
Translation Service DeepL adds Glossary feature to customize translations
Translation service DeepL just announced the introduction of the new glossary feature on the site to improve translations further.
DeepL was established in 2017 as an alternative to Google Translate, Microsoft Translate and other translation services. The developers promised that translations would be more human-like than those of competing services; several blind tests were conducted by DeepL to confirm the claim.

Women are better at cybersecurity than men
Women are better at cybersecurity and protecting themselves online, new research by password manager app NordPass suggests.
The survey shows that women are more concerned about the potential harm of their personal online accounts being hacked. They also tend to use unique passwords more often than men.

Zoom has another security update on the way to cut down on Zoombombing
It seems like it's been a little while since we heard much about Zoom, but we're still in the company's self-imposed 90-day security clean-up operation.
Having already released numerous updates to help lock down the video conferencing software, Zoom is about to release a new update that will help clamp down on the problem of Zoombombing for people with free accounts.

ESET improves security management for Azure users
As organizations move more of their systems to the cloud, they need security solutions that maintain visibility while keeping them safe.
Cybersecurity company ESET is releasing an upgraded version of its Security Management Center for Microsoft Azure, aimed at providing complete, real-time network visibility.

Twitter gives some users the ability to edit tweets... sort of
For years people have been asking -- nay, begging -- Twitter to add the option of editing tweets, and for years the company has resisted. Now, for a handful of iOS users, this is changing.
If you've been holding your breath for an Edit Tweet button, exhale now before you pass out. A proper editing option is not likely to arrive any time soon -- if at all -- but as part of an experiment, Twitter is testing the ability to "revise" tweets.

Microsoft releases Forza Street for free on iOS and Android, but the game is a total clunker
While video games on PCs and consoles can be great, the titles released for smartphones are often quite bad. On-screen controls can be inaccurate and hard to use, leading to a very frustrating experience. Alternatively, developers can "dumb down" their games for mobile with simpler controls, but this often makes them nothing more than time-wasters -- something to do while sitting on the toilet, for instance.
Today, Turn 10 Studios (a Microsoft-owned game studio) releases Forza Street for iOS and Android. The racing game is "free" to play, which is cool, but sadly, it does offer in-game purchases to try and suck some money from your wallet. I installed it on my iPhone, and from what I can tell, the game kind of stinks. In my time "racing" I didn't even get to steer the car! Seriously. Instead, you just hold down a virtual gas pedal. Around turns, you let go of the pedal when the road turns yellow and then hold it down when it turns yellow again. That's pretty much it -- that seems to be the game. Maybe it gets better later, but I won't be finding out. Does the game look good? Absolutely. Is it fun? Heavens, no!

Firefox 76 expands Lockwise password manager capabilities
Mozilla has released Firefox 76.0 for Windows, macOS and Linux, the latest in its long line of major updates to the venerable open source browser.
The chief focus in this new release is the further development of Mozilla’s Lockwise password manager. Users gain several enhancements including alerts of website breaches with prompts to update all online accounts that share the same password.

Ashampoo WinOptimizer 18 is here to speed up and help maintain your PC
Everyone likes the idea of a computer speed boost, right? While some people are happy to get theirs hands dirty and spend time tinkering with endless settings, there are plenty of others who would rather that things were taken care of for them. Ashampoo has just released WinOptimizer 18, the system optimization software that aims to cater for people who fall into both camps.
This is a company that has a long record of producing handy utilities for Windows, and with WinOptimizer 18 this tradition continues. The program is made up of a series of system optimization and clean-up modules that you can work through one at a time, or you can use the one-click optimization to automate and speed up the process.
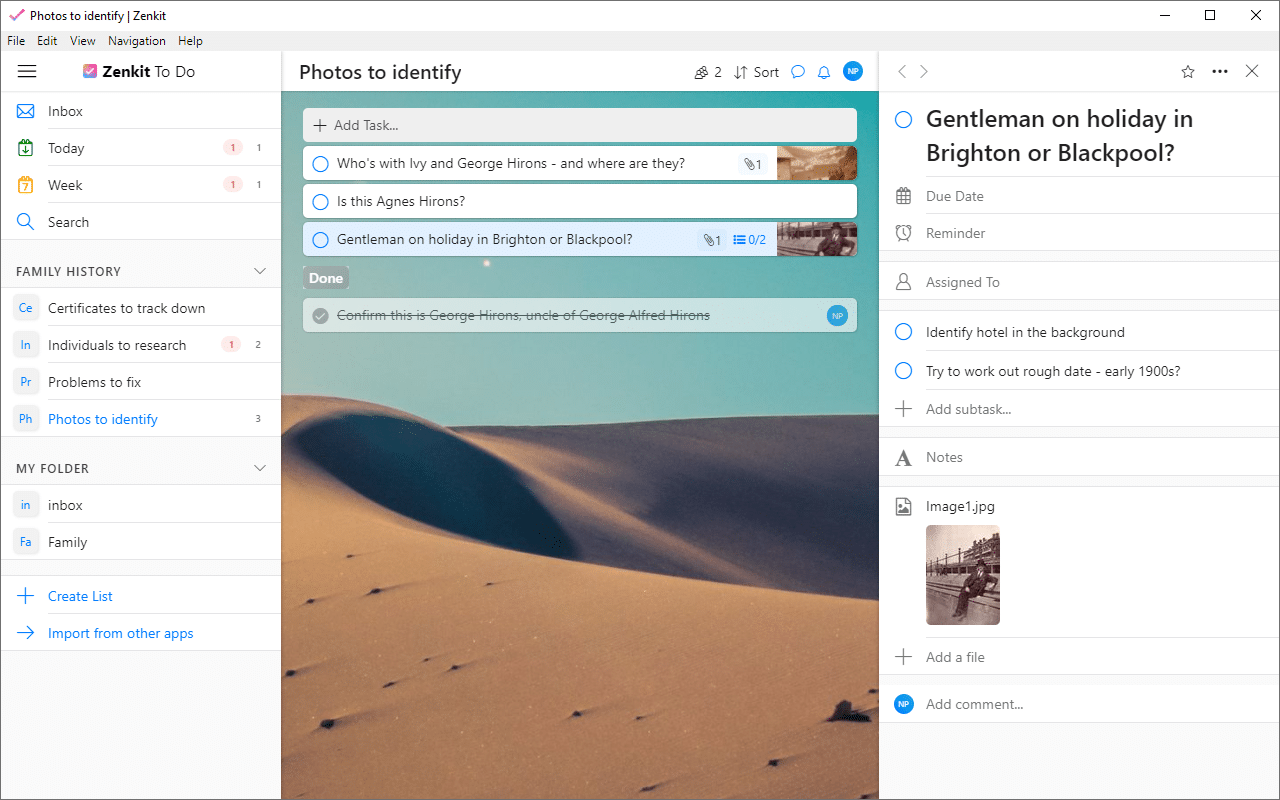
Wunderlist is (almost) dead, long live Zenkit To Do!
The end of Wunderlist is nigh: from tomorrow, Microsoft will finally kill the brilliant task-management app in favor of its own Microsoft To Do application, which while introducing many of Wunderlist’s features has retained a distinct identity of its own.
If you’ve tried To Do and not liked it, then here’s the good news: you don’t need to put up with Microsoft’s replacement. Thanks to the good folks at Zenkit, an app exists that succeeds in retaining the Wunderlist look, feel and core feature set. That app is Zenkit To Do, and if you’re quick, you can transfer your data directly to it from Wunderlist.

How mobile data costs compare around the world
If you have a monthly mobile phone plan you may not think too much about the price you pay for mobile data. However, comparison site cable.co.uk has been looking at mobile data costs around the world with some surprising results.
The United States is one of the most expensive developed nations for purchasing mobile data, coming in 188th in the world, with an average 1GB cost of $8.00 -- well above the global average of $5.09.

How AI and automation is keeping company efficiency up right now
AI and automation were becoming standard business practices long before the pandemic. As coronavirus shutdowns send shockwaves throughout the economy, though, companies turn to these solutions faster than ever before. Organizations around the world are investing in automated systems to maintain efficiency through the outbreak.
Companies are having to deal with a myriad of complications as a result of the ongoing COVID-19 pandemic. Many have had to scale back and let staff go, and some are facing new and unexpected demands. Tools like AI have become vital to sustainment amid the growing recession.

Traumatizing content and towering heights: America's three worst tech jobs
What is the worst job in the tech industry? Even in the United States, where Occupational Health and Safety (OSHA) rules are intended to protect workers from dangerous or inhumane working conditions, there are a few tech jobs in which the cons of the position appear to significantly outweigh the pros.
Here are three of the very worst jobs in technology.

More than half of cyberattacks infiltrate environments without detection
While organizations continue to invest significant amounts in security controls and assume that this means assets are fully protected, the reality is that a majority of attacks successfully infiltrate production environments without their knowledge.
This is among the findings of a new report from Mandiant Solutions -- the threat intelligence arm of FireEye -- based on real attacks, specific malicious behaviors, and actor-attributed techniques and tactics.

'SideScanning' technology offers deeper multi-cloud visibility
While network scanners and agent-based security tools are commonplace, they come with significant operational costs, but still offer only partial visibility, leaving the organization vulnerable to breaches.
Orca Security has produced a patent pending SideScanning technology, which is based on reading the workloads' run time block storage out of band, and cross-referencing this with cloud context pulled directly from the cloud vendors' APIs.

IBM and Red Hat launch edge computing solutions for the 5G era
The rollout of the 5G network, bringing greater speed and lower latency to mobile data, is going to provide a boost to the utility of edge computing.
The second announcement to come from IBM's virtual Think conference today is a set of new offerings built on Red Hat OpenShift, allowing enterprises to autonomously manage workloads across a massive volume of edge devices.
