Increase in third-party access puts OT environments at risk

A new report from Cyolo and the Ponemon Institute reveals that third-party access to operational technology environments is significantly expanding the attack surface.
According to the study, 73 percent permit third-party access to OT environments, with an average of 77 third parties per organization granted such access.
Google unveils Gemma: A new generation of open AI models for responsible development

Today, Google launches Gemma -- a new family of open AI models designed to help developers and researchers build responsible AI applications. Developed by Google DeepMind and other teams across Google, Gemma models are built on the same technology as the Gemini models.
Gemma models are available in two sizes: Gemma 2B and Gemma 7B, each with pre-trained and instruction-tuned variants. Google is also releasing a Responsible Generative AI Toolkit to guide the creation of safer AI applications. The toolkit includes a safety classification methodology, a model debugging tool, and best practices for model builders.
Published CVEs predicted to increase by 25 percent in 2024

The total number of common vulnerabilities and exposures (CVEs) is expected to increase by 25 percent in 2024 to 34,888 vulnerabilities, or roughly 2,900 per month.
This comes from a new report by 'active insurance' provider Coalition which uses honeypots to monitor for spikes to identify the biggest CVEs before they make news headlines -- thus providing companies with the opportunity to take action before an incident can occur.
Cyberattacks follow businesses to the cloud

Cloud intrusions increased by 75 percent overall last year as adversaries set their sights on the cloud through the use of valid credentials.
This is one of the findings of the 2024 CrowdStrike Global Threat Report released today. It notes an increase in interactive intrusions and hands-on-keyboard activity (60 percent) as adversaries increasingly exploit stolen credentials to gain initial access at targeted organizations.
Cybercriminals use identities to target enterprises

A new report from IBM X-Force Threat Intelligence highlights an emerging global identity crisis as cybercriminals double down on exploiting user identities to compromise enterprises worldwide.
The 2024 X-Force Threat Intelligence Index report records a 71 percent spike in cyberattacks caused by exploiting identity as using valid accounts has become the path of least resistance for cybercriminals, with billions of compromised credentials accessible on the Dark Web.
The evolving roles of the CIO and CISO [Q&A]

The relationship between an organization's chief information officer (CIO) and chief information security officer (CISO) has traditionally been somewhat at odds, since CIO's job is built around sharing information and the CISO's job is to secure it. Plus, the CIO was normally higher in the organizational hierarchy, which could also cause some tension.
But the relationship has evolved in recent years, to the point where the two positions are often more on par with each other. And with security's growing importance to the business (and the boardroom), the two jobs often share the same goals and responsibilities.
Xbox Insider Program: A decade of unpaid beta testing for Microsoft?

The Xbox Insider Program, initially known as the "Xbox Preview Program," marked its 10th anniversary in a blog post today. Over the past decade, the program has served as a platform for Xbox enthusiasts to provide feedback and participate in previews, ostensibly contributing to the development of Xbox products and services.
While the program has been touted as a way for fans to directly influence the future of Xbox, it raises questions about the ethics of relying on unpaid labor for product testing. Participants, often referred to as Xbox Insiders, essentially act as beta testers, identifying bugs and suggesting improvements without any form of monetary compensation.
Micron unveils Crucial T705 PCIe 5.0 SSD

Micron has unveiled the Crucial T705 solid state drive. This PCIe 5.0 SSD is built using the company's advanced 232-layer TLC NAND technology, aiming to maximize the potential of Gen5 performance levels. It offers sequential read and write speeds up to 14,500MB/s and 12,700MB/s respectively. These speeds are promise quicker gaming experiences, faster video editing, and more efficient 3D rendering and AI application processing.
In terms of design, the T705 SSD features a premium black aluminum heatsink. This design choice is not just for aesthetics; it serves the practical purpose of dissipating heat efficiently. The SSD is engineered to operate without the need for noisy fans or liquid cooling systems, which could be an advantage for users seeking a quieter computing environment. Additionally, the T705 SSD is backwards compatible with Gen3 and Gen4 motherboards.
Acer unveils new Swift Edge 16 and Swift Go 14 Windows 11 laptops with advanced AI capabilities

Acer has announced the latest additions to its Swift series, the Swift Edge 16 and Swift Go 14. These laptops are designed to offer a blend of AI power and innovative features in a stylish, thin, and light package. Seriously, folks, they are both quite stunning.
These new models are equipped with AMD Ryzen 8040 Series processors, up to AMD Radeon 780M Graphics, and Ryzen AI technology, providing versatile performance and support for Acer’s AI-powered capabilities such as Acer PurifiedVoice, Acer PurifiedView, and the new Acer LiveArt photo-editing feature.
CORSAIR launches K65 PLUS WIRELESS gaming keyboard with compact design and customizable features

CORSAIR has released the K65 PLUS WIRELESS. This keyboard features a compact 75% profile, which saves desk space while including essential arrow and utility keys for convenient game controls. It comes equipped with pre-lubricated CORSAIR MLX Red linear switches, known for their smooth operation and crisp responsiveness. These switches are hot-swappable, allowing users to customize the keyboard with their preferred switches.
In addition to its performance capabilities, the K65 PLUS WIRELESS is designed for a satisfying typing experience. It incorporates two layers of integrated sound dampening to reduce internal noise, resulting in quieter keystrokes. The keyboard is adorned with PBT dye-sublimated keycaps in midnight gray and silver accents, making it a stylish choice for daily use.
Plugable USBC-6950M is a compact dual 4K HDMI adapter for Apple Silicon Macs

Plugable has launched its latest offering, the USBC-6950M. This is a USB-C dual 4K HDMI adapter specifically designed for Apple Silicon Mac users seeking to expand their screen real estate beyond the laptop’s native capabilities. While it is designed for Apple Silicon Mac computers, it is not limited to them -- it is compatible with Chromebooks and Windows laptops too.
The USBC-6950M enables users to connect dual 4K 60Hz displays to their Macs effortlessly. It should be a great option for business travelers, hybrid office users, or anyone aiming to boost the productivity, really. It provides a seamless dual-display experience without the need for a full docking station, making it a convenient solution for those on the move.
Sophisticated phishing campaigns bypass enterprise secure email gateways

A new report from Cofense based on data from its Phishing Detection Center identifies over 1.5 million malicious emails bypassing customers' secure email gateways (SEGs), a 37 percent increase in threats compared to 2022.
The report shows that SEGs struggle to keep pace with sophisticated phishing campaigns and that relying on 'good enough' email security is no longer an option for most enterprises.
New solution secures any browser for the enterprise

With more and more businesses relying on SaaS solutions, securing the endpoint browser is vital. Often this involves enterprises imposing a particular browser on their users rather than allowing a choice.
In a new approach, Menlo Security is launching a complete enterprise browser solution that can turn any browser into a secure enterprise browser.
Windows 12 Mobile is everything a phone operating system should be
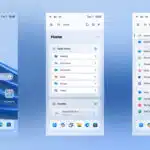
Microsoft made a significant investment in Windows 10 Mobile, including acquiring Nokia to produce its own handsets. Despite the strengths of the tiled mobile operating system, it was unable to compete with the dominant iOS and Android platforms. While Windows 10 went on to become a hugely successful operating system for PCs and tablets, Microsoft was eventually to abandon its mobile ambitions.
Although the tech giant has yet to announce Windows 12, if you’re wondering how that OS would look and perform in the mobile space, we have an answer.
The phishing bait you're most likely to take

Phishing is the most common form of cyberattack as criminals seek to obtain credentials to access bank accounts or corporate networks.
Abnormal Security has analyzed which phishing attacks generate the highest click rate and categorized them based on the words included in the subject line.
Most Commented Stories
It's finally time to say goodbye to Windows 11 -- Nitrux Linux 3.7.0 is the OS you've been waiting for!
Windows 12.1 is everything Windows 11 should be -- and the Microsoft operating system we need!
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.




