center to save energy and boost speed
When we think of optical technology it tends to be in terms of transmitting data over long distances. Today IBM is unveiling a breakthrough in optics technology that for the first time puts the speed and power of fiber optics inside servers and onto circuit boards.
Using a new process that replaces electrical wires with optical waveguides,this effectively enables chip connectivity at the speed of light.

More gamers can install Windows 11 24H2 after Microsoft semi-lifts update block
There are many barriers to running Windows 11, and even if you are using the operating system, you may find that you’re not able to run the very latest version. A variety of problems means that Microsoft has put update blocks in place for systems that meet certain criteria, but is gradually easing up on some of them.
Gamers are among those who have found themselves unable to update to Windows 11 24H2, especially fans of Ubisoft titles. With some of the issues having been resolved, Microsoft has now partially lifted the block on updating.

The race against AI web scrapers: effective strategies to protect your data [Q&A]
A surge in artificial intelligence (AI), generative AI (GenAI), and machine learning (ML) technologies is creating a massive online appetite for data. These tools are hungry for training data, this has boosted AI web scraping, which sits in a legal gray zone. Sometimes it's legal, sometimes it's not, but what's clear is that it's having ripple effects across online businesses.
We talked to Nick Rieniets, field CTO of Kasada, to learn more about the impact of web scraping and what companies can do to protect their content.
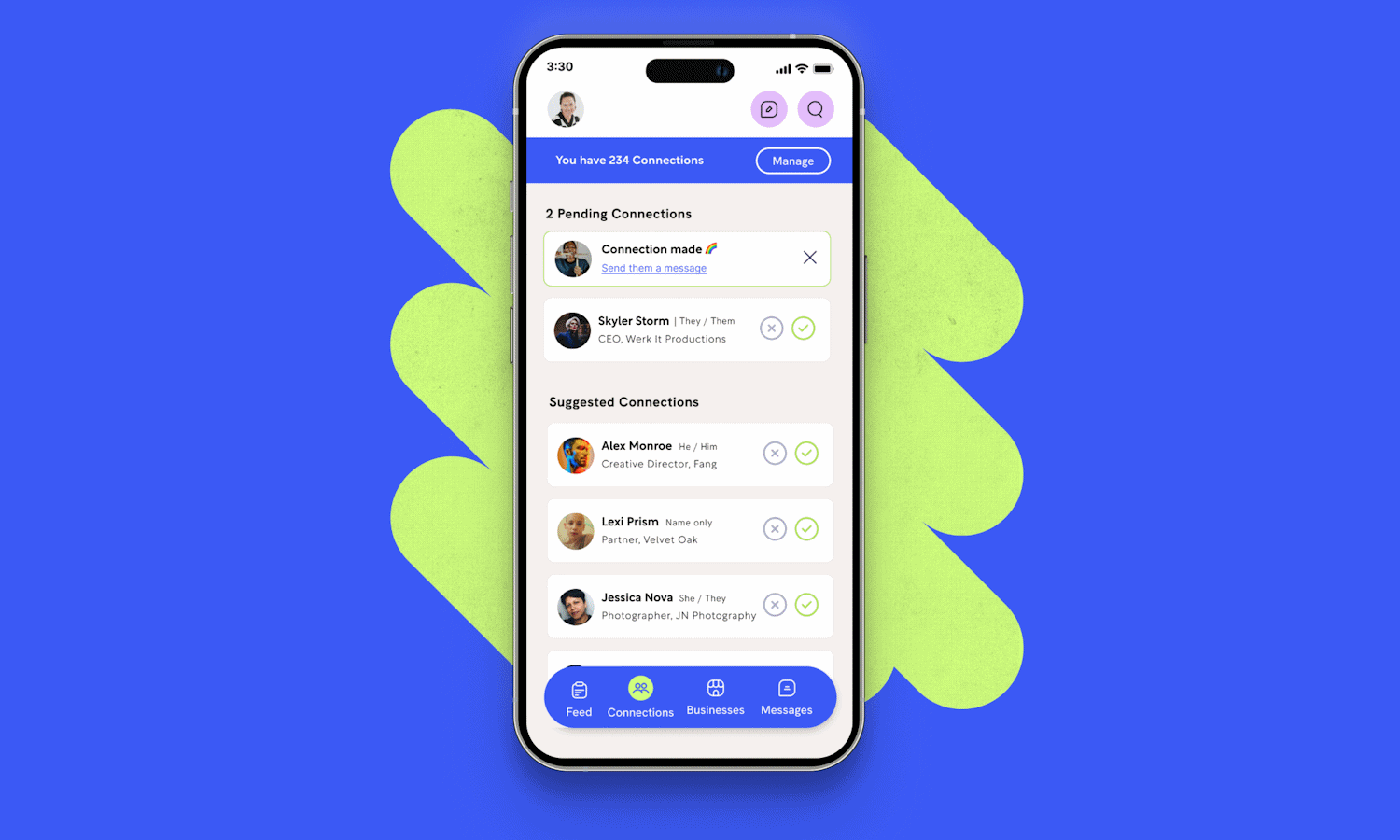
Famm Connect is a queer-focused LinkedIn for establishing LGBTQIA+ business connections
Finding the right platform through which to make meaningful and valuable connections can be difficult, and this is certainly true for LGBTQIA+ professionals and business owners. LinkedIn may be the go-to platform for establishing business connections, but it is very broad and almost too big.
Stepping in to fill a significant gap in the market is Famm Connect, which is billed as “the first mobile app for LGBTQ+ professionals” and the “queer LinkedIn”. The aim is to create a safe environment to establish connections and relationships.

Install Manjaro 24.2 today and leave Microsoft Windows 11 to the boomers
If you’ve been looking for a reason to ditch Windows 11, the latest version of Manjaro Linux, 24.2 Yonada, might just be it. This new release brings updates across its GNOME, Plasma, and XFCE editions, offering a polished experience for both newcomers and seasoned Linux users.
The GNOME edition of Manjaro 24.2 has been updated to the GNOME 47 series, bringing features that put Windows 11’s customization options to shame. For example, users can now choose from a range of accent colors instead of being locked into a single default. Scaling improvements ensure icons and interface elements look sharp and usable, even on older or lower-resolution displays. If you’ve ever been frustrated with screen recording on Windows, Manjaro’s GNOME edition now supports hardware encoding for Intel and AMD GPUs, reducing system strain and providing a smooth recording experience.
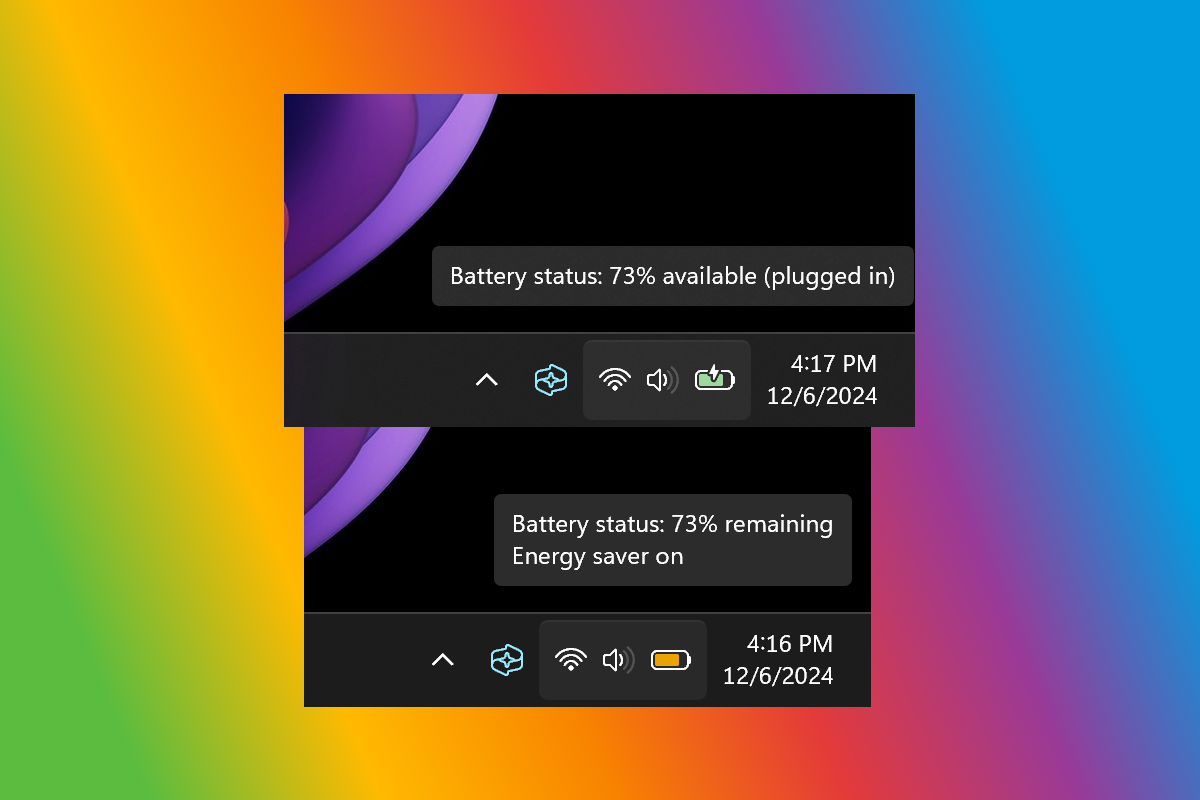
Microsoft brings big change to Windows 11’s battery indicator making it even more useful
The battery indicator in the Taskbar of Windows 11 is – as it has been for many years in previous versions of Windows – entirely functional. But there has always been potential for it to be more.
Now Microsoft is taking action to help the humble battery indicator to reach its potential and ascend beyond merely being good enough. New features means that it will tell you more than just how much charge you have left.

Save $18! Get 'Artificial Intelligence For Dummies, 3rd Edition' for FREE
Artificial intelligence is swiftly moving from a sci-fi future to a modern reality. This edition of Artificial Intelligence For Dummies keeps pace with the lighting-fast expansion of AI tools that are overhauling every corner of reality.
This book demystifies how artificial intelligence systems operate, giving you a look at the inner workings of AI and explaining the important role of data in creating intelligence. You'll get a primer on using AI in everyday life, and you'll also get a glimpse into possible AI-driven futures.

Wine 10.0-rc1 brings major Windows compatibility updates to Linux
The world of Windows application compatibility on Linux has just reached a new milestone. The Wine team has unveiled Wine 10.0-rc1, the very first release candidate for the highly anticipated Wine 10.0. This isn’t just another update -- it’s the beginning of the yearly code freeze, a crucial period where the team hones the software to perfection. Enthusiasts and developers are encouraged to put this release to the test and report any bugs, ensuring the final 10.0 version shines.
Wine 10.0-rc1 isn’t playing it safe. It brings several key upgrades and features that signal serious progress. Among the highlights, the bundled vkd3d has been updated to version 1.14, promising improved Direct3D 12 support. Meanwhile, the Mono engine has been upgraded to version 9.4.0, delivering better .NET compatibility. There’s also an initial version of a Bluetooth driver, a major leap toward better hardware interaction.

Lexar introduces SL300 and ES3 portable SSDs with fast speeds and durable design
Lexar has launched two new portable SSDs, the SL300 and ES3, targeting everyday users and professionals who value speed and reliability in data storage. Both drives offer read speeds of up to 1050MB/s and write speeds of 1000MB/s, claiming to be up to 9.5 times faster than traditional HDDs.
The SL300 and ES3 share nearly identical specifications, with no notable differences apart from their color -- the SL300 comes in black, while the ES3 is silver. Both drives are equipped with double-layer graphite sheets to manage heat during use and feature drop resistance up to 2 meters, making them durable options for those on the move.
