
Microsoft releases KB5070311 update to fix a bunch of Windows 11 issues – and it has problems
Microsoft has managed to do it yet again. On the face of things, the KB5070311 preview update is a great update that not only addresses problems such as File Explorer freezing, but also introduces a raft of new Copilot features.
But, as you will have probably gathered, it does not end there. The KB5070311 preview update is another issue-riddled update, this time breaking dark mode in File Explorer.

New AI assisted tool aims to cut manual processing time for complex PDFs
Extracting data from intricate, awkwardly structured PDF files can be tricky. Tables don’t always line up, text can be weirdly formatted with odd spacing, and it can take ages to copy, check and fix all the various problems by hand.
NE2NE has announced PDFFlex, a new AI assisted tool designed to convert complex PDF content into structured formats such as Excel, XML or JSON. The program brings together several parsing methods and machine learning recognition to handle documents that might previously have been hard to reliably extract data from.

Visa finds shoppers turning to AI and crypto this holiday season
Visa has released the findings of a new survey that show how AI and digital tools are beginning to have an impact on holiday spending habits across the United States. The company says that it is seeing clear differences across generations, with younger consumers moving towards AI assisted shopping, digital currencies and other emerging payment trends.
"The data tells a fascinating story about the spending shift we're witnessing: shoppers are embracing AI and digital tools at remarkable speed, with nearly half of Americans now using AI to enhance their shopping experience," said Bruce Cundiff, vice president, Consumer Insights at Visa.

File-sharing platforms not protecting against malicious content
Cybersecurity company Surfshark has reviewed popular file-sharing platforms and finds that the majority of them don’t scan your files for viruses, nor do they protect you from malicious software on their free plans.
Box and WeTransfer, which together have a total of 138 million registered users, do not scan for viruses on free plans but begin scanning files on paid plans. Dropbox, with 700 million registered users, does not offer scanning at all.

Rapid adoption of agentic AI runs ahead of security readiness
New research finds just two percent of organizations with 500+ employees report having no plans or interest in agentic AI. Indeed a significant portion of respondents are already using or interfacing with AI agents for both internal and external tasks.
But the study, from Enterprise Management Associates (EMA), reveals a critical, organization-wide inability to prepare for the identity and security challenges which these autonomous entities introduce.

Could 2026 be the year you finally update your money habits for a digital-first world?
The way you move money in your daily life has likely changed faster than your old habits have. Cash used to be king, but the pandemic changed things, and accelerated the move to digital. You can now pay friends instantly, subscribe to half your world through your phone and check cryptocurrency prices live the same way you check for the weather.
As 2026 approaches, the financial world is shifting beneath your feet, whether you have adapted or not.

Experian: Cyber threats are no longer just about stealing data, they're about manipulating reality
Experian has released its 2026 Data Breach Industry Forecast. The report covers how cyber threats are expected to evolve in the next year (and beyond) as attackers adopt AI, quantum computing and other emerging tools. Now in its thirteenth year, the forecast makes six predictions that point to more personalized and more persistent intrusion attempts.
The report looks at how cybercriminals are using new technologies to build synthetic profiles, deploy autonomous AI agents and develop malware that can alter its behavior in order to avoid detection. It also raises early concerns about the potential risks connected to brain computer interfaces as those technologies move forward.

88 percent of organizations worried about state-sponsored cyberattacks
A growing sense of unease is gripping boardrooms as 88 percent of cybersecurity and information security leaders surveyed at UK and US organizations now express concern about state-sponsored cyberattacks.
The research from IO shows organizations are increasingly aware of the strategic nature of cyber risk and that the geopolitical threat is increasing, with 33 percent of organizations surveyed concerned about an expanded threat landscape targeting their own systems.

Microsoft confirms the new Outlook has an Excel attachment problem
The new version of Outlook has not proved as popular as Microsoft would have liked, and the company has just been forced to admit to another problem with the email client.
Microsoft has published a warning about a problem with open Excel file attachments, noting that the issue has been around for about two weeks. The cause appears to be the use of non-ASCII characters in file names, and a fix is in the works.

No, Meta is not going to use your DMs to train AI
Every so often there are posts that do the rounds on social media that suggest terrible policy changes are coming. This is happening again, with a message claiming that Meta is going to start using the content of private DMs to train AI.
The unfounded claims are being tied to a Privacy Policy update which is due to come into force on December 16. While it is certainly true that Meta’s new policy kicks in in a couple of weeks, there are falsities being attached to it in scaremongering posts that have gone semi-viral.

A Windows update may have slowed game performance – and NVIDIA has the fix
It is far from uncommon for Microsoft to release an update for Windows that causes problems with the operating system itself. It is also not unknown for Windows updates to cause issues in other software – and this is what some gamers have experienced.
In releasing a new GeForce Hotfix Display Driver, NVIDIA has pointed the finger of blame at a recent update for Windows 11 for slowing down the performance of some titles. Despite NVIDIA’s claims, Microsoft is yet to say anything about the issue.

Apple appoints new vice president of AI as John Giannandrea steps down
Apple has announced that its senior vice president for Machine Learning and AI Strategy, John Giannandrea, plans to retire. Having been with the company since 2018, he will serve as an advisor for a short time before moving on in spring next year.
While no reason has been publicly given for the departure, it is widely thought that there was a degree of discontent at Giannandrea’s management of Siri. The product was blighted by a series of delays and problems that did not reflect well on Apple.
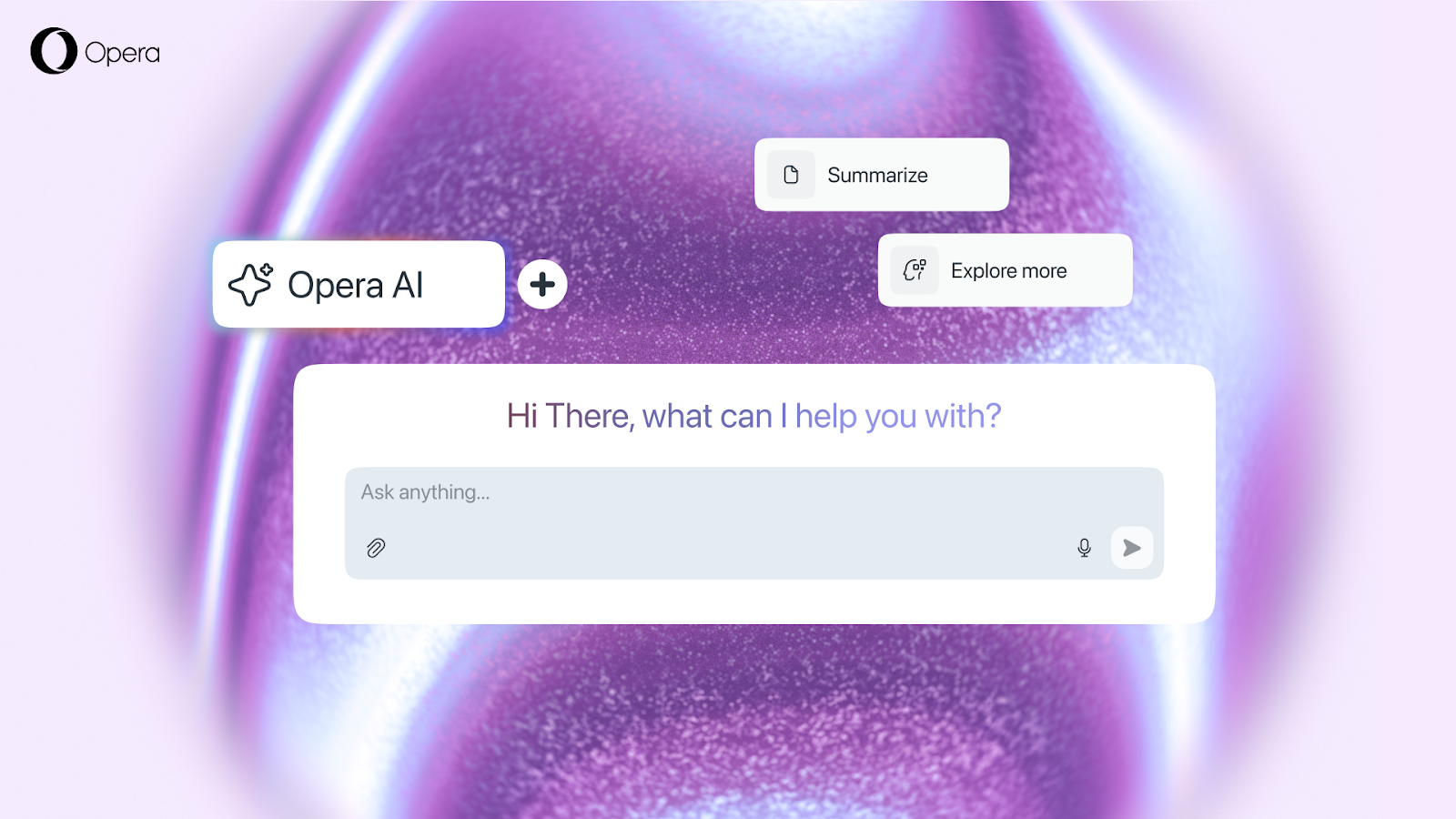
Opera brings upgraded Google AI to its browsers
Opera is rolling out new Google AI features across its Opera One, Opera GX and Opera Neon browsers. This is the result of the browser maker's long running partnership with the search giant, and now includes support for the latest Gemini models.
The new Opera AI appears as a side panel that users can open alongside any webpage, set of tabs, or even playing videos. It will respond within the context of the page, allowing tasks such as research, summaries and tab comparisons. It also supports voice input and output, along with file analysis on images and video.

Sumo Logic brings agentic AI to cybersecurity investigations
Modern security operations centers (SOCs) face a perfect storm of complexity: growing alert volumes, fragmented tools, and pressure to respond faster than ever.
Intelligent operations platform Sumo Logic is announcing new advancements to Dojo AI, its enterprise-grade agentic AI platform for security operations to help security teams reduce alert fatigue, accelerate investigations, and streamline security workflows.

Desktop web traffic overtakes mobile for the first time in 5 years
Global web traffic has done something unexpected, with desktop devices overtaking smartphones for the first time in five years. Data presented by Jemlit shows desktops claimed a 49.7 percent share of worldwide browsing in October, placing them just ahead of smartphones on 48.98 percent.
Mobile phones have held more than 60 percent of global browser traffic for much of the past three years, supported by faster networks and the way people increasingly use their phones for news, shopping, search, and entertainment. Even so, new StatCounter figures show the change began several months earlier, with desktop traffic showing a steady rise from June.



