
Guarding against supply chain attacks [Q&A]
In recent years supply chain attacks have become much more commonplace, targeting vulnerabilities and getting legitimate apps to distribute malware.
We spoke to Nir Valtman, CEO and founder at Arnica, to discuss the issues these attacks raise and how organizations can defend against them.

HP could take up to three months to patch a critical vulnerability in HP Enterprise LaserJet and HP LaserJet Managed printers
HP has issued a security warning about a vulnerability which affects numerous HP Enterprise LaserJet and HP LaserJet Managed printers. The flaw is tracked as CVE-2023-1707 is described as "critical" having been assigned a CVSS rating of 9.1.
Despite the severity of the bug -- which HP says could lead to "information disclosure when IPsec is enabled with FutureSmart version 5.6" -- it could take up to 90 days to issue a fix. However, the company has provided a temporary firmware mitigation.
Microsoft releases PowerToys v0.69.0 with new registry editing tool
It is a month since Microsoft added Mouse Jump and Paste As Plain Text utilities to PowerToys, and now there is yet another new toy to play with -- Registry Preview.
We first heard about this new registry editing and visualization module last week, and now it has been officially released as part of PowerToys v0.69.0. Microsoft says that the v0.69 release cycle focuses on new features, stability and improvements, and the company gives early notice for v0.70 which is due for release next month.

Get 'The Courage Playbook' for FREE
In The Courage Playbook: Five Steps to Overcome Your Fears and Become Your Best Self, Gus Lee, bestselling author and leadership expert, delivers an astonishing reveal that with moral courage, we can overcome our fears.
This is a practical guide to gaining your courage to live rightly, treat others without bias and lead inspirationally.
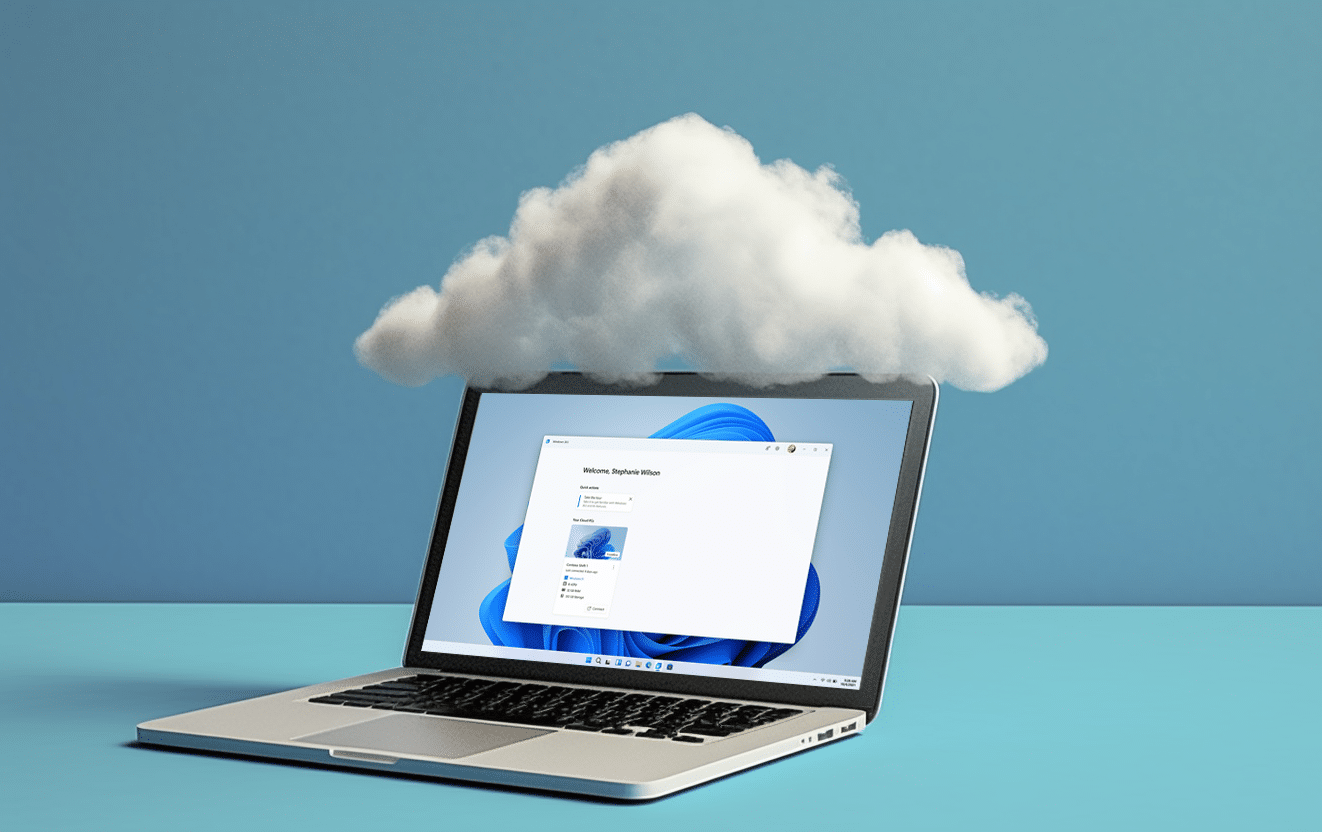
Windows 365 Frontline is now available in public preview
Two years ago, Microsoft unveiled its subscription-based Windows 365 service which allowed users to stream Windows 10 and Windows 11 from the cloud to any device.
Today, it announces Windows 365 Frontline is available to preview, aimed at workers who only need a Cloud PC for a limited amount of time during a working day.

Cloud spending has become a critical performance indicator for data teams
Cloud spending is now a critical KPI for the majority of data teams, according to a new report. Almost 80 percent of business stakeholders say cloud spending is a critical KPI while 55 percent of data practitioners say the same.
The study, from data observability platform Unravel Data, surveyed 350 data professionals at the Data Teams Summit event earlier this year and shows that in addition to cloud spending being elevated as a top KPI, 44 percent report that they believe that they are leaving money on the table when it comes to their public cloud utilization.
Don’t let one 'war room' too many exacerbate the risk of quiet quitting in your DevOps team
As organizations and their customers become more reliant on digital services, DevOps teams are often required to get together quickly to troubleshoot and resolve outages or user experience problems.
However, against the backdrop of the 24/7 economy and a shortage of technology skills, it’s time to reassess whether these 'war rooms' remain an effective tactic for dealing with urgent issues. Or, could they be exacerbating the challenges organizations face in retaining staff and managing skilled DevOps teams’ workloads?

Microsoft 365 Defender is now AI-powered
Since its inception, Microsoft Defender Antivirus (FKA Windows Defender) was considered somewhat of a joke by power users. They would assert that it provided you with the protection of an umbrella in a hurricane. While its deficiencies were often exaggerated, indeed, it didn’t give you the same depth and scope as high-quality third-party solutions.
When Bitdefender retired its free antivirus solution in 2021 (only to release a new free antivirus in 2022), many turned back to Microsoft Defender. After all, Microsoft should ultimately know the best ways to secure its software. It's surprising it took so long for the company to expand the coverage of its Microsoft Defender line, especially, with the largest share of its revenue being made from intelligent cloud computing.

What are the top 5 tools to effectively combat fake news?
When we’re going about our days -- ingesting media from a mountain of different sources -- it is always possible that the information we come across, be it in print, radio, or on the internet, may not be accurate. False information has been around since the beginning of time, but due to the ever-present online world, we are now more likely to consume content that is distorted or fabricated unintentionally.
People are used to having their thoughts shaped by the material they come across online, for example, through influencer marketing or celebrity endorsements. Even if facts don't back up these opinions, they still have a significant impact, and a lot of false news is created to evoke strong emotions. Therefore, it is essential that we take a moment to check if what we have read or heard is true when our feelings are affected.
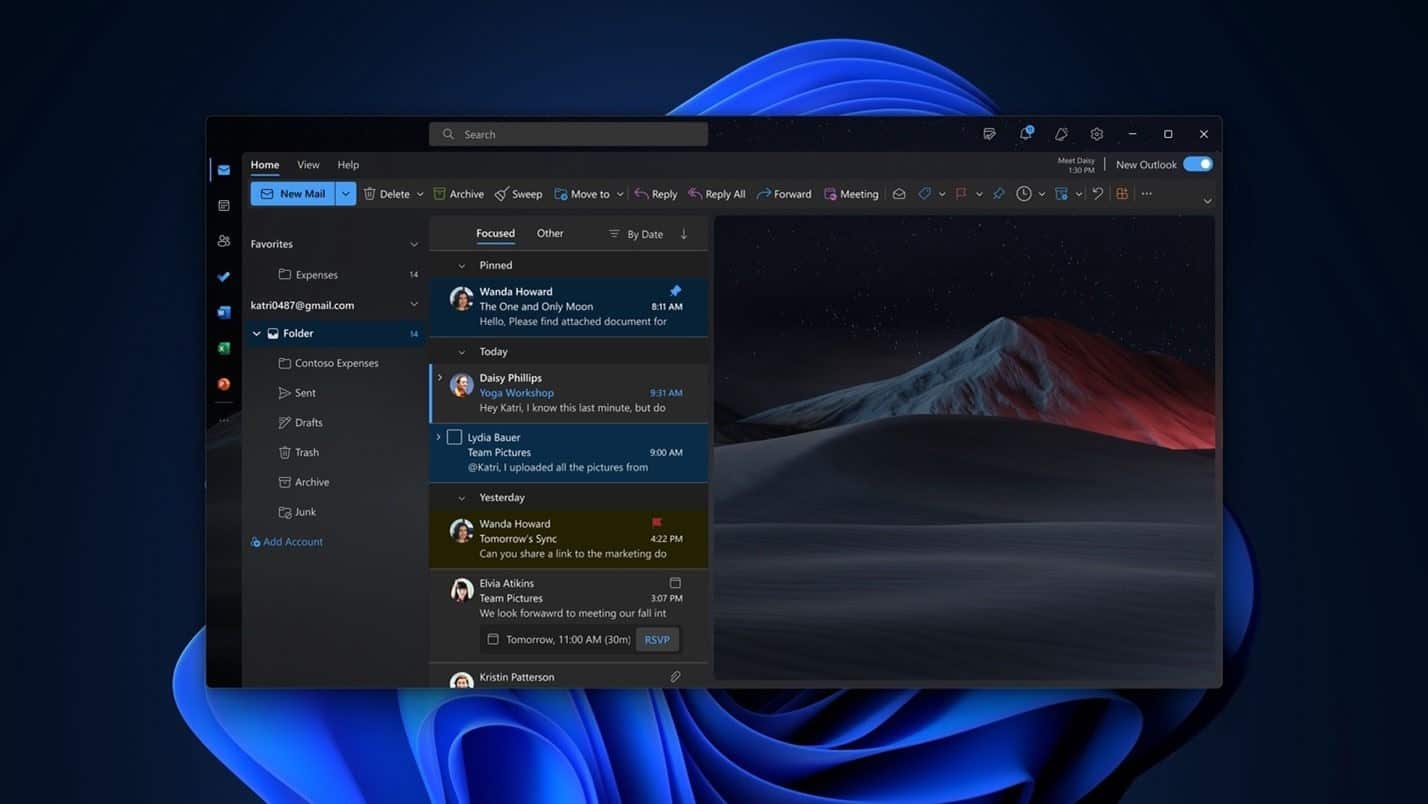
Microsoft brings Gmail support to the new Outlook for Windows preview
Having announced its plans to do so last year, Microsoft has added support for Gmail accounts to the new Outlook for Windows preview for Windows 10 and Windows 11.
Gmail support is something that has been available to Office Insiders for a little while, but now the company is opening it up to anyone who is running the preview of the new Outlook for Windows. Microsoft says that it also plans to add IMAP support as well as support for Yahoo and iCloud, but for now it is Gmail users the company is treating -- but there is something you need to do first.

How to use Windows Sandbox to open files in a secure environment
Windows Sandbox is a built-in feature of Windows 10 and Windows 11. Its main purpose is to provide a safe environment for running applications. Anything that is executed in the sandbox, e.g., a software that is installed, remains trapped inside. It can’t break out and affect the "real" operating system.
As a consequence, malware, spyware and other unwanted and undesirable code, can’t infect the system or pull data from it.

Get 'The Python Workshop -- Second Edition' (worth $39.99) for FREE
Python is among the most popular programming languages in the world. It’s ideal for beginners because it’s easy to read and write, and for developers because it’s widely available with a strong support community, extensive documentation, and phenomenal libraries -- both built-in and user-contributed.
Expert authors have designed this project-based course to get you up and running with Python.

UK telcos not ready for 'One Touch Switching'
The UK telecoms regulator Ofcom's 'One Touch Switching' initiative -- intended to make it easier for consumers to change broadband providers -- has been delayed as service providers aren't ready.
Whilst it was announced in 2021 and meant to come into force this Monday (April 3rd), One Touch Switching has now been pushed back and Ofcom has begun an enforcement program.

Amazon is closing Book Depository after 18 years of free worldwide delivery
Book lovers around the world are mourning the loss of Book Depository following the announcement that the Amazon-owned online bookstore is to close.
Based in the UK, Book Depository has been offering free worldwide delivery of books, including many titles that are hard to get hold of from other sources, since 2007. The shutdown date is imminent -- April 26 -- but as orders are being accepted until that day, there is still time to grab a bargain.

Organizations struggle to manage OT security risks
A new survey from OTORIO and ServiceNow reveals that 58 percent of organizations identify their operational technology (OT) cybersecurity risk level as high or critical.
However, the survey of 200 IT and OT leaders shows only 47 percent of companies surveyed have an OT cybersecurity solution in place, and 81 percent of respondents still manage their OT risks manually rather than having an automated solution.
