How to set gorgeous Windows 10 Spotlight lock screen images as wallpaper
Windows 10 has a lock screen mode called Windows Spotlight that pulls attractive, high resolution images from the web on a daily basis. In most instances, you’ll only see these when you log on, or lock your PC.
If you see an image that you’d like to use as Windows wallpaper, you can’t simply right-click and save it, but there is a way to easily use Windows Spotlight images as your desktop background.
Increased security investments aren't stopping data breaches
Companies are putting more resources into security technologies to detect and respond quickly to a data breach, but the number of breaches is still increasing according to a new report.
The latest annual corporate preparedness study from Experian, based on research carried out by the Ponemon Institute, shows 68 percent of respondents are putting more resources into security, with 57 percent also reporting that they believe their data breach response plans are 'very' or 'highly' effective, up from 49 percent in 2018.

My trip down the rabbit hole of 'Huawei Search'
Poor Huawei. The Chinese company that America loves to hate has been struggling to weather a storm of U.S. regulatory actions that have left it unable pre-load its mobile devices with most Google services. That means no Maps, no Calendar, no Gmail -- and of course, no Google Play Store.
Huawei has tried to cope by developing its own stack of equivalent services, including home grown Maps and Weather apps, with mixed results. However, the one area where the rumored People’s Liberation Army (PLA) front company hasn’t yet dabbled is search. Until now

Leaked: 146 million records relating to users of railway Wi-Fi exposed online
An unsecured database has been found online that contains 146 million records about people who have used free Wi-Fi at railway stations in the UK.
The database was discovered by a security researcher on Amazon web services storage. It was found to include personal details such as usernames, dates of birth, email addresses and details of travel arrangements. Network Rail and the service provider C3UK have confirmed the data leak.

How to play the secret surfing game in Microsoft Edge -- and unlock the hidden NinjaCat player
Everyone loves a good Easter Egg, and Microsoft Edge has an absolute belter -- a hidden surfing game that you can even play using your Xbox controller.
The game was originally used by Microsoft when it was revealing the new logo for Edge, and it is designed -- much like Chrome's dino game -- to give you something to do when you're offline. The surfing game itself is a great bit of fun; here's how to access it, and how to unlock the secret NinjaCat character.
Microsoft starts rolling out new icons to all Windows 10 users
It is a few months since Microsoft first unveiled the new look icons for Windows 10 and various applications.
Now, having started the roll out of the new icons to Windows Insiders, the company is giving everyone access to the new designs. At the moment, it seems to be people running Windows 10 version 1909 that are affected, and this means they can enjoy new icons for Mail, Calendar, Calculator, Photos and more apps.

Microsoft is making Cortana much less useful for most people in a business-focused pivot
Microsoft is planning a major re-focus for Cortana; one that will mean the digital assistant becomes far less useful for most people. When Windows 10 version 2004 (or Windows 10 20H1) arrives, users will lose many of Cortana's consumer and third-party skills as Microsoft gives the assistant more of a business focus.
In dropping feature, Microsoft says that Cortana will be "focused on your productivity with enhanced security and privacy". Other significant change is the impending removal of Cortana from the Android Launcher app and a closer relationship with Microsoft 365.

How to activate all of Windows 10's secret God Modes
Windows 7 introduced a useful hidden God Mode that displays all of the admin tools and control options on a single screen. Because Microsoft has yet to phase out Control Panel entirely, this feature works just fine in Windows 10.
It’s very easy to action God Mode -- you just need to create a folder and give it a special name -- and there’s actually quite a few alternative God Modes available. Here’s what you need to do.
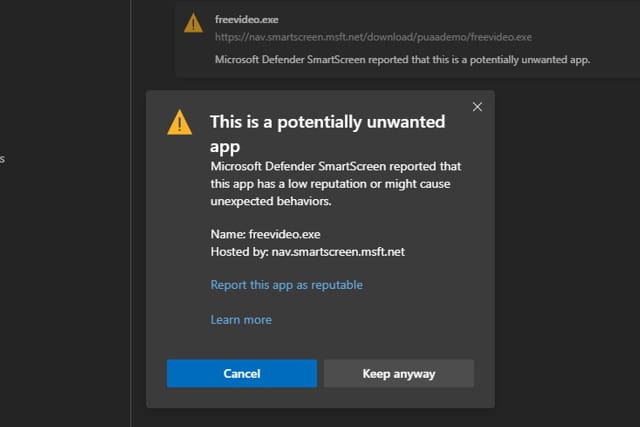
Updated Microsoft Edge will protect you from malware, crypto miners and more
With the switch to the Chromium engine, there's a lot more to like about Microsoft Edge these days. Microsoft is now pushing the browser hard, with the promise of serious speed improvements being used as a lure.
The latest update offers something extra -- protection against potentially unwanted applications (PUA). Microsoft Edge will now step in and block adware, cryptocurrency miners and other unwanted nonsense, particularly when downloading free software. The Microsoft Edge Team explains how to get the most from the protection.

Industrial cybersecurity put on notice as state-sponsored attacks persist
The continuing conflict among nations around the globe has been fueling a surge in state-sponsored cyberattacks.
Magnallium, a known advanced persistent threat (APT) group linked to Iran, has allegedly been trying to hack the US power grid by password-spraying private networks to potentially gain entry into this critical infrastructure. The act is believed to be part of a possible retaliation by Iran against the US in response to the escalation of military hostilities between the two countries earlier this year. Israel also recently reported to have thwarted hacking attempts on airport systems and planes of world leaders attending the World Holocaust Forum.

'M-m-m-my Corona!' [Humor]
The Coronavirus is everywhere! It’s in the air! It’s in elevators! It’s even crawling its way up through your toilet!
There’s no question, this is a major public health crisis, one that requires drastic containment measures. Which is why I am hereby formally declaring war on all things Corona! Anything and everything even tangentially associated with the virus or its name (including its official designation, COVID-19) MUST BE DESTROYED!
Arch Linux-based Manjaro MATE 19.0 'Kyria' available for download
A couple days ago, we shared some pretty great news with you -- Manjaro Linux 19.0 "Kyria" was finally available for download. This Arch-based operating system has exploded in popularity lately, so people were obviously excited to get the new version.
While Manjaro 19.0 initially came with three desktop environment options (GNOME, KDE, and Xfce) that obviously wasn't enough to please everyone. After all, this is the Linux community we are talking about here -- many users treat distros and desktop environments like tribalism. And so, MATE fans were sadly left out of the party. Today this changes, thankfully, as Manjaro MATE 19.0 is now available.

Microsoft releases KB4535996 update to fix Windows 10 search and printing problems
Microsoft has released a new cumulative update that, among other things, addresses problems introduced by previous updates to Windows 10.
The KB4535996 update applies to both Windows 10 1903 and Windows 10 1909. It fixes issues such as the Wiindows Search box failing to render properly, as well as network printing problems.

Why data quality is essential to cloud migration [Q&A]
Migrating to the cloud is an increasingly popular option for businesses, but to be successful the data involved needs to be in good shape.
We spoke to Kevin Kline, principal program manager at SentryOne, to find out why the quality of data is so essential to successful migration and what businesses need to do to ensure their migration succeeds.

YouTube TV strikes out with New York Yankees
YouTube TV is without a doubt the best streaming television service, but it is about to lose a lot of subscribers. You see, the TV service has lost the New York Yankees! As a New York Mets fan, this doesn't really bother me, but there are many hardcore Yankees fans in NY, and not watching their games is a huge deal breaker.
Sadly, YouTube TV sent out an email alert to its impacted subscribers in the New York area to tell them that at the end of this month, they are losing the Yes Network -- the channel that broadcasts the majority of Yankees games. In addition, FOX Regional Sports Networks will be dropped as well.
