Google makes it easier to try out beta Android apps with new Early Access section in the Play Store
As the Windows 10 insider preview program has demonstrated, people love to get their hands on pre-release software. While it's easy to install beta software on a desktop computer, it has not been as straightforward for Android users. Until now.
Google has added an Early Access section to Google Play which -- you've guessed it -- features not-quite-ready-for-prime-time apps in beta form. The new section makes installing beta apps as simple as installing any other app and, after rolling out to a few users this week, the option is now available to everyone.
Is the Internet of Things the next Industrial Revolution?

The Industrial Revolution changed society and led to the growth of towns and cities with consequent mass production and movement of population.
Electronics retailer RS Components has produced an infographic looking at how the Internet of Things is leading a move to create a new industrial internet, powered by intelligent machines.
Google's 60 Tbps undersea cable connecting US and Japan is live

Japan’s Internet is set for a large speed boost as Google’s 9,000km undersea Internet cable that connects the country to the United States is now officially up and running.
In 2014, the company announced that it would lay an undersea cable connecting the two countries that would have a 60 terabits per second capacity. Google’s senior vice president of technical infrastructure, Urs Hölzle, said the cable has a capacity that is "more than any active subsea cable" and is "10 million times faster than your cable modem".
AVG announces 6 new tools to free your data from ransomware

Ransomware has gone mainstream with several high-profile attacks. It essentially locks your data away and demands money to free it – essentially mob protection money. While some tools have been released to aid frantic people in these times, most versions have gone unfixed.
Now AVG, the free antivirus company, has come out with six new tools designed to fight this affliction. Each is for a different form of this malware.
Microsoft sets off fireworks with Windows 10 Insider Preview Build 14379 for PC and Mobile

Fourth of July is coming up this Monday, and tomorrow is Friday. This is significant in the business world, as many folks transform a three-day weekend into four by taking off the Friday before a holiday. In other words, it is a great way to get a mini-vacation while only sacrificing a single vacation day.
Apparently, Dona Sarkar and team are getting an early start on celebrating USA Independence. In anticipation of the extended weekend, she is setting off some fireworks -- figuratively speaking, that is. Today, Microsoft releases Windows 10 Insider Preview Build 14379 for PC and Mobile to the fast ring.
Cisco buys cloud security provider CloudLock

Cisco has announced that it will be acquiring the cloud-based security provider CloudLock for $293 million in cash and equity.
CloudLock makes use of application program interface (API) technology to allow enterprises to apply and monitor the security of documents and other content that is accessible via cloud-based applications. The service works with Office 365, Google Drive, Salesforce applications and thousands of other apps and programs.
Google reveals that Android N will be called... Android Nougat!

The developer previews of Android N have been available for a little while now, giving a tantalizing taste of what’s to come. But one thing has been missing: the name.
After months of teasing and misdirection -- there can't be many people who weren't expecting to see Android Nutella -- Google has officially announced that Android 7 (probably) will be known as Android Nougat.
Let there be light: Why visibility is key to building an effective mobile policy

Consider this: Unrestricted use of Tinder may not pose a problem at a company where the majority of staff is over fifty, but if you work with millennials, you may need to swipe left and reject your current mobile policy. Don’t let your company be the next one to lose precious data and suffer the devastating cost of a data breach simply because you lacked visibility and control over how your investment in mobility is having an impact on the organization.
The mobile device is a distinctive technology that delivers tangible benefits in both personal and business settings. According to IDC’s U.S Mobile Worker Forecast, mobile workers will account for nearly three quarters (72.3 percent) of the total U.S. workforce -- or 105.4 million employees -- by 2020, creating an environment where workers expect to leverage mobile technology at work. As enterprise IT begins to more widely deploy mobile technologies in support of everyday business, mobile devices must increasingly meet corporate standards for security, compliance and acceptable use.
Declare independence from Windows 10 by downloading Linux Mint 18 'Sarah' now!

As we approach the Fourth of July weekend, I begin thinking about independence. I am very proud of my forefathers for defeating the British -- our now-ally -- and creating our great nation, the USA.
With that said, there are other things from which you can declare independence -- such as Windows 10. Look, I think Microsoft's desktop operating system is pretty good, although I understand that some folks are fearful of spying and forced-upgrade behavior. If you want to be free from Microsoft and Windows, I have good news -- today, Linux Mint 18 is finally available. Will you download it and declare your independence?
Anonymous takes the FBI to task for corruption

Hacktivist collective Anonymous targets all sorts of people and organizations. Past and on-going operations have focused on Islamic State, white supremacists, the Church of Scientology, Ku Klux Klan, and Donald Trump.
Whatever your view on Anonymous, the group certainly likes to pick fights with high profile foes. The latest organization to have the Anonymous spotlight shone on its affairs is the Federal Bureau of Investigation.
Home alarms let users keep default credentials

German investigative journalists from the c’t magazine said many home security systems come with a huge vulnerability which can put every home using the system at risk.
The vulnerability, however, is nothing fancy in hacking terms -- it’s pretty obvious and straightforward, but frequently overlooked. You see, similar to Internet routers, these home security systems are configured through a browser, and many come with easily crackable passwords like "1234" or "admin1234".
At long, long last, Google Maps on Android and iOS has multiple destination support
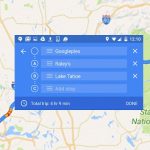
Google Maps has long been helping walkers, drivers and cyclists get from A to B. But for far too long, the desktop version of the navigation tool has been more powerful than the mobile version -- which is silly, really, as the mobile app is the one you're going to use while, you know, traveling.
Today, Google is rolling out an important new feature to the mobile app -- the ability to configure a route with multiple stop-off points along the way. Getting from A to B is great, but sometimes you need to go via X and Y. Now you can.
Euro 2016 app leaking private user data

I’ve been trying not to think about Euro 2016 after England’s whimpering exit on Monday night, but new research from mobile security and management firm Wandera has grabbed my attention.
According to analysis of data traffic patterns from enterprise mobile devices, the official UEFA Euro 2016 Fan Guide App is leaking user’s personal information -- including usernames, passwords, addresses and phone numbers -- over unsecure internet connections.
What makes an adversary profile invaluable?

One of the most common questions I am asked when collaborating with customers is "…what makes a useful adversary profile?" The easy answer is any summary that allows your team to make faster and more accurate decisions when push comes to shove, but the deeper answer is more artful than scientific. Adversary profiles are the intelligence intersection across a team’s defensive efforts and can demonstrate a distinction from teams who have made a conscious decision to transform from 'whack-a-mole' to 'know thy enemy'.
So…What makes an invaluable adversary profile? Here are a couple points you should consider when structuring an adversary blueprint.
New cloud platform gives companies insight into channel sales

Companies selling IT solutions via channel partners can easily find that they spend all their time dealing with resellers and distributors, and consequently lose touch with their end users.
Channel management company Zyme is launching a new cloud platform that helps global B2B and B2C enterprises monitor and optimize the performance of their distribution channels through timely, actionable intelligence.
Recent Headlines
Most Commented Stories
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.